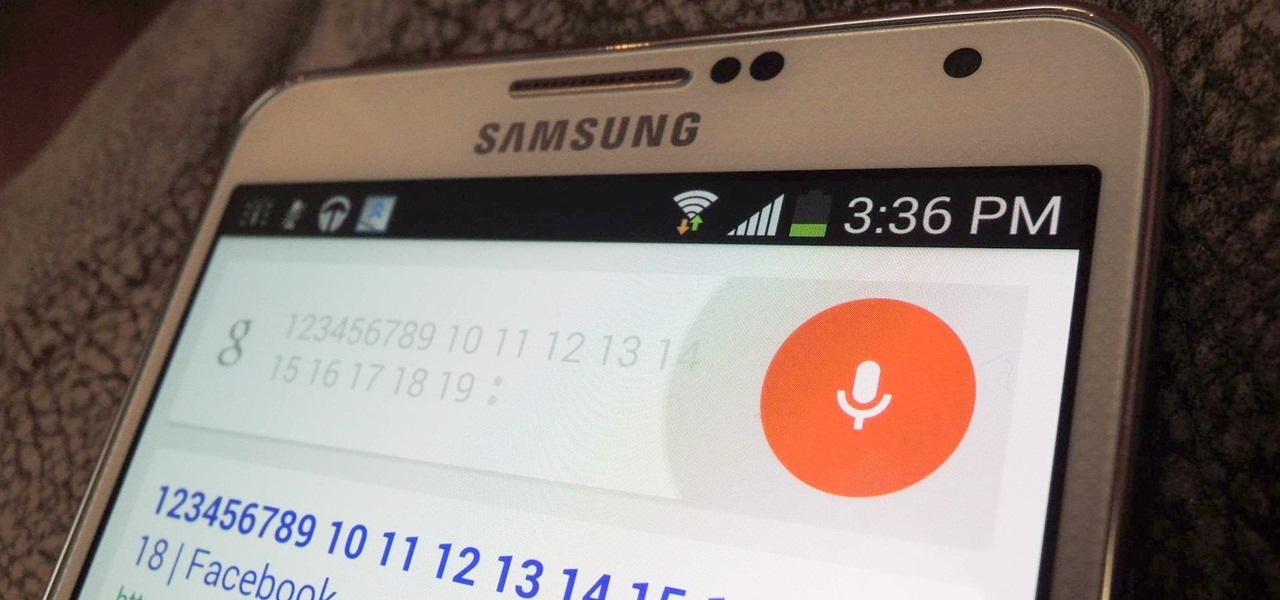
When Google first introduced Android 4.4, the most glaring user-facing change was a new trend towards transparency. The stock launcher, originally exclusive to the Nexus 5, had transparent status and navigation bars and its app drawer added a touch of transparency.

When I'm showing off my HTC One, the first thing I do is unlock my device and say, "OK Google". It may earn me a weird look or two, but in the end people are amazed by the voice recognition and automation of the Google Now Launcher.

Update: April 24, 2014 Looks the the one day availability was a precursor to a wider launch, as now anyone can buy a pair of the Glass Explorer Edition without needing an invite. Check out Google's Glass Shop for some easy ordering, still with the $1500 price tag.

Earlier this morning, Twitter announced (through a tweet, naturally) that it has acquired Cover, roughly a minute after Cover made the same announcement. Cover Lock Screen, a lockscreen replacement app, has been vastly popular during its first year. The app places relevant shortcuts on your lockscreen that adapt to your habits, so whether you're at home, work, or in the car, you'll find the apps you use the most in these situations readily available for you. For more information on Cover, inc...

