
How To: Make easy baked ziti
When you want to feed a crowd without spending hours working in the kitchen, follow these steps to make an Italian dish that's sure to please the whole family.


When you want to feed a crowd without spending hours working in the kitchen, follow these steps to make an Italian dish that's sure to please the whole family.
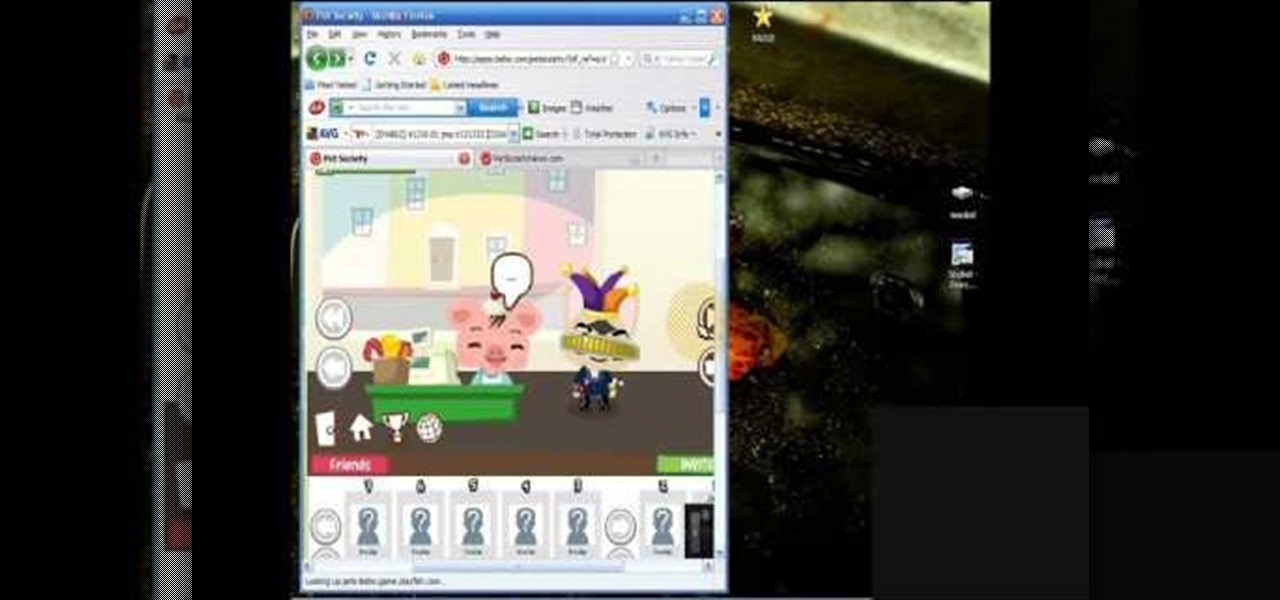
How to hack Pet Society! Pet Society cheats, tricks, hacks. Watch this video tutorial to learn how to hack gold in Pet Society (09/29/09).
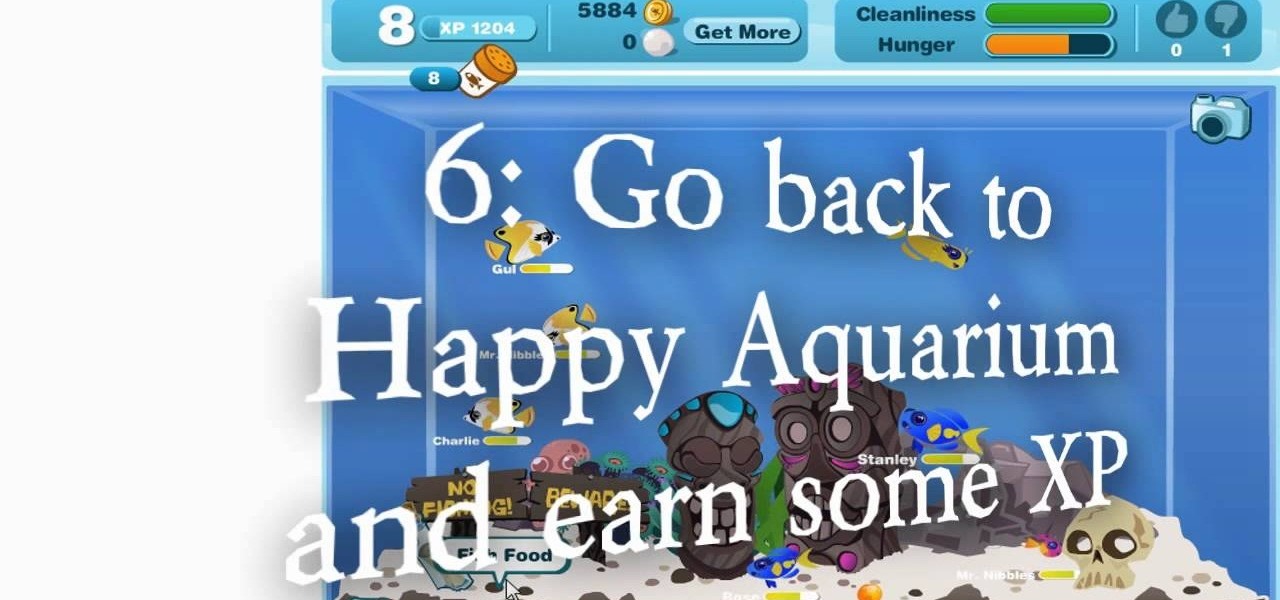
This might be an old hack for Happy Aquarium, but for some of you it may still work. Most of you will not be able to do this, but it's always worth a shot, right? It's a cheat from 9/29/09 (wow!—retro hack) for which you need Cheat Engine 5.4. Newer versions of Cheat Engine should work, too.

