Preparing and serving seafood can be a daunting task. Fish is so delicate that one extra minute of heat can turn a juicy, flaky filet into a dried-out disaster. But that same fragility also allows us to use unconventional methods to chemically transform the fish into its cooked consistency.

In the world of breakfast, a great trench of injustice divides French toast and pancakes. Just look at the average brunch menu. While pancakes are treated to a wealth of variety (chocolate chip, silver dollar, blueberry, banana, and even some with pop culture references), French toast is often regarded with a one-size-fits-all attitude.

Returning your device to stock, whether it is because you need to sell it or just want to receive OTAs again, is not always a simple process. Since HTC has released countless variations of both the M7 and M8 HTC One, it can be a pain in the ass finding the right files and tools to get your phone back to stock settings.
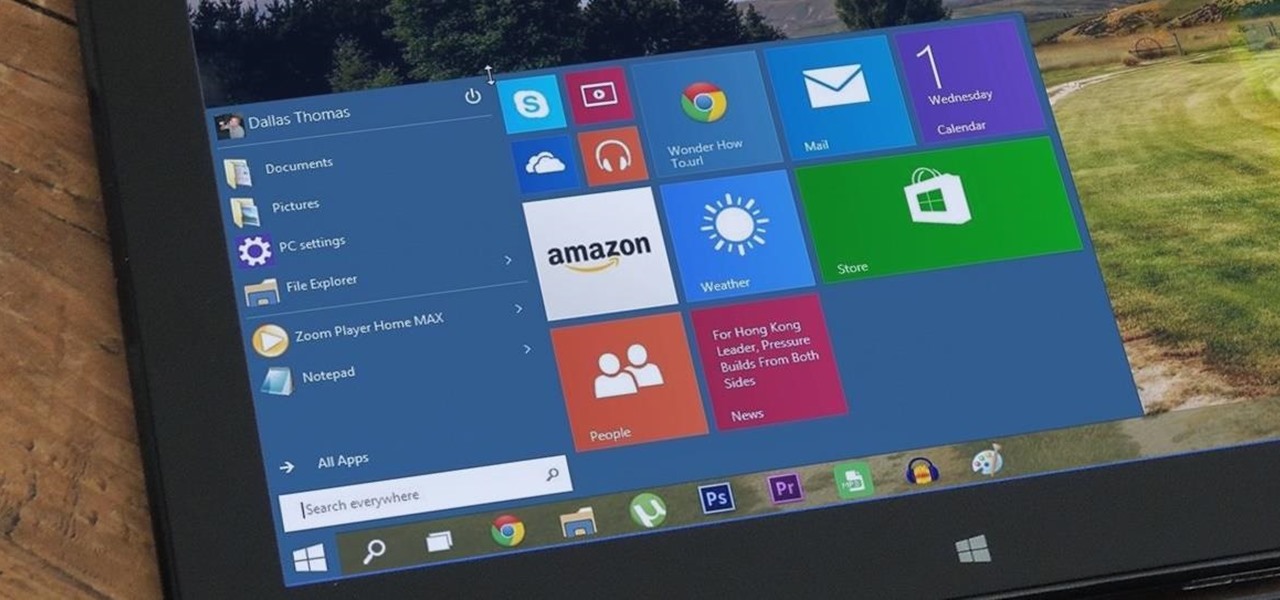
Windows 10 marks a new era for Microsoft with the return of the Start menu, the demise of Internet Explorer, and the introduction of the remodeled Windows Store.

Developing GUI apps in python is really cool. I ask those who understand the language to help convert some of the command-line or console programs or apps ( I mean programs that are useful to a hacker ) to GUI. I know GUI makes us lazy and not wanna learn but we should all know its fast. Today's tutorial is on p2p chat app I developed last week and decided to share it with the community since its kinda cool.

In recent weeks, major bank websites around the world have experienced outages after being have been hit with Distributed Denial of Service (DDoS) attacks. Although few, if any, of these banks have been totally knocked offline, these DoS attacks have dramatically slowed the response time of their websites to legitimate customers. The most recent victim was the Royal Bank of Scotland. Due to this attack, RBS customers were unable to access their accounts for about an hour last week.

hello my dear colleagues, I made a visit to nullbyte and found that there is not a complete tutorial about the google dorks, so I felt the need for this tutorial, and seeing that there are many newbies around, so here's a tutorial that will teach you how to use google to hack.

