Seriously, what's with all of the candy corn hate? I don't care what anyone says, candy corn is and always has been the perfect Halloween snack for me. Only recently did I realize that not everyone gets as hype as I do about small, sugary vegetables.

One of the main reasons for installing a custom ROM on an Android device is all of the added features. For instance, OmniROM offers a souped-up multitasking mod called OmniSwitch, so instead of the regular app switcher, you get an interface that lets you pin your favorite apps, access settings, view memory usage, and more.
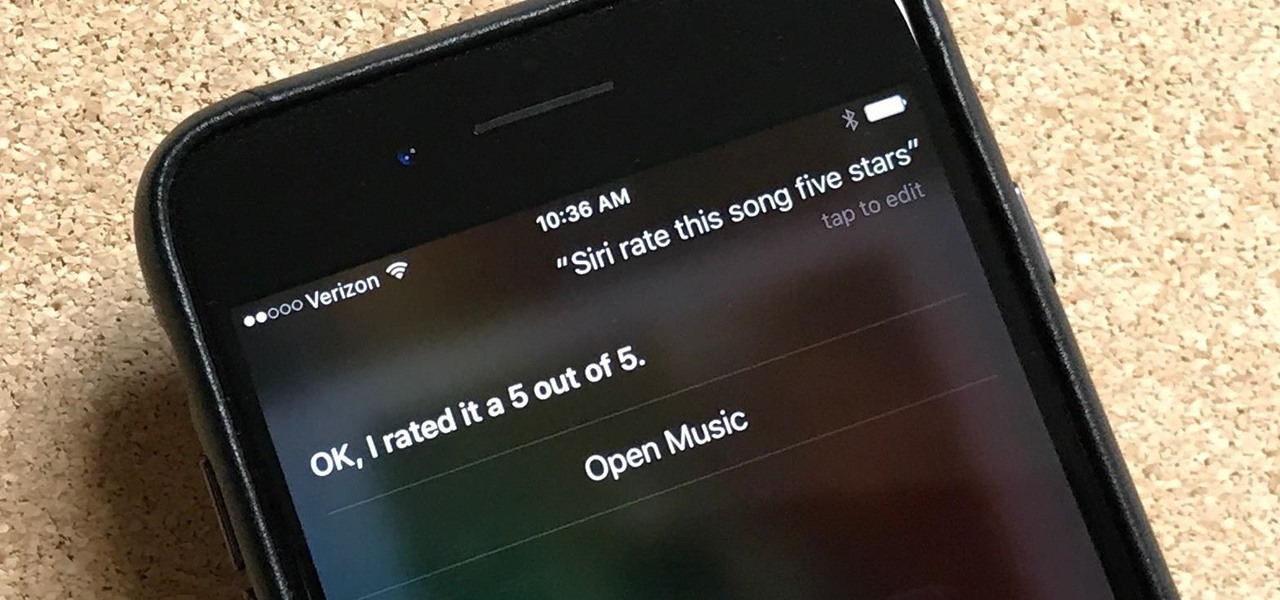
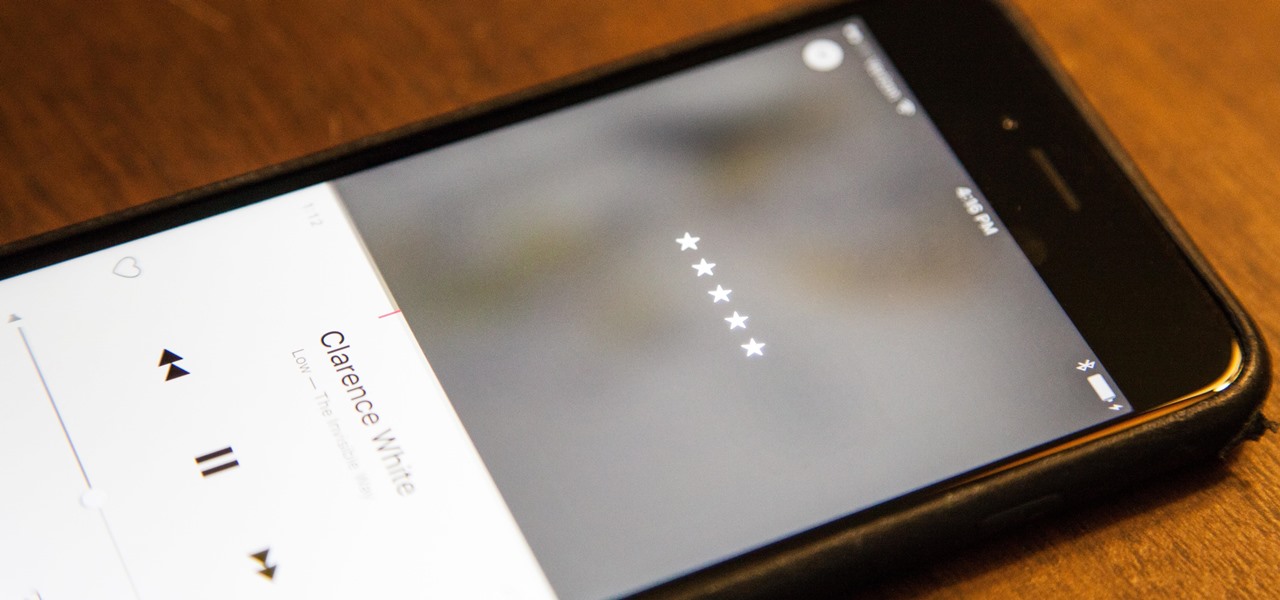
Can't figure out how to give songs star ratings anymore in your iPhone's Music app? That's because Apple removed the ability to do so from the new iOS 10 update, just as I expected they would. It's still possible to rate songs, it's just very irritating.

