In the second part of this tutorial, we are going to crack the hashes that we've captured previously. I'm going to explain how to do it with the powerful John the Ripper. It comes with Kali by default, so no need to install!

If you ever need help troubleshooting an issue that you're having with your Android device, one of the most useful tools you have available to you is the screenshot. Essentially, this is an exact copy of everything that is showing on your screen at any point in time, which you could use to capture the issue you're having, then share the screenshot with your tech support.

Google's Chrome browser is evolving into a very powerful platform. Not only can it be used to view your favorite website or mirror tabs to your Chromecast, but now that it has an App Engine, more powerful tools can be run within Chrome.

Magic Leap, the virtual-reality software group backed by Google, just released a teaser video on their YouTube channel. In a word, it's amazing.
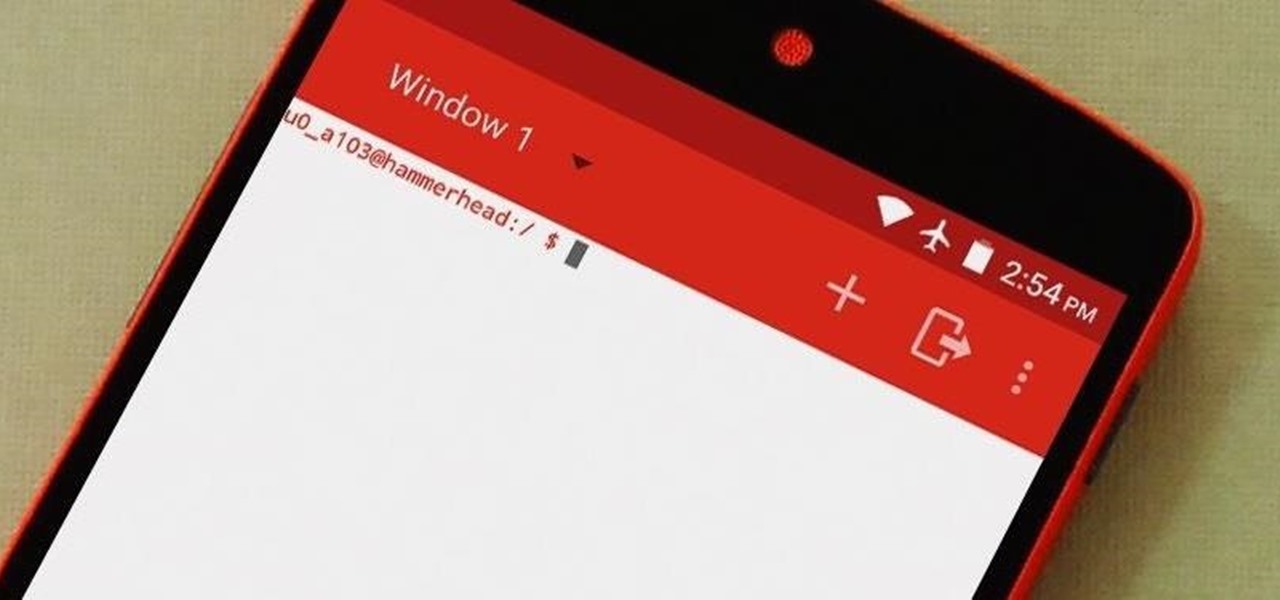
Deep down, Android is a fork of Linux, which is a desktop operating system that started out as entirely command prompt-based. For that reason, many system-level tasks can still be executed within a terminal emulator app.

Android Debug Bridge, or ADB for short, is a very powerful utility that can remotely execute commands on your Android device. This remote terminal interface, however, is not very "remote" at all. You have to be tied down to your computer to use it, since a USB cable is normally required.

