One of the big hurdles when equipping vehicles with sensors for autonomous driving is the cost. For example, the Light Detection and Ranging (LiDAR) sensors that power many versions of self-driving car technology are pricey, currently ranging from around several thousand dollars up to $85,000 per sensor—and vehicles often need multiple sensors to see enough of what is going on around them to drive safely.

To much of the United States, Zika seems like a tropical disease that causes horrible problems in other countries but is nothing to be worried about stateside. It may make you rethink your beach vacation abroad, but not much more than that. However, if you live in Florida or Texas, the possibility of getting a Zika infection where you live is real — and local outbreaks are more and more a possibility.

When a dead body is discovered, finding out when the person died is just as important as finding out how the person died. Determining the time of death has always involved lots of complicated scientific detective work and less-than-reliable methods. However, a study by Nathan H. Lents, a molecular biologist at the John Jay College of Criminal Justice in New York, is the first of its kind to show how microbes colonize a body's ears and nose after death.

In the first part of my containers series, we learned how to install Docker on our local machine, pull down "hello-world" and Ubuntu containers, SSH into containers, and install software when in a container. Now, we're going to work on building, customizing, and storing our refined hacking Ubuntu container. Before we dive right in, though, let's make sure we still have a functional Docker installation.

As a former repair tech, I've heard the same reasons over and over as to why people opt not to purchase phone insurance. Some cite the cost—why pay extra every month for insurance when you're careful with your phone? Deductibles are expensive, so why not just spend that money on a repair instead of getting a refurbished phone as a replacement?

Oh no... your precious iPhone is in shambles. Maybe you shattered your screen after a crazy night of celebrating, or maybe your two-year-old jabbed a toy into your iPhone's charging port, completely destroying it in the process. Now what? Do you take it to a repair shop, or go to an Apple Store to have it fixed? This brief article will help you weigh your options.

Whether you're riding the subway on your way home from work, or stuck in the backseat of the car on a long road trip, there are times when you need to entertain yourself without a mobile data connection. A good mobile game would pass the time perfectly, but not every game works without an internet connection.

Cleanliness is next to godliness. My interpretation of that age-old adage means that keeping your house clean is just as un-fun and boring as being a goody two shoes. That's why they call things like laundry and doing dishes "chores," I assume. Yuck.

As we reported first here on Gadget Hacks, the Google Pixel and Pixel XL have unlockable bootloaders, with the exception of models purchased from Verizon. This means that once the TWRP custom recovery is installed, you can flash ZIPs and even root your device in a few taps—as long as you unlock the bootloader beforehand.

Now that we've talked about encryption and managing your passwords, let's continue this series on getting your Mac ready for hacking by turning our attention to the terminal.

This is the very first article in my series on setting up a Mac for hacking. In this series, I will be operating under the assumption that you have a clean install of macOS (previously OS X). If you aren't starting with a clean installation, there may be a few differences, but nothing we can't help you out with.

Thanks to the Edge variants, Samsung's Galaxy S phones are just a few millimeters off in body size when compared to the Note series, and just 0.2 inches smaller when it comes to displays. Now that the two flagship models are almost identical in size—with matching curved displays—there's really only one thing that separates the Note7 from the Galaxy S7 Edge: The S Pen.