A long time ago I was reading an issue of Saveur and saw an article about a trendsetting bar in Portland. The bartender at the joint had started making enormous blocks of smoked ice for his cocktails. When a patron ordered a drink that called for the smoked ice, the bartender would chip off a large chunk and place it in a glass with the booze. Then, as the ice slowly melted, the drink would take on more and more smoky notes, and the flavor profile of the beverage would change with every passi...

No offense to water, but if I could survive on coffee alone, I would. I swear I'm not addicted... I just really, really, really love the taste of a cuppa joe, whether it's hot, cold, frothed, milked, flavored, plain, whatever! And while my favorite thing to do with coffee will always be to drink it, recently I've become crazy about using coffee in cooking.

We've all been there: we're enjoying a nice cob of corn, happily covering our face in butter and salt, when suddenly we realize that there's a thread of corn silk stuck in our teeth. We try to dislodge it with our tongue; no luck. We pick around with our fingers; still no luck. That silk is staying there until you return home to your toothbrush and dental floss. And if you think that corn silk is bad for most people, try having braces!

Welcome back, my aspiring hackers! In many of my earlier tutorials, I mentioned the complementary nature of hacking and forensics. Both disciplines, hacking and forensics, benefit from a knowledge of the other. In many cases, both disciplines will use the same tool. In this tutorial, we will use another tool that can be used in either discipline—Sysinternals—a suite of tools developed by Mark Russinovich.

Hi there, Crackers, Welcome to my 7th post (Part-1), this tutorial will explain about the basics of Batch Scripting.

Hi nullbytes! I've been recently reading the whole Linux Basics for the Aspiring Hacker series and felt like it was missing some stuff I know, so I felt like sharing it with anyone who might find it useful too.

Hi everyone! Last time we explained what roles Ebp and Esp registers have. We first introduced function's stack frame building, return address and calling conventions, but left some of the concepts floating without a full stop.

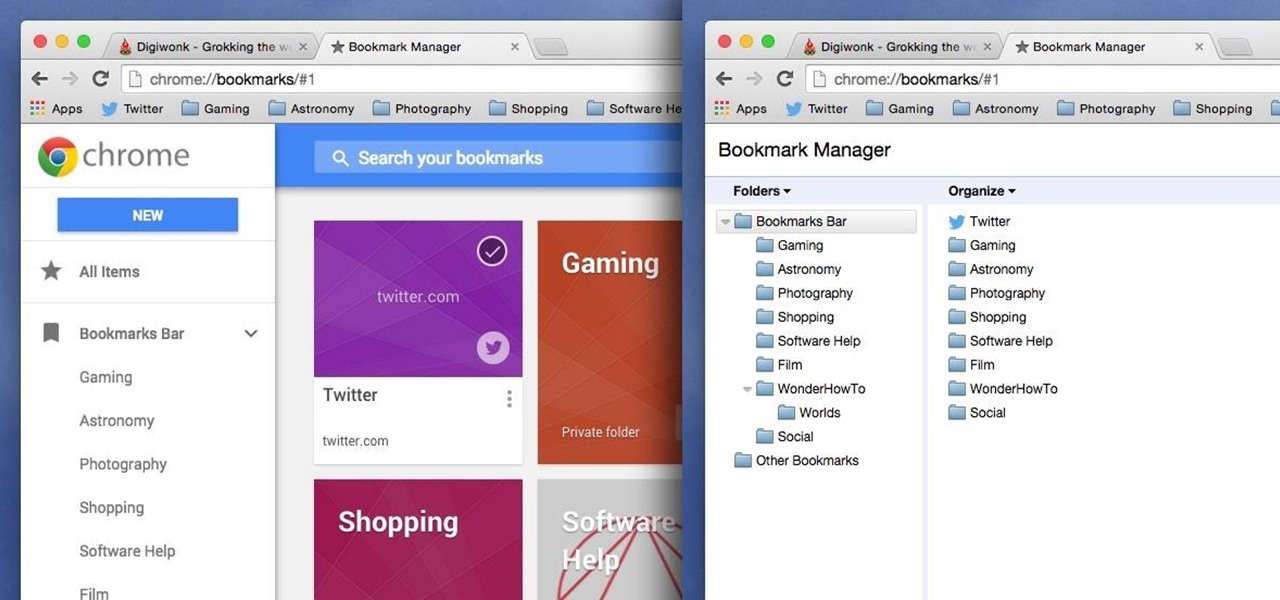
Chrome has been pushing out a lot of new changes lately, but not all of them are as good as they think they are. Earlier this year, there was an update that changed how user profiles worked, which made it harder to actually switch profiles. Luckily, there was a way to get back the old profile management interface, but now there's another "improvement" that you might want to change—Chrome's new Bookmarks Manager interface.

