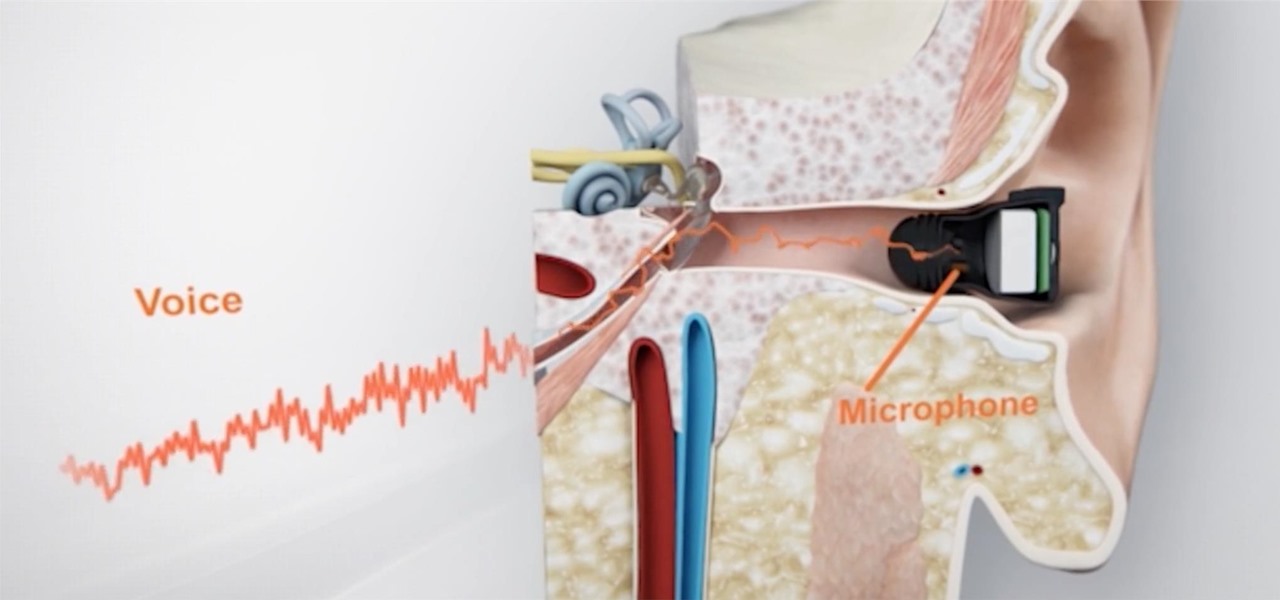
What's better than wireless in-ear headphones with noise-canceling technology? Giving them a microphone to hear you talk from inside your head. And that's exactly what you get with RippleBuds; its inside-facing mic helps keep your voice crystal clear over phone calls, and makes sure Siri, Cortana, and Google Now will always get the right command.
Modern smartphones are packed to the brim with low-power sensors like accelerometers and gyroscopes, which means they're capable of precisely measuring almost any type of movement. So why is it that when you just want to get walking directions somewhere, your device still uses its battery-sucking GPS connection to track your progress?
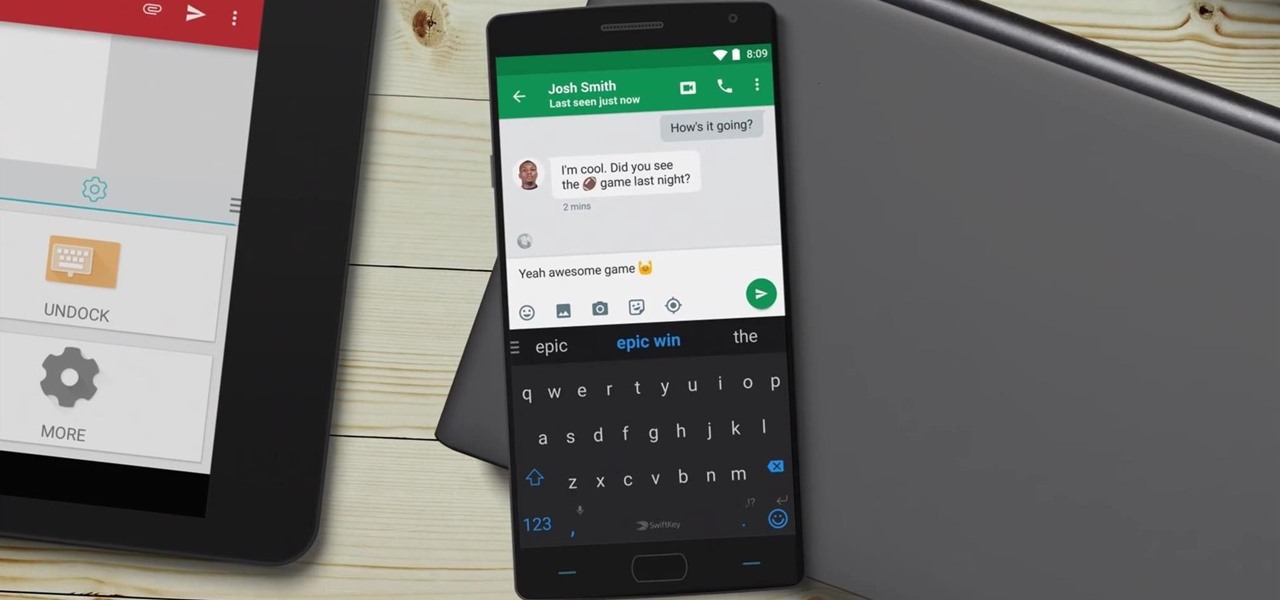
Microsoft announced Wednesday morning that it has entered into an agreement to acquire SwiftKey, makers of the SwiftKey predictive keyboard and its SDK that runs on over 300 million Android and iOS smartphones, for about $250 million.

