In this video tutorial, Chris Pels will show how to include JavaScript to an ASP.NET page for use on the client page to provide a richer and more robust user experience. First, see how to include JavaScript directly within an ASP.NET page and reference the script from within HTML page elements. Next, see how to abstract the JavaScript to an external JavaScript file which offers the advantage of being cached by the browser and can be used by multiple pages. Lastly, learn how to add JavaScript ...

The Geminid meteor shower 2010 is tonight, climaxing sometime between midnight and dawn Tuesday. Usually, the Geminid meteor showers in December are awesome spectacles, one of the most intense meteor showers of the year, but this year the moon will be out until after midnight, lessening visibility. But just because you can't see the meteor shower this year, doesn't mean a meteorite or two didn't sneak into Earth's atmosphere, hurdling to the ground, waiting for you to find it. So, get your me...

Hydrazine sulfate has many uses, but most notably, it's been used under the trade name of Sehydrin, a treatment for anorexia, cachexia and some even think cancer. But for we DIY chemists, it's useful for something entirely different— as a substitute for the more dangerous pure liquid hydrazine in chemical reactions. NurdRage shows you how to make it via some hypochlorite and the Ketazine process.

This week, the beginning of an epic legal battle was set to begin between augmented reality players Magic Leap and Nreal, the small China-based startup accused by the former of stealing trade secrets.

With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassing antivirus software and Windows Defender.

Hello partners, first of all I would like to thank all those who have sent me positive feedback about my posts, to say that I'm always willing to learn and teach. I'm also open to answer the appropriate questions.

With just one line of Ruby code embedded into a fake PDF, a hacker can remotely control any Mac computer from anywhere in the world. Creating the command is the easy part, but getting the target to open the code is where a hacker will need to get creative.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

At Facebook's first Communities Summit, admins from top Facebook groups assembled to discuss tools to better manage and optimize their members. Here, Facebook CEO Mark Zuckerberg announced that these changes fuel the company's shifting focus from connecting the world to uniting it.

What's up guys? Welcome to a sort of general walkthrough on how one might approach a reversing and analysis on a crypted malware. This is by no means a universal technique so don't assume that this will occur in every scenario, it's more of a demonstration than anything really.

Welcome back to control structures, part two featuring the three types of loops. Here we go! What Is a Loop?

Kung fu is an ancient Chinese martial art that combines technique, balance and power into an effective fighting style. Learn several beginning kung fu combinations with tips from a professional kung fu instructor in this free martial arts video series.

Aikido has countless wrist grab forms and techniques for any method of martial arts self defense someone might need to call upon. Learn many of these tips from an Aikido expert in this free video clip series.