In direct competition with Pandora, iTunes Radio, and Spotify, Samsung has just launched Milk Music—a strangely named, yet completely free music streaming service for Android.
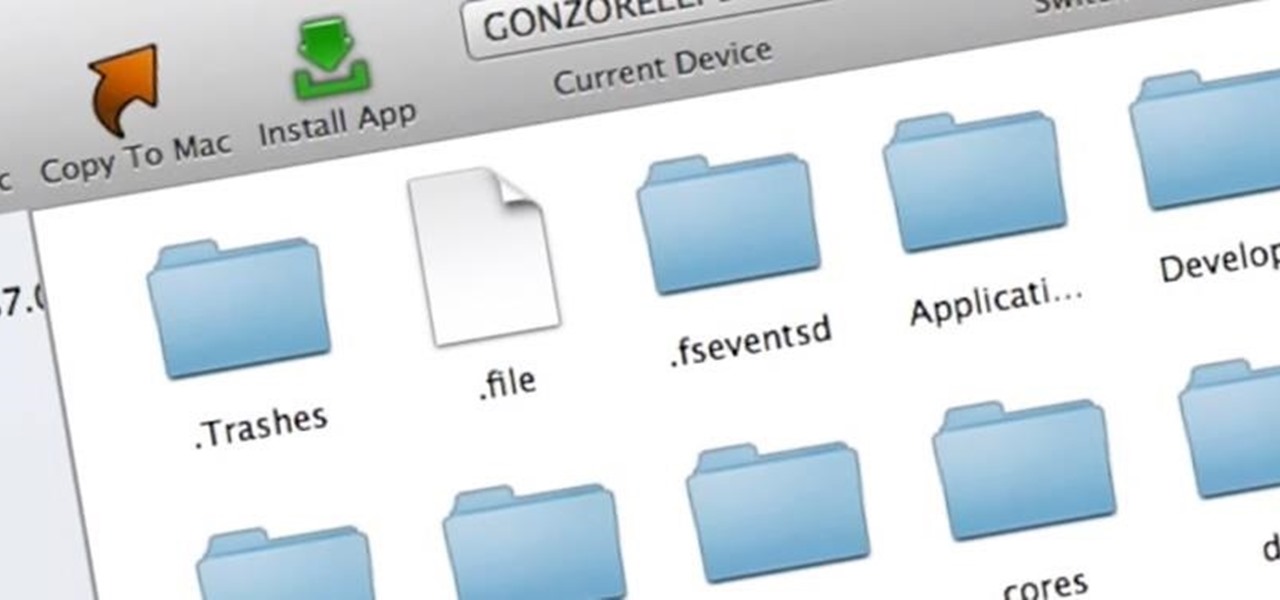
There are a ton of great mods and tweaks available in Cydia, but occasionally there will be one you want to install that hasn't quite made it into one of the main repositories yet. If you're not patient, it can be still be installed by manually placing the .deb file directly onto your device and installing it with iFile.

Exclusive to only a handful of smartphones, including the Nexus 5, the Google Experience Launcher allows us to open Google Now simply by speaking out a certain phrase, at any time—dubbed a "hotword."

I know all of you softModders love these little modifications, like enabling the hidden battery percentage on the Nexus 7 or getting the exclusive Google Launcher on your Nexus, so here's an easy one that lets you hide the soft-keys from your tablet, which will actually expand your screen to look a little bit longer.

Full screen mode, also called immersive mode, is one of the most popular features on CyanogenMod, but it's almost exclusive to CM and other custom ROMs. What this feature does essentially is remove the Status bar and soft keys from your screen, creating a more mesmeric feel.

Sometimes, taking a picture of your friend doing a crazy stunt just doesn't suffice. Getting the progression of the stunt in one image does!

For now, the redesigned and fresh-faced Android 4.4 KitKat is exclusive to the new Nexus 5, though it will be rolling out to other Google (Nexus 4, Nexus 7, Nexus 10) and Google Play Editions (Samsung Galaxy S4, HTC One) devices in the next week or two.

With its awesomely enormous size, the Samsung Galaxy Note 2 can at times be difficult to navigate when you only have one hand free—especially if you have really small hands.

Are you constantly traveling? Well, as a Hilton HHonors member, you can enjoy special treatment at all of their hotels and resorts. It's free to register, but the difficulty lies in climbing up their membership level. To reach Gold elite status, Hilton HHonors requires that you have a minimum of 20 stays, 40 nights, or 75,000 base points—all in one year. While this may very will be easily attainable for those with jobs that revolve around traveling, it's almost damn near impossible for the re...

In an effort to appease iPhone fans eager for an NFC-equipped device, an option that is available on many other smartphones, Apple created Passbook, their version of a digital wallet.

Without an available browser, it is challenging to enjoy media on your Nvidia Shield outside of the apps on the Play Store. It is because of this limitation that file transferring is vital, as only then can you enjoy your movies and music.