Whether it's delivery drones or getting the U.S. Postal Service to ship packages on Sundays, Amazon continues to remain innovative and ahead of the game, as further evidenced with their mobile app, Amazon Underground.

For all that money spent on a new Watch, Apple could've given us more than just a charger and its case. I mean, the case is nice and all, but what realistic use is there for it? In all honesty, it'll probably find its way onto a shelf high above in the closet—but it doesn't have to.

Wearables were everywhere at CES 2015... you literally couldn't walk 10 feet without seeing some new and innovative device. Among the sleep, fitness, dog, and baby wearables, we came across one with a different, more important purpose—the Linx IAS injury prevention headband.

Often, when you crack open a beer with friends, your buddies are more focused on texting and Snapchatting than what's happening right in front of them. Smartphones have wedged their way into bars around the world—but an innovative new beer glass is encouraging patrons to put down the phone and engage with friends.

Samsung introduced a wave of seriously unique and innovative features on the Galaxy S4, including air gestures and weather sensors, but a lot of the features are actually just updated ones from the Galaxy S3. Unfortunately, one of those that returned was the dreaded increasing ringtone. In their increasing ringtone system, the ringtone will start off on a low volume and increase until it reaches your set volume. In theory, this is useful for not shocking the user with a sudden, blaring ringto...

With the Xperia Z release for most major U.S. carriers expected sometime very shortly, many are both excited and curious at Sony's new flagship device. Much of the hype surrounding the new smartphone has stemmed from several ads that Sony has released, touting their waterproof phone to be as innovative as their Trinitron, PlayStation, and Walkman brands. Your worries about dropping your phone in a tiny fishbowl are finally over.

One of the more innovative features about the new Windows 8 operating system is the ability to unlock the screen via a picture password. This new feature allows the user to select any photo they would like and use taps, circles or straight lines to unlock the device. The video below shows the picture unlock in action.

Join Matt Null (NCA/Millersville/Cheer Excel), Lindsey (Fire and Ice Allstars), Carly (Seton La Salle HS), Greg (Step 1 Allstars) and EJ (IUP) as you learn how to load, set and execute a sponge to prep (elevator) to sponge. Great tips for the beginning cheer leading coach or cheerleader!