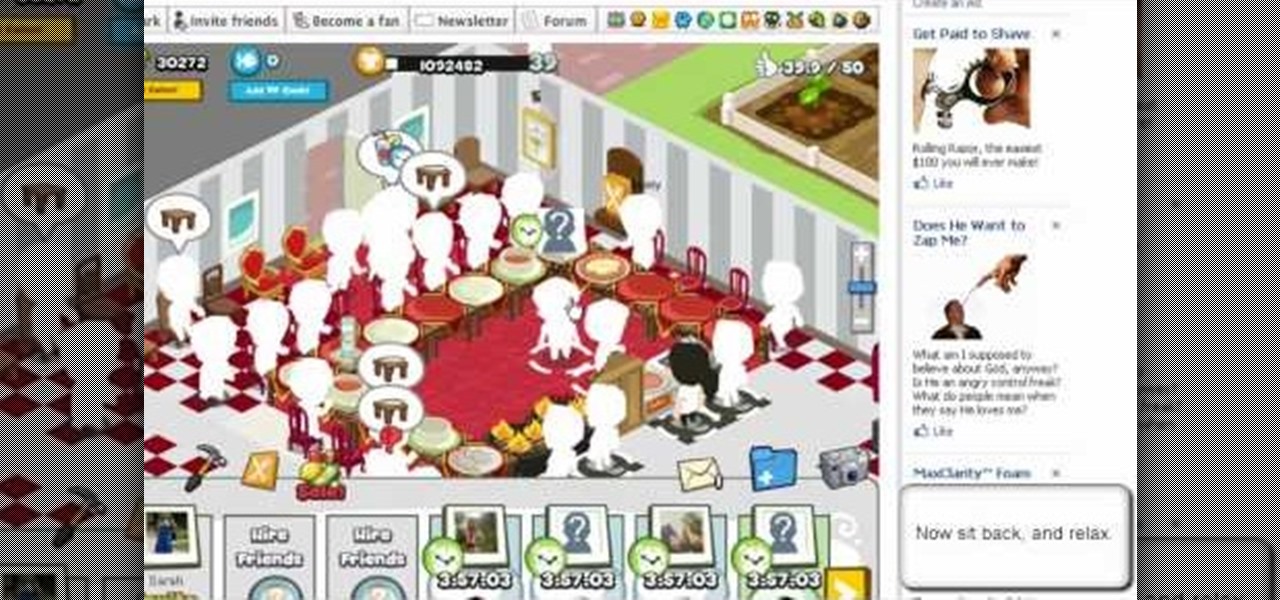
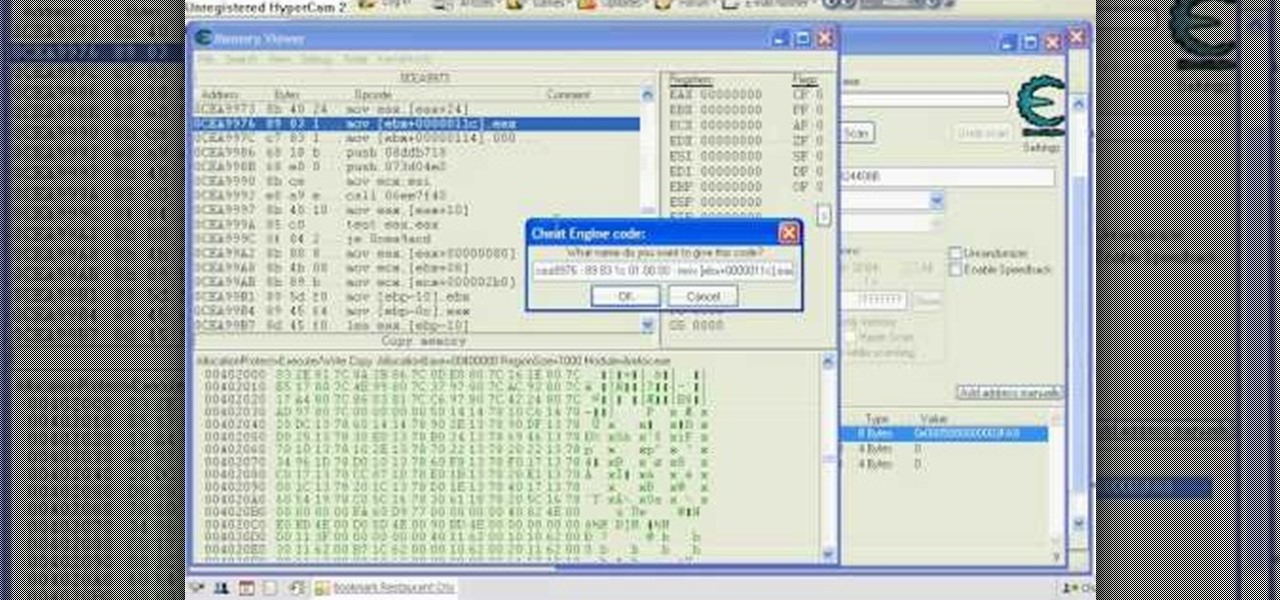
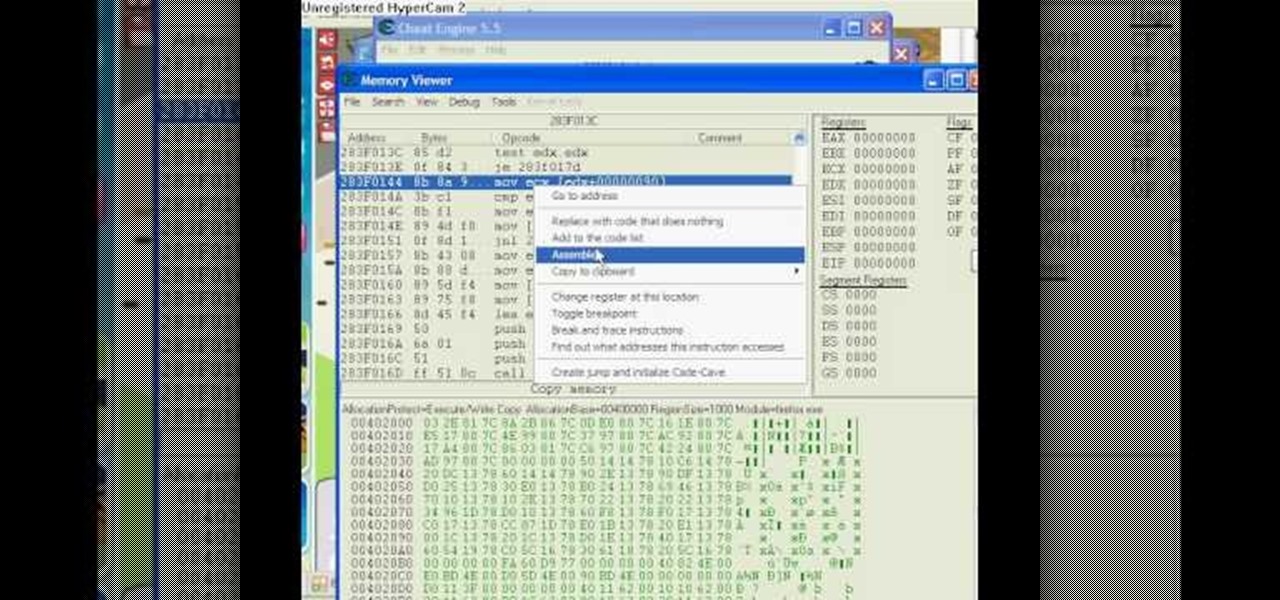
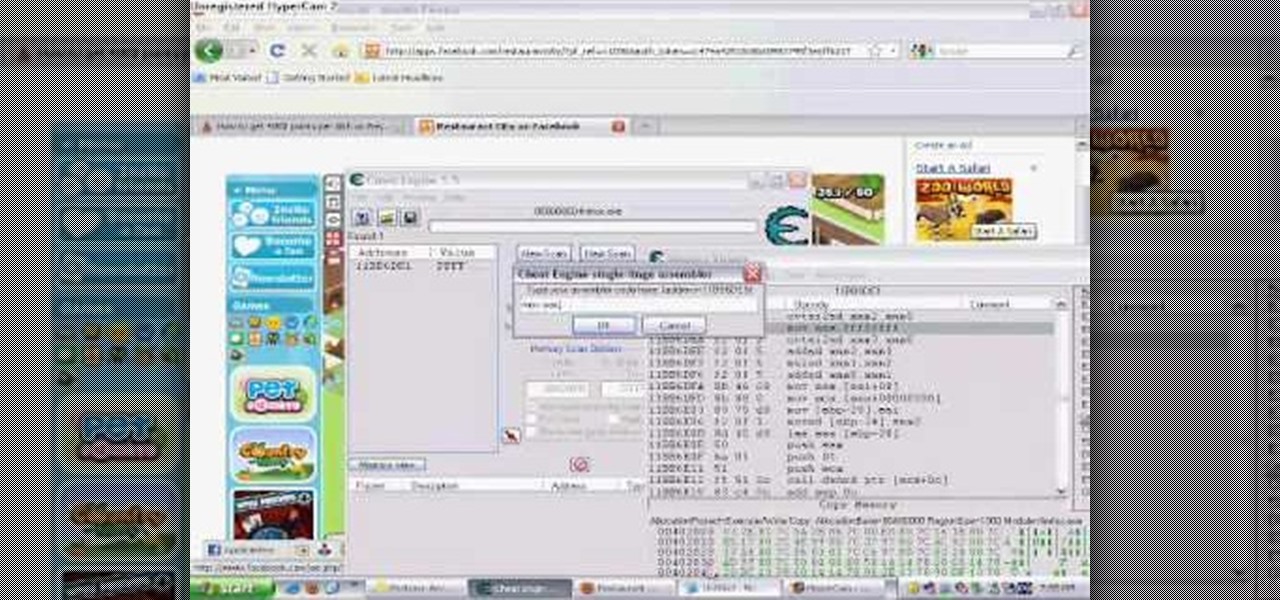
Want to be the Donald Trump of Restaurant City? Watch this video tutorial to learn how to hack Restaurant City (02/21/10) with Cheat Engine 5.6.