Don't hide in a cave when the market is down. Find stocks that will pay off when the bull makes its return.

All you need is a deck of cards and a friend to play the fun game of Crazy Eights. You Will Need
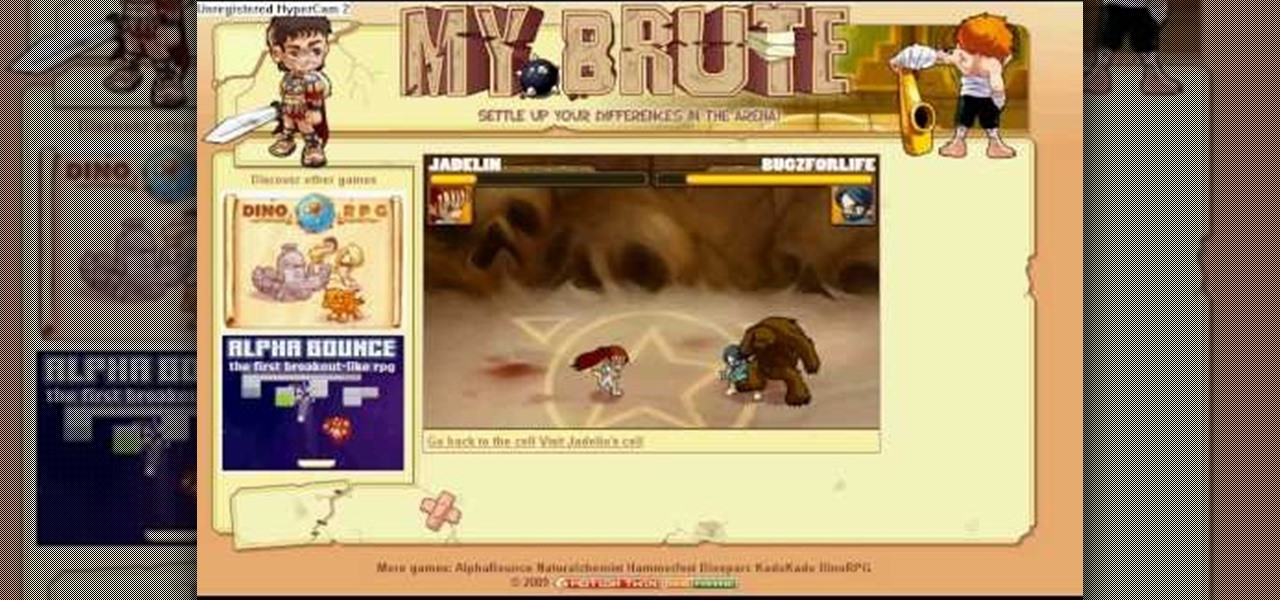
Here is a cheat guide to having more pupils or faster levels in MyBrute. You can play this game at least 5-10 minutes a day!

