Last week, Apple issued an iOS 7.0.6 update that fixed a serious security vulnerability that could allow hackers to steal passwords, read emails, and get info from other SSL-encrypted communications.

I can be pretty forgetful. If there's something important to remember, I need to jot it down right away or risk losing it forever.

It's always the snack you're most looking forward to that ends up being moldy when you open the fridge to grab it. Always. That slice of leftover pizza or chunk of cheese you've been thinking about all day? We've all been there. What separates us is how we choose to deal with it. Personally, I toss anything that has even the slightest hint of mold, but not everyone errs on the side of caution. Some people don't mind the risk and just cut off the green or fuzzy parts and eat the rest.

Drilling holes in wall tiles is a fairly easy skill to master once you know how. Follow these simple steps on how to drill a hole in a tiled wall for a hassle free experience.

A lot of computers come with a ton of pre-installed software from the manufacturer, some of which you need and some of which you could most certainly live without. And over time, you may have downloaded and installed a bunch of programs and apps that you probably can't even remember. Now, you could go ahead and uninstall everything that you don't think you need, but then you run the risk of removing something that could really mess up the system. When I open up my Programs folder, I feel like...

I had my wallet stolen a few months ago, and I knew I would never see it again. My biggest gripe was not the credit cards in there, since they're easily cancelled, but the gift cards. I had some pretty good gift cards in there, and there's no way to get those back.

For the most part, nobody makes money off of Facebook. Sure, some people make a living by updating pages for businesses and celebrities, but hardly anyone gets a dime from the site itself.

Not many people fly kites anymore. Most of us don't have the patience or attention span because, let's face it, we're used to smartphones and other gadgets that have games and apps galore to entertain us. Heck, you can even fly a kite on them if you really want.

Here's a technique I used to whip up a batch of super cheap and easy to make smoke flares! WARNING: Ignition of an incendiary or explosive material may not be legal in your area, so check local laws before attempting. Use of this video content is at your own risk.

Maybe not water per-se, but with this simple technique you can turn one of the most abundant materials on earth into a highly explosive gas.

There is no better example of a risk-versus-reward scenario than jailbreaking your iPhone or rooting your Android phone. While both jailbreaking and rooting undoubtedly has its advantages, this possibility of something going wrong and you ending up with a 500-dollar doorstop is never too far out of mind.

Do you own an HP printer? If so, it may be vulnerable to malware attacks. Researchers at Columbia University discovered that 25% of Hewlett-Packard printers have significant vulnerabilities that put your printer in danger from hackers—even your home. With a budget of just $2,000, researchers Salvatore Stolfo and Ang Cui were able to hack into the printers using remote firmware to install malware, and in some cases even cause the printer to catch on fire. The main issue is with the printer's c...

Trust is one of the most important aspects in a relationship. You can work on some trust building exercises and activities to strengthen your current relationships. Plus some of these activities are just fun.

Add a perfect theme dessert to your next Hawaiian luau with this decadent coconut cream pie. After a long week at work there’s nothing better than a little back yard barbecue fun with friends topped off with the perfect treat.

Depending on where you live, you will have to prepare for the hazards from different types of natural disasters. You can sleep easy if you have a secure location, stalked with food and supplied you might need if there is an emergency.

This video demonstrates a method of fixing the E 74 Xbox 360 error. In order to do this, you first must disassemble your XBox, which will void your warranty, so this is at your own risk.

Aba Wood Flooring demonstrates how to sand between coats when working with water-based finishes on hardwood floors. When you use an electric sander, avoid overheating the surface when sanding between coats of a water-based finish. Accomplish this by replacing conventional sand screen pads with a Velcro triple head sanding plate and soft interface pads. The triple head sanding plate and interface pads offer better dust extraction and a more effective final sanding. This system also offers bett...

Don't buy those $100+ laser pointers. Watch this video, and for under $50 you can make your own that is capable of burning, popping balloons, and cutting things!

This entertaining video demonstrates how to make a bottle rocket using tape, paper napkins, Mentos, and Diet Coke or Coke Zero. Try at your own risk! Make a pouch with the paper napkin. Put the Mentos in the pouch and roll the napkin with the Mentos into a tube shape. Open the plastic bottle of Diet Coke or Coke Zero. Place the tube in the top of the bottle, but don't let the Mentos make contact with the soda. Keep the napkin/Mentos tube stuck tightly in the top of the bottle. Re-attach the b...

Want more range out of your wireless mouse? How about your keyboard? Maybe you like working from your couch and the signal's a little bit finicky. Well, this is the solution for you, but it requires a little work.

Check out this how-to video for a discussion of the card strategy game, Mystery Rummy Case #1 with its designer, Mike Fitzgerald. Mystery Rummy Case #1 is a two to four player game. Take a look at these Mystery Rummy cards!

See how to increase the mW of a 5 mW Green Laser Pointer!