Join Matt Null (NCA/Millersville/Cheer Excel), Lindsey (Fire and Ice Allstars), Carly (Seton La Salle HS), Greg (Step 1 Allstars) and EJ (IUP) as you learn how to load, set and execute an extension with a cradle dismount. Great tips for the beginning cheer leading coach or cheerleader!

An attacker can repurpose public MyBB forums to act as command-and-control servers. It only takes a few lines of code to configure a MacBook to fetch commands and send responses to any website the attacker desires.

Whether you love Motion Sense or think it's a gimmick, one thing we can agree on is that its functionality is limited. It's currently limited to switching tracks on a playlist, snoozing alarms, silencing calls, lowering the volume of alerts, and checking notifications. But a new mod will help you do so much more with it.

PowerShell Empire is a post-exploitation framework for computers and servers running Microsoft Windows, Windows Server operating systems, or both. In these tutorials, we will be exploring everything from how to install Powershell Empire to how to snoop around a target's computer without the antivirus software knowing about it. If we are lucky, we might even be able to obtain domain administrator credentials and own the whole network.

We recently covered an app called Fingerprint Quick Action that let you use your fingerprint scanner to expand your notification tray like the Google Pixel, along with a few other actions. It's definitely a useful mod, but there's a similar app can make your fingerprint scanner do almost anything—literally.

GitHub is an extremely popular site that allows developers to store source code and interact with other users about their projects. Anyone can download public, open-source files on GitHub manually or with Git, and anyone can fork off someone's project to expand or improve it into its own project. It's a really great site for programmers, developers, and even inspiring hackers.

Welcome back, my budding hackers! Metasploit, one of my favorite hacking/pentesting tools, has so many capabilities that even after my many tutorials on it, I have only scratched the surface of it capabilities. For instance, it can be used with Nexpose for vulnerability scanning, with Nmap for port scanning, and with its numerous auxiliary modules, nearly unlimited other hacking related capabilities.

Hello my anxious hackers, the week has started and here we begin a new series that I think will help many here and not only, for those that have the opportunity to follow our tutorials but they are not yet part of the community.

When attempting to compromise a target, we want as much control as possible over the victim. Metasploit's meterpreter allows us to have immense control over the victim, the only issue is that sometimes we can't land a meterpreter. We may only be able to land a standard shell, but fear not, there is a way to upgrade our shell into the all powerful meterpreter!

Hello all! In this tutorial, I'd like to show you one way of getting root on OS X. Check out this GitHub page for a recent privilege escalation exploit that was recently discovered. I've tested it and it works on both OS X 10.9 Mavericks and OS X 10.10 Yosemite, but appears to have been patched with OS X 10.11 El Capitan. If you check out the file main.m you can see where most of the magic is happening. This source code can very easily be changed to make it do more than just the system("/bin/...

Welcome back, my fledgling hackers! With this first article, I am initiating a new series intended to convey to my readers the skills necessary to develop your own exploits.

Welcome back, my greenhorn hackers! Recently, I asked the Null Byte community what subject they would most like me to cover in future tutorials. Many of you cited scripting, and I decided it's best to cover this subject soon, so here goes.

In my first tutorial on Linux basics, I discussed the importance of hackers using Linux and the structure of the directory system. We also looked briefly at the cd command. In this second Linux guide, I'll spend a bit more time with changing directories, listing directories, creating files and directories, and finally, getting help. Let's open up BackTrack and getting started learning more Linux for the aspiring hacker.

Learn in this video how to use XMLSpy to create and edit XQuery documents, debug them and profile execution speed and bottlenecks, and execute them against local XML data or XML stored on a database server. XML editing can't get easier then this.

In my first installment in this series on professional hacking tools, we downloaded and installed Metasploit, the exploitation framework. Now, we will begin to explore the Metasploit Framework and initiate a tried and true hack.

At first, it seemed like a clever art installation housed on the web, but now we're not so sure... the Newstweek hack may indeed be legit.

