Hear me out. No, really. Before you sharpen your pitchforks and give me anecdotal evidence of your Chinese restaurant syndrome, I think you need to know a few things about monosodium glutamate. First of all, it's a naturally-occurring chemical compound that can be found in anything from tomatoes to cheese, and is used in all kinds of foods from KFC to breakfast sandwiches. So spare me the comments on MSG and Chinese food—you probably eat MSG on a daily basis without even knowing it. (And also...

There seems to be a nearly cult-like craze surrounding those glasses filled with summery, pink-hued rosé wine. From picnics in the park to long days spent on the beach, rosé wine offers light, warm-weather refreshment to its lucky imbiber.

Hello my fellow hackers, it's been a while since my last post, I can't get the time now-a-days for the posts but can manage to tend to comments.

Welcome back, my budding hackers! As I have mentioned many times throughout this series, knowing a bit of digital forensics might keep you out of a lot of trouble. In addition, digital forensics is a burgeoning and high paying career. Some knowledge and certifications in this field will likely help you land a Security Engineer position or put you on the Incident Response Team at your employer.

Welcome back, my greenhorn hackers! Digital forensics and hacking are complementary disciplines. The better you are at digital forensics, the better hacker you are, and the better hacker you are, the better you are digital forensics. Unfortunately, few people in either profession cross these discipline lines.

Sherlock Holmes is one of the most famous characters in modern history, and has appeared in film more often than any other character. No less than 78 different actors have taken their turn at portraying the enigmatic deduction machine in various mediums, and each has brought their own foibles to the role. Some of the names may even surprise you: Tom Baker, John Cleese, Peter Cushing, Charlton Heston, Christopher Lee, Roger Moore, and even Leonard Nimoy.

Choosing which programming language to learn next can seem like a nearly impossible task, regardless of whether you're a novice developer or a seasoned coding pro with years of experience creating apps and websites. But if you haven't already learned Python, look no further.

You've just picked up your new Samsung Galaxy S20, S20+, or S20 Ultra — but wait. After you turn it on and restore your data, there a few apps you should install to get the most out of your updated phone. Installing these eight apps right away will help maximize your experience from the very beginning.

One of my favorite perks of this job is the opportunity to try out all the big flagship phones each year. Whether it's rating their suitability for a particular use-case or just entering their specs into our comparison tool, we have to get our hands on all major phones released in the US. We pride ourselves on being fair in our reviews and roundups, but that doesn't mean we don't have preferences.

Christmas is just one week before Jan. 1. That means a lot of New Year's resolutions filled with promises to better ourselves with increased productivity, focus, and work ethics — but getting started can be challenging. Give the people in your life a leg up this holiday season with these smartphone gifts to keep them on-task in 2020.

Remember when typing without physical keys seemed ridiculous? Now, touch typing is the smartphone norm. That said, mistakes are inevitable on small screens. So before you start hammering on that delete key or shaking your iPhone like a madman, know that there's a better way to undo text you didn't mean to type — no shaking involved.

iPhones with Face ID all retail for at least $999, which many still believe is just too much for a smartphone. But that's okay, because Apple just introduced the iPhone 11 for roughly $700. It's not necessarily the best value, though, because the iPhone 11 already has some stiff competition in this price range.

With Android 10 "Q" right around the corner, now would be a great time to get accustomed to the new system-wide dark mode it's bringing with it. Dark themes not only allow for more comfortable viewing at night, but can also consume less battery at the same time. With a single button tap, you'll be able to enable this new dark theme for all compatible apps without having to jump through hoops.

For the first time, you can officially use a computer mouse with your iPhone, thanks to Apple's new Accessibility settings in iOS 13. It works for all types of Bluetooth mice, so if you have one, it'll already work. Plus, those with wireless receivers and even wired mice are supported by using a USB to Lightning adapter.

We recently set out to find the best phones for people whose primary usage revolves around social media apps like Facebook and Instagram. Samsung, Apple, and Google were the three brands that made our top five, and while the latter only had one finalist, the two bigger OEMs had a pair of phones each. What struck us, however, was that Samsung's phones edged out Apple's not once, but twice.

