In this video tutorial, we learn how to perform the "Force Factor" card trick. For more information about the trick and its execution, including detailed, step-by-step instructions, and to get started incorporating this trick into your own routines, watch this free video card magic lesson.

In this video tutorial, we learn how to perform the "Alternating Prediction" card trick. For more information about the trick and its execution, including detailed, step-by-step instructions, and to get started incorporating this trick into your own routines, watch this free video card magic lesson.

In this video tutorial, we learn how to perform a simple, mathematical card trick. For more information about the trick and its execution, including detailed, step-by-step instructions, and to get started incorporating this trick into your own routines, watch this free video card magic lesson.

In this video tutorial, we learn how to perform an impressive ACAAN card trick using two decks and the Si Stebbins stack method. For more information about the trick and its execution, including detailed, step-by-step instructions, and to get started incorporating this trick into your own routines, watch this free video card magic lesson.

In this video tutorial, we learn how to perform the "Not Playing with a Full Deck" card trick. For more information about the trick and its execution, including detailed, step-by-step instructions, and to get started incorporating this trick into your own routines, watch this free video card magic lesson.

The prank is one of the most cherished traditional forms of expression around the world, from Japan to the Middle East to the good ol' US of A. Without them, how would people settle their disputes with one another while having a good laugh at the same time? Every time a new phenomenon enters our lives, new pranks emerge that can be performed with it. We at Wonderhowto love pranks as much as anybody, and to that end we've scoured the internet for videos demonstrating the proper setup and execu...

In this video Chris Pels shows how to create an MSBuild project that orchestrates the execution of the aspnet_compiler and aspnet_merge utilities for an ASP.NET web site. First, learn the fundamentals of the compilation process for an ASP.NET web site and the role of the two command line utilities. Next, see how to create an MSBuild project file and the primary elements such as PropertyGroup and Target. Then learn the details of how to execute the aspnet_compiler and aspnet_merge utilities fr...

Learn how to write a grant proposal. If your organization has come up with a great idea that needs money to get off the ground, you'll need a great proposal. Here's how to write one.

While building a deck may not be the easiest DIY project, it can be done with proper planning and execution. In part one of this five part series, learn about decking material options, deck style options, building codes restrictions and much more.

Being able to write your own hacking tools is what separates the script kiddies from the legendary hackers. While this can take many forms, one of the most coveted skills in hacking is the ability to dig through the binary files of a program and identify vulnerabilities at the lowest level. This is referred to as binary exploitation, and today we're going to check out a tool known as Protostar.

After nearly two months of beta testing, Apple is finally pushing the iOS 15.6 software update to all iPhone users. While it's not as feature-rich as the iOS 15.5 or iOS 15.4 that came before it, there are still a few things you'll want to know about it.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

Welcome back, reader! In this tutorial, we will be covering our first program! So let's get to it. We all know the unspoken tradition of the first program when learning a language and of course, here we will respect and complete it. Fire up your favorite text editor (be it vim, emacs, gedit, it's all the same to me, no h8) and try to keep up.
Project management covers a lot of processes needed for project completion. Among the many functions in managing projects, one of the most important is resource management. It is an aspect of project management which deals with various project management resources like human, materials, equipment and costs.

Apple's latest big software update includes an entirely new Apple app, a controversial change in the TV app, better Siri control, an improved Shortcuts app, interesting Safari upgrades, Apple Music Sing, and more. Keep reading to see what iOS 16.2 has to offer your iPhone.

Apple's latest iPhone and iPad software, iOS 15.5 and iPadOS 15.5, became available on May 16, so you can download and install it right now if you haven't already. While there aren't as many new features as iOS 15.4 and iPadOS 15.4 had, there are a few big ones in the U.S. you'll want to know beyond Apple's minuscule "About this Update" information in the "Software Update" menu.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

