
News: Marvel Continues Its Augmented Reality Rampage with Iron Man Robot for 'Avengers: Endgame'
Already a dominant force at the box office, Marvel Studios appears intent on establishing itself as the ruler of augmented reality media as well.


Already a dominant force at the box office, Marvel Studios appears intent on establishing itself as the ruler of augmented reality media as well.

While Magic Leap turned heads at the Game Developers Conference with AR experiences at the Unity and Unreal Engine booths, news broke that the company was the winning bidder for ODG's patents.

While the tech industries giants and eager startups chase the dream of widespread consumer augmented reality, enterprise AR is living the dream today.

Websites are often misconfigured in ways that allow an attacker to view directories that are not ordinarily meant to be seen. These directories can contain sensitive information such as private credentials or configuration files that can be used to devise an attack against the server. With a tool called Websploit, hackers can scan targets for these hidden directories without difficulty.
For those of you who like to frequently change the icon shapes on your home screen, the process has changed in Android 10. The setting is buried and now applies to more than just home screen icons.

While a release date for Harry Potter: Wizards Unite has not yet materialized, co-developers Niantic and WB Games have finally released gameplay footage and an in-depth game description to whet the appetites of eager Harry Potter fans.

The hype for HBO's Game of Thrones reached proportions as epic as the series itself this week with the latest release of the final season's official trailer, but it's a Snapchat promotion that will truly make fans at SXSW bend the knee.
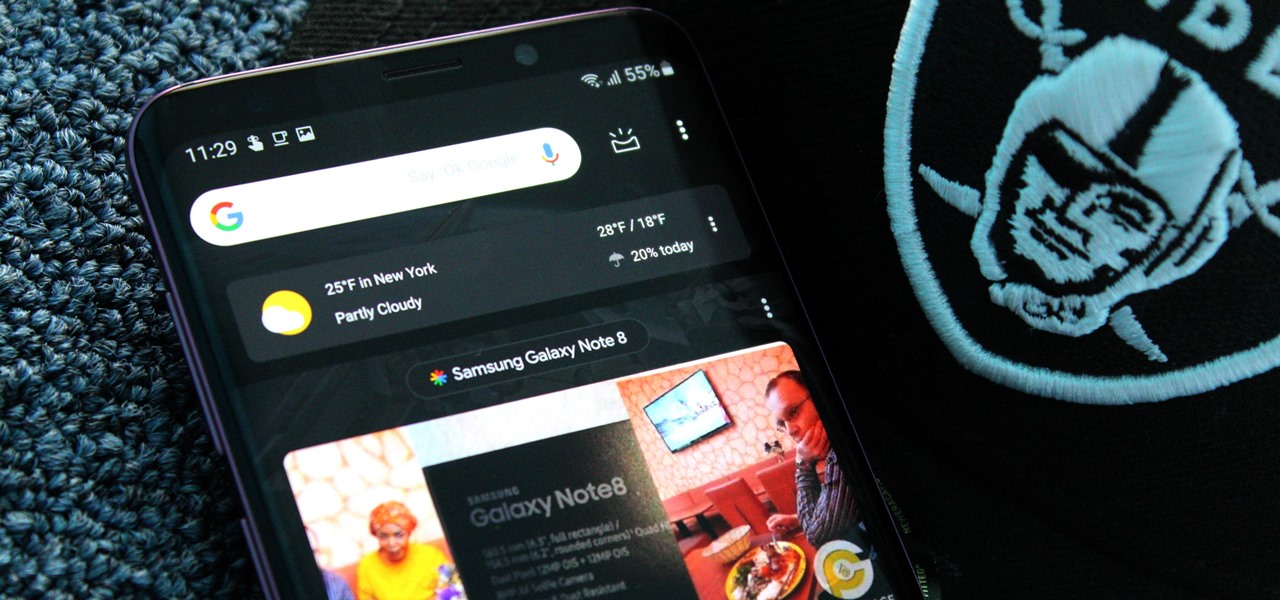
The word on the street is Android users want a dark mode. With the increased usage of AMOLED panels on smartphones (including some midrange devices), there is a considerable demand for dark themes and their battery saving benefits. Recently, Nova just added the feature to Google Discover.
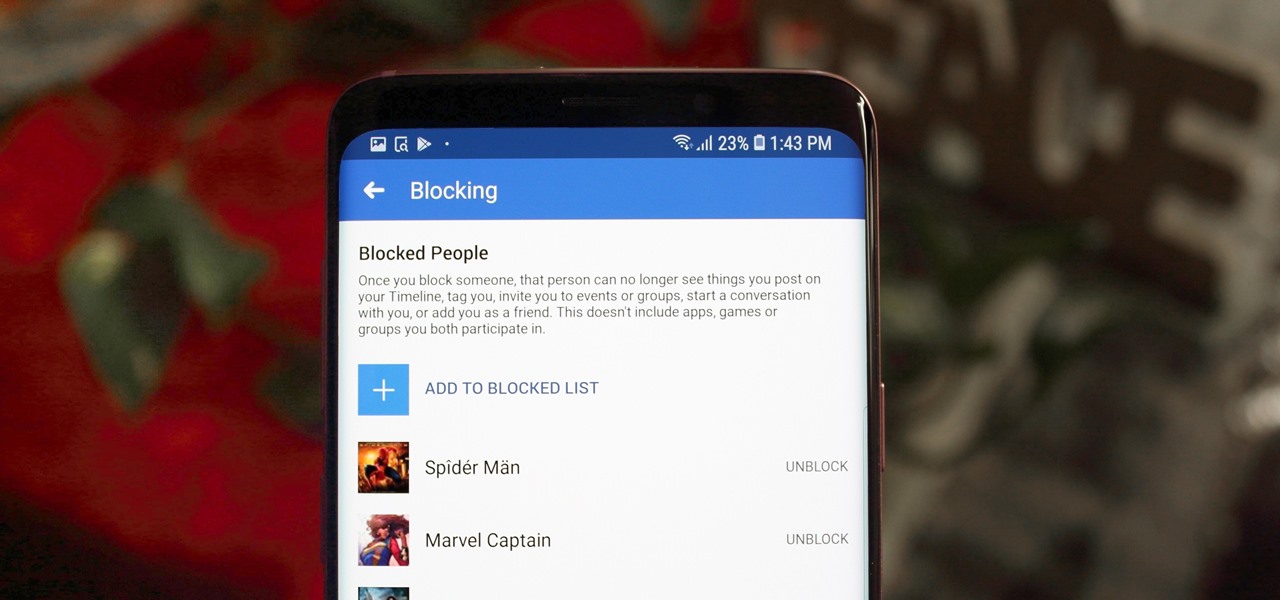
Whether it's an ex you can't stand, that annoyingly political friend of a friend, or good old fashioned trolls, the block feature on Facebook can be a great way to de-stress your feed. It will keep people from contacting you, and it will also prevent them from viewing your profile altogether. It's not just a tool for the full desktop website — in fact, the blocked list is easy to manage right from your phone.

