New updates are always exciting, even more so when Google's behind the wheel. Yes, Android 10 "Q" is here, at least in beta form, ready for software testers to dive in and explore all the new changes. Among those changes, however, lie some issues. We won't sugarcoat it — there are some annoying things baked into Android 10.

With the growing list of products Apple offers, the number of devices connected to your Apple ID can get quite extensive. Having all those devices connected to your Apple ID helps you keep track of them, but when it comes time to part ways with an Apple TV or Apple Watch, those devices can still be attached to your Apple ID. In some cases, this could affect the overall security of your account.

The augmented reality industry had enough twists this week to surprise even M. Night Shyamalan.

While iPhones may be more expensive than ever, it won't stop us from losing them or having them stolen. Whether you have an iPhone 5S or an iPhone XS Max, there's a good chance it'll go missing at some time during your ownership. It could end up in a couch cushion or in the hands of a pickpocket, but no matter what happens to it, you need to prepare it beforehand for the inevitable.
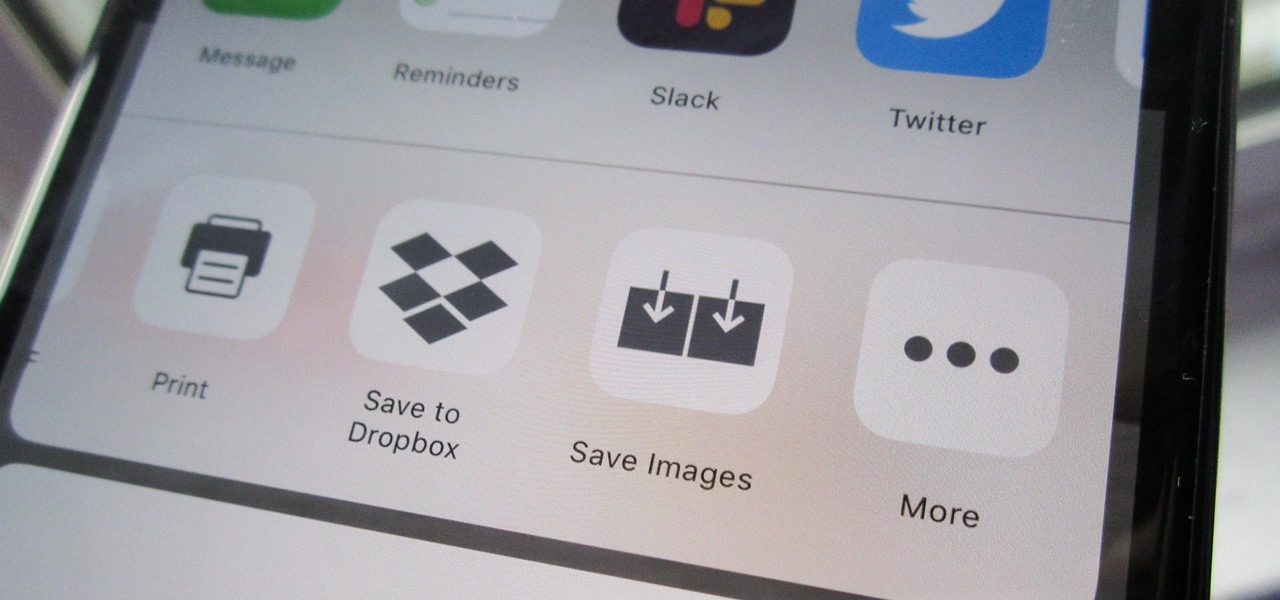
Some websites block image downloads on their webpages so you can't save them for reuse. That means long-pressing or force-pressing on protected images in Safari on your iPhone will not do anything or will omit the "Save Image" option. Taking a screenshot is the obvious solution to bypass restrictions, but you won't get the best quality. Thankfully, there's another way.

The latest film addition in the American-produced Millennium series, The Girl in the Spider's Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous English and Swedish language movies centered around hacker Lisbeth Salander. Of course, with the quick pace of some scenes, the hacks can be hard to follow.

Smart home speakers, such as Google Home and Apple HomePod, are must-have accessories if you're trying to turn your home into a smart home. While HomePod is made to be used with the Apple ecosystem, the less-expensive Google Home can also be used with your iPhone — in more ways than you'd think.

Stories are everywhere in social media today, but that wasn't always the case. In 2013, Snapchat introduced the world to these temporary windows into our daily lives. Since then, stories have infiltrated other popular apps. However, to stand out, you can't solely rely on the app where the story will be posted. Instead, you need a suite of apps that can turn your story into something special.

Augmented reality startup Nreal was a hit at this month's CES event, with some even calling the device a worthy challenger to the Magic Leap One.

When Google finally gave us a dark theme for YouTube, it was a bit disappointing. They didn't use a pure black background, reducing some of the battery savings you'd get with an OLED panel. But with the help of another app, we can fix this, and not only get a real dark mode, but other colors as well.