The ability to browse the web in coffee shops, libraries, airports, and practically anywhere else you can imagine is more than convenient, but convenience has risks. Using public Wi-Fi allows others to spy on you easily. Even your own internet service provider can see every website you've ever visited. Don't fall into the trap of protecting your identity, data, and devices after it's too late.

Regardless of whether you're an aspiring or established coding pro, knowing just one or two programming languages and platforms is no longer sufficient if you want to be truly competitive in an increasingly popular and lucrative field. But before you spend an excessive amount of time mastering six new platforms, do yourself a favor and master Linux.

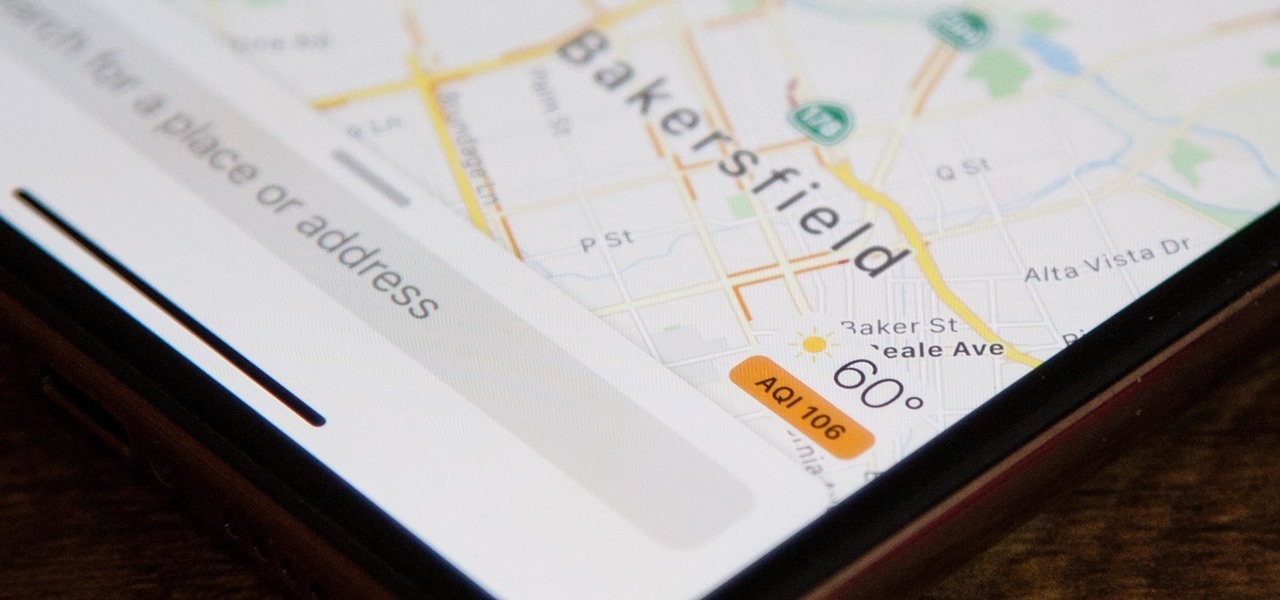
While the United States, in general, doesn't have the worst overall pollution, the air quality can drastically change from one day to the next. If you're particularly sensitive to pollutants in the air, there are apps that show how clean or polluted the air is in your area, as well as in cities you plan on traveling to, but Apple's making those apps less relevant with a new feature in Apple Maps.

Huawei has been in a losing battle with the US government for around ten years, with the last year being the spike of Huawei's problems. Because of US pushback against some Chinese-based smartphone manufacturers due to security concerns, Huawei is hoping to limit its dependency on US-based companies, and recent rumors of Huawei's very own mobile operating system may be the first step.

Look, tests are no fun, and doing poorly on them is rarely an option. Whether you're studious or a slacker, everyone needs a little boost now and again. While students have found ways to cheat as long as tests have existed, the invention of smartphones has greatly enhanced the potential to get ... creative.

With the announcement of ARKit 2.0 at WWDC 2018, Apple is bringing some powerful new capabilities to mobile augmented reality apps this fall.