Returning to the spotlight after its debut at last year's CES, augmented reality smartglasses maker Rokid is back with a new update.

You've had your fun swiping, but now it's time to walk away from all of your online dating apps. Whether it's because you found someone you're interested in or just need some time away, it's important to know how to permanently erase your online dating footprint — and that includes deleting your Bumble account.

After joining Google and Huawei in underwriting the UW Reality Lab at the University of Washington in January, it appears Facebook is already seeing a return on its donation.
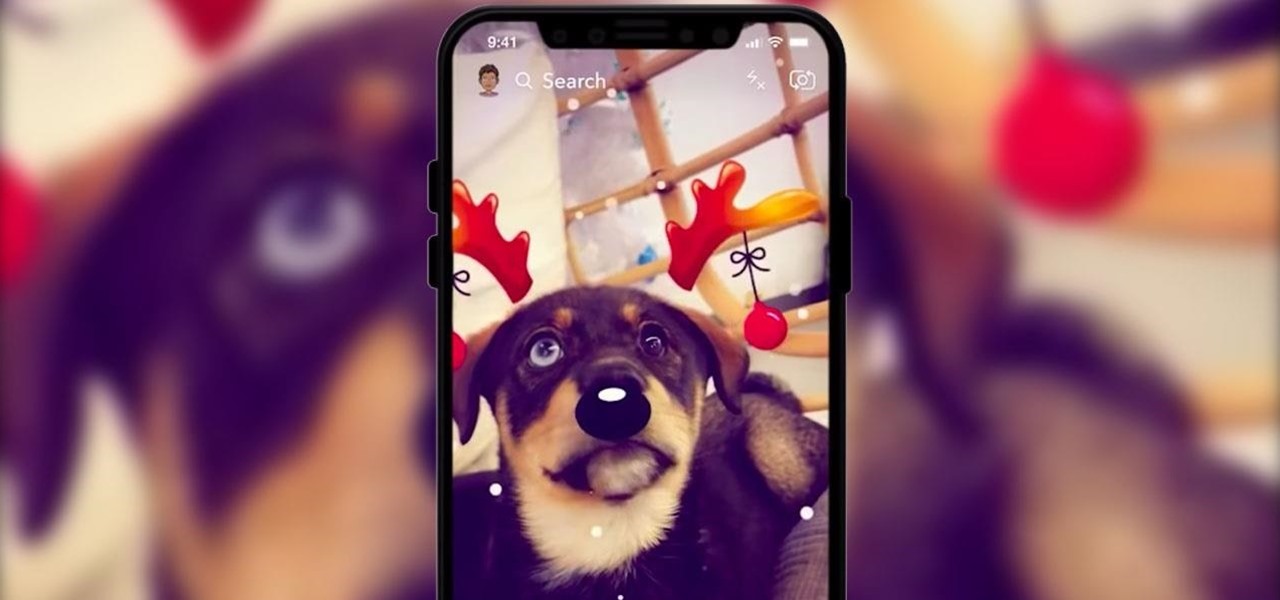
First, there was SnapCat. Now, we have DogChat! Or SnapBark? In October, Snapchat took social media by storm with its Lenses for cats. But the latest addition to the camera app has given dog lovers an augmented reality Christmas gift they won't want to return.

Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.

According to App Annie, the average person's phone contains 60–90 apps. Such a large amount can easily crowd an app drawer, especially since the same source states that only about 30 are used in a month. Having a way to organize apps in the app drawer can help you avoid wasting time searching.

Automotive augmented reality display maker WayRay is making a move to help developers get all those slick, futuristic AR functions we see in concept videos into the real cars of today.

Before you can dive into customizing your OnePlus 6T, you must take the initial step of unlocking the bootloader to gain the ability to install TWRP, Magisk, custom ROMs, and other mods.

Apple unveiled the iPhone X-like redesign of its iPad Pro line Tuesday, Oct. 30. Among the many new changes to the company's famous tablet was a glimpse at its new wallpapers. These images, while clearly intended to take advantage of the new iPad's striking screen ratio, are clearly well suited for any iPhone as well. That's why we've made it easy for you to download them all.

Electronic Arts is inviting players of The Sims Freeplay and their friends to visit the homes of their Sims in augmented reality with a new AR mode that supports multiplayer and persistent content using ARKit 2.0.

Have you ever browsed through Lenses on Snapchat and got bummed out when the app recommends that you "try this with a friend" and you're all alone? Well, now you can take AR snaps with your cat!

Late last year, we got a little surprise from Razer. The gaming company released its first smartphone, and as expected, it targeted gamers. Branded as a gaming phone, it started a trend which several other companies followed soon after, including ASUS, Xiaomi, and even Samsung. So as you can imagine, many are excited about its successor.
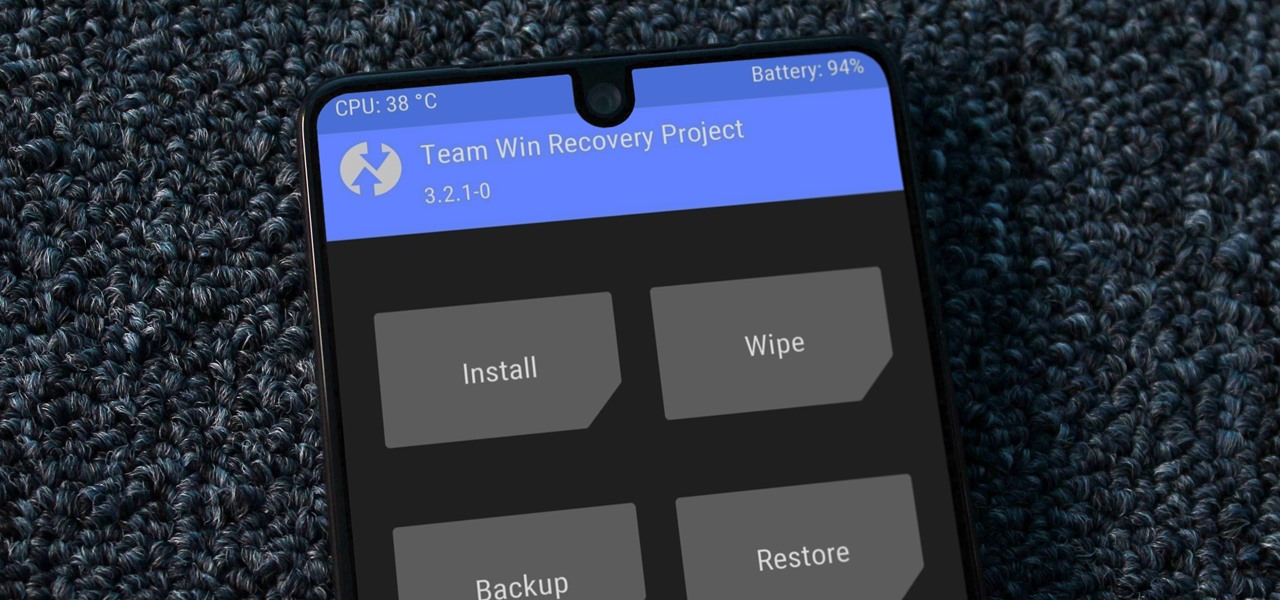
For modders, there are few tools more important than TWRP. TeamWin's custom recovery makes flashing mods like Magisk, Xposed, and custom ROMs incredibly easy, and it lets you root your phone at the press of a button. On top of that, it can make complete backups of your phone in case you mess up. That's why, for Essential users, this should be the first mod you add.