Traditional root ad-blockers like AdAway and AdBlock Plus have no effect on YouTube anymore. Until now, if you wanted to get rid of the commercials that play before your favorite videos, there have only been two ways—either by paying for a YouTube Red subscription, or by using an Xposed module to modify the YouTube app itself and force it into not showing ads.

Thanks to the Edge variants, Samsung's Galaxy S phones are just a few millimeters off in body size when compared to the Note series, and just 0.2 inches smaller when it comes to displays. Now that the two flagship models are almost identical in size—with matching curved displays—there's really only one thing that separates the Note7 from the Galaxy S7 Edge: The S Pen.

Okay, so that headline definitely got your attention, but what the hell do cats have to do with Android Nougat? Well, apparently, Google's on a far-out trip reminiscent of the post-India Beatles era, because this is actually a thing.

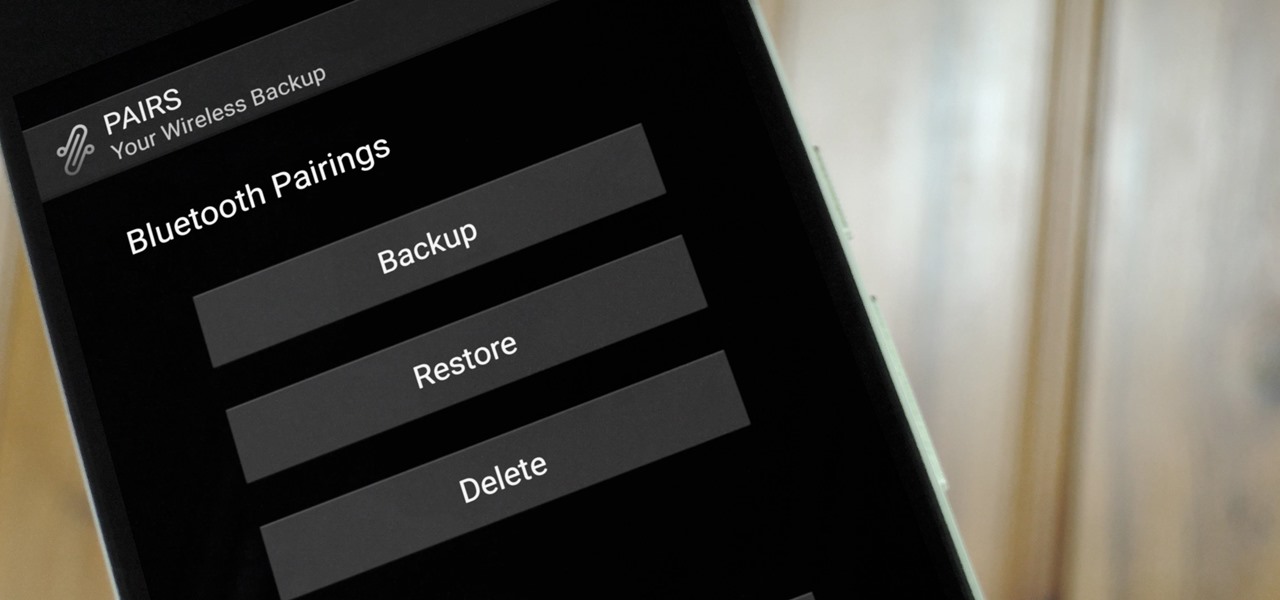
If you enjoy modding your Android device with root utilities, custom ROMs, and Xposed modules, then there's a good chance you've had to factory reset your phone when something went awry. Plus, when you're switching ROMs, it's always recommended that you wipe all data, so us modders spend a lot of time restoring and tweaking various settings.