The saga of augmented reality startup Meta appeared to be at end, but there are new developments unfolding in real time that may either sink Meta deeper into trouble, or provide a tenuous lifeline for the beleaguered augmented reality company.

All of the the tech industry giants, including Apple, Facebook, and Google, are working on new smartglasses and/or AR headsets, but this week, Google took a major step forward with gesture recognition technology that could make its way into AR wearables, posing a threat to Leap Motion and its hand-tracking controllers.

Anyone remember Google Goggles? Well, it's back with a new name: Google Lens. But this time, there's more machine learning and it's integrated into many different Google apps and services. The latest is the Google app for iPhones.

Safari has a convenient "Find" feature to search for specific words and phrases in a webpage, and Apple Books has a similar feature for e-books and PDFs. But those do nothing for you when searching text in the real world. Hardcover and paperback books are still very much a thing, as well as paper-based documents, and finding what you need is as simple as pointing your iPhone's camera at the page.

Before you can dive into customizing your OnePlus 6T, you must take the initial step of unlocking the bootloader to gain the ability to install TWRP, Magisk, custom ROMs, and other mods.

If you store important, sensitive information on your iPhone in Notes, you'll want to be more careful. When Notes syncs across your iPad and Mac via iCloud — devices that family members or coworkers may share — you run the risk of having your notes read, edited, and deleted by other people. Such a catastrophe is easily avoided.

The ability to execute system commands via a vulnerable web application makes command injection a fruitful attack vector for any hacker. But while this type of vulnerability is highly prized, it can often take quite a bit of time to probe through an entire application to find these flaws. Luckily, there is a useful tool called Commix that can automate this process for us.

When OnePlus announced their partnership with T-Mobile and the deal the magenta carrier is set to offer, mouths dropped. But as usual, this deal comes with some caveats. The bulk of these will hurt the folks who love to root, something a large portion of the OnePlus community enjoys doing.

Augmented reality is becoming a slam dunk for sports entertainment, as leagues, their teams, and their broadcast partners have been quick to adopt AR.

Because timing is everything, the latest entry in the location-based augmented reality gaming sweepstakes, Ghostbusters World, has arrived just in time for Halloween.

There's more to recording calls than just protecting yourself against liability or an angry ex — oftentimes, this feature is the perfect tool to save momentous calls like breaking news of your recent engagement to loved ones. And with the prevalence of video calls, you can even capture memorable video chats such as your mom's first glimpse of your newborn on your mobile, courtesy of Skype.

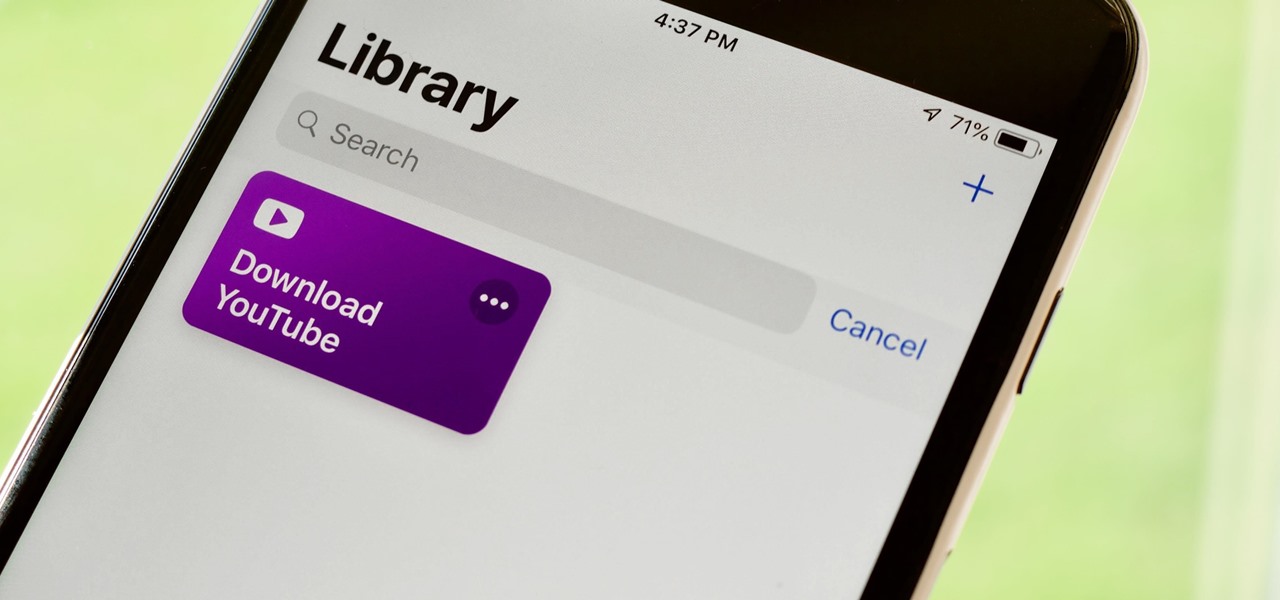
If you've ever wanted to download YouTube videos directly to your iPhone, there's an easy solution — just update to iOS 12 and install Apple's new Shortcuts app. With the Workflow-replacement app, you can add a shortcut that lets you download any YouTube video you want, without needing to jailbreak or use shady third-party tools.

