Popping a shell is often the main goal of a hacker, and it can be exciting when executed properly, but sometimes they do have their limitations. Metasploit's Meterpreter probably needs no introduction, but this powerful, dynamic payload can offer a leg up over normal shells. To prove it, we'll show how to take a normal command shell and elevate it to a Meterpreter session.

Last year, Razer kicked off a new trend by building a smartphone from the ground up with mobile gamers in mind. At the time, many thought the Razer Phone solved a problem that no one really had — but a year later, we're starting to see that gaming phones are perfect for more than just Fortnite players.

Samsung Experience isn't for everyone. While it's a far cry from the TouchWiz days, it is still too heavy of a skin for Android purists. But you shouldn't let that dissuade you from a powerful device that checks nearly all other boxes — there are ways to make the Galaxy Note 9's software look and feel almost exactly like stock.

Last year, OnePlus released not one but two excellent flagship devices with the OnePlus 5 and 5T. While the 5T released sooner than expected, it brought some worthwhile upgrades, such as a near bezel-less display and a much-needed camera enhancement. Now, that the OnePlus 6 has arrived, it's time to see what OnePlus has in store for 2018.

Mobile World Congress 2018 is here, and with it, Samsung has officially announced the highly anticipated Galaxy S9 and S9+. While we already knew much about the new phones, Samsung's presentation officially filled us in on what to expect from the S9's cameras, including dual aperture, two cameras, and super slo-mo.

For all those times when an app either isn't available or simply won't cut it, your phone's internet browser provides access to your favorite websites and services. But some browsers are flat-out better than others, and chances are, the browser that came pre-installed on your phone isn't the best option out there.

If you own a Pixel or Nexus device, Project Fi is a great alternative for cellular service outside of the four major US carriers. Project Fi is a Google-managed MVNO, providing service primarily through the T-Mobile and Sprint networks. One of the biggest mysteries on Fi is which network you're connected to at any given time, but there's a simple solution.

Windows 10 has proved to be immensely popular (free upgrades certainly don't hurt), and with back to school time, there's a good chance you have a new computer running Microsoft's latest OS. You maybe you decided to go with a clean installation rather than an upgrade, or just haven't used your computer for much more than surfing the web and watching Netflix.

Enough with zoodles (zucchini noodles), spaghetti squash, and carrot 'pasta' spirals. A well-prepared dish of zoodles with sauce is beautiful and tasty, but let's get real, it doesn't fill you up. If you use it as a meal replacement, then you'll be hungry about 30 minutes later.

Even if you've put aside your percolator and have gone the way of the pod coffeemaker, there are still dozens of ways to use your leftover coffee filters. Incredibly cheap, absorbent, and shaped with a ruffle, coffee filters are useful in the kitchen, garden, and around the house.

In this video, I'm going to show you how to make an effective DIY pop filter using nothing but a few sheets of paper and a tissue. This will give you an excellent quality recording with your microphone. In fact, the no-cost pop filter I'm about to show you how to make is the same one I used to record this video, so the results are right here for you to hear.

Any pizza lover knows that a quality crust is crucial to the whole experience. Good pizza crust should be delicious on its own, for once you get to the edge, it will be without any toppings, sauce, or cheese to disguise a bad character. It should be redolent of fresh, good wheat and taste full-bodied, rather than flat, flabby, or metallic, the way so many big chain and frozen pizza crusts do. The exterior should be crisp, while the interior contains an airy crumb as well as having a tender, s...

Video: . How to Dye Weave Extensions Easy!!

Welcome back, my budding hackers! I've written several listener guides on creating a malicious PDF or malicious Word document that would carry in it a payload with the Meterpreter, or reverse shell enabling you to own the system. One of the hurdles to using these techniques is the antivirus (AV) software on the target system. For instance, if you try to email a malicious PDF or Word doc, it's likely that the victim system will alert the victim that it contains a virus or other malware.

Welcome back, my fledgling hackers! The database is the hacker's "pot-of-gold," as it contains information that is very valuable to both the business and the hacker. In this, the second of my series on hacking databases, we're on the "hunt" for Microsoft's SQL Server. Although far from the most commonly used database (Oracle hold's that title), Microsoft's SQL Server is very often found in small-to-medium sized businesses. Even a few big businesses use it.