Most of the time we only use the microwave to reheat or defrost, but you can actually save a lot of time by using it for cooking. These genius recipes make the most of this underused appliance, and also turn out some pretty tasty dishes.

If you've got a desktop computer, I can almost guarantee that you've got a widescreen monitor set up in landscape mode. It's how just about everyone uses their monitor these days, including myself. Except that it's not always the best way of working.

YouTube's main player interface got a pretty big makeover recently, but chances are, the new UI hasn't made it your way just yet. Google has a habit of slowly testing the waters as they roll out new features, so cool tweaks like this can take some time to reach all users.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Welcome back, my tenderfoot hackers! Now that we have begun this trip down web app hacking lane, we need to first address target reconnaissance. Like any hack, reconnaissance is critical. (Are you tired of me saying that yet?)

Ironing is a serious chore: hot, unpleasant, and frustrating all in one, but necessary if you don't want to look like you crawled out of bed just before work. While you might only turn to your flatiron when faced with wrinkled clothing, this little appliance packs the power to tackle even greater challenges—and here are our 10 favorites.

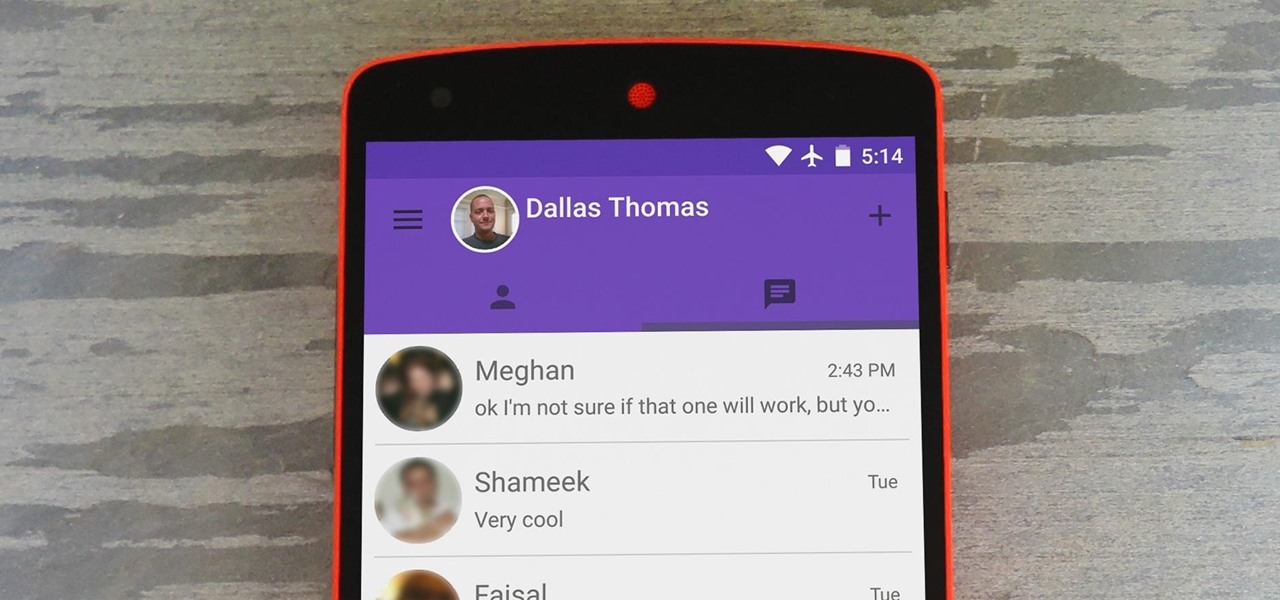
Hangouts is a great cross-platform messaging service from Google that works with almost any device, making it one of the few messengers that can be installed on Mac, Windows, iOS, and Android gadgets alike. With its many useful features, one of the few debatable downsides is its not-so-attractive color scheme.

Apple's Touch ID, introduced on the iPhone 5S, has definitely made my life a little easier. Not only can I unlock my device, I can use the tech to log in to websites, make purchases through iTunes, and buy groceries at Walgreens using just my fingerprint. Still, as awesome as Touch ID is, it's pretty limited as to what it can do on native apps.

Job interview success can be a difficult thing to measure. Is confidence a job-winning trait? Or were the interviewer's questions not answered as fully as they had hoped? Maybe you weren't sure how your big, happy smile went over with such a formal setting.