Apple released the first beta for iOS 12.1 on Tuesday, Sept. 18. The update comes just one day after the official release of iOS 12. For developers, it's the first beta release since the "gold master" version on Sept. 12.

Facing mixed reviews for the Magic Leap One, Magic Leap has already returned to the lab to improve on the device's successor.

As a longtime Android user, one of the changes I was most excited about with Android Pie was the fact that the volume rocker finally controls media volume by default. However, the new way isn't ideal for everyone, but thankfully, there's an app that can change it back.
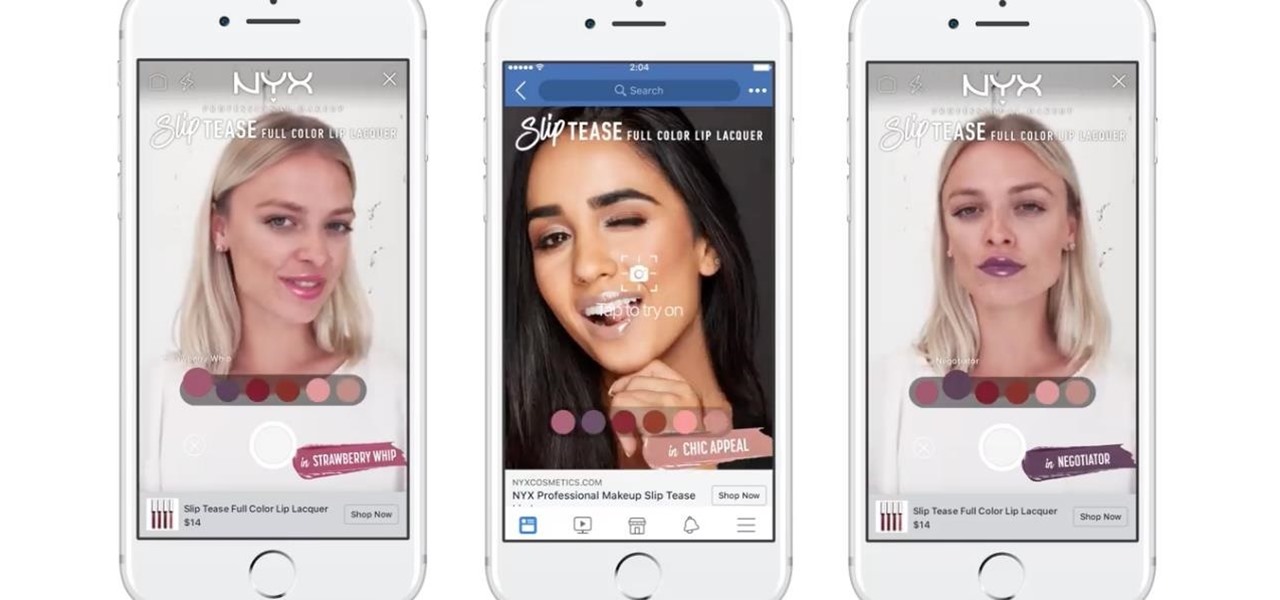