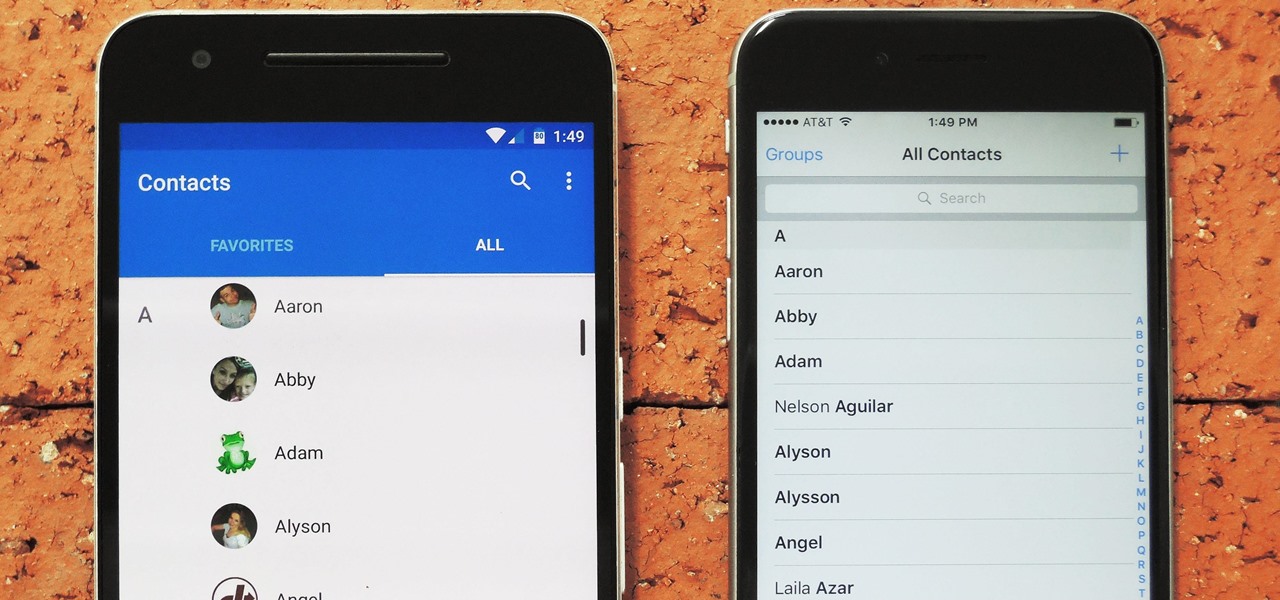
Switching between mobile operating systems is fairly easy, but there are a few bumps along the way that you're bound to encounter. One of the first issues you'll run into is that the contacts on your old iPhone don't easily sync with your new Android device.

We're year-round pesto eaters. We eat pesto outdoors in the summertime on a light pasta with a glass of rosé. We eat pesto in the wintertime by the fire atop a bowl of soup with a warm mug of tea. We eat pesto with scrambled eggs for breakfast, pesto-slathered sandwiches for lunch, and baked pesto chicken for dinner.

You may not know what HTTP is exactly, but you definitely know that every single website you visit starts with it. Without the Hypertext Transfer Protocol, there'd be no easy way to view all the text, media, and data that you're able to see online. However, all communication between your browser and a website are unencrypted, which means it can be eavesdropped on.

Several major web services—most notably Facebook—have horrendous Android apps that occupy way too much space and drain battery life at an alarming rate. Such issues have led to a new trend where third-party developers create minimalist "lite" apps that are essentially the mobile website bundled into a native Android wrapper, freeing up storage space and saving battery life without sacrificing many features at all.