Fluorescein is a commonly used fluorescent dye that is quite hard to come by in a concentrated form. Fortunately, it's used in relatively large quantities in highlighter markers and can be extracted by a fairly simple process. Fluorescein makes spectacular explosions of color as it dissolves into water and can be used for many different purposes that are addressed in the video below.

If you have read any of my previous articles or viewed the many videos I have published, it's quite clear that I appreciate a good rocket or fiery projectile. The following video will certainly not lessen that reputation.

It's a real challenge to create exploding targets that can be set off by low velocity projectiles, yet remain safe to handle without risk of ignition during construction.

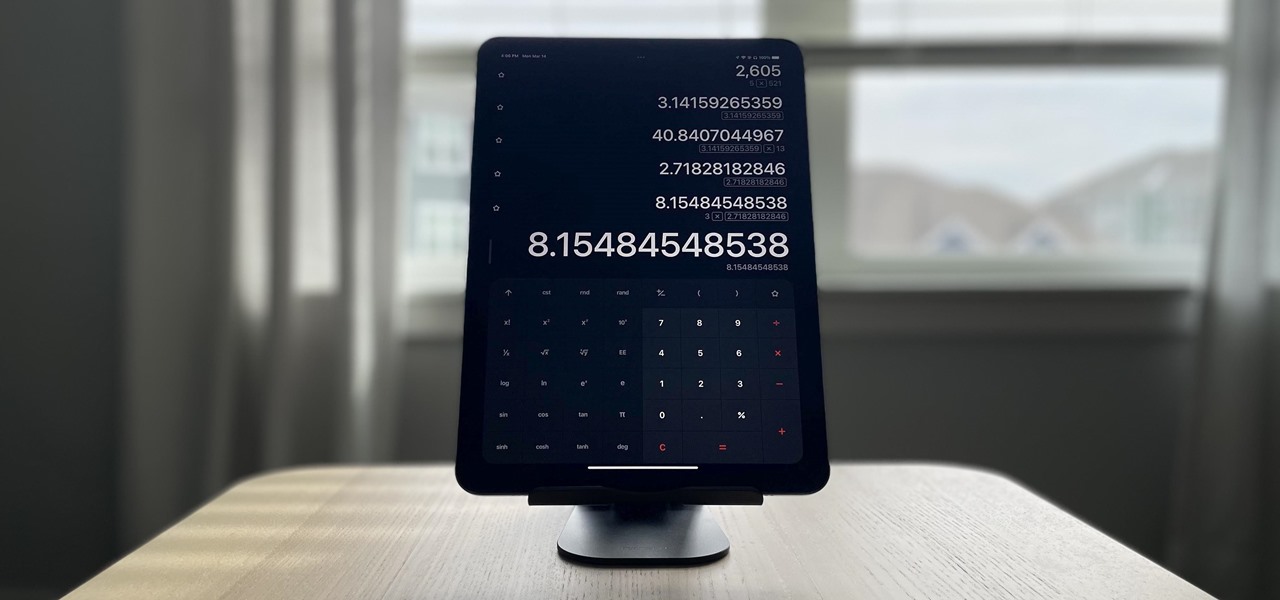
Apple doesn't include its Calculator app on the iPad and never did. One almost appeared over 12 years ago but was nothing more than a blown-up version of the iPhone app. Since then, the company still hasn't made an iPad-optimized calculator, and there is no shortage of third-party alternatives to fill the gap. It may happen one day, but for now, these are the best calculator apps for your iPad.

You're a busy, on-the-go professional, so you deserve an email client that keeps up with you. "Mail" on iPhone wasn't always the best option, but thanks to iOS 13, it feels like a completely different app. That said, there are plenty of alternatives that offer a different experience. Better yet, these apps are free. You won't need to spend a dime to try them out for yourself.