Already one of the leaders in augmented reality for cosmetics, L'Oréal is extending the reach of its ModiFace virtual try-on platform through a partnership with Facebook.
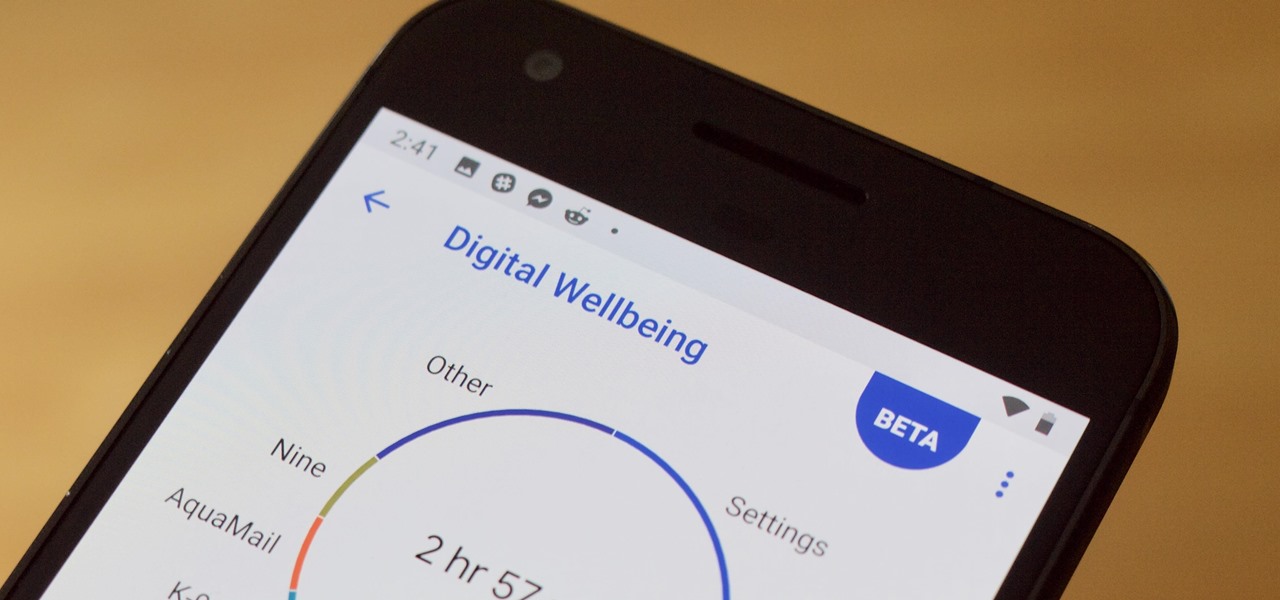
Is your smartphone taking over your life? Do you need help putting your Pixel down at night? Well, update to Android Pie! Android 9.0 comes with Digital Wellbeing, a new tool to both help you understand your smartphone habits and perhaps step away from the apps, games, and notifications every now and then.
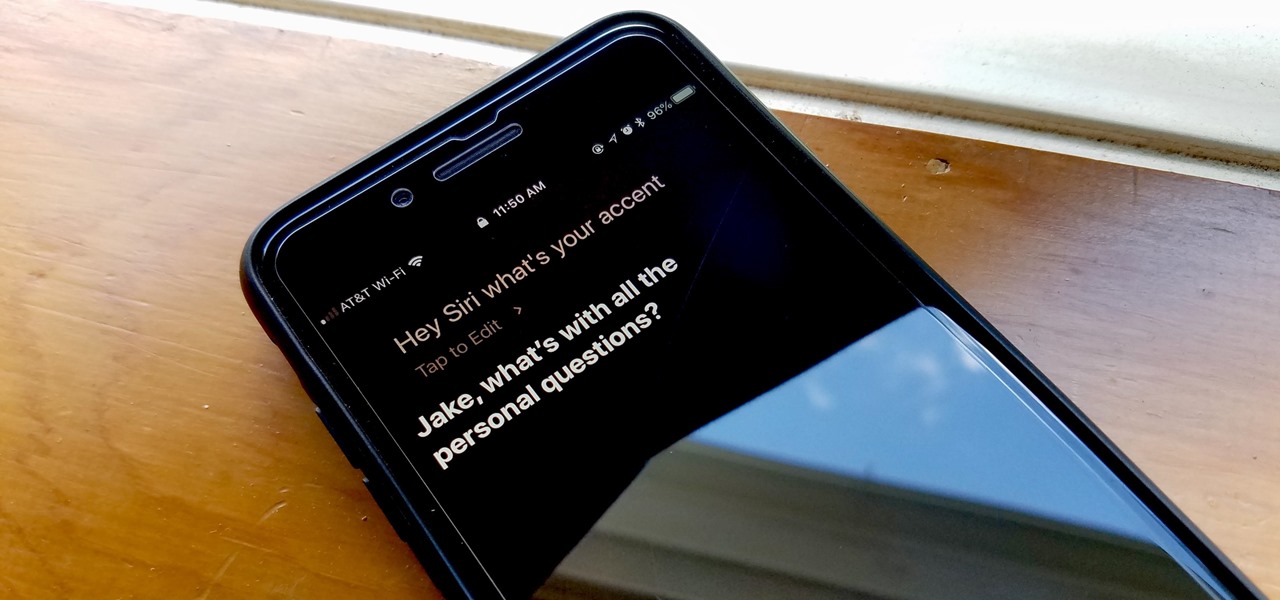
Apple's iOS assistant has an undeniably iconic voice — you know Siri when you hear her. As memorable a voice as it may be, you don't need to stick with her default American accent. In iOS 11, you can choose from two