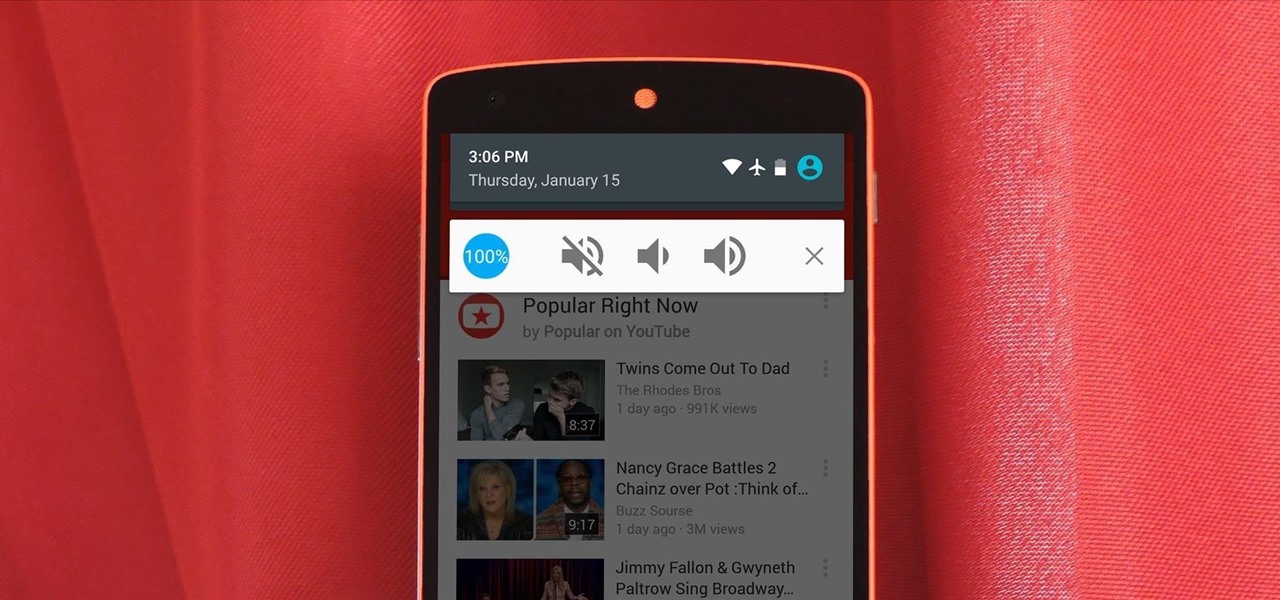
If there's one gripe I have with Android Lollipop, it's the new volume menu. When Priority mode was introduced, the stock volume panel was revamped to accommodate it, and somewhere along the way a bit of functionality was lost.

So you've decided to transform your drab backyard into a Japanese Zen garden. You've made the right choice. Yes, tire swings and crab grass can slowly kill the soul. That being said, a bit of planning lies ahead. This article offers a list of How To tips, culled from the Landscape Network and other professional Japanese style landscapers, for planning an effective Japanese style landscape in your home. Step 1: Research.

Ah, the art of the April Fool's prank. If you're a dedicated prankster, you probably already know who you're going to get on the big day. But if you're still searching for a prank to pull, never fear—we've got one that's pretty easy to execute and is guaranteed to get reactions. Those Oreo cookies look irresistible, right? Unless you're on a strict no-chocolate diet, you wouldn't be able to help yourself from shoving those in your mouth—and that's where the fun comes in.

With the the general computer users understanding of Information security rising (at least to the point of not clicking on unknown links), and operating system security getting better by default. We need to look for new and creative ways to gain a foothold in a system.

There are tons of ways to make simple DIY lamps out of things you have lying around at home. If you've got an empty container, (even an orange or tuna can), there's probably a way to upcycle it into a lamp of some sort, and they can come in handy if you ever lose power.

UPDATE: A patch to fix the exploit has been released. Download it here.

Nearly ten years since the first Galaxy Note and yet the Galaxy Note 20 still hasn't solved one of its biggest problems: bloatware. There are still over 20 redundant or unnecessary apps that are on this $1,000+ phone. But while it does require some advanced tools, it's still possible to remove them.

One of the most promising avenues of attack in a web application is the file upload. With results ranging from XSS to full-blown code execution, file uploads are an attractive target for hackers. There are usually restrictions in place that can make it challenging to execute an attack, but there are various techniques a hacker could use to beat file upload restrictions to get a shell.

Windows 10 and macOS have poor reputations when it comes to customer privacy and user policies. Our hacking Windows 10 and hacking macOS articles might make it seem like a reasonably secure operating system doesn't exist. But I'm here to tell you that there is a viable alternative that could provide some sense of security and trust.

With the global COVID-19 pandemic preventing Pokémon GO players from venturing into the real world, developer Niantic has adapted the game for trainers to play in a socially-distanced manner.