Brian Brushwood and Scam School give you another way to score free booze at the bar. Memorize a few configs and you'll hold the key to another unbeatable game and loads of free drinks!

Vegetables are the foundation of a healthy, balanced diet, many experts recommending 3-5 servings a day. When choosing your vegetables, it's always best to choose fresh; although, frozen and canned still have nutritional value and benefits as well. Also, look for vegetables that are bright in color like this red pepper, also carrots that are brightly orange and brightly-colored green broccoli. The brighter the color, the more nutrients that are in it. Try these tips for buying vegetables in t...

As you progress in the world of information security, you'll find yourself in situations where data protection is paramount. No doubt you will have files to hide and secrets to share, so I'm going to show you how to use the GNU Privacy Guard (GnuPG or GPG for short) to encrypt and decrypt as you need. GPG is a great open-source version of Pretty Good Privacy (PGP), a similar application used for encryption, but licensing and patent problems led to the development of GPG in its wake.

With the Consumer Electronics Show opening tomorrow, it’s going to be a ‘breaking news’ week here at Edit on a Dime. Stop by often for updates on the latest cheap and easy apps to make your video just that little bit better.

Only so much data can be passed through the network and to your computer's networking interfaces. This is limited by the amount of bandwidth you have. The more bandwidth you have, the faster your network connections will be. Not only this, but your transfers will be more parallel and distributed so that all of your speed isn't taken up by one transfer. When all of your bandwidth is sapped and unable to be used, this is called a denial of service, or a DOS.

If you've ever heard software piracy terminology being discussed, I'm sure the term KeyGens came up. KeyGens is short for key generator, which is a program that exploits algorithmic faults in software by generating software license keys that appear to be genuine. Normally used as a technique to protect the source code software and prevent piracy, a key generator exploits the key algorithm to effectively nullify the need for any software licenses. For example, we must try to find patterns in t...

If you've ever wondered how software pirates can take software and crack it time and time again, even with security in place, this small series is for you. Even with today's most advanced methods of defeating piracy in place, it is still relatively easy to crack almost any program in the world. This is mainly due to computer processes' ability to be completely manipulated by an assembly debugger. Using this, you can completely bypass the registration process by making it skip the application'...

Oh, teenagers. Maybe you would be better off planning a scavenger hunt for the screaming toddlers. Just kidding! Despite the mood swings, teens will enjoy a scavenger hunt more than younger kids. Some things to keep in mind, though:
Make money promoting yourself, build links and drive traffic. Yes thats is right you can get paid to promote yourself by using free to join sites that let you share revenue, I have included a list of sites that will allow you to build links to your online content or sites. this will aid in building your site authority as well as let you make some revenue to help you pay for your hosting fees ect.

F.A.T. Lab (Free Art and Technology) is a network of artists, engineers, scientists, lawyers, and musicians dedicated to the research and development of new technologies and creative media. They are "committed to supporting open values and the public domain through the use of emerging open licenses, support for open entrepreneurship and the admonishment of secrecy, copyright monopolies and patents."

53-year-old artist Scottish artist David Mach uses tens of thousands of matchsticks to create sculptures of animals, as well as religious and political icons. He first creates a plastic or fiberglass mold, and then inserts the matchsticks, one at a time. His work sells anywhere from $30,000 to $52,000... unless he sets the piece on fire, of course.
BrickLink is the Craigslist/Ebay/master aggregator of all LEGO commerce on the web. (Almost 100 million products currently for sale!)

100% functional LEGO ATM by Ronald McCrae. This bonafide brick bank performs the following functions:

Carly Waito's beautifully rendered oil paintings of minerals totally inspire me to pick up a brush and start painting.
Hello, hackies... Today i want to give you a simple but effective step-by-step guide to

There are two sets of baseball cards: A = Contains 7 top players.

Poker, Blackjack, Old Maid... take your pick. A marked deck will make you an ace at 'em all. For this cheat you need a Bicycle deck, a box cutter, keen eyesight and an excellent memory of the code. Essentially, you're carving a miniscule symbol for every card's value onto its back.