other vocal deliveries, and in iOS 12, there are two more accents at your disposal for a total of four more.
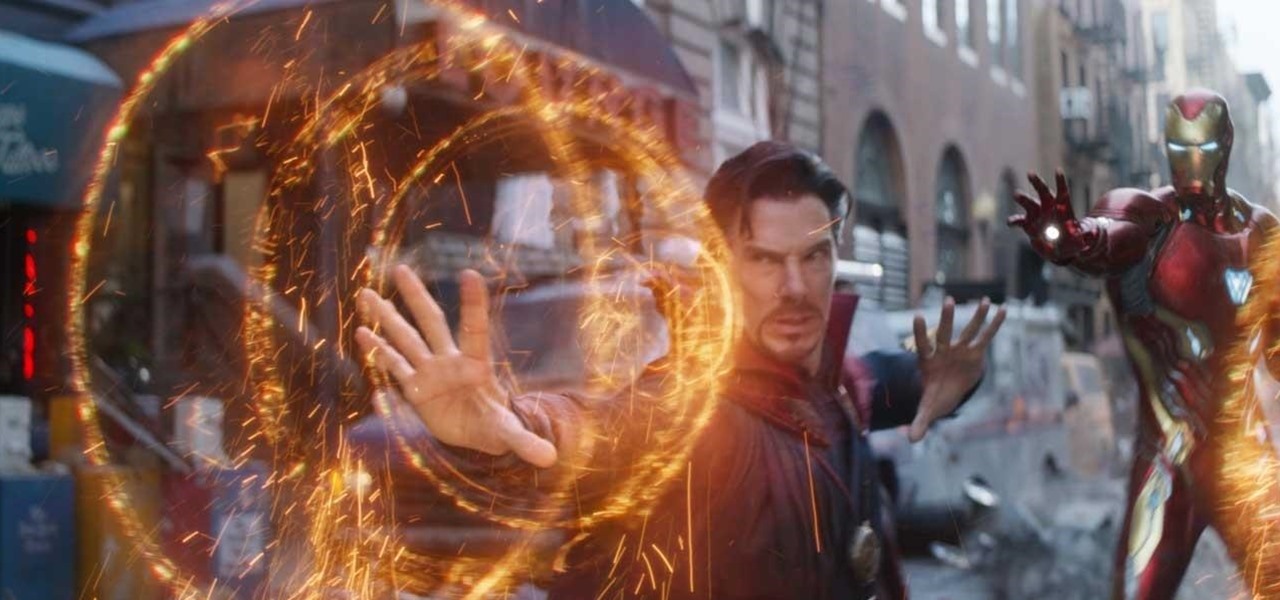
For years, Magic Leap has promised to deliver stunning augmented reality experiences that will outperform any other competitor, and a newly revealed partnership hints that the company may be able to deliver on those promises.
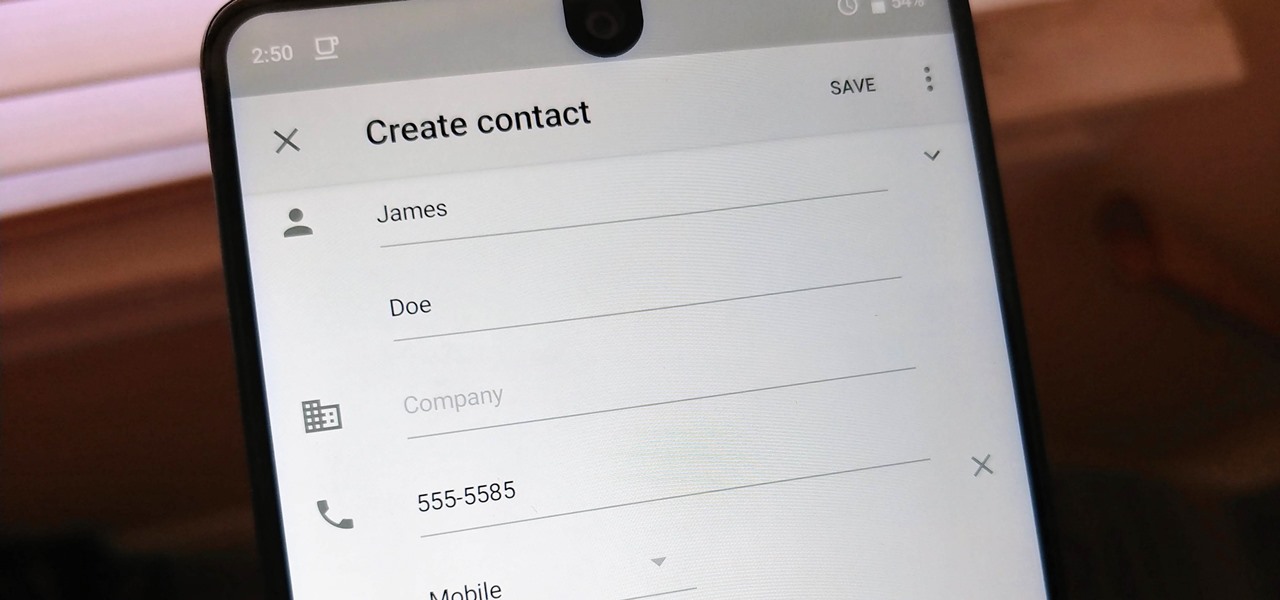
Android lets you sync your contacts across devices. The OS will use not only contacts saved on your phone, but also your Gmail. This choice can lead to a contacts list populated with entries that don't have a phone number, which can quickly add up. To mitigate this problem, there are a few methods.

