The 68th Annual Golden Globe Awards take place this Sunday, January 16th, 2011 between the hours of 5 and 8 PM PST — that's 8 & 11 PM for those of you on the East Coast (and Somewhere in the Middle for those of you Somewhere in the Middle).

Parental involvement is a crucial ingredient in the success of many children. Teachers know the saying all too well that it takes more than a village to raise a child, for one - it takes parental involvement. Thus, it is important for teachers to reach out to parents in that first week of school. Teachers should write a formal letter that is welcoming and easily comprehensible to the parent and the student. This letter should be able to communicate that the teacher values the child’s educatio...

There is no fan experience in professional sports quite like watching an NBA game live. Partly, this can be attributed to the combination of fluid teamwork and jaw-dropping athleticism the players exude in the form of size, speed, jumping ability, grace, and strength. What truly differentiates the NBA from the spectators' perspective, though, is the figurative nakedness of the players. While the NFL buries its athletes beneath pads and masks, the NBA presents its talent in shorts and a tank top.

Since its launch in 2001, Wikipedia has become the number one reference site on the web, used by anyone and everyone, written by anyone and everyone. With over 18 million collaboratively written articles, there's backgrounds and descriptions on practically everything—if it exists, there's probably a Wikipedia page for it.

Remember KODACHROME? That color reversal film from Kodak? The film that was the inspiration for Paul Simon? The only brand of film to have a state park named after it?

According to Amazon.com, Kindle was their best-selling item this year, which means many, if not all of you are playing with a brand new Kindle on Christmas Day. Of all of Amazon's Kindle models, the Kindle 3 (6") will be the most common eReader in everyone's hands, either the Wi-Fi version or the 3G model.

Zynga games has released their ZLotto feature that you can use to get exclusive prizes for FarmVille, Mafia Wars, YoVille, PetVille, and FrontierVille!

Socket programming in Unix allows multiple computer programs to "talk" to each other in the form of open "pipes". This is used in many popular programs for the Linux system (see any distribution). This how-to is created to understand the simple creation of a socket and what the various parts of the call mean.

Eager to share your favorite pieces of literature, but can't find any electronic version of the book? Don't worry! You can create your own e-book library. All you need is a digital camera and some free software.

Health, safety and security are three main issues which determine if your cruise is a successful vacation.