Execute the 9th puzzle, called Hat Trick, in Assassin's Creed 2. Image 1: Move the cursor onto Houdini’s torso. Image 2: Move the cursor over Gandhi’s heart. Code wheel puzzle: Your hint here is pretty obvious; there’s a big, glaring “6=1” next to Oswald’s picture. So move the red wheel so that the 6 is over the gray 1, and plug in the corresponding numbers. For more info, watch the whole gameplay.

Practice What You Preach: Just make sure you know what you're doing. Return to Leonardo in Florence and he'll use your collected codices to give you some new skills. After the cut scene, look for the marker on your map that points you to a courtyard behind Leonardo's pad. There are three new stealth kills you've learned, and you need to practice each.

Have you tried working out with reverse curls? If so you know that they are an essential part of lifting weights and strength training. This fitness how-to video demonstrates work out the bicep muscle with reverse curls. Learn about curls and weightlifting exercises in this workout video.

People use browsers for all types of things, and in general, we trust a lot of personal information to them. That's why browsers are a perfect attack surface for a hacker, because the target may not even know they are infected and feed you all of the information you could want.

While Toyota ranks as the leading automotive brand in the world, the company is a follower when it comes to augmented reality.

Mixed reviews of Magic Leap One aside, it would be hard to deny that Magic Leap has had a big year. And the AR unicorn isn't coasting to the finish line, with a number of new apps dropping and prescription frames finally arriving to bring relief to those who wear eyeglasses.

Locating and abusing files containing unsafe permissions is an easy and surefire way to elevate shell privileges on a backdoored macOS device. This time around, we'll be more aggressive and attempt to phish a user's login password by prompting a convincing popup message merely asking the target for their password.