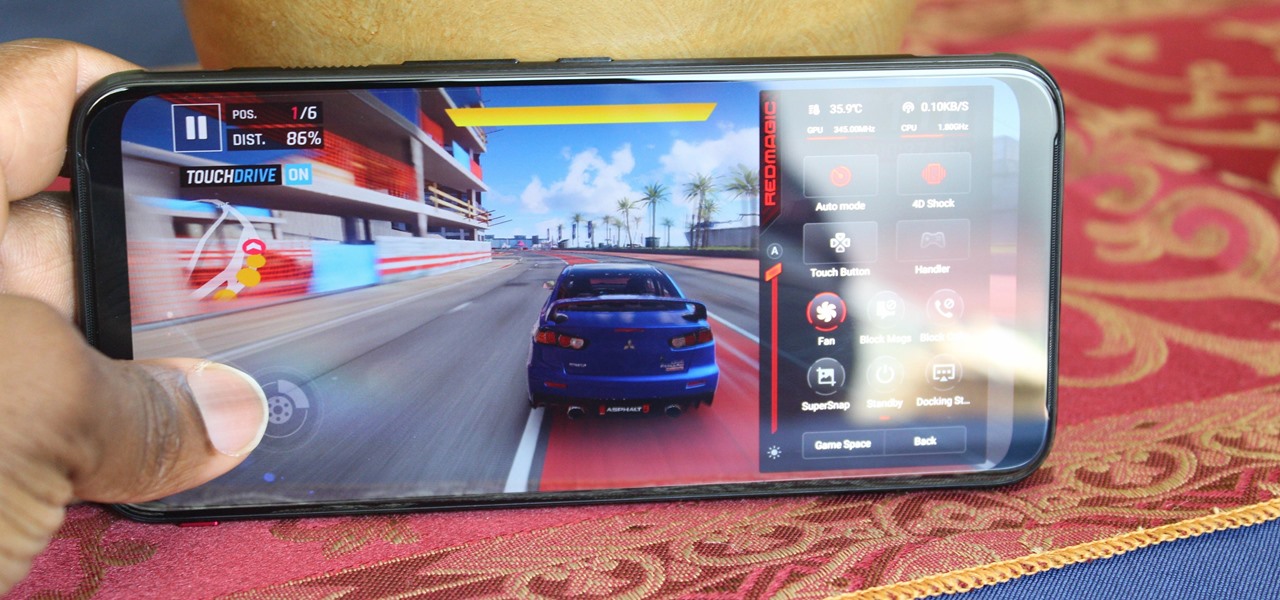
Mobile gaming has exploded in recent years, with experts predicting 2.4 billion global mobile players by the end of 2019. It already accounts for 47% of the worldwide gaming market, besting console and PC. No wonder we've seen the rise of gaming smartphones, a class of phones that specialize in mobile gaming.

Your phone's keyboard is one of the most commonly used apps. Whether you're typing out status updates, sending private messages, or just bombarding everyone in sight with as many emoji as you possibly can, you probably couldn't get by without a good keyboard app.

For many, phones are starting to replace televisions as the primary device for watching videos. Thanks to their portability and easy to use apps, it's often simpler to watch Netflix, Hulu, YouTube, or Prime Instant Video on the smaller screen. But not every phone is suited to fit this need, so we did some testing to find the best of the best when it comes to streaming videos.

Okay, so you've decided to take the plunge, and participate in our Love. Earn program with a how-to article. But, for whatever reason, your article keeps getting rejected by WonderHowTo, and you're wondering, well, where's the love?

It's not hard to let the new SARS-CoV-2 strain of coronavirus put pressure on our minds. Fear of catching COVID-19 is never far from the topic of conversation. But it doesn't have to be that way. If you're struggling with anxiety, stress, depression, or any negative emotions due to the virus's effect on our lives right now, you might find some solace in meditation.

If you just got a new iPhone, chances are you picked up the iPhone 11, successor to the iPhone XR, the most popular device in Apple's 2018 series. Since the XR did so well, it was predicted that the iPhone 11 would too, and so far, it has lived up to that prediction, beating the 11 Pro and 11 Pro Max in sales in 2019.