When it comes to sharing files between a smartphone and a computer, there are several solutions available for a Windows and Android pairing. But for those of us with Apple devices, the selection of apps in this category isn't quite as great. You can use AirDrop to quickly share files, but searching for files is not so easy.

Back in iOS 8.4, Apple introduce a new "heart" icon in their Music app, which works in direct correlation with their Apple Music service that was released at the same time. By hearting a song, you're telling Apple that you love that song, and they can make better suggestions for you (in the "For You'" tab) based on it.

Even with today's high-powered devices, battery life is still an issue. We, as users, have to almost habitually check the current battery percentage, because otherwise, we might end up draining too much in the morning, then get stuck with a dead phone at night.

There are so many great apps in the Google Play Store that it's become the number one app marketplace in the world.

Why, for the love of God, do people keep inventing ridiculous devices that make the simplest things more complicated in the name of convenience? This may be a rhetorical question that will forever go unanswered—because these crazy gadgets just keep rolling out, one after the other.

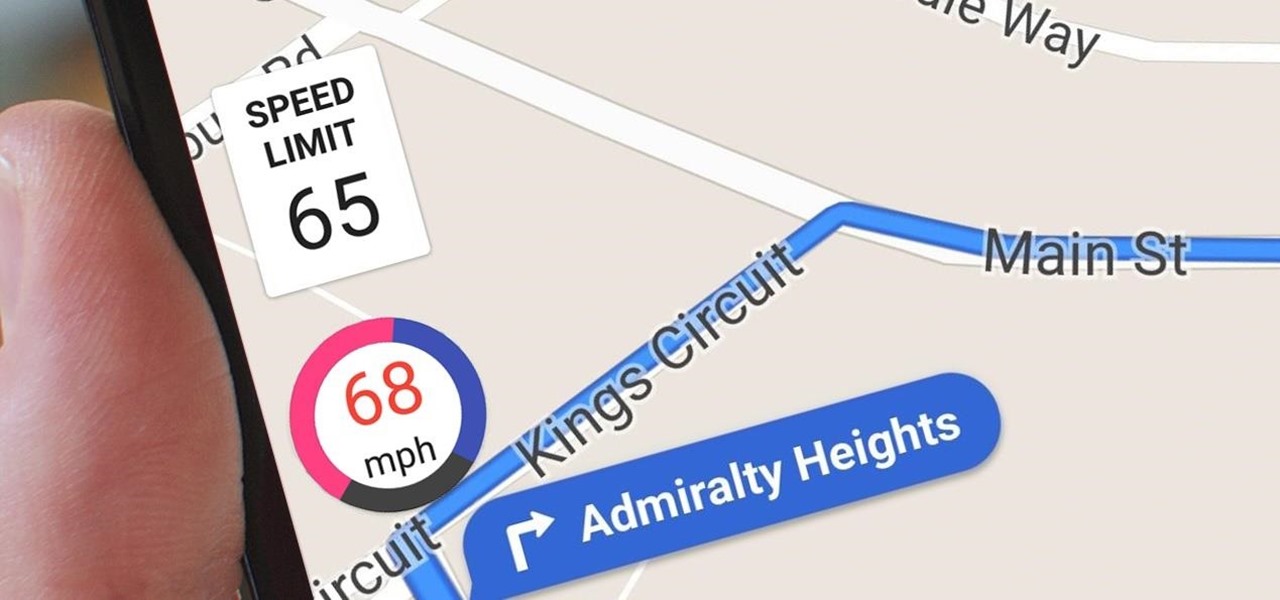
Google Maps does a lot of things well, but one feature it's always been lacking is an on-screen speedometer. Well, now you can add one with Velociraptor, and you can even set it to alert you when you're traveling above the speed limit.