One of iOS 12's biggest attractions is Group FaceTime, which would allow up to 32 people to video chat together at the same time. It's quite the pitch, and many iOS users are excited to see in action. Unfortunately, Apple has confirmed that Group FaceTime won't be included with iOS 12 when it launches, leaving everyone to chat one-on-one just a little bit longer.

On Thursday, Osterhout Design Group (ODG) revealed a new, specially-crafted oxygen mask that uses the same augmented reality technology from its smartglasses to assist FedEx Express pilots navigating dangerous conditions.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

Razer just released their first flagship Android smartphone, appropriately named the Razer Phone. While mobile gaming fans are sure to enjoy the Razer Phone, the buttery-smooth 120 Hz display makes this an appealing option for anyone in the market for a new phone. If you've just picked up the Razer Phone or it's piqued your interest, here are ten awesome tips to hit the ground running.

After numerous scandals like the Equifax data breach and the 2016 US election, cybersecurity has become a significant issue for Americans. Unfortunately, anytime we use our devices, we're open to a cyber attack — especially when we browse the web. However, there are ways that we can make it harder for hackers and data miners.

HDR, or high-dynamic range, is currently the best way to view movies and TV shows on your iPhone 8 or 8 Plus. With a wider color gamut and a broad luminance range, there's no beating HDR video for the ultimate viewing experience. Unless, of course, you don't have the storage to hold those giant Dolby Vision or HDR10 files.

In my previous article, we learned how to generate a vulnerable virtual machine using SecGen to safely and legally practice hacking. In this tutorial, we will put it all together, and learn how to actually hack our practice VM. This will provide some insight into the methodology behind an actual attack and demonstrate the proper way to practice on a VM.

With augmented reality comes an infinite realm of possibilities for storytelling. We have seen it through wineries telling their history with interactive AR experiences and through authors that use augmented reality to bring portions of their books to life. However, filmmaker Peter Jackson might take the cake on creating an incredible new way of storytelling.

One of the first things you'll do with the HoloLens is place little holograms around your room, and it'll look like you have a large figurine collection. Ralph Barbagallo, Edward Dawson-Taylor, and their HoloHacks team decided to take that a bit further and created an app that allows the user to produce and tour virtual art exhibits.

Welcome back everyone. This article isn't going to contain anything related to scripting, but rather some updates about the series. We'll be quickly discussing what we've covered so far and what is to come.

Welcome back, my hacker novitiates! In the previous two posts in this series, we looked at the basics of buffer overflows. In this post, we will look at one technique for finding buffer overflows. We will try to send random, oversized, and invalid data at a variable to see whether we can make it crash or overflow. This process is known as fuzzing. It is often the first step to developing an exploit, as we need to find some variable that is susceptible to overflowing.

My years in the restaurant business have taught me many things. Some of those things are best left unsaid and other things require a PhD in vulgarity, but the one thing I learned that I keep coming back to night after night is that you do not have to spend a lot of money to drink excellent wine. This is especially true of champagne...I'm sorry, sparkling wines.

Gatorade: its popular red flavor can stain the whitest fabric, and its sweet taste is oddly refreshing after breaking a sweat. If you've ever participated in a sport, you probably spent halftime at games and practice breaks chugging the stuff. Though it made its name as a sports drink, Gatorade is also a well-known hangover helper—but its beneficial and interesting uses don't end there. The brightly colored drink can do so much more than just hydrate you.

Diabetes is a well known metabolic disorder occurs due to disturbance of insulin level in the blood leading to high glucose level which has a very serious impacts on our body To Avoid Diabetes; You Have to Do Four Things

Welcome back, my neophyte hackers! I have already done a few tutorials on password cracking, including ones for Linux and Windows, WEP and WPA2, and even online passwords using THC Hydra. Now, I thought it might be worthwhile to begin a series on password cracking in general. Password cracking is both an art and a science, and I hope to show you the many ways and subtleties involved.

Interesting reaction coke and milk The reaction of phosphoric acid (V) to proteins in the milk - they are cut and causes a precipitate

Mermaid Braid Hair Style Tutorial For Beginners!!!!