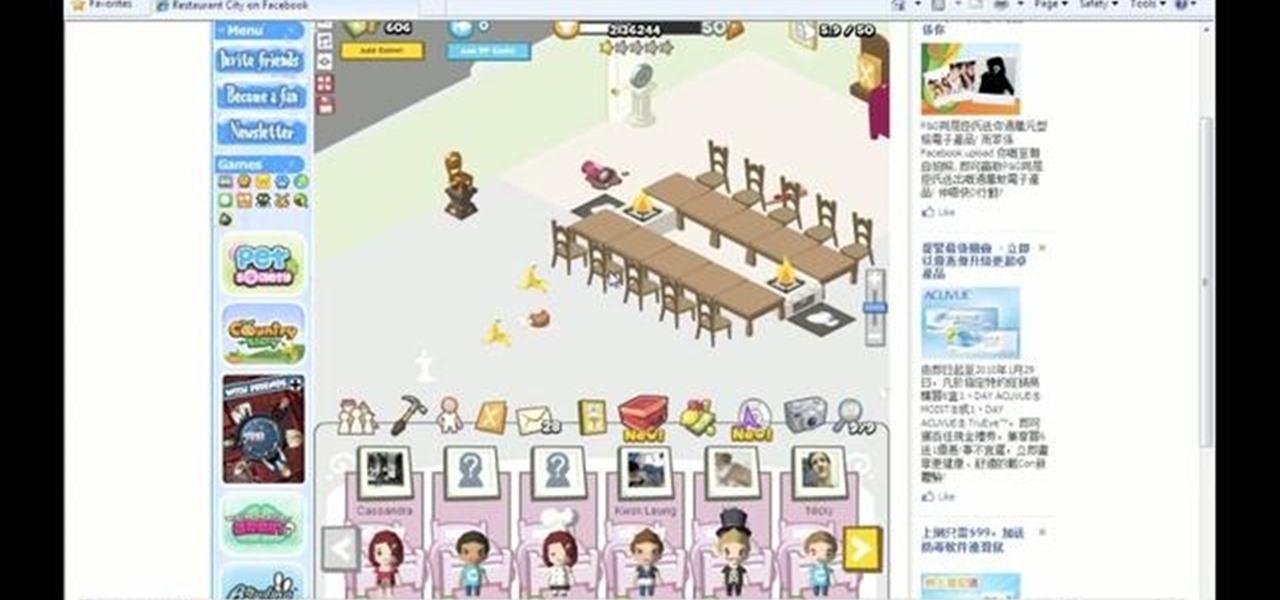
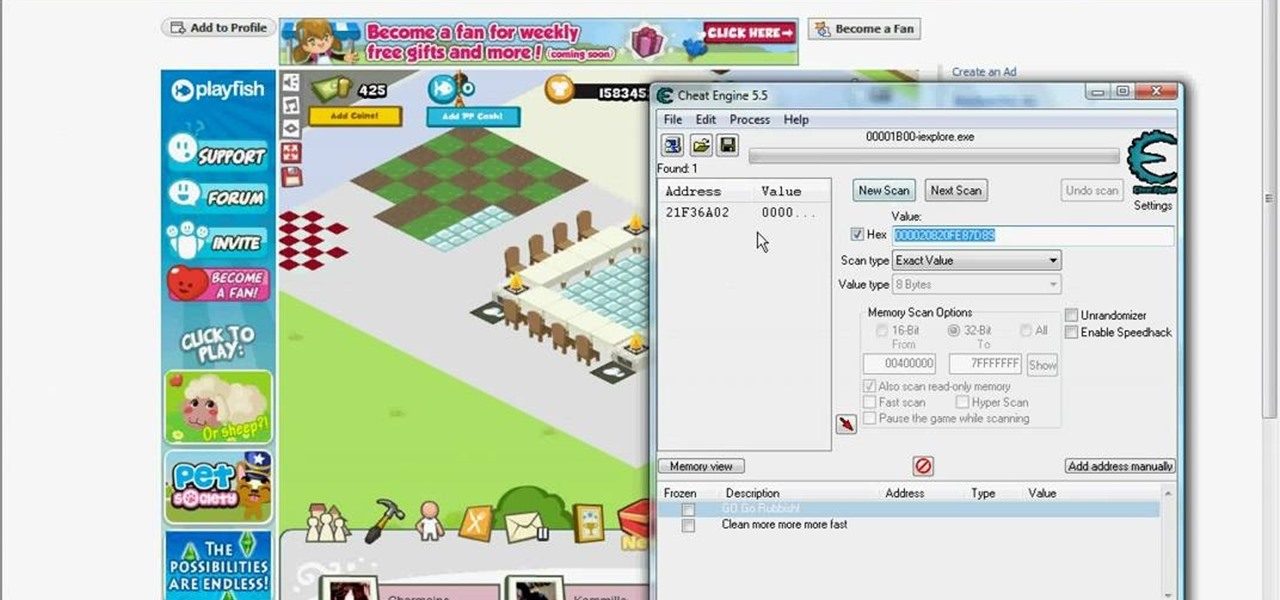
Want a pile of coins, Scrooge McDuck style? Watch this video tutorial to learn how to hack Restaurant City (01/08/10) with Cheat Engine 5.5 for unlimited free money.

