Culinary collective Studiofeast is known for thinking outside the box, especially when it comes to food. They've hosted inventive and spectacular events like the L Train Lunch, where a high-end meal was served to guests on a moving train, and the Datalicious Last Supper, where results from a survey of people's desired "last meals" informed the menu.

The initiative known as Project Aria has been the focus of curiosity around Facebook's augmented reality plans ever since Mark Zuckerberg revealed the device around this time last year.

I must admit, upon learning that the NFL was broadcasting the contest between the New Orleans Saints and Chicago Bears on CBS, Amazon Prime Video, and Nickelodeon, the latter was the only option I wanted, purely for the novelty of the experience.

Does TikTok scare you? Trust me, I get it. It's a strange, unfamiliar place to those of us not accustomed to its ways, populated by teenagers and college students with their own subcultures, memes, and humor. But here's the thing: TikTok has something for everyone, you included.

Here at Next Reality, our typical approach to all things augmented reality involves vision combined with remote control, either via a handheld device, gaze control, or hand/finger tracking.

Hacker's are always looking for new ways to exploit systems and exfiltrate passwords, even in hashed form. Sophisticated brute-force attacks powered by high-end GPUs can perform millions of password attempts per second. But Ubuntu and Debian users aren't completely helpless. There are ways to harden the hashed password to better defend against Hashcat attacks.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

In the previous article, we learned how to set up our VPS, configure our PHP server, and developed an in-depth understanding of how the payload works. With all that taken care of, we can get into disguising our payload to appear as an image and crafting the note in the greeting card being delivered to our intended target.

In one of my previous articles, I discussed ShinoBot, a remote administration tool that makes itself obvious. The goal is to see if the user could detect a remote administration tool or RAT on their system. In this article, I'll be demonstrating the use of Pupy, an actual RAT, on a target Ubuntu 16.04 server.

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.

I know, "Steamdown" conjures images of a hoedown, but "Steampunk prop breakdown" is a bit of a mouthful, I thought.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. Well this is it folks, the final Pre-Release before Minecraft officially launches! These changes should be the final game changes until it releases in Vegas this Friday. Mojang has made it clear, however, that they will continue making changes to the game while it's released.

Welcome to Minecraft World! Check out our advanced tutorials and come play with us on our free server.

We usually focus on augmented reality here, but when something important in VR happens, we highlight it as part of the overall immersive computing story.

Since the start of the COVID-19 pandemic, Google has packed new functionality into Google Meet to compete with Zoom, Microsoft Teams, and other video conferencing platforms.

Sure, Snapchat AR Lenses can be fun, but they can help communicate complex issues as well. While our Facebook news feeds were filled with references to 311 Day, March 11 is also World Kidney Day, the United Kingdom's National Health Service Blood and Transplant (NHSBT) used the occasion to educate its constituents about organ donation.

Rumors of Apple developing smartglasses have persisted as prophecy since 2016, but the arrival of what many herald as the savior of augmented reality have eluded even Nostradamus himself.

Business hours and addresses change, but they're not always updated on Yelp by business owners for the rest of us to see. Showing up when a business is closed or going to the incorrect address is a major annoyance, which is why the company allows us, the customers, to help update business information through the Yelp mobile app on iOS and Android. If owners won't do it, somebody has to.

We need to take our privacy and security much more seriously. Whether it's malware-infected apps or the mishandling of our data by companies like Facebook, there are threats all around us in this digital world. Fortunately, some smartphones are simply designed to protect us better.

It seems like each day new rumors and leaks come out for Huawei's upcoming P series devices. Everything from its name change to its specs has been leaked, sometimes with contradicting rumors. One of the biggest leaks is the inclusion of triple rear cameras, a first for smartphones.

