
How To: Hack Restaurant City EXP (12/04/09)
First download Cheat Engine 5.5. Once you have CE 5.5, you're ready to hack Restaurant City experience. EXP is hard to earn, but not with Cheat Engine… hack it.


First download Cheat Engine 5.5. Once you have CE 5.5, you're ready to hack Restaurant City experience. EXP is hard to earn, but not with Cheat Engine… hack it.
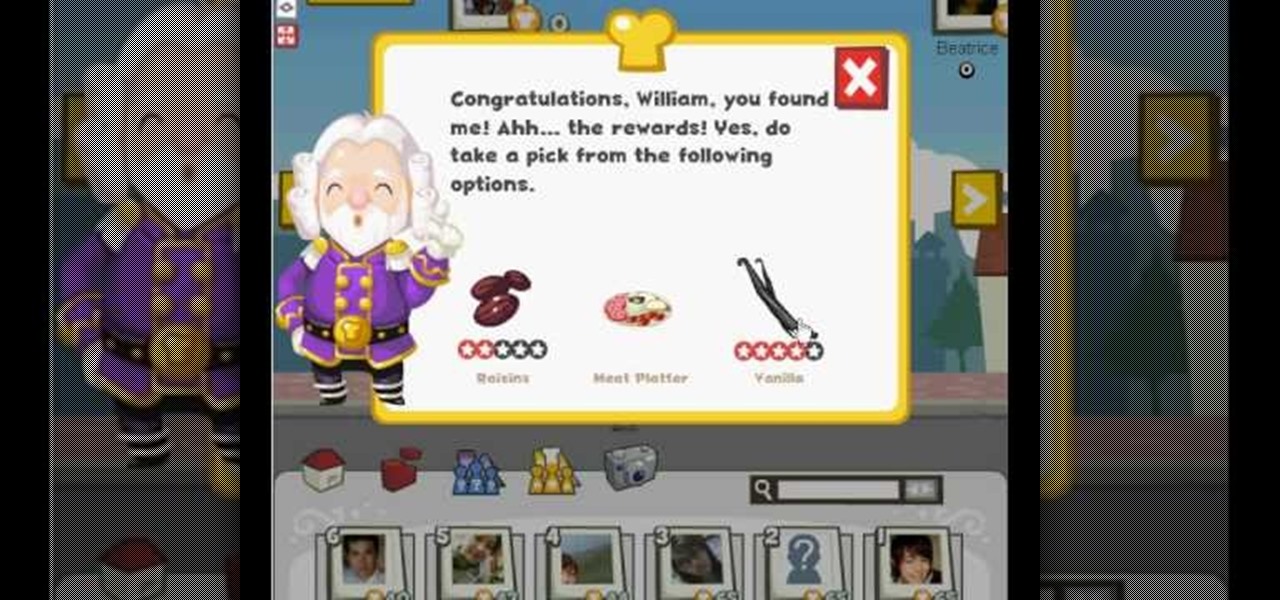
With this Restaurant City hack, you'll find the Gourmet King and get a choice between the following rewards; raisins, met platter, or vanilla. It's pretty simple to do, as long as you have Piaip's RC Hack v2.22.
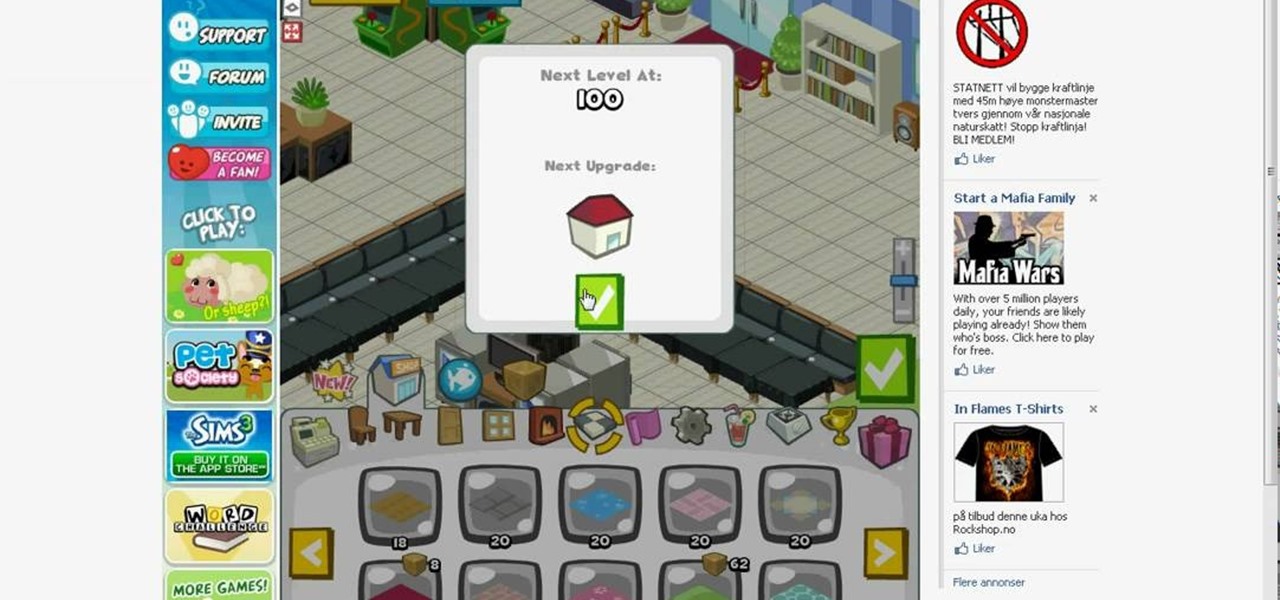
Restaurant City is a Facebook game that allows you to create and manage your own virtual restaurant. Watch this video tutorial to learn how to hack Restaurant City money (11/12/09). You need Cheat Engine 5.5 and the hex is: 00000039840FD285.