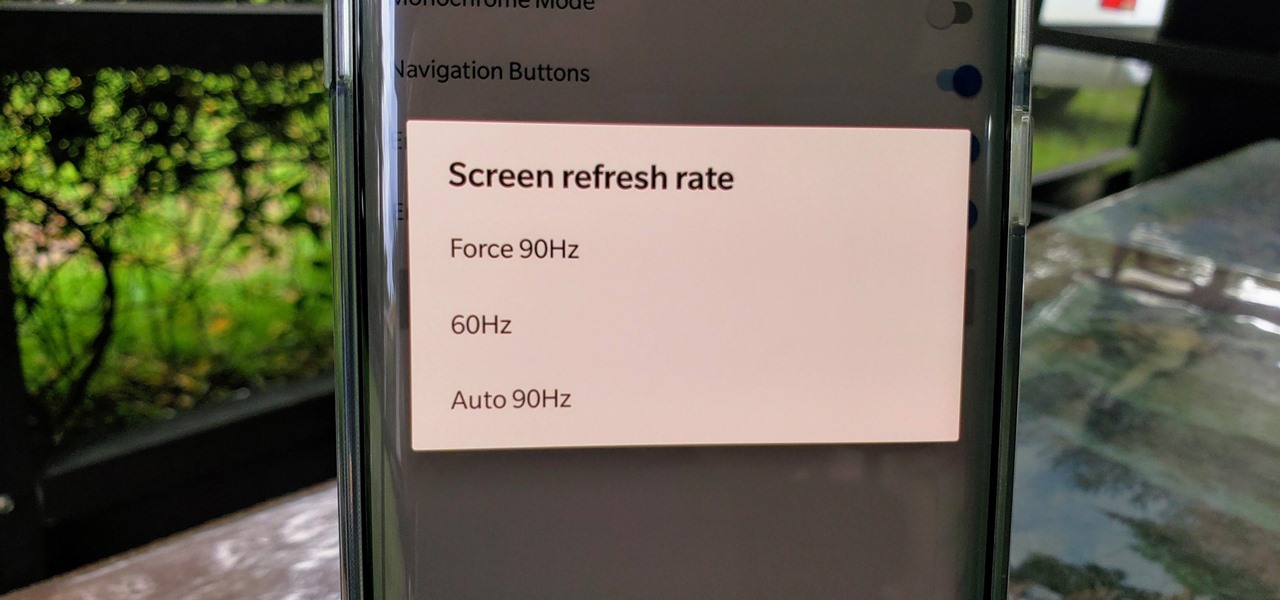
One of the standout features of the OnePlus 7 Pro is the 90 Hz display. A higher refresh rate means smoother gameplay for all your favorite games, which is precisely what you'd want out of your gaming experience. However, not all games play nicely with these higher refresh rates — but luckily, there's a pretty simple fix.

While photography usually gets all the love, our phones have gotten really good at capturing video. Think about it — when was the last time you needed a camcorder for a vacation? With mobile cameras getting better each year, we're now at a point where smartphones can be used for pro-level videography.

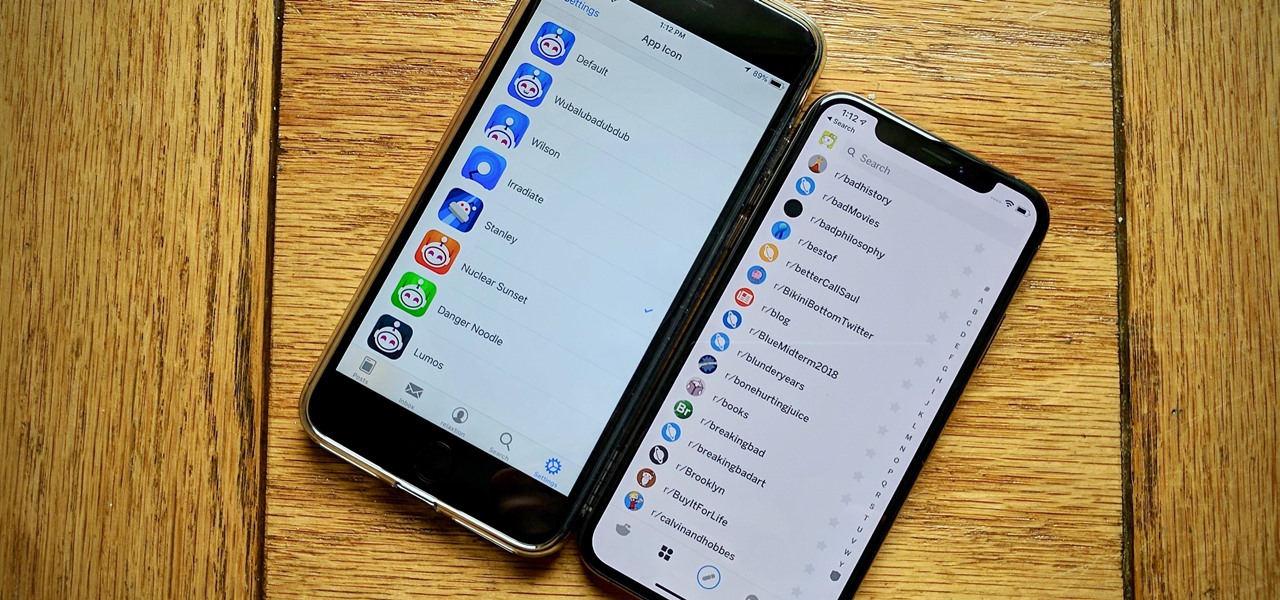
These days, using Reddit on your iPhone is just as good, if not better, than Redditing on a desktop browser. While there's an official Reddit app for iOS, there are plenty of third-party clients that have similar features as well as custom perks to enhance the experience. But figuring out which Reddit client is best for your daily use can be a lot of work — work that we can make easier on you.