This is the Double Pointer Coin Hack for RC. The tools you need for this hack are Cheat Engine 5.5, Adobe Flash Player 9 or 10, Mozilla Firefox or Flock, and Mouse Recorder.

This is a Piaip's and Cheat Engine hack for RC. Restaurant City is a Facebook game that allows you to create and manage your own virtual restaurant. Watch this video tutorial to learn how to hack Restaurant City: Garbage Guru trophy (11/15/09).

Restaurant City is a Facebook game that allows you to create and manage your own virtual restaurant. Watch this video tutorial to learn how to hack Restaurant City coins (11/12/09). You need Cheat Engine 5.5, RC Tools 5.1, and RC Tools Online.

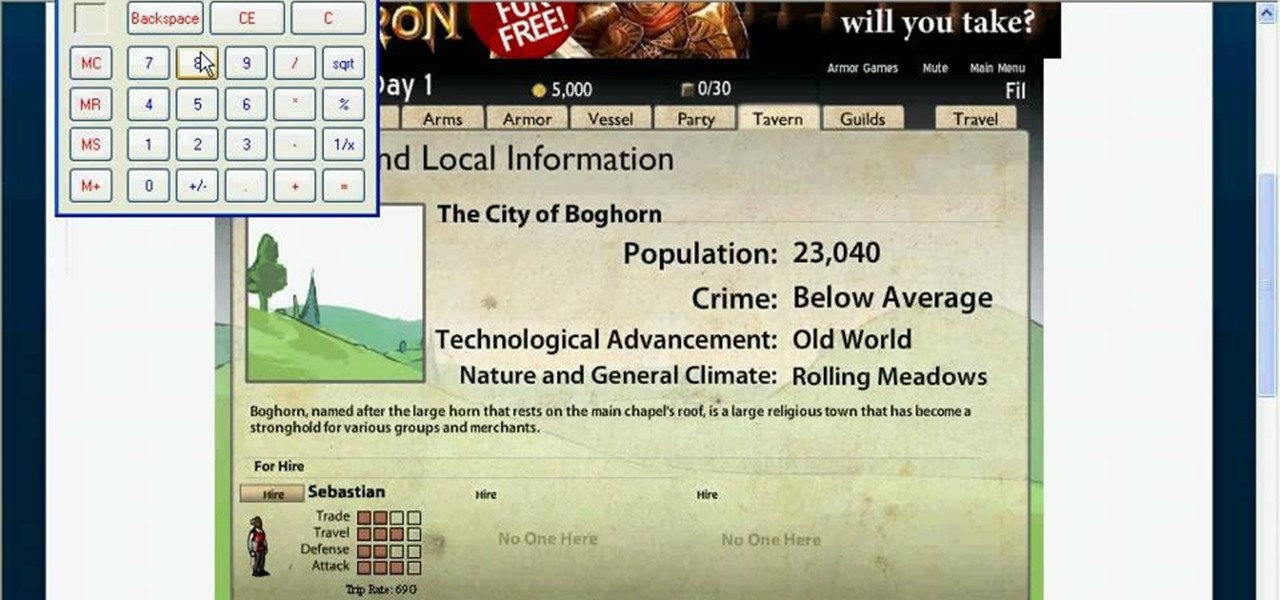
Frontier is a flash game from Armor Games. Learn how to hack Frontier with tricks and cheats. Watch this video tutorial to learn how to be rich on Frontier with Cheat Engine (09/13/09). See how to get an infinite amount of gold on Frontier.