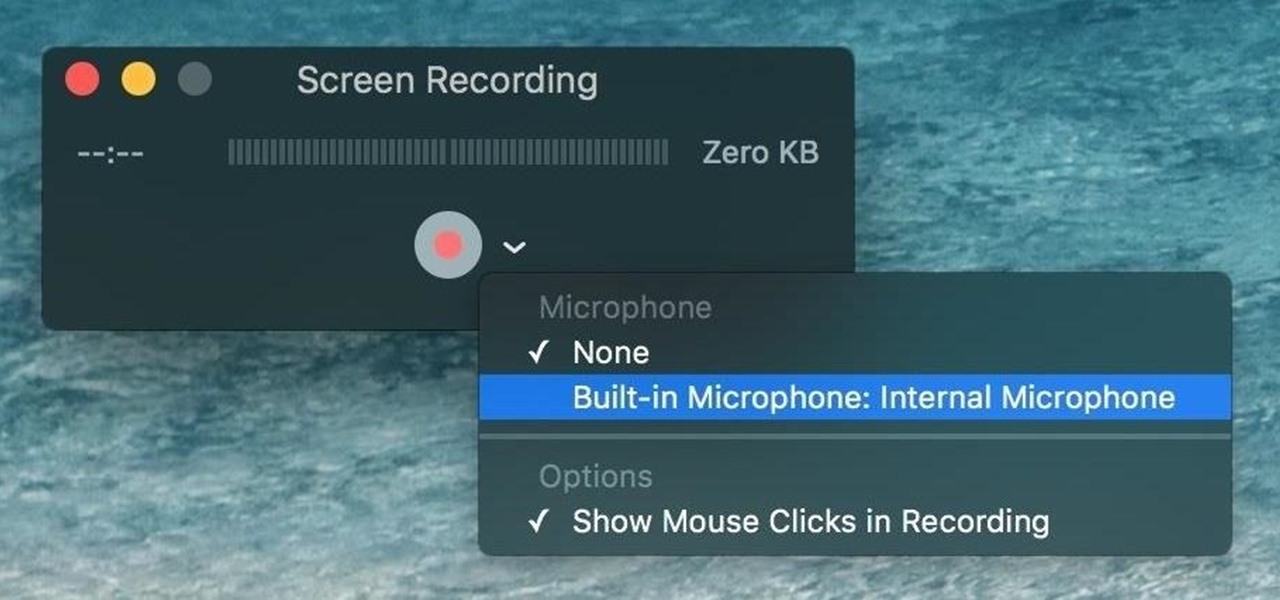
When a friend asks me what screen recording software is best to use, I always say the same thing—you don't need any! Even though it's been around since 2009, many Mac owners do not realize that they have a powerful screen recording software built right into OS X.

Fresh herbs are a surefire way to enhance a dish, but buying them at the store each time you need them is costly. Luckily, growing your own herbs is a lot easier than it seems: You can even using cuttings from the herbs you already buy to start your own little herb garden.

Welcome back everyone. I apologize for the lack of training articles, but I've been rater busy lately. I've recently picked up a second job and my college courses are now back in session, so I'm a bit strapped for time.

Make delicious candy for Easter from the comfort of your kitchen with copycat versions of your favorite classics: Marshmallow Peeps, Cadbury Creme Eggs, Reese's Peanut Butter eggs, Almond Joy bars, and chocolate bunnies. The best part is that you get your sugar fix without the preservatives.

When a headache strikes, I reach for the nearest painkiller. Forget closing my eyes, laying down, or even applying an ice pack—I seek the quickest and most immediate relief possible, and normally that comes in the form of pills. However, fast relief can be found from another, more natural source: herbal beverages. So if you're tired of popping pills when you have aches and pains, try some of these herbal drinks out instead.

In my last tutorial, I talked about creating a virus inside of a Word Document in the scenario of a mass-mailer attack. In this post, however, I'm going to be covering creating a fake image or screenshot with a meterpreter backdoor hidden inside to be used in a similar scenario. Step 1: Creating the Virus

Up until the last 15 years or so, watching the commercials during the Super Bowl was arguably more exciting than the game itself. Super Bowl XXIV featured the San Francisco 49ers blowing out the Broncos, 55-10, in the worst Super Bowl beatdown of all time. The game might not have been that exciting, but the commercials sure were.

Welcome to a tutorial on crypting technology. In this article, we will be discussing types of crypters, how they work and why they work. After defining these, we will then make our own basic crypter using the function I gave to you as a task to complete by yourself in the previous tutorial.

We here at Food Hacks are all about saving you, our wonderful readers, time and trouble in the kitchen. So when I saw that Barilla had come out with their Pronto line of "One Pan, No Boil, No Drain" pasta, I had to give it a try. While no-boil lasagna noodles have been around for a while and allow the pasta to essentially cook en casserole, this relatively new addition to the pasta scene includes elbow, penne, spaghetti, and rotini varieties that allow for usage in a greater variety of pasta ...

hello hackers,newbies and followers of this great community, after some research here in our community, I noticed that there is not even one tutorial that teach Web Development. We have a lot of tutorials on how to hack web site but many do not know exactly how a web site is composed, then I decided, meeting the community's needs, begin to teach people how to develop web sites.