The Galaxy S9 is now in the hands of millons of excited users. Getting a new phone is always fun, but it's important to think about protecting your device. Perhaps the most popular cases for the Galaxy S9 are the official OEM options from Samsung. There are a plethora of cases, whatever your preference and needs may be. Let's take a look at each case individually, along with the pros and cons.

Nmap is possibly the most widely used security scanner of its kind, in part because of its appearances in films such as The Matrix Reloaded and Live Free or Die Hard. Still, most of Nmap's best features are under-appreciated by hackers and pentesters, one of which will improve one's abilities to quickly identify exploits and vulnerabilities when scanning servers.

Recently, I ran across SecGen, a project which allows a user to create random vulnerable machines. I absolutely love vulnerable machines, since a vulnerable VM is a safe and legal way to practice hacking tactics, test out new tools, and exercise your puzzle-solving skills.

A remote administration tool, or RAT, is a piece of software used for remotely controlling machines. They are commonly used by tech support to gain remote access for troubleshooting purposes, but RATs are also an important part of a hacker's advanced persistent threat (APT) toolkit. Unlike standard administration RATs, these tools are designed to be delivered stealthily and operate undetected.

In my previous article, I discussed installing and configuring OpenVAS on Kali Linux. Now it's time to start using OpenVAS with the Greenbone Security Assistant to audit networks for security issues. This can be extremely helpful when you are looking for vulnerabilities or misconfigurations in a large number of hosts.

Keystroke injection attacks are popular because they exploit the trust computers have in human interface devices (HIDs). One of the most popular and easily accessible keystroke injection tools is the USB Rubber Ducky from Hack5, which has a huge range of uses beyond simple HID attacks. The USB Rubber Ducky can be used to attack any unlocked computer in seconds or to automate processes and save time.

Hear me out. No, really. Before you sharpen your pitchforks and give me anecdotal evidence of your Chinese restaurant syndrome, I think you need to know a few things about monosodium glutamate. First of all, it's a naturally-occurring chemical compound that can be found in anything from tomatoes to cheese, and is used in all kinds of foods from KFC to breakfast sandwiches. So spare me the comments on MSG and Chinese food—you probably eat MSG on a daily basis without even knowing it. (And also...

There seems to be a nearly cult-like craze surrounding those glasses filled with summery, pink-hued rosé wine. From picnics in the park to long days spent on the beach, rosé wine offers light, warm-weather refreshment to its lucky imbiber.

Hello my fellow hackers, it's been a while since my last post, I can't get the time now-a-days for the posts but can manage to tend to comments.

Welcome back, my budding hackers! As I have mentioned many times throughout this series, knowing a bit of digital forensics might keep you out of a lot of trouble. In addition, digital forensics is a burgeoning and high paying career. Some knowledge and certifications in this field will likely help you land a Security Engineer position or put you on the Incident Response Team at your employer.

Welcome back, my greenhorn hackers! Digital forensics and hacking are complementary disciplines. The better you are at digital forensics, the better hacker you are, and the better hacker you are, the better you are digital forensics. Unfortunately, few people in either profession cross these discipline lines.