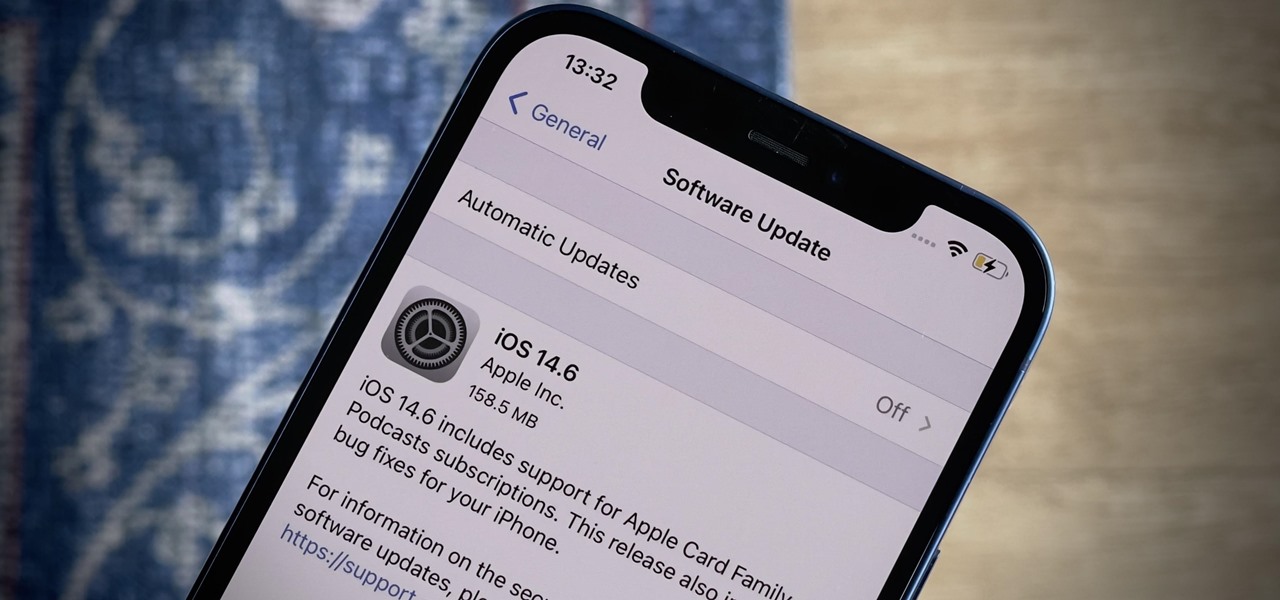
Apple released the latest version of its iPhone OS, iOS 14.6, today, Monday, May 24. This latest update (build number 18F72) introduces new features like unlocking your iPhone with Voice Control after a restart, Apple Card Family support for up to five people, and subscription support for shows in Podcasts.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

You may have seen news reports over the last two days detailing a major security flaw in virtually all smartphones. The devices that are at risk are not limited to either iPhone or Android — all of us are affected. If you want to make sure your smartphone and its data stay secure, there are a few steps you can take.

In my last how-to, we built a man-in-the-middle tool. The aforementioned script only established a man-in-the-middle. Today we'll be building a tool to utilize it. We'll be building a DNS packet sniffer. In a nutshell, this listens for DNS queries from the victim and shows them to us. This allows us to track the victims activity and perform some useful recon.

Hi everyone! Last time we finished analyzing the assembly representation of our vulnerable piece of code (have I ever told you it is vulnerable?). This time we are going to introduce some fundaments about exploitation by demonstrating how to crash a program's execution. If that sounds lame, next time we will see how this crash can in fact be useful to control the program's execution, achieving remote code execution!

In this video tutorial, we learn how to perform the "Down and Dirty" card trick. For more information about the trick and its execution, including detailed, step-by-step instructions, and to get started incorporating this trick into your own routines, watch this free video card magic lesson.

For those of us who aren't very good at magic, but are looking for a cool way to make an extra buck with a little magic, this is one of the easist card prediction tricks out there! This video will show you the steps for set up and execution in great detail and helps you to understand the whole process from start to finish.

This video tutorial shows the execution of a simple yet effective sleight of hand trick using a rope. Narration accompanies the visual explanation of how to pull it off. Watch this how-to video and learn how to perform a mystery knot magic rope trick.

BPS golf instructor Steve Bishop discusses setting up for a chip shot and the proper execution of a chip shot. Included with this lesson is also a drill which will help with your chipping technique.

After a long hiatus, we shall once again emerge from the shadowy depths of the internet to build an exploit. This time, we'll be looking at how to defeat a non-executable stack by using the ret2libc technique — a lean, mean, and brilliant way of exploiting a stack overflow vulnerability.

When we talk about driverless technology, the go-to companies are usually Waymo, Uber, or Tesla. However, traditional automakers like Ford and GM are also staking claims to the driverless and advanced driver assistance spaces.

As many of you know, processor's clock frequency improvement got stuck in about 2003, causing the origin of multicore CPU (and other technologies). In this article I'll introduce you on how to run code simultaneously in various processors (I suppose that all of you have a multicore CPU). When you write code without any parallel directive, it only executes in one CPU at the same time (see it below). OpenMP make simple to work with various cores (if not with all of them) , without so much heada...

Welcome back, my fledgling hackers! With this first article, I am initiating a new series intended to convey to my readers the skills necessary to develop your own exploits.

Welcome back, my rookie hackers! Several of you have written me asking about where they can find the latest hacks, exploits, and vulnerabilities. In response, I offer you this first in a series of tutorials on finding hacks, exploits, and vulnerabilities. First up: Microsoft Security Bulletins.