Kung fu is an ancient Chinese martial art that involves using powerful punching techniques. Learn several punching combinations from a professional kung fu instructor in this free video series.

Aikido has countless wrist grab forms and techniques for any method of martial arts self defense someone might need to call upon. Learn many of these tips from an Aikido expert in this free video clip series.

The video presents "How to start your own Clothing Line Business". The steps include getting the financing, designing the prototype outfit/s, producing the line of clothing, promotion and sales. A good way of financing for a small business such as this is to sell your idea to family, friends and even colleagues. Research and prepare the business plan for your clothing line and be passionate about it in your presentation to convince them to fund your business. The next step is to get the produ...

How to make a great green apple martini. First we start with the tools of the trade, you will need a glass, champagne or martini glass will do, next a set of tumblers, a speed pour-er, and a martini strainer. Now that all of those are laid out we need to chill the glass down, so take the larger tumbler and fill it 3/4 full of ice. Add the ice to the glass and set aside. While the glass is chilling out, we need to get our liquor out and ready to mix, these are the liquors needed:

Looking to create a savings account? Once you see how much you can save when you spend only on needs rather than wants, you may never go back to frivolous shopping. In this video, ways to stop spending so much money are gone over.

Not sticking to your New Year's resolution of finally getting rid of that spare tire? Trade in those love handles for a slender waistline by following these tips starting today!
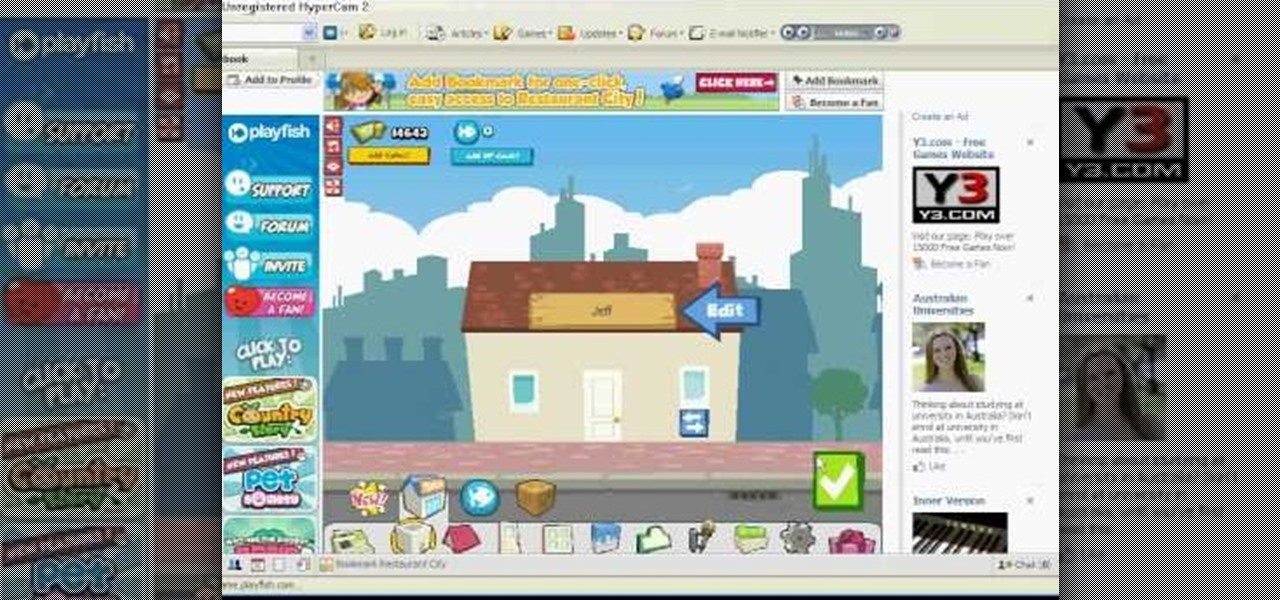
This is the RC Pointer Coin Hack for Restaurant City. You can keep getting coins and coins and coins… it just depends on how long and how far you are willing to go.