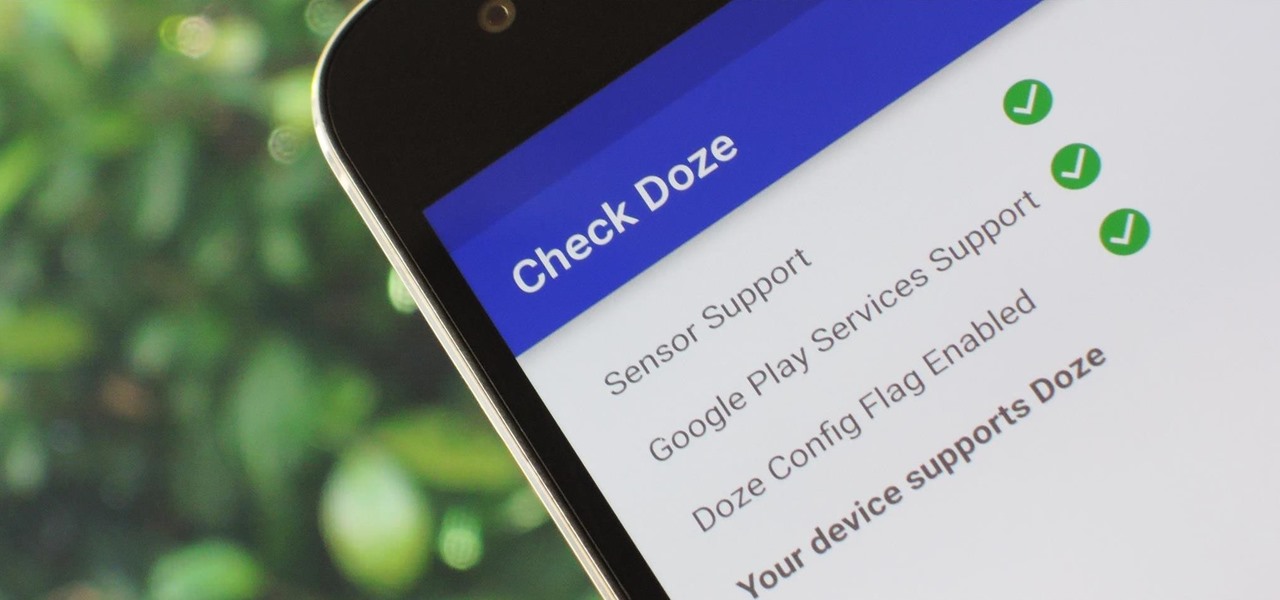
Out of all the new functionality introduced alongside Android 6.0 Marshmallow, a battery-saving feature called Doze Mode has been the biggest hit. Essentially, Doze waits until your device is laying flat and still, at which point it triggers an aggressive battery-saving mode that drastically increases standby time on your device.

Store-bought marinades and sauces have an ability to jazz up the simplest items. But after a while, those favorite tastes seem a bit repetitive and mundane, and that got us to experimenting with different add-ins to make our marinades stand out. Fruits, herbs, spices—all of the usual suspects were delicious, but not spectacular.

The potato masher is one of the most dreaded tools in my kitchen; it always gives me flashbacks to when I had to mash potatoes for Thanksgiving dinners while growing up.

You've probably noticed artichokes at the front and center of your local grocery store or farmer's market recently, as spring is artichoke season; They may look like strange, complicated vegetables if you've never cooked them before.

Let's set the scene: you're at home, it's late in the evening, and you have a hankering for those deliciously decadent chocolate-wrapped squares of ice cream goodness. You could drive to the store and pick up the usual pack of Klondike Bars in the ice cream aisle... or, you can easily make these babies in the comfort of your own home with only three ingredients for a fraction of the cost—in any flavor you want! The choice is obvious. So, without further ado... Ready, set, Klondike!

Last week, the U.S. Justice Department issued criminal indictments against seven Iranian hackers. These hackers, working for private companies in Iran, are accused of orchestrating DDoS attacks against U.S. financial institutions from 2011-2013 as well as intruding into the control panel of a small dam in Rye, New York. It is thought that these attacks were a response to the U.S. tightening financial restrictions on Iran during those years and the NSA-based Stuxnet attack on their uranium enr...

Although there has been much speculation about how much damage could be done if hackers were to take control of a country's SCADA systems, there have been few examples - until a few months ago, with the power outage in Ukraine caused by hackers.

We're so used to seeing things in particular ways that anything different just doesn't make sense to our brains. Culturally, we like to read things from left to right, and from top to bottom. Change that and our brains struggle to adjust.

Creamer, milk (whole or skim), sugar, or even butter—you've probably added at least one of these to your coffee to improve its taste at some point. If you're looking for something different, though, try a new twist with a dash of cinnamon. This sweet, sharp spice can do so much more than improve coffee's taste, and I've got 10 examples for you to consider.