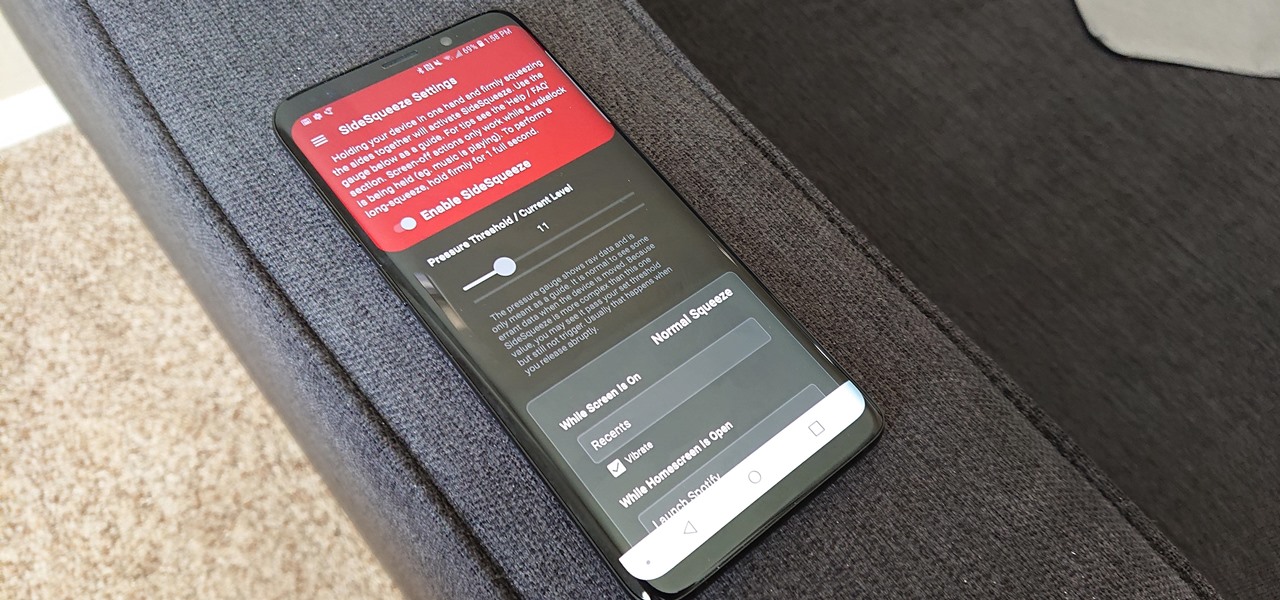
All the Android fans out there undoubtedly remember the squeeze gestures introduced with the HTC U11. Google continued the trend by bringing the gestures to the Pixel 2 and Pixel 2 XL. Thanks to a brand new app, you can now enable similar squeeze actions on your Galaxy S9 or S9+, and even some older Samsung phones.

As the third-largest smartphone manufacturer in the world, Apple devices are a constant target for hackers everywhere. While iOS has seen fewer common vulnerabilities and exploits (CVEs) in recent years, iPhones still aren't hack-proof. Fortunately, you can strengthen your security with the help of a few apps.

Over the years, the internet has become a dangerous place. As its popularity has increased, it has attracted more hackers looking to make a quick buck. However, as our dependency on the web grows, it becomes increasingly difficult to sever all ties. This means we have to protect one of our weakest points, the password.

Armis Labs has revealed eight vulnerabilities, called "BlueBorne", which put 5.3 billion Android, iOS, Windows, and Linux devices that use Bluetooth at risk. With it, hackers can control devices, access data, and spread malware to other vulnerable devices through networks. In this post, we will learn about the vulnerabilities, then look at how to find devices that have them.

The bacteria in our gut — a community called the gut microbiome — have been in the spotlight a lot lately. What we're learning about how our intestinal bacteria adapt and grow with our bodies could help athletes perform better, according to researchers starting a company focused on creating probiotics that mimic athletes' microbiomes.

Whether or not a microbe is successful at establishing an infection depends both on the microbe and the host. Scientists from Duke found that a single DNA change can allow Salmonella typhi, the bacteria that causes typhoid fever, to invade cells. That single genetic variation increased the amount of cholesterol on cell membranes that Salmonella and other bacteria use as a docking station to attach to a cell to invade it. They also found that common cholesterol-lowering drugs protected zebrafi...

There is a reason the Amanita phalloides mushroom is called the "Death Cap." It can kill you. Mushrooms are a type of fungi, an organism that produces thread-like mycelia that often produce spores. Spores allow the fungi to reproduce. Molds, lichens, and yeast are all fungi, but the most visible fungi are mushrooms. Some fungi are delicious, but others can cause disease or, and still others, like Penicillium, can cure it.

Nineteen days ago, several hundred people could have been exposed by a traveler with measles in Nova Scotia, Canada. The next day, someone flying from Minnesota to Nebraska may have spread the measles to other passengers. A couple weeks ago, it's possible that a man and his six-month old child spread the measles in several Seattle-based locations. Authorities are trying to locate persons who may have been in contact with these people. None of the persons with measles were vaccinated. Why?

In a world increasingly regulated by computers, bugs are like real-life cheat codes. They give you the power to break the rules and do good or bad without ever leaving your seat. And government agencies around the world are discovering and stockpiling unreported bugs as cyberweapons to use against anybody they see fit.

For some, drinking raw milk is a way to get back to nature, improve family nutrition, and hedge against asthma and allergies. However, according to public health authorities, drinking raw or unpasteurized milk is a big mistake—even fatal. So what's the story?

At a global security conference in Munich, philanthropist and businessman Bill Gates spoke about the next pandemic and a dire lack of global readiness. Here's how his statement could come true—and how to be ready when it does.

Jostled in the airport, someone is coughing in line. The air looks empty but it is loaded with microbes that make their way into your body. You get sick. You give it to your family, and that's pretty much it. But what if you were so contagious that you spread it to your entire community and beyond?