
News: 31-Legged Race Executed with Fascist Precision
30 Japanese schoolchildren, leg-to-leg. And they're good. Really good. What was I doing at that age, in the neon-lit elementary school gymnasium? Square dancing. Sweaty-palmed square dancing.


30 Japanese schoolchildren, leg-to-leg. And they're good. Really good. What was I doing at that age, in the neon-lit elementary school gymnasium? Square dancing. Sweaty-palmed square dancing.

In this tutorial, you will learn exactly how to make a router-based inlay. And inlay is made up of small cut out sections of wood, and looks like a stencil or pattern when you are finished.
Watch this fine art video tutorial to learn how to illustrate with markers and colored pencils. "This video shows my process for making an illustration (non tradigital). I use illustration markers (usually prismacolor) and color pencils (usually prisma once again) and a wax blending stick. I make my illustrations in two steps:

Join professional skateboarder Ryan Smith as he teaches you how to perform a big spin on your board. This video tutorial will how you just how to do the big spin trick, perfectly.

Master your tennis serve progressions. Be sure to click on all the video chapters to view the entire tutorial.

This video by StenLTran92 shows how to accomplish the break-dance moves "Windmill" and "Standing Mill." The video begins by first displaying the move in it's entirety. Then, the instructor takes us through the step by step of performing the break-dance move. The moves are all broken down into various kicks, drops, and facings that are to be followed if the move is to be done correctly. After the first lesson, the instructor moves on to how to accomplish a variation on the "Windmill" move. Bot...

Learn how to do floor crunches. Presented by Real Jock Gay Fitness Health & Life. Benefits

Practice What You Preach: Just make sure you know what you're doing. Return to Leonardo in Florence and he'll use your collected codices to give you some new skills. After the cut scene, look for the marker on your map that points you to a courtyard behind Leonardo's pad. There are three new stealth kills you've learned, and you need to practice each.

In this dance video tutorial, you will see how the heel toe move is done step-by-step. The heel toe move is one of the moves involved in c-walking. There is no voice or text in the tutorial, but you should be able to understand how the move is executed as the creator of the video takes you through the whole thing slowly and step-by-step.

Finish the football practice by going over 10 plays until each is executed perfectly - great for repetition and conditioning. This coaching video will give you some tips and examples.

Group 5 is the final group of basic bo hojo-undo moves but they are anything but basic! See how they should be executed in this video.

This video gives an analysis of second bo kata, cho un no kon and shows you how it is executed.
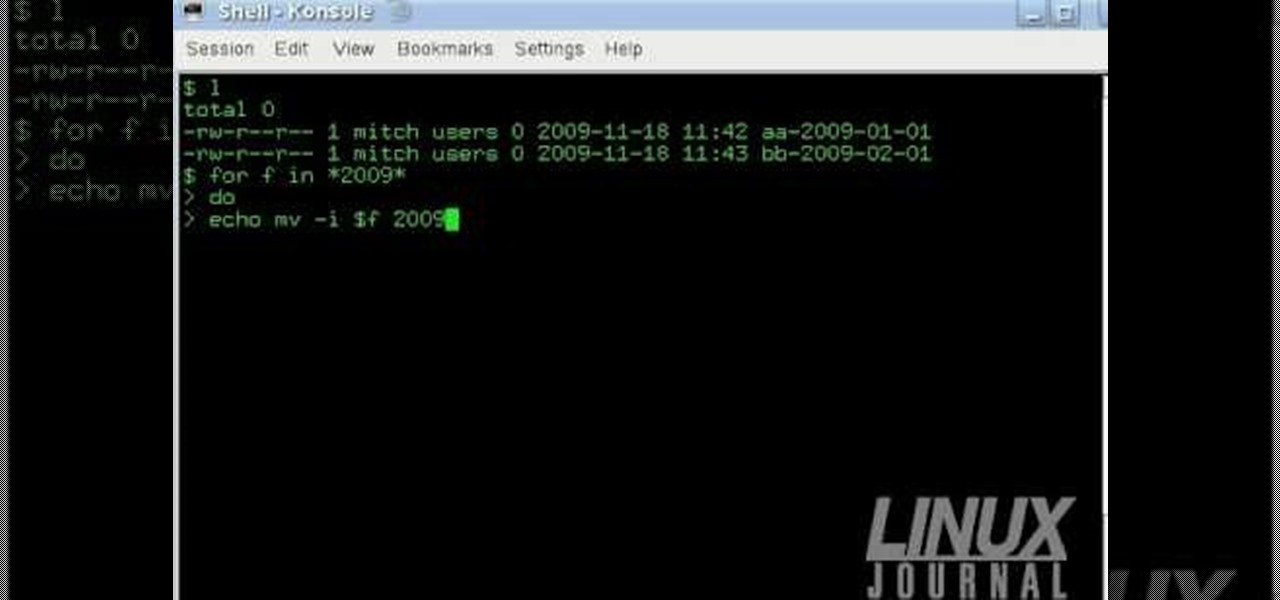
The Linux command shell provides a very powerful interface for doing various system tasks. This video explains with an example, how to use a bit of programming techniques to batch rename files with similar naming conventions.