Let's take a step back in time to the Mesozoic era of WonderHowTo. Before the time of electricity, your mother and I used to follow step-by-step tutorials on how to make a Lockheed Martin F16...from papyrus.

Fist full of pennies weighing you down? This will certainly make your pockets lighter.
Unlike past Pixel releases, it appears Google isn't done with their current lineup. Rumors have it that Google plans to put out two new phones that act as budget variants for their existing devices. And based on the leaks, it looks like one of these variants might be better than its non-budget counterpart.

After building its business on virtual reality, Jaunt is leaving the technology behind to focus on building tools for creating augmented reality content.

In a leaked company memo, Snap CEO (and NR30 member) Evan Spiegel has made it clear that the future of the company lies not only augmented reality but also hardware that enables those AR experiences.

To quote MKBHD, cheap phones are getting good. Each year we are seeing manufacturers start to offer more for much less. This not only translates to cheaper flagship phones, but better budget phones. The latest example of this is the Alcatel 3V, which is redefining what you can get at $150.
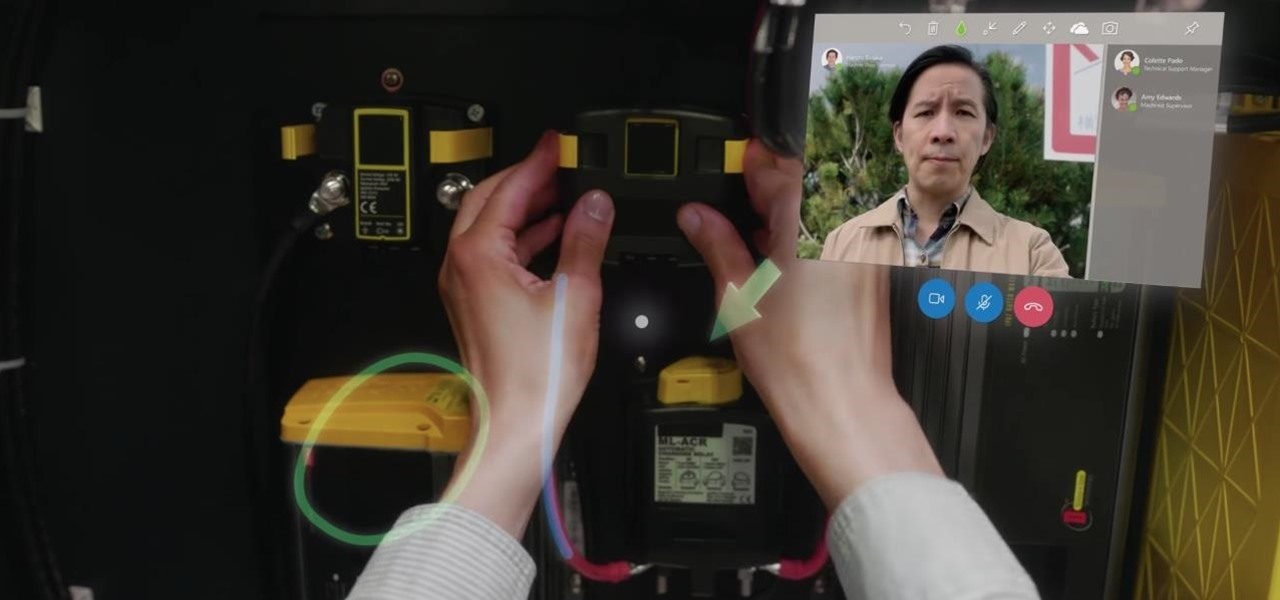
On Monday, at its annual Build developer conference, Microsoft revealed two new apps for the HoloLens apps.
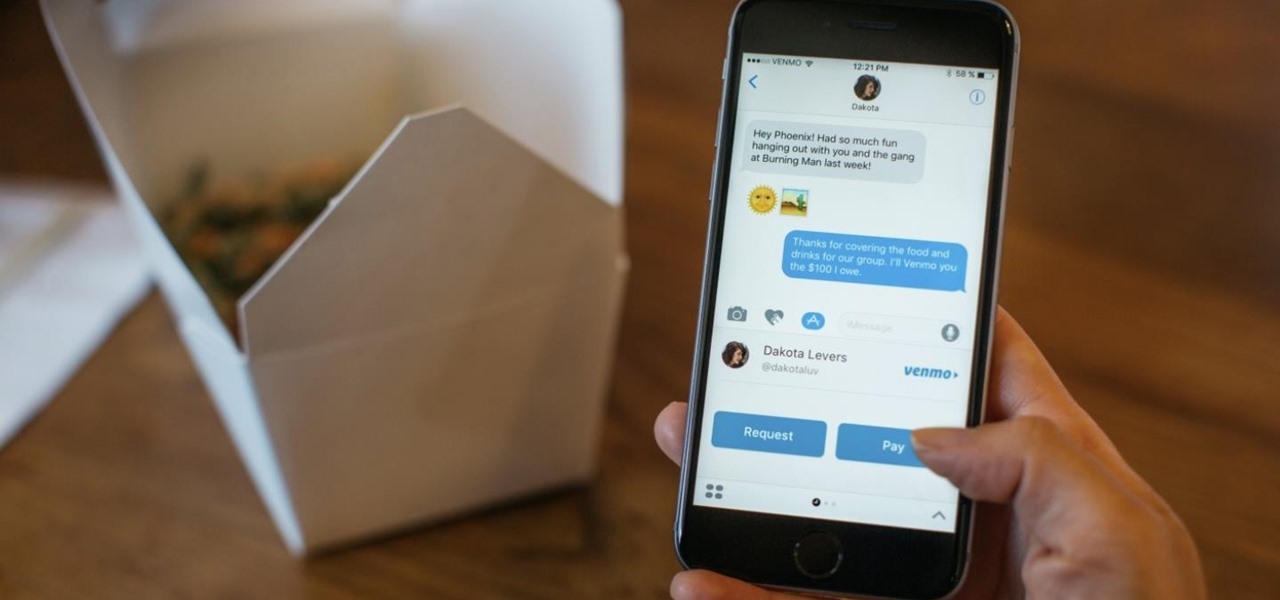
For $0.25 per transaction, PayPal will soon be allowing you to transfer money through their app that will get delivered within seconds rather than days.