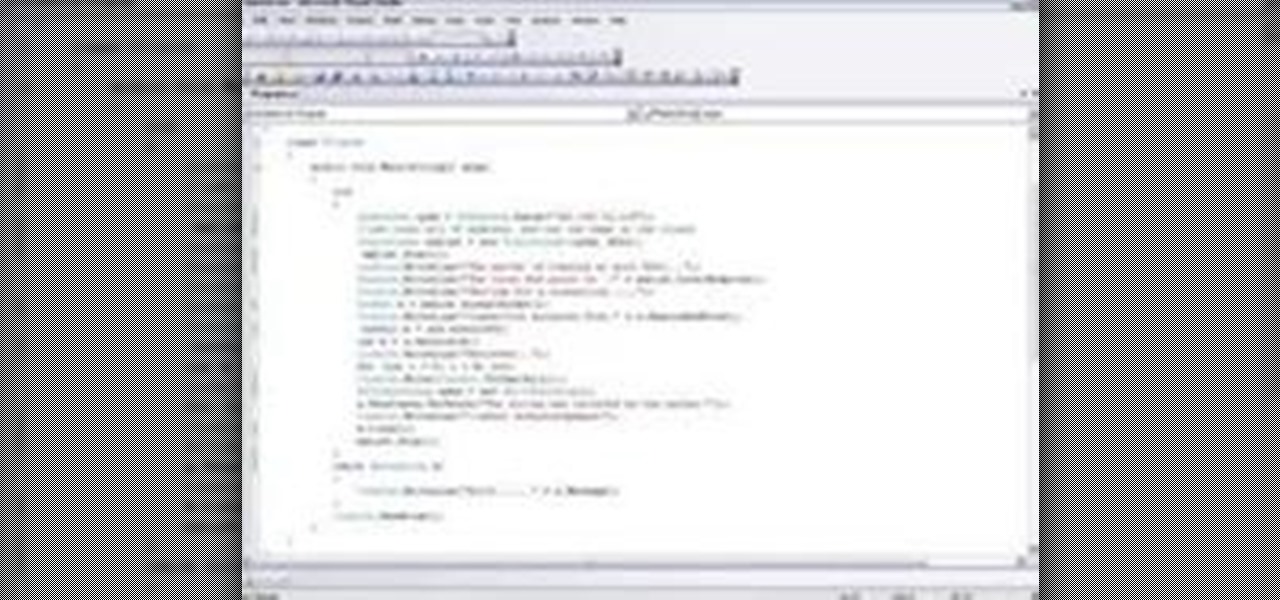
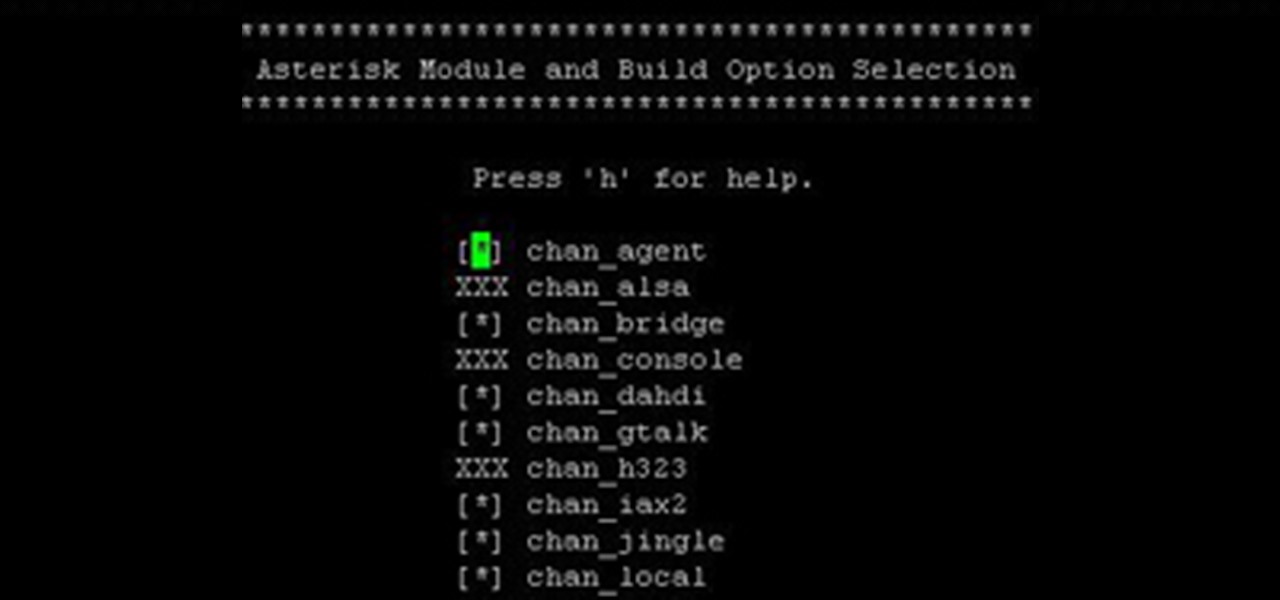
Over the years, I have enjoyed playing with Asterisk. I have found Asterisk to be extremely powerful and fun to play with. There are several books and many scattered how to articles out there, but most are outdated and the information required to build Asterisk from beginning to end can be a bit daunting. I wanted to combine all the steps into a single article and share my experience with everyone. If I have left out any steps please let me know.

If you're a diehard Apple fan, chances are the new iPad 2 caught your eye, stole your heart and emptied your wallet. Who couldn't resist the sophisticated slim-body design or its fascinating new Smart Cover? Well—it seems nobody could. And if you were late to jump on the bandwagon, you're still probably cleaning that dust out of your mouth because it took off without you—leaving the latest and greatest Apple gadget out of your reach.

Back in the eighties, I used to hate television commercials, but I eventually got used to them. Had to, in order to enjoy my favorite shows. Then, the increasing number of billboard ads annoyed me in the nineties. They followed me everywhere I went—no escape—persuading me to buy the newest whatever. It seemed like Big Brotherism—like They Live. But, I got used to it. When I finally entered the digital age and became a web addict, I was peeved at the constant sight of online ads everywhere I v...

There's a whole lot of brouhaha going on right now about the hidden plug-ins being installed unknowingly in the Mozilla Firefox web browser, with companies like Apple, Microsoft and even Google being named top offenders.