Privilege escalation is one of the essential skills a hacker can have and often separates the newbies from the pros. With a continually changing landscape and a plethora of exploits out there, it can be a problematic aspect of any attack. Luckily, some tools can help expedite the process. Linux Exploit Suggester is just one of many to help you get root.

Stadia is a lot like an Xbox or PS4, except there's no console — the games just stream from Google's servers to your phone, computer, or TV. But Stadia is limited to Pixel phones for right now, and when Google does expand support, it will still only be for select phones. Thankfully, there's a workaround for that if you're rooted.

When it comes to customizing Android, there's no better way to make it your own than by installing a custom ROM. You gain new features that were not accessible on the stock firmware that came with the phone, and you get complete control over how your system looks and feels. But there's definitely a learning curve.

Websites are often misconfigured in ways that allow an attacker to view directories that are not ordinarily meant to be seen. These directories can contain sensitive information such as private credentials or configuration files that can be used to devise an attack against the server. With a tool called Websploit, hackers can scan targets for these hidden directories without difficulty.

Hundreds of Windows 10, macOS, and Linux vulnerabilities are disclosed every single week, many of which elude mainstream attention. Most users aren't even aware that newly found exploits and vulnerabilities exist, nor that CVEs can be located by anyone in just a few clicks from a selection of websites online.

One of the things that sets a seasoned hacker apart from the script kiddies is the ability to effectively sneak past antivirus defenses when executing an attack. One way to do this is to use custom shellcode in an exploit. Not everyone is an expert at writing shellcode, but luckily there's an easy way to do this that is both quick and effective.

When it comes to the sub-$250 price range, the new Nokia 5.1 might be the perfect phone. Of all the new models announced at Nokia's event in Moscow, the Nokia 5.1 offers the most with the least compromises. For a third of the cost of a flagship, you get a phone with a premium build, solid specs, and good battery life.

Google collects an enormous amount of personal data. While some of this data is used for targeted ads, others tidbits of info such as our location are used to improve our mobile experience. While it is natural for us to distrust Google's intentions, by allowing their data collection, we can add new functionality to our favorite apps.

With Mobile World Congress fast approaching, all eyes in the industry are set on Samsung's Galaxy S9 announcement on February 25. While leaks and rumors about the S9 and S9+ have been flooding in for quite some time, we're getting a much clearer picture of these handsets as the announcement draws near.

IFTTT is an application that allows you to automate certain tasks on your iPhone or Android. It can communicate with a myriad of apps and services on your phone by creating applets that perform actions automatically — actions you'd normally have to do manually. Finding those applets, however, can be a little difficult.

It's the holidays. That means new smartphones, and new smartphones mean new cases. Whether it's the Galaxy S8, the iPhone X, or the Note 8, your new phone deserves to be protected. Of course, good cases can get pricey fast. That's what Black Friday is for, of course.

HTC is heading in a strange direction lately. Instead of releasing just one flagship in the spring season, they released two top-tier phones, with one having last year's specs and both having last year's design. They were also supposed to manufacture both the Pixel 2 and 2 XL, but Google was unimpressed by the HTC-made Pixel 2 XL and looked to LG for the bigger device. Now it seems, HTC isn't finished yet.

Since its debut 9 years ago, the iOS App Store has always had roughly the same functionality: Featured apps, categories, top charts, a search function, and a place to update your apps. But starting with iOS 11, that's all changing — drastically.

Every Friday, Next Reality reviews the latest headlines from the financial side of augmented and mixed reality. This Market Reality column covers funding announcements, mergers and acquisitions, market analysis, and the like. This week's column is led by two companies cashing in on visual inputs.

When it comes to modding an Android device, a custom kernel can take you farther than almost anything else. Most offer the ability to overclock your processor for performance gains, change your CPU governor, or even under-volt to increase battery life, among other features.

With some of the groundwork out of the way in getting a Mac set up for hacking, it's time to start looking at toolboxes. Our first toolbox is Git, which will be used throughout future tutorials.

Welcome back, my greenhorn hackers! A few years back, Microsoft implicitly recognized the superiority of the Linux terminal over the GUI-based operating system by developing PowerShell. Since Windows 7, every Windows operating system has had PowerShell installed by default, and they even made PowerShell capable of running Linux commands on Windows!

Welcome back, my rookie hackers! The Golden Fleece of hackers is to develop a zero-day exploit, an exploit that has not been seen by antivirus (AV) software or and intrusion detection system (IDS). A zero-day exploit is capable of skating right past these defenses as they do not contain a signature or another way of detecting them.