In this how-to video, you will learn how to identify and control problems with Ash and Golden Rain Trees. If there are discolorations in the tree branch, there may be a few problems. If you see a severe orange color, this will damage the tree. You can paint the tree with a white paint to avoid this problem. Pruning cuts that have been executed poorly will also cause discoloration and rot. If the leaves have tip burn, this may mean that the air is dry and arid. If twigs on Junipers look dirty ...
Walt Ribeiro shows you how beats per minute work along with time signatures. This video takes you through the steps with a detailed explanation of how they work together and is executed using a drum along with a handy saying to help you keep your time signatures going steady to the beats per minute. Walt explains this using an electronic tempo clock while changing up the time signature. If you have ever had a music question with how these two things relate to each other then video is for you.

Do you want to know what's the secret to a great looking lawn ? Then you have to watch this video in which Lowe's home improvement expert Mike Kraft explains how to sharpen or replace a Lawn Mower blade. Mike will share with you all the tips and the secrets of this simple and yet crucial operation. From the tools required to the safety measures, everything will be explained to you in this video with all the steps actually executed and filmed right in front of you.
In this video tutorial, Chris Pels will show how to include JavaScript to an ASP.NET page for use on the client page to provide a richer and more robust user experience. First, see how to include JavaScript directly within an ASP.NET page and reference the script from within HTML page elements. Next, see how to abstract the JavaScript to an external JavaScript file which offers the advantage of being cached by the browser and can be used by multiple pages. Lastly, learn how to add JavaScript ...

This game goes by a bunch of names: "fast and loose," "pricking the garter," "the endless chain," "the strap..." The object is simple: a chain is laid in a figure-eight configuration. One of the holes is the true center of the chain and will hold "fast," while the other will not hold, and is instead "loose". Follow along with this how-to video and learn how to perform the bar trick.

Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.

The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data.

With just one line of Ruby code embedded into a fake PDF, a hacker can remotely control any Mac computer from anywhere in the world. Creating the command is the easy part, but getting the target to open the code is where a hacker will need to get creative.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

If you've ever attempted to report a bug to a developer, no doubt you've heard the response, "Get a logcat." This is infinitely important to a developer because of the fact that a logcat captures a full report of every command that was recently executed on your Android device, and it allows them to see exactly where something went wrong.

This is the first installment in a new series that I am calling "Hacker Hurdles." These are things, methods, techniques that make our job as hackers more challenging and difficult. Don't misunderstand me, these items don't make our task impossible, but rather more challenging and, therefore, more gratifying when we are successful. One of the most important new hurdles for hackers is DEP and ASLR. Data Execution Prevention (DEP) and Address Space Layout Randomization (ASLR) are designed to pre...

The Mentos and soda prank is as old as Mentos. You combine Mentos and soda, and a symphony of sticky fluid will erupt. This video features one charming young man explaining how he executed the prank on his younger sister, with step-by-step instructions and questionable video quality. Prank on.

With the macOS stager created and the attacker's system hosting the Empire listener, the malicious AppleScript can be designed and disguised to appear as a legitimate PDF using a few Unicode and icon manipulation tricks.

Yesterday, we pointed out that hackers could remote-wipe certain Android-based Samsung smartphones like the Galaxy S III using a USSD exploit. All they have to do is hide a small code into any webpage or text—even barcodes—then once you click on it, the phone resets to factory settings in a matter of seconds. The video below shows just how easy it is.

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

It's easier than you might think to hack into Wi-Fi routers using just one unrooted Android phone. This method doesn't require brute-forcing the password, a Windows OS for converting PowerShell scripts into EXE format, a reliable VPS for intercepting hacked Wi-Fi passwords, or Metasploit for post-exploitation tricks.

One of the best ways to improve your skills as a hacker is to learn to combine different avenues of attack to achieve success. What if it were possible to get a victim to connect to our machine and execute a chosen payload on our behalf? This is indeed possible with the almighty Metasploit and the aid of a technique known as command injection.

It is often said that the best hackers remain unknown, and the greatest attacks are left undiscovered, but it's hard for an up-and-coming penetration tester or white hat to learn anything unless one of those factors is actually known or discovered. But the end goal here in our SQL injection lessons is to make that statement as true as possible for us when performing our hacks.

Welcome back, everyone. In the previous part of this rapid-fire miniseries, we built the attacker portion of the shell. In this article, we'll just be testing it to see if everything works correctly.

Welcome back to control structures, part two featuring the three types of loops. Here we go! What Is a Loop?
Deep down, Android is a fork of Linux, which is a desktop operating system that started out as entirely command prompt-based. For that reason, many system-level tasks can still be executed within a terminal emulator app.

In this video the instructor shows how to choose options on a batch file. In a batch file if you write the command '@ echo off', the person running the batch file cannot see the commands being executed. You can use the 'if' condition to make the program execute either of two commands depending on the condition. While writing the if statements make sure that there is space between the 'if' and the '%' sign. If you write 'shutdown -t 30' command in your batch file, then the batch program when r...

File inclusion can allow an attacker to view files on a remote host they shouldn't be able to see, and it can even allow the attacker to run code on a target.

While Toyota ranks as the leading automotive brand in the world, the company is a follower when it comes to augmented reality.

Although there has been much speculation about how much damage could be done if hackers were to take control of a country's SCADA systems, there have been few examples - until a few months ago, with the power outage in Ukraine caused by hackers.

An attacker can repurpose public MyBB forums to act as command-and-control servers. It only takes a few lines of code to configure a MacBook to fetch commands and send responses to any website the attacker desires.

With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassing antivirus software and Windows Defender.