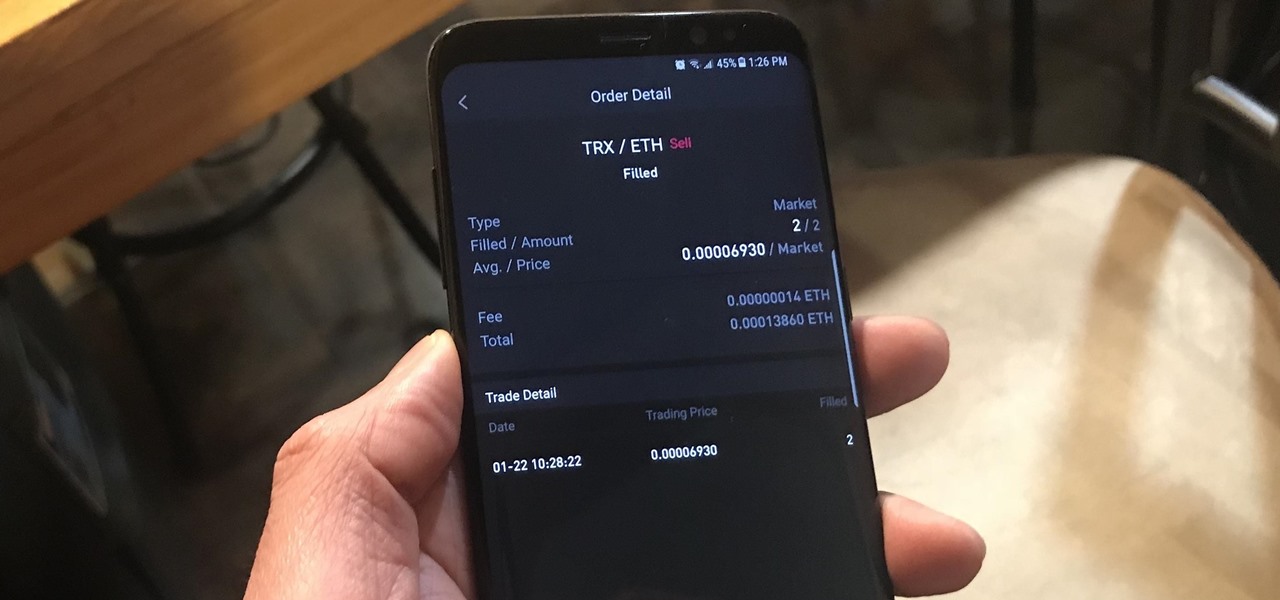
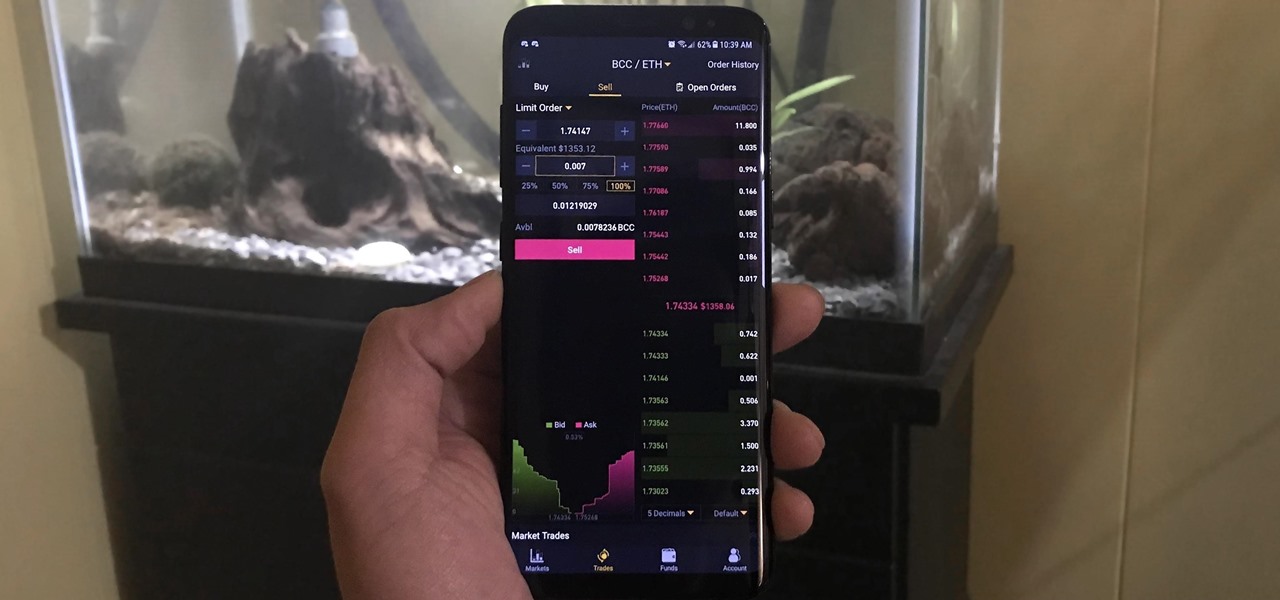
Selling alt-coins like Stellar (XLM) or Ripple (XRP) in exchange for more widespread coins like Ethereum (ETH) or Bitcoin (BTC) can be a daunting task if you're new to cryptocurrency. Though you'll still need to do your research to avoid potential disasters, Binance takes the hassle out of trading digital currencies on your smartphone.

Using Bitcoin (BTC) or Ethereum (ETH) to buy alt-coins like TRON (TRX), Stellar (XLM), or Ripple (XRP) can seem intimidating if you're new to cryptocurrency. Though you'll still need to do your research to avoid potential disasters, Binance takes the hassle out of trading digital currencies on your smartphone.

Recently, I ran across SecGen, a project which allows a user to create random vulnerable machines. I absolutely love vulnerable machines, since a vulnerable VM is a safe and legal way to practice hacking tactics, test out new tools, and exercise your puzzle-solving skills.

While its direct-selling model echoes brands like Avon and Tupperware, Indonesia's MindStores gives the approach a modern twist—with augmented reality.

Metasploit is an extremely popular pentesting tool capable of enumeration, exploitation, and injecting shell code, and is a part of almost every hacking toolkit. So there's no way I could leave this out of our series on getting your Mac set up for hacking.

Traditional root ad-blockers like AdAway and AdBlock Plus have no effect on YouTube anymore. Until now, if you wanted to get rid of the commercials that play before your favorite videos, there have only been two ways—either by paying for a YouTube Red subscription, or by using an Xposed module to modify the YouTube app itself and force it into not showing ads.