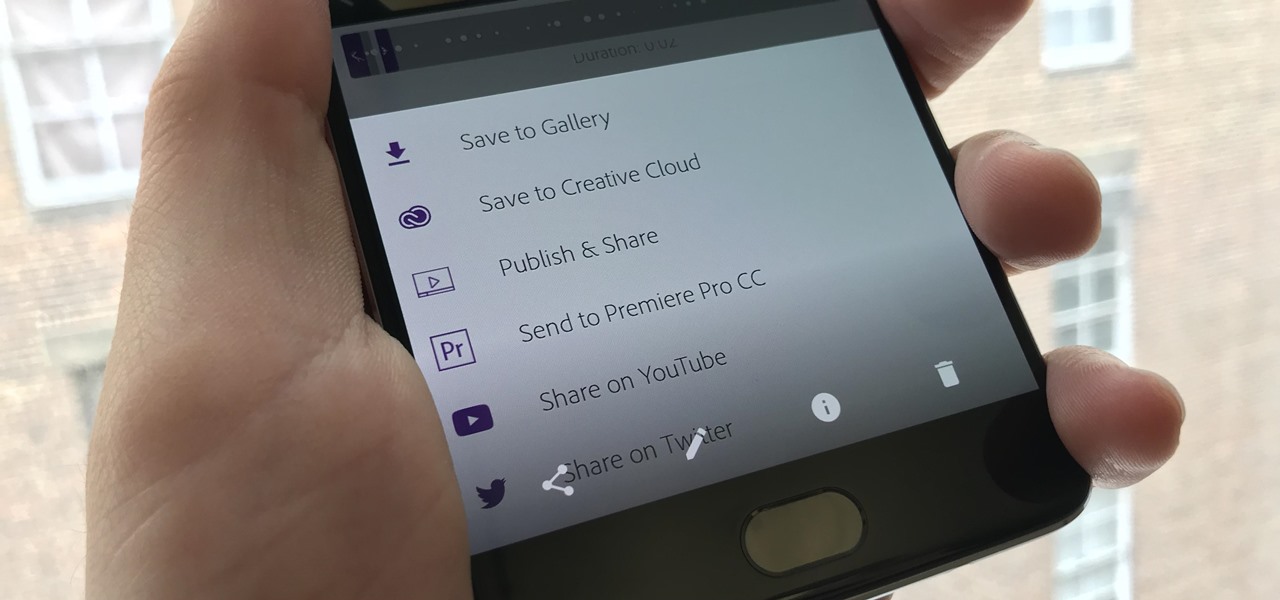
If you've taken the time to edit a video on your iPhone or Android phone, you probably have a purpose for it. Maybe you want to share it to YouTube in hopes of making the next viral sensation. Maybe you just want to save the video to your phone to show off to friends and family when you can.

Mobile augmented reality developer Blippar has updated its mobile app for iOS and Android with an augmented reality face profiles feature based on the company's real-time facial recognition engine.

Open-source data scraping is an essential reconnaissance tool for government agencies and hackers alike, with big data turning our digital fingerprints into giant neon signs. The problem is no longer whether the right data exists, it's filtering it down to the exact answer you want. TheHarvester is a Python email scraper which does just that by searching open-source data for target email addresses.

Greetings aspiring hackers. I have observed an increasing number of questions, both here on Null-Byte and on other forums, regarding the decision of which USB wireless network adapter to pick from when performing Wi-Fi hacks. So in today's guide I will be tackling this dilemma. First I will explain the ideal requirements, then I will cover chipsets, and lastly I will talk about examples of wireless cards and my personal recommendations. Without further ado, let's cut to the chase.

Juicing fruits and vegetables is very beneficial to your health. For some, it's a trend; but to me, it's a part of my morning routine.

Sangria... the elixir of summer. When properly prepared, there are few things more refreshing and magical. If you're looking for a way to mix things up and "get out of the bottle," try one of these lovely libations before the warm weather ends: peach-mango sangria, pineapple-basil sangria, watermelon-raspberry sangria, or blueberry-plum sangria.

Staying healthy is a progressive challenge we all face throughout our lives, and figuring out just how to do that can be a challenge when it's not your job. For doctors, however, it is. Here's how they keep themselves healthy day to day.

Although your friends might roll their eyes every time you talk about playing Clash of Clans, Call of Duty, or Candy Crush Saga, your excessive gaming habits might actually be making you healthier than everyone else.

Steampunk is a tremendously interesting phenomenon because of its reliance on science fiction, and fiction in general. Steampunk can arguably be broken down into two categories: the fiction, and the aesthetic. Sometimes these categories cross over, but they're often more distinct than most people suspect; that said, the aesthetic is firmly based in works of fiction.

These days, eReaders are everywhere. For die-hard book nerds, eReaders offer the convenience of a full library without having to sacrifice shelf space. Sure, there are the paper buffs who swear that you just can't take an eReader with you into the bathtub, but when's the last time anyone actually did that? Face it, eReaders are convenient and here to stay. But there's a dizzying array of information out there, so what should you look for in an eReader?