Restaurant City is a Facebook game that allows you to create and manage your own virtual restaurant. Watch this video tutorial to learn how to hack millions on Restaurant City (11/15/09).

Watch this video tutorial to learn how to make a frappé. Save money and time by making a blended frozen coffee drink from the neighborhood cafe right at home.

Knowing a few tricks of the trade will help you cry at the drop of a hat. You Will Need:

This fun twist on a sandwich is guaranteed not to be traded or thrown away. Follow along as our Food Network host shows you how to make banana dogs for your kids. This cooking how-to video is part of Cooking for Kids show hosted by Cricket Azima. Kid-food expert Cricket Azima makes yummy and healthy meals the little ones will flip over. Banana dogs are so easy to make, you can have the kids help you make them.

The still-unfolding story of China's Nreal augmented reality startup continues to develop, with each turn uncovering another unexpected wrinkle.

It's no secret that iPhones are expensive. Whether or not you believe the price tag is justified, $1,000 is a lot to spend on an iPhone 11 Pro. But if you're in need of a new iPhone, you picked a great time. Black Friday is rapidly approaching, and for Walmart, many of those deals are already available.

Norway-based production tools company Vizrt is putting the real into augmented reality with its broadcast AR solution that's designed to keep sports fans (and other audiences) watching.

The newest version of macOS has arrived. While everyone's mind is being blown by Mojave's groundbreaking new Dark Mode, we'll be taking advantage of its insecure file permissions to establish a persistent backdoor with a self-destructing payload that leaves little evidence for forensics.

It turns out that coming up groundbreaking technology and raising billions may actually be the easy part for Magic Leap, as a new report has revealed yet another legal entanglement at the Florida-based company.

Meta Company has filed its response to allegations that the user interface for their augmented reality headsets infringe on six patents owned by a mostly-unknown company.

Apple officially unveiled the long-awaited iPhone X, its tenth-anniversary edition iPhone, on September 12. With preorder and release dates just around the corner, you'll want to brush up on all things iPhone X to make sure you get your hands on one as soon as possible. After all, preorders start Friday, October 27.

While Meta Company has agreed to a settlement in its lawsuit against a former employee and his company, they find the tables have now turned on them in the form of patent infringement allegations from another entity.

Usually, when I see a video that is captioned "wait for it," I'm quick to dismiss what could possibly come at the end of the clip. In this case, however, I was totally wrong and the final result was definitely worth the wait.

Sup? Today, we'll be learning about for loops in Java: What they are, how they work, and how to create them.

In this article I will show you how to obtain victim's credentials without cracking any hashes. There are a couple of ways to perform this task (for example dumping the SAM file and cracking the NTLM hashes), but here I will explain how to do it using PowerShell and a bit of social engineering. We are going to create a fake login popup.

Your English teacher is a creep. The way he looks at your girlfriend, the way he always spends ages with the girls in the class going over their work but not the boys, just the way he is.

Now that we have control over a victim's browser, we need to use some attacks to maintain the connection, or even better: upload a shell.

OTW's great Tutorial Hack Like a Pro: How to Save the World from Nuclear Annihilation gives me the inspiration to try this on Win7 sp1.

Apple is notoriously cryptic when it comes to the reveals of its new products, and as usual, they've kept us guessing about the release of the iPhone 5 (or "New iPhone?"). It's expected to be officially revealed on September 12, and rumor has it that sales will begin on the 21st. Though the whole world seems to be anxiously awaiting the announcement, there has also been some controversy surrounding the iPhone 5's production. With the high number of suicides and poor working conditions at Foxc...

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

UnrealIRCd is an open-source IRC server that has been around since 1999 and is perhaps the most widely used one today. Version 3.2.8.1 was vulnerable to remote code execution due to a backdoor in the software. Today, we will be exploiting the vulnerability with Metasploit, examining the underlying code to understand it, and creating our own version of the exploit in Python.

Microsoft.com is one of the most extensive domains on the internet with thousands of registered subdomains. Windows 10 will ping these subdomains hundreds of times an hour, making it challenging to firewall and monitor all of the requests made by the operating system. An attacker can use these subdomains to serve payloads to evade network firewalls.