The road to becoming a skilled white hat is paved with many milestones, one of those being learning how to perform a simple Nmap scan. A little further down that road lies more advanced scanning, along with utilizing a powerful feature of Nmap called the Nmap Scripting Engine. Even further down the road is learning how to modify and write scripts for NSE, which is what we'll be doing today.

Apple's successor to the iPhone X is a beautifully made smartphone with much of the same characteristics, including a 5.8-inch OLED screen, two storage choices, and Face ID. But many features set the iPhone XS apart from its predecessor, as well as the other 2018 lineup of iPhones, making it a worthy choice to upgrade to if you're in the market for a new mobile device.

This week, Next Reality published its annual feature on the leaders in the augmented reality industry, the Next Reality 30. So it's no coincidence that the companies represented in the top four spots of the NR30 also made business headlines in AR this week.

In iOS, the Control Center is an easy way to toggle settings such as Wi-Fi, Do Not Disturb, and Low Power Mode. Its Android counterpart is called "Quick Settings," which provides much of the same functionality with a few bonuses. If you're curious about how this toggle menu works or miss having it before you made the switch from Android, you can test it out on your iPhone right now.

With iOS 12, iCloud Keychain has become a more useful password manager for your iPhone with strong password suggestions, password reuse auditing, and Siri support. However, before you jump ship from your current password manager, you should consider all the reasons why iCloud Keychain doesn't make sense as your primary password manager.

From its introduction and all the way through iOS 11, FaceTime has been restricted to one-on-one calls. Apple will be changing that in a future iOS 12 update with Group FaceTime, which adds support for up to 32 people total in group audio and video calls. But that's not all we'll be getting in iOS 12 — there are more features that FaceTime has or will be getting soon that you should know about.

If you didn't get the memo, passwords aren't enough protection for your online accounts. Even a long and complex password offers only one line of defense which can falter. Two-factor authentication adds an additional layer, bolsters your defense, and decreases the risk of your account becoming compromised.

The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other devices on the network. All of this can be done without installing additional software or modifying any files.

For the augmented reality hardware industry to progress towards the consumer segment, display technology needs to get better. Investors recognize that, and they are showing AR display makers the money.

If you want the best two-factor authentication app out there, our pick is Authy. A close second is LastPass Authenticator. If neither of those is to your liking, try Duo Mobile or Microsoft Authenticator. But if you're fine with missing out on great features, then and only then should you look at using Google Authenticator.

While Magic Leap has gained attention for its ability to raise capital, the company (now with an actual product on the market) still faces an uphill climb against the titans of the industry.

In most macOS hacks, a non-root terminal is used to create a backdoor into the device. A lot of damage can be done as a low-privileged user, but it has its limitations. Think twice before granting a file permission to execute — an attacker might be able to convert your harmless scripts into persistent root backdoors.

There are dozens of apps like Glympse, Family Locator, and Find My Kids that let parents see where their children's phones are, but they all have one fatal flaw: It's incredibly easy to spoof locations to make it look like the phone is somewhere else.

One of the most critical bugs to come out in the last five years was Shellshock, a vulnerability which allows attackers to execute arbitrary code via the Unix Bash shell remotely. This vulnerability has been around for a while now, but due to the ubiquity of Unix machines connected to the web, Shellshock is still a very real threat, especially for unpatched systems.

Each year, Apple seems to design its devices to be more difficult for owners to repair themselves. So when an iPhone breaks, a trip to the Genius Bar or an Apple Authorized Service Provider is most likely necessary. But if you have an iPhone X that needs a new battery, a leaked video just spilled the beans on how to replace the battery precisely as Apple would.

Most users don't realize how much valuable data is in their network traffic. With a few simple tools, an attacker can quickly pick out cookies, passwords, and DNS queries from a macOS device as it covertly streams the victim's network traffic to the attacker's system. Here, we will cover two methods for analyzing packets flowing from a Mac.

With the rise of website encryption (TLS), sniffing passwords from network activity has become difficult. However, it's still possible to quietly exfiltrate a target's network traffic in real time to extract passwords and sensitive information. Pertaining to macOS, there are two methods for retrieving traffic from a backdoored Mac.

Every once in a while, we find ourselves in a predicament where we need an inexpensive smartphone. Whether we're finally upgrading from that feature phone we held onto too long or we dropped our current smartphone, sometimes we need a quick replacement to get back on track. That's where Android One comes in.