With the number of web applications out there today, it comes as no surprise that there are just as many vulnerabilities waiting for hackers to discover. Finding those vulnerabilities can be a difficult task, but there are plenty of tools available to make the process easier. While it won't help find any zero-days, web scanners such as Uniscan will detect common vulnerabilities.

During our last adventure into the realm of format string exploitation, we learned how we can manipulate format specifiers to rewrite a program's memory with an arbitrary value. While that's all well and good, arbitrary values are boring. We want to gain full control over the values we write, and today we are going to learn how to do just that.

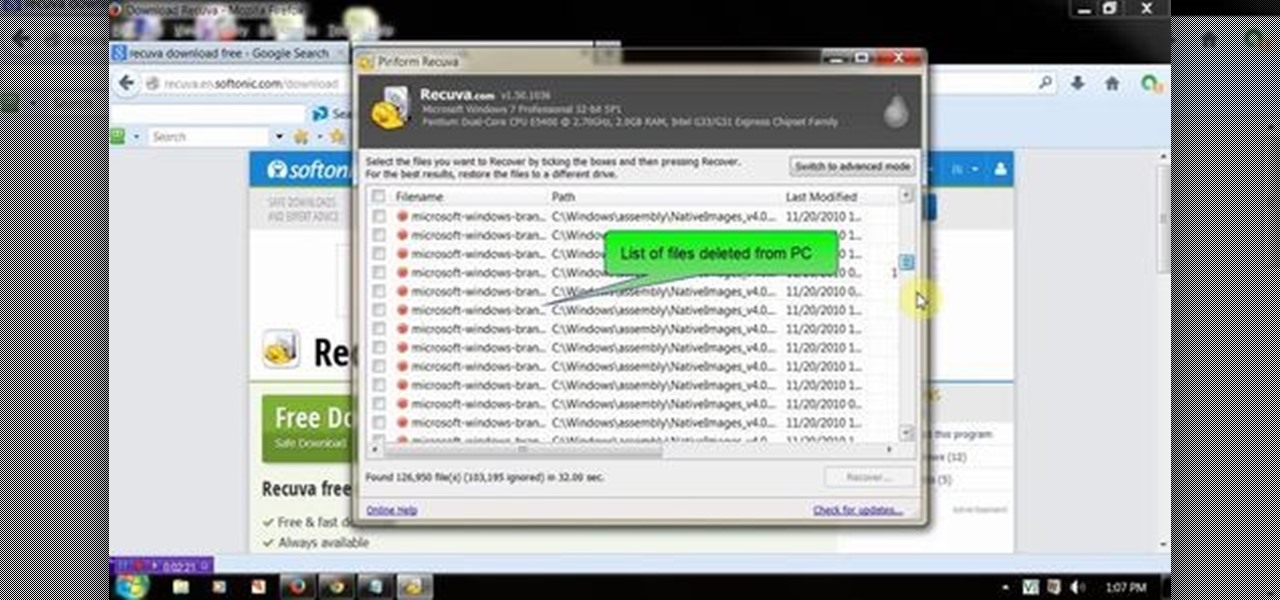
This video will show you how to recover permanently deleted file which you have deleted from recycle bin. But if any new file allocated to those positions then the files could not be recovered with this tool. Watch the video from the installation to execution of the tool to recover deleted data.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

In our previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when an MS Word document is opened. Because Microsoft built DDE into all of its Office products as a way to transfer data one time or continuously between applications, we can do the same thing in Excel to create a spreadsheet that runs malicious code when opened. The best part is, it will do so without requiring macros to be enabled.

Hello partners, first of all I would like to thank all those who have sent me positive feedback about my posts, to say that I'm always willing to learn and teach. I'm also open to answer the appropriate questions.

In this simple tutorial you will be shown step-by-step how to write local shellcode for use on 64-Bit Linux systems. Shellcode is simple code, usually written in assembly that is used as payload in exploits such as buffer overflow attacks. Payloads are the arrow head of an exploit: though the rest of the arrow is important for the delivery of the attack, the arrow head deals the killing blow. In reality, payloads are slightly less exciting yet far more interesting and intelligent than medieva...

This is the first installment in a new series that I am calling "Hacker Hurdles." These are things, methods, techniques that make our job as hackers more challenging and difficult. Don't misunderstand me, these items don't make our task impossible, but rather more challenging and, therefore, more gratifying when we are successful. One of the most important new hurdles for hackers is DEP and ASLR. Data Execution Prevention (DEP) and Address Space Layout Randomization (ASLR) are designed to pre...

Armis Labs has revealed eight vulnerabilities, called "BlueBorne", which put 5.3 billion Android, iOS, Windows, and Linux devices that use Bluetooth at risk. With it, hackers can control devices, access data, and spread malware to other vulnerable devices through networks. In this post, we will learn about the vulnerabilities, then look at how to find devices that have them.