It is often said that the best hackers remain unknown, and the greatest attacks are left undiscovered, but it's hard for an up-and-coming penetration tester or white hat to learn anything unless one of those factors is actually known or discovered. But the end goal here in our SQL injection lessons is to make that statement as true as possible for us when performing our hacks.

In one of my previous articles, I discussed ShinoBot, a remote administration tool that makes itself obvious. The goal is to see if the user could detect a remote administration tool or RAT on their system. In this article, I'll be demonstrating the use of Pupy, an actual RAT, on a target Ubuntu 16.04 server.

Welcome to a tutorial on crypting technology. In this article, we will be discussing types of crypters, how they work and why they work. After defining these, we will then make our own basic crypter using the function I gave to you as a task to complete by yourself in the previous tutorial.

When it comes to give away or sell your iPhone, you can't just power it down, take out the SIM card, and hope everything will be okay. There's valuable data on your iPhone, and you need to get rid of it. Plus, if you don't perform all the necessary steps, chances are whoever ends up with the device won't even be able to use it. If you're selling it, that could ding your seller reputation.

Welcome back, my greenhorn hackers! I recently began a series on scripting and have received such positive feedback that I'm going to keep this series going. As I've said before, to graduate from the script kiddie to the pro hacker, you'll need to have some scripting skills. The better you are at scripting, the more advanced your hacking. Ultimately, we are leading up to developing the skills to build your own zero day exploits.
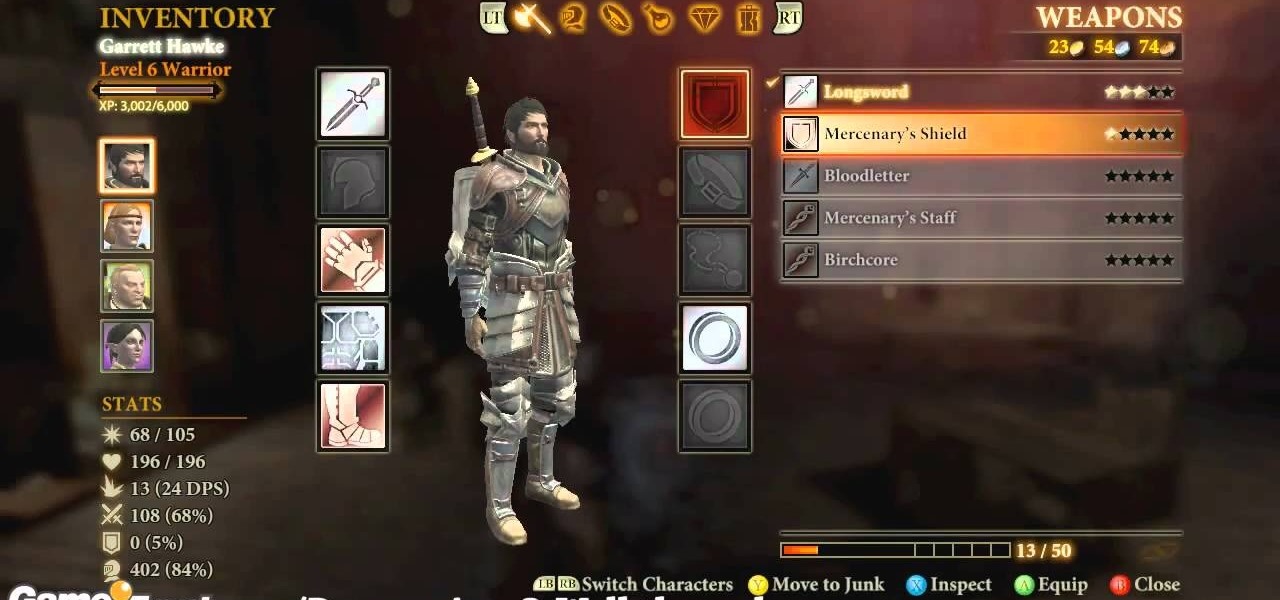
Dragon Age 2 seems to have more awesome and easy-to-execute exploitable glitches than any game in a long time. It almost seem deliberate, which would be a really awesome move on Bioware's part. This video will teach you how to use a really simple inventory glitch to max out any character's armor stat at 100% in less than a minute. You will be almost indestructible, and you can stop whenever you want if you just want a more reasonable boost.

To get the Guerilla Tactics achievement / trophy in Bulletstorm, you must execute 25 skillshots in a single Echoes map. Skillshots are the most fun part Bulletstorm. This video will give you a handy step-by-step guide to getting the achievement in Collapsed Building.

First, you will need a gallon of milk that's about a quarter full. It's best if you empty out the contents, but make sure to save it though because you will be needing it later.