Fire. It’s everywhere— always has been. From the Ordovician Period where the first fossil record of fire appears to the present day everyday uses of the Holocene. Today, we abundantly create flames (intentionally or unintentionally) in power plants, extractive metallurgy, incendiary bombs, combustion engines, controlled burns, wildfires, fireplaces, campfires, grills, candles, gas stoves and ovens, matches, cigarettes, and the list goes on... Yet with our societies' prodigal use of fire, t...

Since iOS 6, "Respond with Text" has allowed us to quickly respond to a call we can't (or don't want to) answer. But Apple only gives you three options to choose from, and if you don't have time to type out your own response, those three might not cut it. Luckily, you can customize these three replies to whatever you want.

Picture in Picture mode is one of Android's best multitasking tools. Ever since its introduction in Android 8.0 Oreo, you've been able to watch videos in a floating window while you use other apps. In Android 11, this feature is getting its first real upgrade.

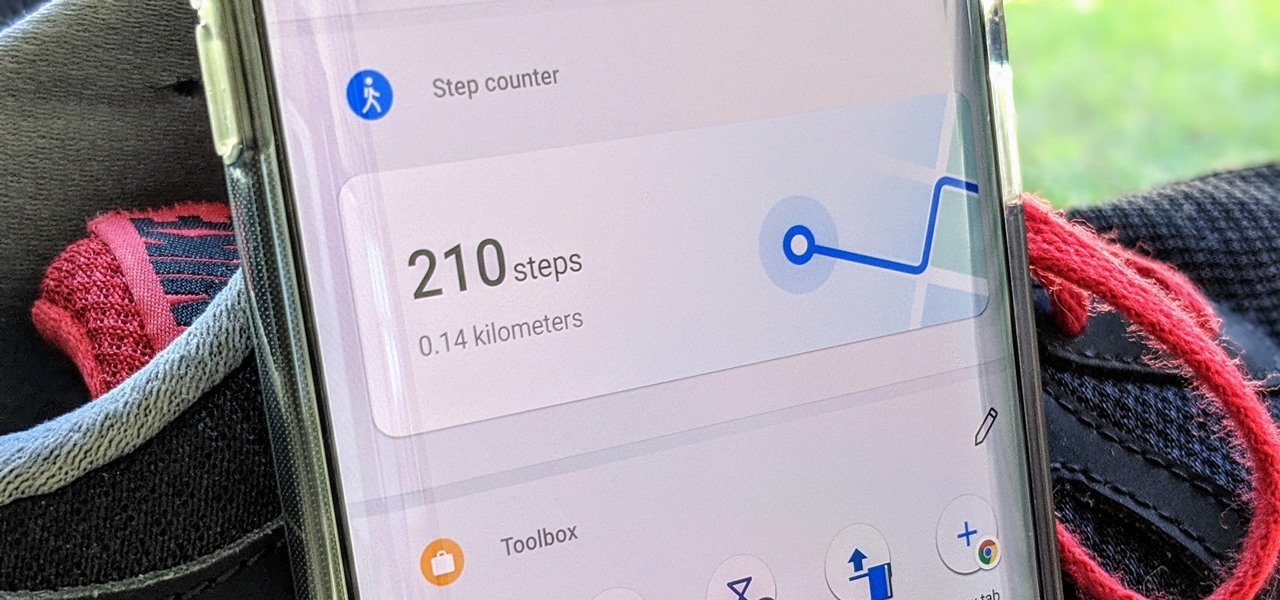
A great way to incorporate a healthy exercise routine is by taking lots of steps throughout the day. While most smartphones can track and report your steps via a third-party app, you can check them right from your home screen if you have a OnePlus phone.

A Self-Protection Guide 1) You can help protect yourself from violent crimes.

Microcontrollers are great. You can do anything from water your garden to catch wildlife trash diggers in the act—and on the cheap. I prefer to use the Arduino microcontroller because of the large and helpful community built around the website. Though it is my favorite, there are some drawbacks to using an Arduino board in every project. It gets expensive, the board can take up too much space, and the rat's nest of breadboard wires are a pain to repair.

The community here on Null Byte has always been great and helpful in sharing their know-how, even before I took up admin duties in this World. I jumped at the chance of leading Null Byte because I enjoy teaching and informing people on all of the important need-to-know things out there, but more so than that—there is a deeper reason.