You can get strong ripped abs by letting your inner child loose! By combining playground exercises and cardio you can have washboard abs that you are proud of. This video shows how to properly execute playground type exercises such as pull-ups to strengthen your arms and push ups to work your arms, back and chest. Follow along to find other quick and easy exercises that you can incorporate into your every day life to get the body you've always desired!

Knowing how to properly set up your mounts for cheerleading will help you execute your stunts safer and better. Learn how to do some stunt mounts in this video tutorial.

kicks since they require greater balance and strength than basic kicks. Learn kung fu jump kicks in this free video series on kung fu training.

The line dance is a dance with repeated sequence of steps in which a group of people dance in one or more lines, all facing the same direction, and executing the steps at the same time. Line dancing's popularity grew out of the 1970's, when the country-western dance continued to explore and develop this form of dancing.

The line dance is a dance with repeated sequence of steps in which a group of people dance in one or more lines, all facing the same direction, and executing the steps at the same time. Line dancing's popularity grew out of the 1970's, when the country-western dance continued to explore and develop this form of dancing.

Learn how to practice quick decision making (pass or shoot) when on the high post and establish good basketball game rhythm. Videos two through four cover when and how to execute each option: jump shot, seal the post (pass the ball down to the player at the low post), and swing the ball (after setting the pick and sealing the post).

Compromised uTorrent clients can be abused to download a malicious torrent file. The malicious file is designed to embed a persistent backdoor and execute when Windows 10 reboots, granting the attacker remote access to the operating system at will.

When OnePlus announced their partnership with T-Mobile and the deal the magenta carrier is set to offer, mouths dropped. But as usual, this deal comes with some caveats. The bulk of these will hurt the folks who love to root, something a large portion of the OnePlus community enjoys doing.

Backdooring a powered-off MacBook is easy when a few minutes of physical access is allowed. That attack works well if the hacker also shares a Wi-Fi network with the victim, but this time, I'll show how to remotely establish a connection to the backdoored MacBook as it moves between different Wi-Fi networks.