Hello partners, first of all I would like to thank all those who have sent me positive feedback about my posts, to say that I'm always willing to learn and teach. I'm also open to answer the appropriate questions.

Welcome back, my greenhorn hackers! Throughout this series on Metasploit, and in most of my hacking tutorials here on Null Byte that use Metasploit (there are many; type "metasploit" into the search bar and you will find dozens), I have focused primarily on just two types of modules: exploits and payloads. Remember, Metasploit has six types of modules:

Welcome back, my fledgling hackers! Over the years, we have examined multiple ways to own, exploit, or compromise a system. On the other hand, we have not spent a lot of time on denial-of-service (DoS) attacks.

Welcome back, my greenhorn hackers! Many new hackers come from a Windows background, but seldom, if ever, use its built-in command-line tools. As a hacker, you will often be forced to control the target system using just Windows commands and no GUI.

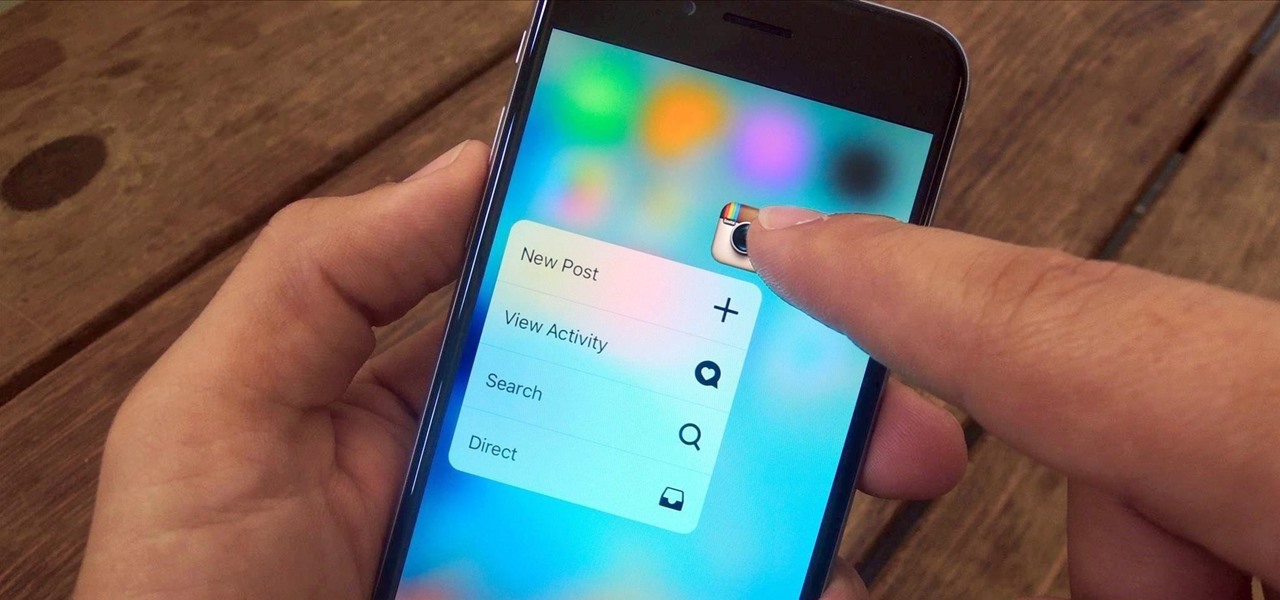
3D Touch is a new feature on the iPhone 6S and 6S Plus that's reinventing the way we interact with our smartphones. With just a little bit of added pressure when tapping on the display, you can perform Quick Actions from an app's home screen icon, "Peek" at emails, stories, and photos in-app, as well as perform other app-specific gestures. Since 3D Touch is such a new concept, here are some of the apps that currently support it, along with the shortcuts you can use.

Cheap Chinese knockoffs have been around for ages, but recently, skyrocketing demand has led to a massive influx of counterfeit smartphones. Sellers on Craigslist seem to have no trouble getting ahold of these fake devices, then passing them off as the real deal and turning a solid profit before vanishing into thin air. This type of scam tends to happen even more frequently after Apple launches a new iPhone or Samsung debuts a new Galaxy.