Welcome back, my novice hackers! As we saw in my first tutorial on Facebook hacking, it is not a simple task. However, with the right skills and tools, as well as persistence and ingenuity, nothing is beyond our capabilities.

Google's Chrome Web Store is packed to the brim with extensions that do everything from letting you customize Facebook to improving your Google+ experience. While there are thousands of extensions for basically anything you can think of, the problem is sifting through them all.

Welcome back, my budding hackers! This is the initial post of a new series on how to hack Facebook. It's important to note here that each hack I'll be covering is very specific. I have said it before, but I feel I need to repeat it again: there is NO SILVER BULLET that works under all circumstances. Obviously, the good folks at Facebook have taken precautions to make certain that their app is not hacked, but if we are creative, persistent, and ingenious, we can still get in.

There's nothing more jarring than the sound of your morning alarm. Even hearing it on others' phones, hours after your own abrupt wakeup, can cause you to flinch in fear. Though we depend on that shrill sound to get up each morning, it's actually better to wake up naturally—so don't even think about hitting that snooze button.

Welcome back, my hacker novitiates! Eluding and evading antivirus software and intrusion detection systems is one of the most critical tasks of the hacker. As soon as a new exploit is developed and discovered, the AV and IDS developers build a signature for the attack, which is then likely to be detected and prevented.

Christmas trees, once decorated and brightly lit, are the penultimate holiday decoration, but authentic pines lose their brilliance fast without any nourishment. Plus, they are major fire hazards without regular hydration. But watering one requires a lot of sliding around on the floor, and it can be hard to tell how much water is in the bowl beneath the dark, prickly branches. These five hacks can help!

Our workdays are typically filled with one thought: get as much completed as possible. Whether you face an inbox filled with tasks or just a project or two, both our bosses and our inner workhorses encourage us to knock out as many tasks as we can each day. But is being super-productive the best course of action for our minds and our employers?

Spills happen in the kitchen, and while every good cook knows to clean as you go, not every cook has an endless supply of cleaning materials. Besides, one spill can exhaust your entire stockpile of sponges, paper towels, and rags in a matter of minutes. Particularly egregious mishaps can make everything they touch feel sticky and gross.

I love pomegranates. I don't even mind the mind-numbing task of picking out the arils (which is what those ruby-colored seed-like things in the pomegranate are called). However, I'm always on the lookout for new, easy ways to peel it that don't make my kitchen look like a crime scene.

Investing is like exercise—we all know we should be doing more of it, but we often just can't find the time. I mean, really, who's got the hours, inclination, and skill to pour through volumes of data and put together a balanced yet sophisticated portfolio of investment vehicles tailored specifically to optimize their returns while mitigating potential risks. Not me, that's for sure.

iCloud Drive is Apple's new solution to file management syncing across iOS and Mac OS X. If you've upgraded to iOS 8 and you have an iCloud account, you can use iCloud Drive to store files for certain apps. While you won't really be able to benefit with file syncing between iOS and Mac apps until you get Yosemite, you can still access your iCloud Drive documents online.

At a closed-door presentation on September 30th, 2014, Microsoft unveiled the latest iteration of its industry-leading operating system. Dubbed Windows 10 (seems as if Redmond isn't too fond of the "9" moniker), this new version brings along with it many UI optimizations and under-the-hood tweaks. With a particular focus on optimizing the interface for traditional mouse and keyboard computers, one of the most noticeable changes is the return of the Start Menu. While touch-optimized devices wi...

Welcome back, my hacker novitiates! Every so often, a MAJOR vulnerability appears that makes millions of systems vulnerable to attack. The most recent, named Shellshock, basically leaves every Mac OS X, Linux, and UNIX system on the planet vulnerable. As nearly two-thirds of all web servers on planet Earth run one of these operating systems (primarily Linux), that's a whole lot of systems out there waiting to be harvested.

Welcome back, my novice hackers! Before we try to attack a website, it's worthwhile understanding the structure, directories, and files that the website uses. In this way, we can begin to map an attack strategy that will be most effective.

When it comes to give away or sell your iPhone, you can't just power it down, take out the SIM card, and hope everything will be okay. There's valuable data on your iPhone, and you need to get rid of it. Plus, if you don't perform all the necessary steps, chances are whoever ends up with the device won't even be able to use it. If you're selling it, that could ding your seller reputation.

If you've been testing out the Mac OS X Yosemite preview, you already know that Mac OS X 10.10 has a ton of cool under-the-hood tweaks and optimizations. One of the most noticeable changes for me has to be the new flatter look and "Dark Mode," which changes most UI elements from silver to black, making it easier to use your Mac in low-light conditions.