Verizon launched the $80 unlimited prepaid plan this week and we've found that it actually isn't as limitless as they would have you believe.

The ride-sharing company Lyft has managed to secure $500 million in funding, which will certainly help its ongoing competition with Uber. According to recent reports, the cab firm is currently valued somewhere between $6.9 billion and $7.5 billion, but this still pales in comparison to Uber's estimated $70 billion valuation.
There's one thing that I've always liked about iPhones, and that's their centered digital clock in the status bar at the top of the screen. On Android, it's always on the right side by default, and there's no easy setting that lets you just change it to the center position. But if you have a Google Pixel XL, there's a simple modification you can perform to get exactly that—a centered status bar clock.
Some manufacturers, like Samsung and LG, have had split-screen multitasking on their custom versions of Android for years. But starting with Android Nougat, Google added this functionality to AOSP, which means that all phones and tablets running Android 7.0 or higher will now have a new multi-window mode.

Hello again, and welcome back to another tutorial on functions, this time, covering recursion. What Is Recursion?

Tahini: it sounds like the name of a high-end fashion designer... or perhaps a variation on a two-piece swimsuit. But this "weird ingredient" is actually a delicious and nutritious paste made from toasted sesame seeds and oil.

Programming is an essential thing in hacking/pentesting, and at times, I do not feel that it is being addressed enough here, at Null-byte. I understand that this is a forum dedicated for hacking, but I'll address some of the stuff I feel is muy importante about programming. I am not a professional programmer, but I do have experience and I do want to share some of the stuff professionals have taught me.

If your PC setup includes a mouse and keyboard, you'll be happy to know that most of the touchscreen-first features of Windows 8 have gone by the wayside in Windows 10. Where it once required awkward gestures to access key features, Windows now recognizes when you're using a traditional desktop or laptop, then responds by making sure that all features can be easily discovered with clickable buttons and menu entries.

Welcome back, friends! Many times, businesses, friends, and family will lock their zip files with a password to keep their files secure. It is reasonable, and understandable. Well, thanks to hackers, there are many ways to get past this wall of security.