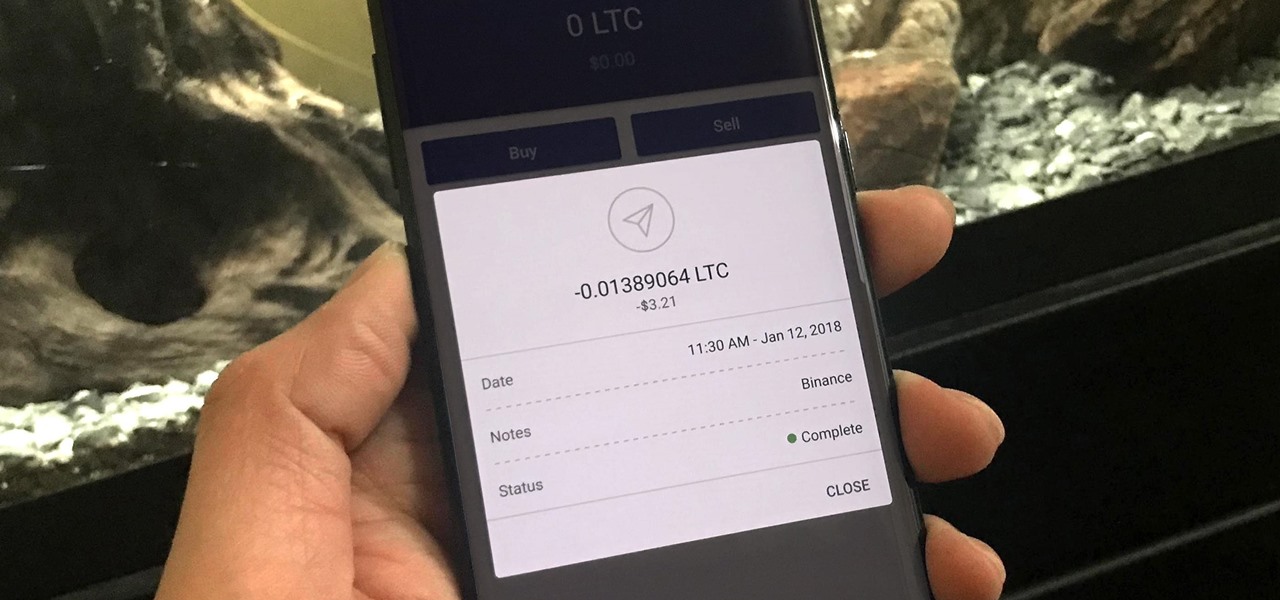
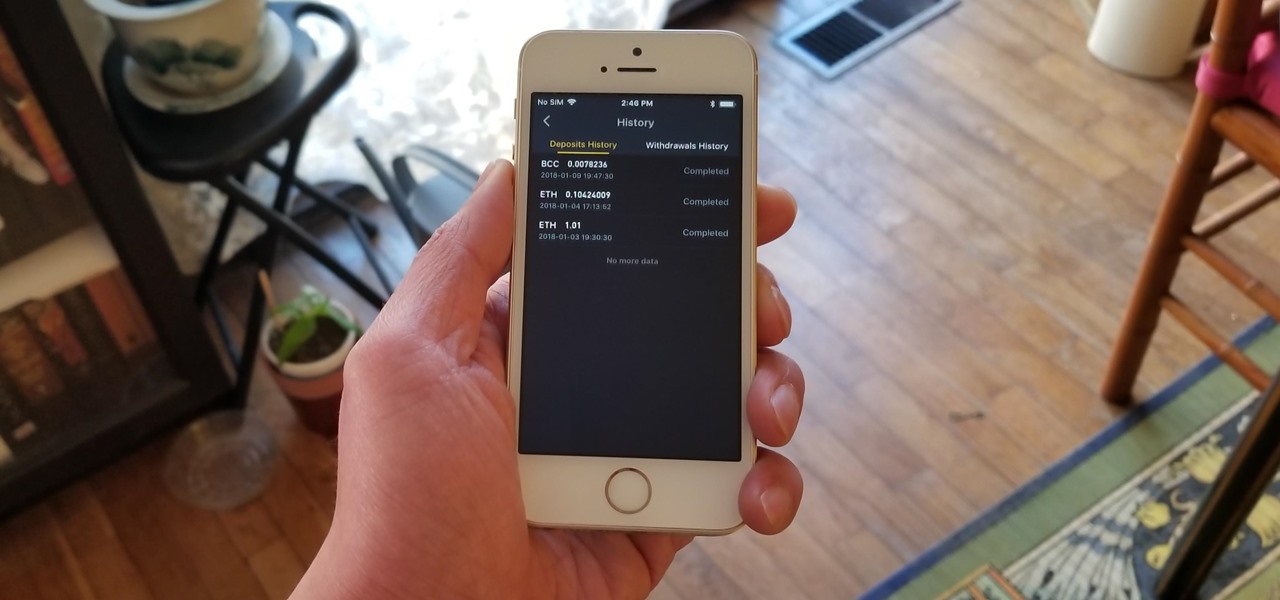
The most convenient way for US users to buy Ripple (XRP) or Stellar (XRM) is through Binance. However, you can't deposit money directly into this app, but you can deposit cryptocurrency like ether or bitcoins to buy other alt-coins. The easiest way to do that is by using Coinbase, the most popular cryptocurrency app.

As cryptocurrencies gain mainstream acceptance, it's not far-fetched to think that we'll one day be able to buy alt coins like Ripple (XRP) and Stellar (XLM) using debit cards and bank accounts. Until then, we'll have to rely on using bitcoins and ethereum to buy digital coins. Thankfully, depositing and withdrawing cryptocurrencies with Binance is relatively hassle-free.

In a previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when a Microsoft Word document is opened. The biggest challenge of this attack is that it requires getting the user to agree to a pop-up prompt. Fortunately, since I posted that article, many new obfuscation techniques have been discovered to make this easier. Today, we explore and combine some of them to make the ultimate hidden DDE attack.

In our previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when an MS Word document is opened. Because Microsoft built DDE into all of its Office products as a way to transfer data one time or continuously between applications, we can do the same thing in Excel to create a spreadsheet that runs malicious code when opened. The best part is, it will do so without requiring macros to be enabled.
Hello everyone! This is my first attempt at a tutorial here. There are a couple great assembly tutorials here, and I wanted to toss my coin in the fountain.