Out of nowhere, Google released a preview build of the upcoming Android N release back in March—a full two months early. As if that weren't enough excitement for one day, they topped themselves by following up that announcement with the debut of a new "Android Beta" program that allows users with eligible devices receive preview builds as a regular OTA update, meaning no losing data or manual installation.

Although lots of the bigger hotel chains are lessening the restrictions they put on their room TVs, some smaller ones are still taking measures to prevent you from plugging in computers or streaming devices into an HDMI port. However, there are a few steps you can take to bypass these restrictions and watch your own media in a hotel that has restricted TVs.

In this series you will learn how to use PHP to perform attacks, gather information, and setup backdoors. Along with performing attacks you will learn how to protect yourself from them. In this part you will learn about PHP as well as install Apache and PHP. What you'll need for this series

Hello NullByte, it's mkilic! This time I'm here with the C.H.I.P from NTC. Although it is not too popular, the C.H.I.P is a brand new micro computer. It is very similar to the Raspberry Pi or Beaglebone Black. The key difference with this particular board is its cost and size. The C.H.I.P only costs $9 and measures 2.5 x 1.5 inches. In addition to this, the C.H.I.P has built in 802.11 b/g/n Wifi and Bluetooth 4.0. Considering these great specs, what could a Hacker use this for? Step 1: The In...

Cable TV providers were dealt a pretty significant blow on Thursday, February 18th, 2016, when the Federal Communications Commission decided that customers should have a choice in what type of device they use to watch cable, instead of being forced to rent a set-top box.

NMAP is an essential tool in any hacker's arsenal. Originally written by Gordon Lyon aka Fydor, it's used to locate hosts and services and create a map of the network. NMAP has always been an incredibly powerful tool, but with it's newest release, which dropped mid-November of last year, they've really out done themselves.

As many of you know, I have been running a couple of series here on Null Byte about digital forensics called Digital Forensics for the Aspiring Hacker and Digital Forensics Using Kali. Although many readers have seemed to enjoy these series, just as many seem to be pondering, "Why should I study digital forensics?"

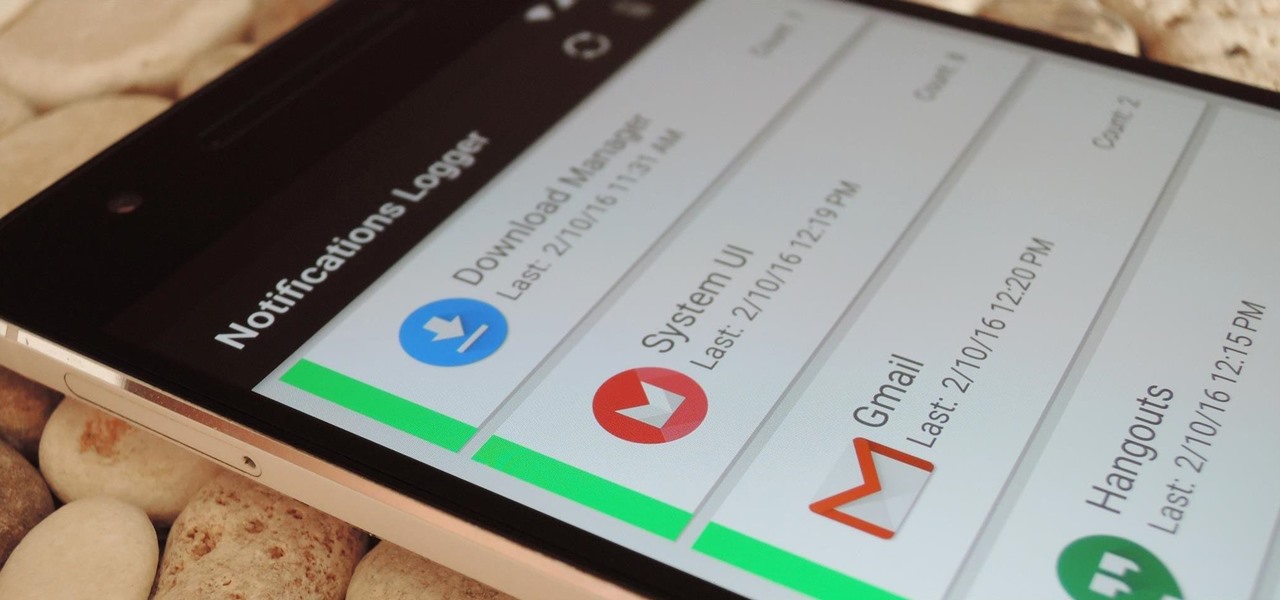
If you've ever prematurely dismissed all of your push notifications before you got a chance to read each one, you know how annoying it can be to dig through all of your apps to try and find the one with the missed notification.