In my Wireshark article, we talked a little bit about packet sniffing, but we focused more on the underlying protocols and models. Now, I'd like to dive right back into Wireshark and start stealing packets.

Welcome to Minecraft World! Check out our tutorials, post to the community corkboard, and come play on our free server!

This morning, I received a message from a friend who was reading a hack log, and she had some questions about the commands used. This got me thinking, as Linux has a ton of commands and some can be archaic, yet useful. We are going to go over everything you need to know to read a hack log and hopefully implant the steps in your head for future use.

ACTION MOVIES The Hunger Games (2012)

Industrial espionage, social engineering and no-tech hacking are all very real and there are simple precautions that you can take to protect yourself, which this article will discuss. Whether you are a high-profile businessman or a housewife (or husband), keeping information you want to keep private, private, should be important to you.

Oh yeah, this is a big topic, at-least for me. All the frequent flyers will/should be interested in this topic. I'm sure all of you have heard at-least something about the TSA, and most of it should have been bad. Complaints, lawsuits and general disgust surround this organization. Is there a reason, or are the 'extremist liberals' at it again? Let's find out!

In my recent Darknet series, I attempted to connect the dots on the Deep Web. I covered the two largest anonymity networks on the Internet today, Tor and I2P. While my initial four articles were meant as an introduction, I ended up receiving a lot of interesting comments and messages asking the technical differences between the two. I'd like to thank all of you for letting me know what was on your minds, as you should always!

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. This past weekend, our Weekly Workshop focused on building a suffocation trap. But today, we're going to be covering a different type of redstone trap in Minecraft—one with a 100% success rate (perfect for PvP servers).

This is the third part of my electromagnetic pulse series (see Part One and Part Two). By now, I've covered the hardware and general concept of electromagnetic pulse generators, but how exactly do they disable electronics? How can an invisible field of energy have such a catastrophic effect on computers, cell phones, and most any other electronics? I'll be answering all these questions in part three of Making Electromagnetic Weapons.

We're officially seeking Null Byters on a weekly basis who are willing to take the time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (IF up to par, of course). There is no need to be intimidated if you fear you lack the writing skills. I will edit your drafts if necessary and get them looking top-notch! You can write tutorials of any skill level, about anything you feel like sharing that is ...

For this particular example, I will be working on Wndows (sorry X users). I might write a similar guide once I am more comfortable with programming in Linux.

A degree in nursing from Kaplan University addresses the challenges and scenarios real nurses work through on a daily basis. Kaplan University’s Master of Science in Nursing (MSN program) is based on relevant material to help ensure our students are prepared for their careers. Our online nursing degrees are based on flexible coursework; students enrolled in the Kaplan University School of Nursing program are already nurses and there is no easier way to cater to the ever-changing schedule of a...

One of the primary goals of a social network is for you to share what you find interesting with your followers and friends, but on Google+, sharing has so many layers that it can be confusing for most people to really take advantage of it properly. Some of the tools in place that enable you do deal with spam and manage your privacy aren't very clear, so this week's round up is all about how you can share what you want with who you want on Google+.

At GDC 2011 this past March, three of the world's best game designers participated in a contest called Game Design Challenge. Each presented their vision for a game that fit the prompt "Bigger than Jesus: games as religion" before an audience, with applause to determine the winner. Jenova Chen, John Romero, and Jason Rohrer all spoke, and Rohrer won in a landslide with his revolutionary game called Chain World.

Are you finding that the Google+ features you've been waiting for are still not rolling out quickly enough for you? Although we've provided many solutions to Google+ issues with different Chrome extensions, it still seems like it's not enough. Now that we've been using Google+ for almost two months, our priorities have changed, and we're finding that we want and need different extensions to make Google+ work better. From filtering to circles, these Google+ Chrome extensions will solve many of...

If you follow indie games at all, you've probably heard of Bastion. During its development, it took home numerous Best in Show prizes from E3 and other game conventions while building up an incredible amount of buzz in the games press. Part of what is intriguing about Bastion is its cool art design, which in the last couple months, peaked my interest more so than the gameplay or the much-ballyhooed narration.
I've struggled for a long time trying to set up a virtual network between my KVM virtual machines. I tried several forums and tutorials on the web, but still on my system it just wouldn't work. I eventually got it owrking, so I've decided to make some notes of my own. Hopefully it will be helpful to you as a reader as well.