Among its many new features, Android P returns the spirit of lock screen widgets to users by presenting the current temperature and weather conditions underneath the clock. It isn't flashy, but it's a fun and useful addition that, unfortunately, does not always work. If your lock screen weather isn't showing up, you might want to try these steps to fix it.

Whichever web browser you use, each comes with a way to surf the net "secretly." While nothing on the internet is truly anonymous, private browsing modes can help keep your movements hidden from those who might have access to your data. The "secret mode" for the Samsung Internet app goes a step further on Android, by locking your private browsing behind a unique password.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.

According to Google at their 2018 I/O conference, Google Assistant is now available on over 500 million devices. Now that the assistant is available on iPhones as well, Google has to give iOS users a reason to switch to its assistant over the built-in Siri. Today, Google has eight more reasons for users to do so.

If $200 was too much for you to get in on some Star Wars augmented reality action, Best Buy is now selling refurbished Star Wars Jedi Challenges sets for $79.99 and new ones for $99.99.
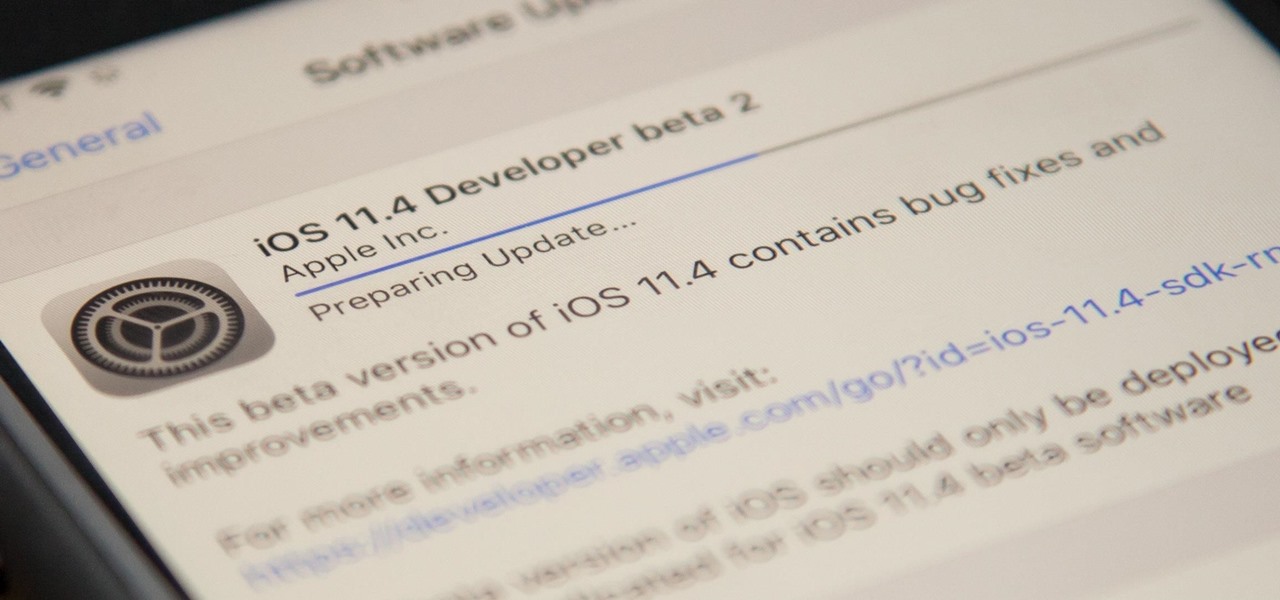
Apple released the second beta for iOS 11.4 on Monday, April 16. Its release comes eighteen days after the company pushed the first 11.4 beta to iPhones, as well as the official build of iOS 11.3. This beta fixes issues with AirPlay, Music, and Keychain, and it also adds a new wallpaper.
Update: Google's new Pixel models have been released! Check out our full guides on the Pixel 3 and Pixel 3 XL to see all the details, but we'll leave the rumor roundup intact below for posterity.
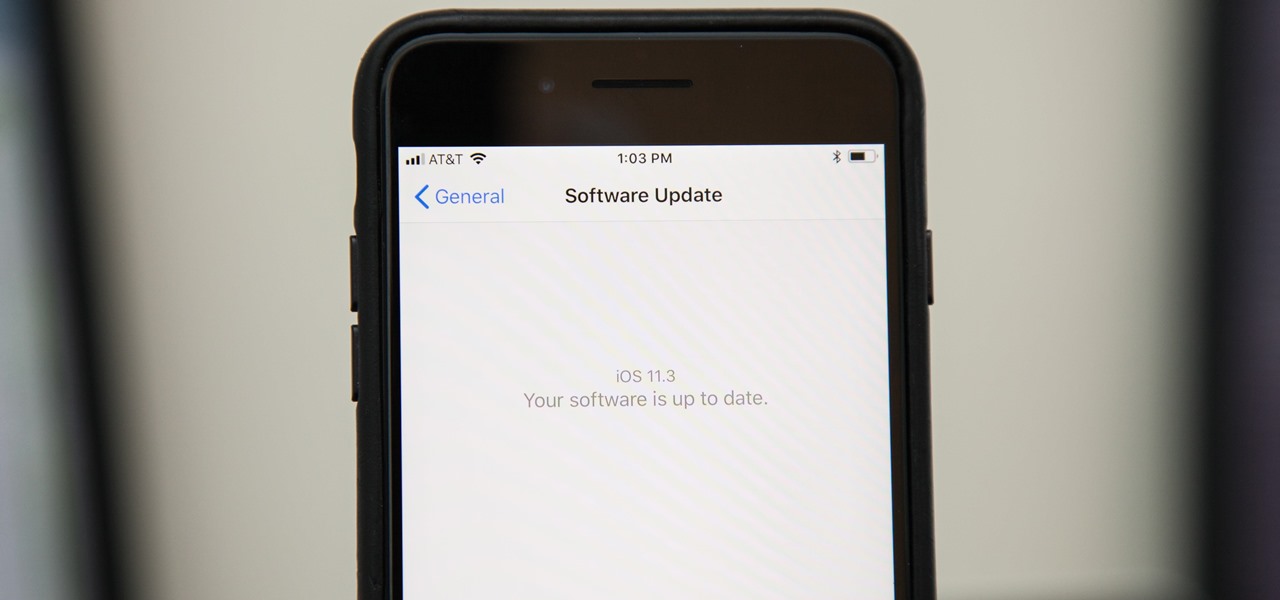
Three months after its promise, Apple has pushed out an iOS update that gives you important information about the health of your iPhone's battery. This means you no longer need tools such as Geekbench and Battery Life to determine whether or not you need a replacement battery.