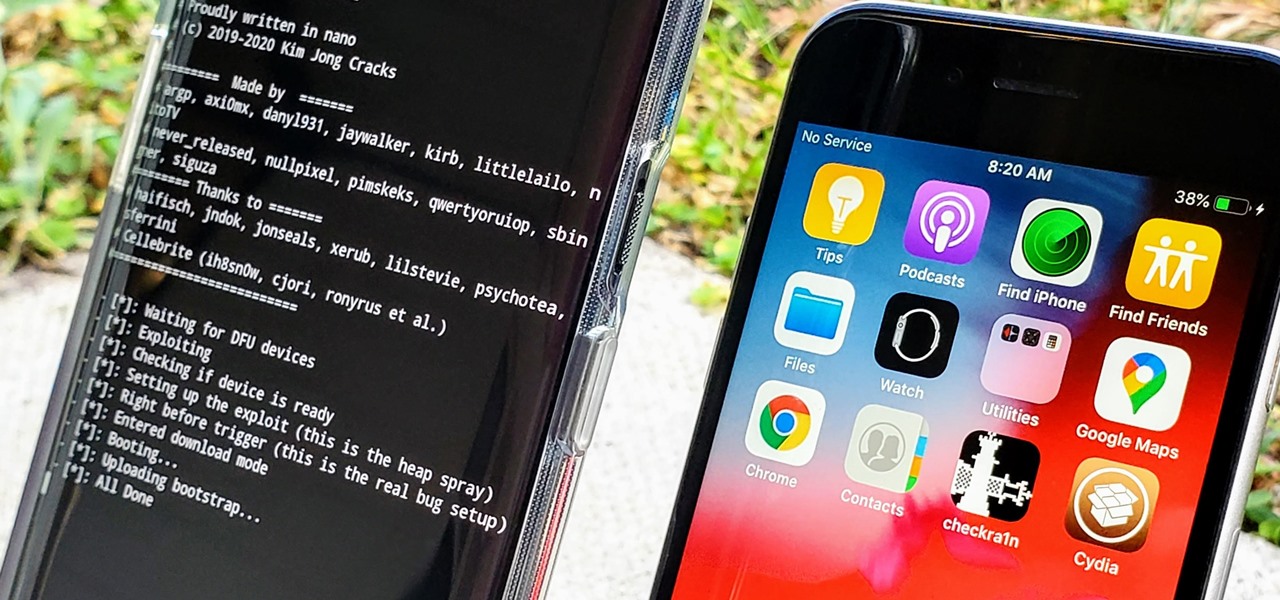
In the iPhone modding scene, the Checkm8 bootrom exploit, by developer axi0mX, led to a powerful jailbreaking tool known as Checkra1n. With it, you can jailbreak a variety of iPhone models without worrying about it getting patched later on. But in the past, it required you to have a macOS computer — but not anymore.

We're a few weeks away from the fireworks associated with New Year's celebrations, but that doesn't mean you can't start a little early — in augmented reality.

Apple seeded the official version of iOS 13 to compatible iPhones on Sept. 19. Since then, we've seen two major updates — iOS 13.1, which, by our count, introduced 22 new features, and iOS 13.2, which also added 22 new features. Today, Dec. 10, Apple introduced the third major update: iOS 13.3.

From the iPhone X onward, the Side button has taken on many of the functions associated with the Home button, such as summoning Siri, pulling up the AssistiveTouch shortcut, and more. So if you've finally ditched your Home button iPhone for the latest iPhone 11, the process of shutting down and restarting is something you'll need to learn all over.

After playing Mario Kart Tour for a little while, you'll notice it's a bit different from previous games in the series. The biggest change is how they've deferred to new players by automating many of the controls. But what if you want the traditional experience? We've got you covered.

The Oscars are fast approaching, which means that all the most talked about films are getting a second dose of heavy promotion in hopes of winning an Academy Award.