In this video, I'll be showing you how classic black snakes work and how to make them at home. There are actually two methods covered in the video — one that uses fire and one that does not. So just choose the one that fits best for your situation.

It may seem like a trivial topic, but the majority of people don't use paper towels the proper way (just as they don't crap the proper way). The outcome of this improper usage?

"Jef with one F" from the Houston Press compiled a list of the 10 best steampunk songs, but it's really a collection of the best steampunk music videos. There are some amazing videos in the collection, such as this one, "Brass Goggles" by Steam-Powered Giraffe. It's not the best-looking, but it's a great performance.
1 Identify the child's talents, and discuss the opportunities he has to use them in productive ways. If you notice that the child you're mentoring is excellent with counting money, talk about how the child should consider a career in banking or running a business one day.

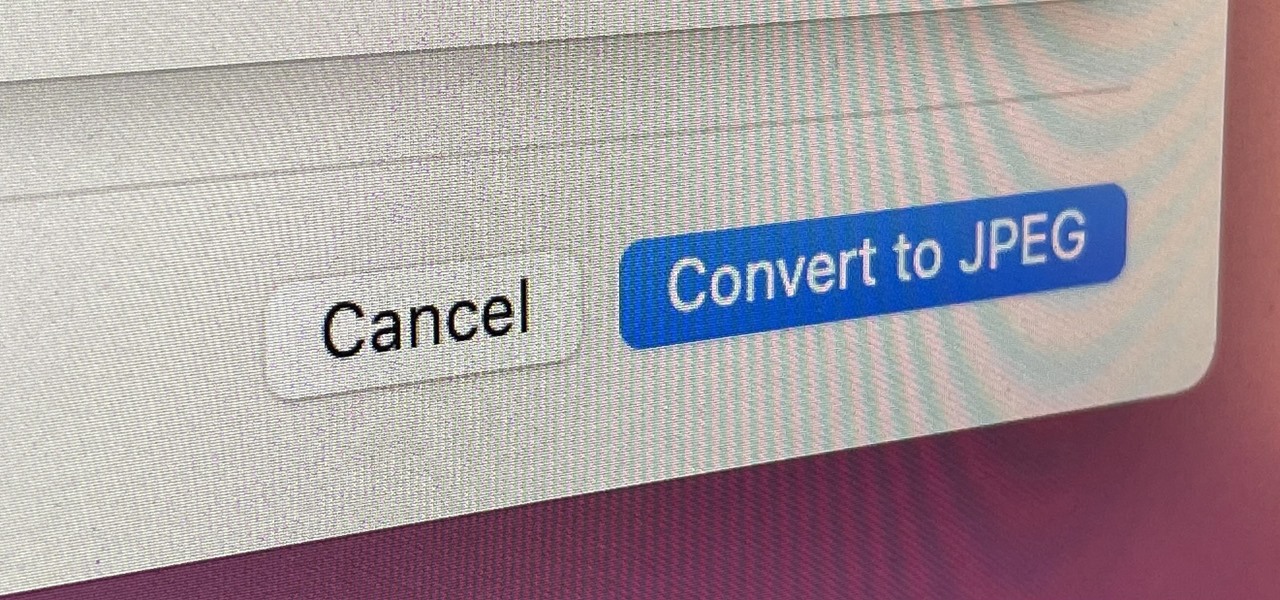
If you regularly run into issues opening images that use the .heic extension, the easiest solution is to convert the file into a more compatible format. Using apps like Photos and Preview on a Mac makes the process simple, but macOS Monterey just streamlined the process so that you don't even have to open an app anymore.

OnePlus will be releasing a new phone in the second half of 2018, specifically, an upgrade to their T-series. Over the past two years, #T versions have come out about five months after their predecessors and have included small updates that fix any problems from the previous OnePlus device. While we do know a bit about OnePlus 6T, what it could be is much more exciting.

Coinhive, a JavaScript cryptocurrency miner, was reportedly discovered on the BlackBerry Mobile website. It was placed there by hackers who exploited a vulnerability in the site's e-commerce software that allowed them to anonymously mine cryptocurrency every time the website was viewed. There's no doubt Coinhive, an innovative mining method, is being abused and exploited by hackers in the wild.