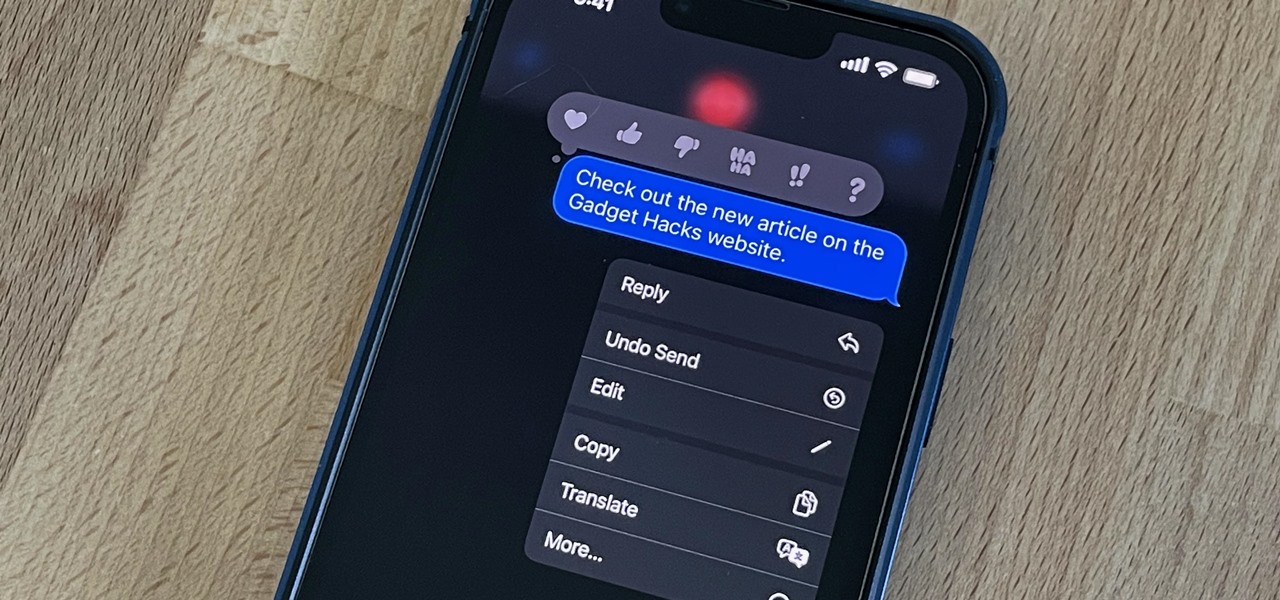
While you can quickly see the edit history of a modified iMessage in the Messages app, there's no way to view an iMessage that somebody in the conversation deleted unless you happened to see it before it disappeared. But that's only true if you didn't implement these security measures on your iPhone.

Apple CEO Tim Cook has said that augmented reality (or, AR for short) will "change everything." But what, exactly, is augmented reality?

For almost a decade, projector phones have tried to entice consumers with their convenience as media machines. While these devices are alluring, they've never really taken off with mainstream success. The latest effort, Moviphone, sounds tempting if you watch a lot of films and TV on your smartphone, but is it good enough to be your daily driver?

The Play Store hasn't been the most secure place for apps lately. A quick Google search for "Play Store malware" will give you a taste of some of the malicious apps that snuck their way onto Android's official app store. Google is aware of the problem and they're tying to fix it, but their new Play Protect program doesn't have a great track record, so you might want to look elsewhere.

A new technological movement without the technology itself is just an idea sitting and waiting. Once the technology is present in the equation, movement forward can begin. This is how many of us see the head-mounted displays (HMDs) and smartglasses that have recently entered the augmented and mixed reality market — or are coming out in the next few months. This is a movement that will sweep over the world, changing everything in its path, and these are some of the people behind it.

I don't know how many of you had this experience in your youth, but when I was a kid, I used to actively think about what would happen if I suddenly woke up in a fantasy land, or were to pass through a portal into another space and time. I knew it wouldn't really happen, but when you're a kid, these can be important issues to you. So I slept with my glasses on every night, just in case. Photo from George Pal's The Time Machine.

With NFTs taking the art world by storm, it's a bit refreshing to know that you can enjoy world famous masterpieces in the comfort of your own home via augmented reality without emptying your cryptocurrency wallet.

The average business person likely recognizes Epson for its printers or even its projectors, not the futuristic AR wearables.

Why pay for a movie when you can get it for free? Thanks to Movies Anywhere, you can claim and download a video for your digital film collection right now at no cost. And getting your freebie flick couldn't be any easier.

One of the benefits of Blu-ray and DVD is the ability to share discs with friends and family without any hassle. Want to show off your favorite movie? Just lend them your copy. A digital movie isn't so kind, as it's typically locked to the account that purchased it. But now there is a way to share your digitally purchased movies with friends and family — and it won't cost you or them a dime.