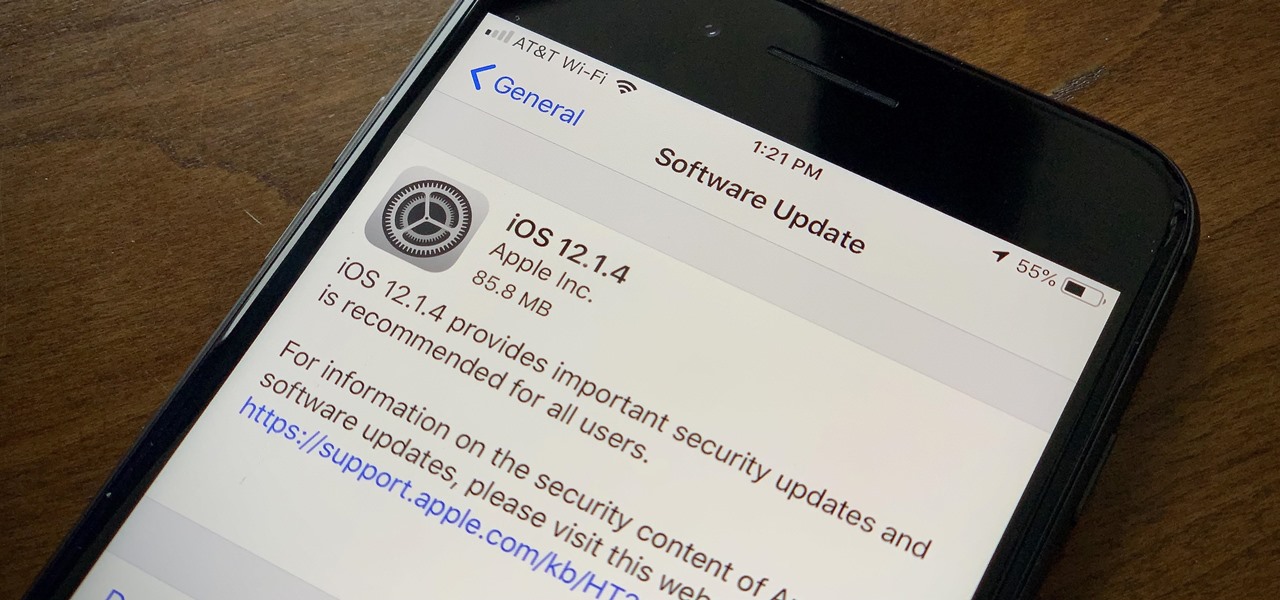
Apple found itself in serious trouble last week when a teenager discovered a critical FaceTime bug that threatened the security of nearly every iPhone user. The bug enabled a user using Group FaceTime to access either the microphone or the camera of a recipient before they answered the call. According to Apple, the issues have been fixed in an iOS 12.1.4 update released Thursday, Feb. 7.

Location-based gaming pioneer Niantic has been preparing its flavor of AR cloud, the Niantic Real World Platform, to bring more realistic and interactive augmented reality experiences to mobile apps. And now the company is looking for a few good developers to help execute its vision on the platform.

In a move sure to stir up even more speculation about the future of Snap Inc., the company's vice president of content, Nick Bell, is leaving the company after five years.

With the iPhone X, Apple introduced a brand new way for iOS users to interact with their iPhones. Gestures took the spotlight, as they very apparently replaced functions you would normally execute on the Home button. But swipes aren't everything for the new iPhone XS, XS Max, and XR. Don't believe us? Just take a look at the Side button.

The iPhone X ushered in the Swiss Army Knife-like Side button, which can perform numerous functions, such as summoning Siri and opening Apple Pay through click gestures. This has carried over into the iPhone XS, XS Max, and iPhone XR, so if you've upgraded to one of these devices from a Home button-equipped iPhone, you'll have to learn how to shut down your new device.

PUBG is continually getting better and more intuitive with each update, and version 0.4.0 is no exception. Besides a new training map to help you practice and a faster-paced arcade mode for on-the-go gaming, the newest version of PUBG now includes a feature that exclusively caters to iPhones from the 6S on up.

Android Pie is bringing in plenty of changes, but the headlining feature is a set of navigation gestures like the iPhone X uses. With Android 9.0, you can now navigate through your phone using a total of seven new swipe gestures.

Every dollar that comes your way is a blessing, especially when it comes to trading in the volatile world of bitcoins. Thankfully, Coinbase rewards you for sending much valued customers their way, giving you more money to feed your cryptocurrency trading needs.

On Wednesday, Scope AR, makers of Remote AR, the augmented reality video conference calling and remote assistance solution, announced that the app is finally available for HoloLens. Next Reality had a chance to talk with the founder and CEO/CTO of Scope AR, Scott Montgomerie, inside this new version of Remote AR.

With a new installment of the Saw horror series opening in theaters nationwide this weekend, Lionsgate is betting its ad dollars on immersive advertising to sell tickets.