Dinner is meant to be enjoyed after a long day away from home—it shouldn't cause stress or fuss. But for many, that's exactly what a home-cooked meal represents, especially on a work night. The prep work, the steps involved in following the recipe, the numerous amount of bowls, pots, and pans you use, and... worst of all, a sink full of dishes to clean.

Welcome back, my greenhorn hackers! As expected with Null Byte's dramatic growth over the last year, we have added many new aspiring hackers who are still lacking in the basics of networking. In addition, with the new "White Hat" certifications coming out shortly, the exam will require some basic networking skills and knowledge to pass.

The first written account of "stock" as a culinary staple goes back to 1653, when La Varenne's Cookery described boiling mushroom stems and table scraps with other ingredients (such as herbs and basic vegetables) in water to use for sauces. But really, the concept of stock has probably been around for as long as people have been using water to boil food.

Welcome back, my budding hackers! In this series, we are trying to understand how AV software works so that we can learn to evade it. To that end, we are working with the open-source AV software, ClamAV. I had previously introduced ClamAV in Part 2 of this series. If you have not installed it yet, go back to that and install it.

When there's a crappy stock app you want to hide, the easiest thing to do is just bury it in the back of a miscellaneous folder. But what if there's an app you want to hide on your home screen that you actually use? For instance, what if you don't want everybody in eyeshot to see what banks you use, or don't want anyone to know about your "dating" apps or porn shortcuts?

With T-Day on the horizon and approaching rapidly, you are probably in one of two camps. The one that is eagerly awaiting the holiday feast with barely-contained drool. Or the one that involves breathing heavily into a paper bag while worrying about your lack of oven and stovetop real estate, while also bemoaning the lack of multiples of you to get all the prep work done.

Yes, screen savers are fun to look at for a few seconds, but those animations actually used to serve a purpose beyond simple entertainment.

So this is my methodology for this project of writing a rootkit. Please leave feedback on what is right/wrong. I tried to simplify concepts the best I could however...

If you use Google Chrome as your default desktop/laptop browser, then Chrome OS will be pretty easy to get up and running if transitioning from Windows or macOS. Google has created an operating system that is fast, lightweight, and versatile enough to be adopted by pros and novices alike.

Like the majestic mountain structure it's named after, Apple's latest version of OS X, El Capitan, goes a little deeper to expand on the foundation laid by Yosemite. While the update may not be as monumental as some have hoped, it is an improvement and includes tons of useful new features you don't want to miss.

Hello all! In this tutorial, I'd like to show you one way of getting root on OS X. Check out this GitHub page for a recent privilege escalation exploit that was recently discovered. I've tested it and it works on both OS X 10.9 Mavericks and OS X 10.10 Yosemite, but appears to have been patched with OS X 10.11 El Capitan. If you check out the file main.m you can see where most of the magic is happening. This source code can very easily be changed to make it do more than just the system("/bin/...

Windows 10 is officially here, and frankly, there's a ton of new features in Microsoft's latest operating system. From the return of the Start menu to the new Edge browser, Windows 10 can take some getting used to.

In most cases, when the free trial of software is over, that's it—you're left to either pay for it or find an alternative. But what happens if the trial wasn't long enough to sell you on the product? It'd be nice if there was a way to test it out again without having to whip out your credit card.

A vending machine is an invaluable yet totally frustrating piece of equipment. It's a godsend whenever your tummy's growling or you need an ice-cold drink on a hot summer day. But when something gets stuck inside or the machine flat-out malfunctions, it quickly becomes your archenemy. And when you're broke, it's basically just one big tease.

When it comes to security, there are usually only a handful of things that you want protected from prying eyes on your iPhone—private photos, scandalous videos, and important text, such as credit card and social security numbers.

Welcome back, my greenhorn hackers! One of the most important issues any hacker must address is how to get past security devices and remain undetected. These can include antivirus software, intrusion detection systems, firewalls, web application firewalls, and numerous others. As nearly all of these devices employ a signature-based detection scheme where they maintain a database of known exploits and payload signatures, the key is to either:

I've been a diehard Chrome user since its inception, and even more so since Android was released. The ability to sync bookmarks, passwords, and web history across all of my devices made the switch a no-brainer, but what really made me fall in love was the amount of extensions available for it.

Summer's coming, and that means burger season. Okay, never mind... every season is burger season. Burgers are universally loved; they're the one meal you can find at numerous fast food shacks and haute cuisine spots.