Welcome back, my hacker novitiates! There are many ways to hack databases, and most of these techniques require SQL injection (SQLi), which is a way of sending SQL commands back to the database from a web form or other input. In this tutorial, we will use SQL injection to get access to the underlying server. So instead of getting access to the database and its data, we will use the database as an intermediary to gain access to the underlying server.

I'm sure that many of us have heard of that nasty Shellshock vulnerability, but not very many people know how to exploit it. Try these few tricks on vulnerable websites!

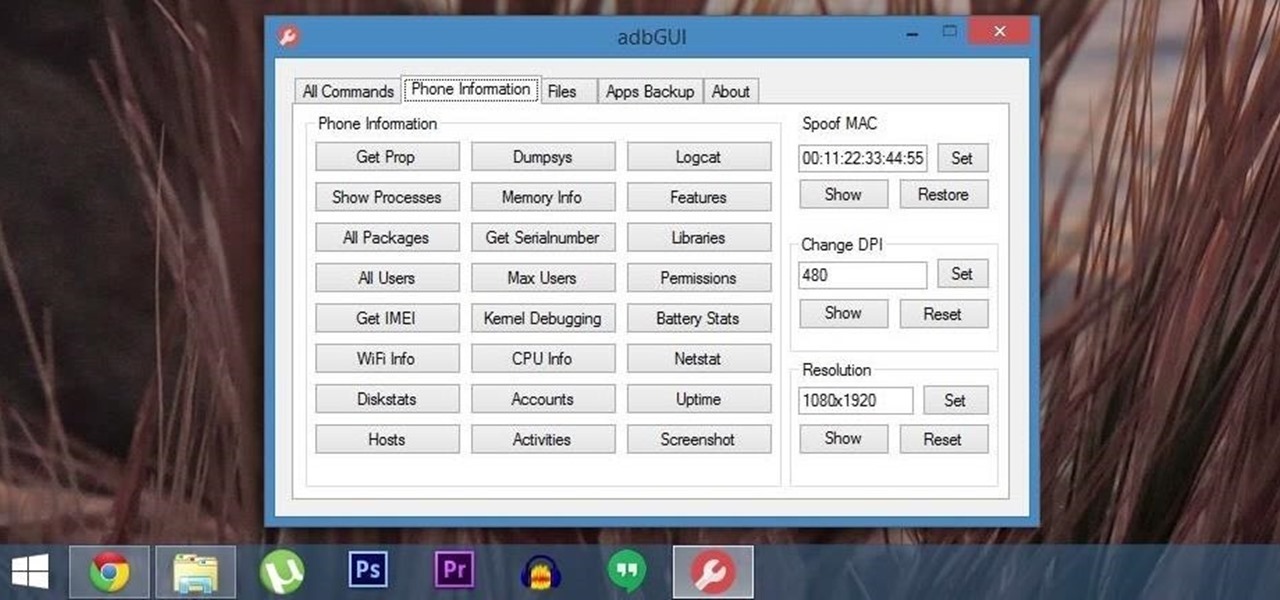
Android Debug Bridge (or ADB for short) serves as a remote terminal interface for executing shell commands on any Android device. Put simply, ADB lets you send commands from your computer to your phone or tablet, some of which would require root access if they were performed on the Android side of the connection.

If you forgot about April Fool's Day, you're going to have to get creative if you want to pull off some not-so-predictable pranks last minute. To help you with that, in this video you'll learn how to set up and execute 5 of the best last-minute April Fool's Day pranks. April 1st will still be a fun day for you, your friends, and family... just watch!

If you've ever attempted to report a bug to a developer, no doubt you've heard the response, "Get a logcat." This is infinitely important to a developer because of the fact that a logcat captures a full report of every command that was recently executed on your Android device, and it allows them to see exactly where something went wrong.

Ah, Halloween—the funnest, but scariest day of the year. You don't just dress up and go door to door asking for candy—it's the best day to pull off scary/spooky pranks.

Want to know how to get 4000 gourmet points per dish in Restaurant City? Cheat Engine, that's how. With Cheat Engine, it's super easy to hack RC for gourmet points, so see for yourself.