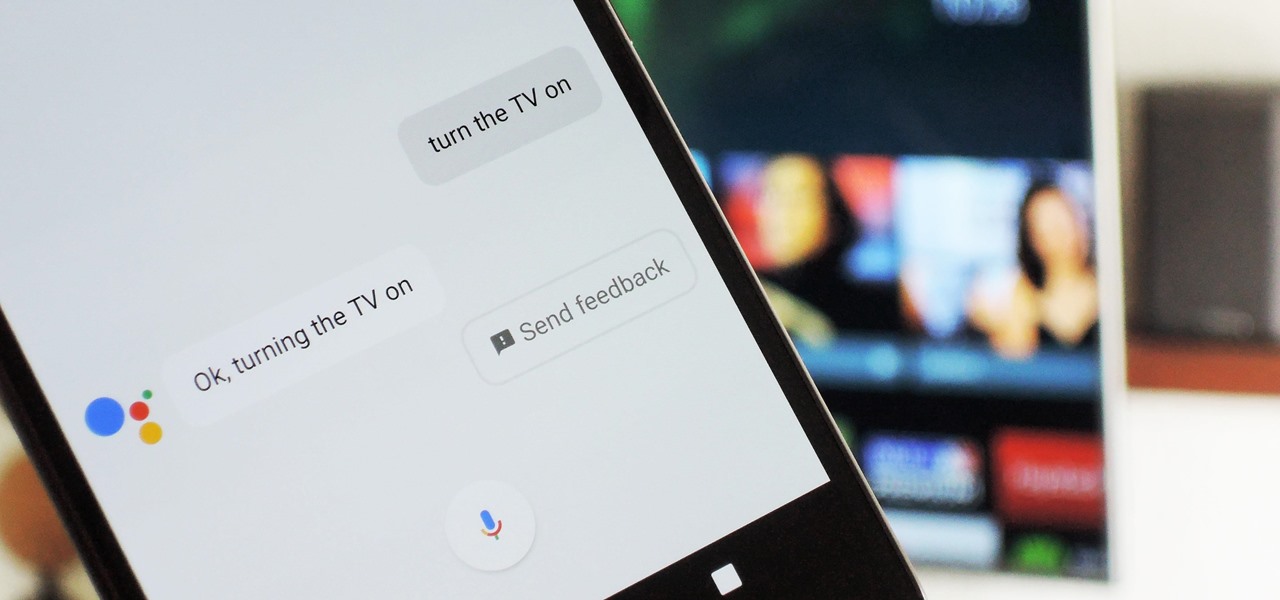
The Google Assistant is great about understanding what you actually mean, so you don't have to issue exact commands like you do with Amazon Alexa, for instance. But even though it's a master of colloquial speech, it could still be better, and that's where shortcuts come into play.

There's not much you can do to customize the look and feel of your iPhone's home screen, at least when it comes to official options provided by Apple. But thanks to a new bug discovered by YouTuber iDeviceHelp, you can now hide text labels for app icons and folders on your iPhone or iPad, and this hack doesn't even require a jailbroken device.

Google Assistant just got a lot more powerful thanks to IFTTT. The automation platform, whose name stands for If This, Then That, connects your favorite online services and smart devices to one another, allowing for a seamless experience with many different gadgets—and Google Assistant is officially supported.

Copying files from a computer to your Android device has always been pretty straightforward—just connect the two devices with a USB cable, open your desktop file explorer, then move the files over. But what if you didn't need any wires at all?

Hey everyone, this guide will show the process of stealing your victims Facebook credentials. This is a followup to my previous post.

Hello, everyone. Stealth is a large part of any successful hack; if we don't get noticed, we're much less likely to be caught. In these next few articles, we'll be building a shell based on keeping us hidden from a firewall. There are many ways to stay hidden from a firewall, but we'll only be incorporating a couple into our shell. This article will outline and explain these evasion concepts and techniques.

Welcome to my very first tutorial ever. Today I will be teaching you how you can use Arachni to scan vulnerabilities of web applications. I welcome all criticism good or bad as a teaching method for myself.

How's it goin'? In this tutorial, we will learn about the security issues of the popen and system functions. I've seen a few people attempting to run command line utilities or whatever it is they require with calls to these two functions but may not know the security implications which come along with it. I will show you using an example from the wargame IO Smash The Stack.