Hello, everyone. Stealth is a large part of any successful hack; if we don't get noticed, we're much less likely to be caught. In these next few articles, we'll be building a shell based on keeping us hidden from a firewall. There are many ways to stay hidden from a firewall, but we'll only be incorporating a couple into our shell. This article will outline and explain these evasion concepts and techniques.

Whether you're anxious to tune into this Sunday's Super Bowl 50 to see Cam Newton and the Carolina Panthers take on Peyton Manning and the Denver Broncos, or to see if you win some money on your silly prop bet, or just want to tune in for the commercials, there are a handful of ways to catch the Big Game without an antenna or cable/satellite subscription. When & Where

Hello again, readers! In our previous crypter tutorial, we looked at how we could obfuscate our malware (or any program) by using a simple one-byte XOR key. In this quick tutorial, we will be looking at how a simple little tweak can create a better means of obfuscation. Let's get right into it!

Unless you're in law enforcement, you won't usually have a flashlight on hand for those rare moments when you need to sift through the dark. However, it is very likely that you will have your phone on you, so you'll have fast access to a bright light with just a few easy taps.

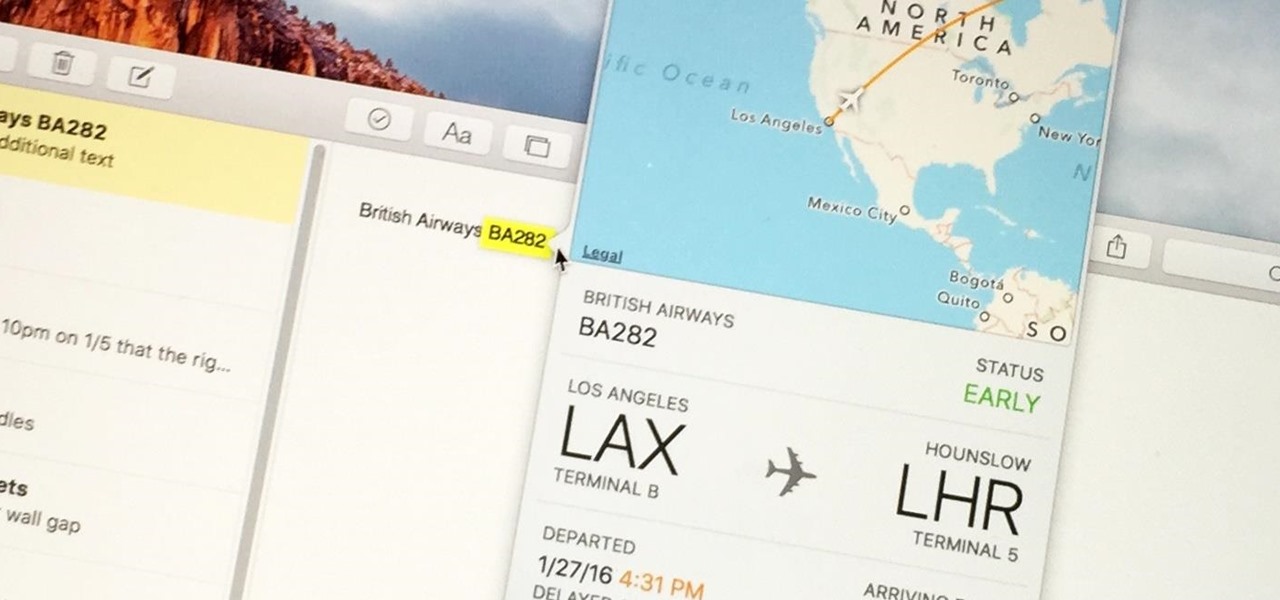
Turns out, you no longer need third-party flight tracking apps to get information on yours or others' flights—your iPhone and Mac can now give you flight details right from your Mail, Notes, and Messages apps.