While Apple usually sets the precedent for its consumers to follow, the iPhone SE returned the company's iconic smartphone to a small form factor, one that had been ditched by the iPhone 6 and beyond. However, it appears Apple is finished with 4-inch phones for good, as the iPhone SE 2 looks to be even larger than last year's iPhone X.
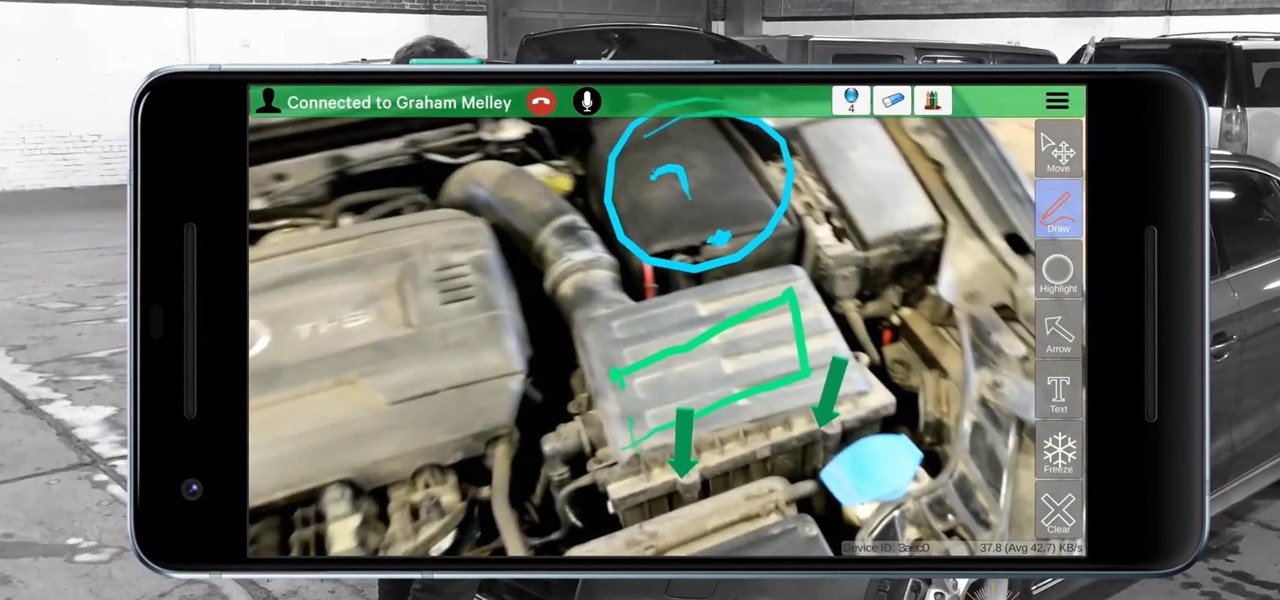
Scope AR has decided to take its live remote assistance enterprise application, Remote AR, further into the mobile augmented reality realm by harnessing the powers of Google's recently released ARCore.