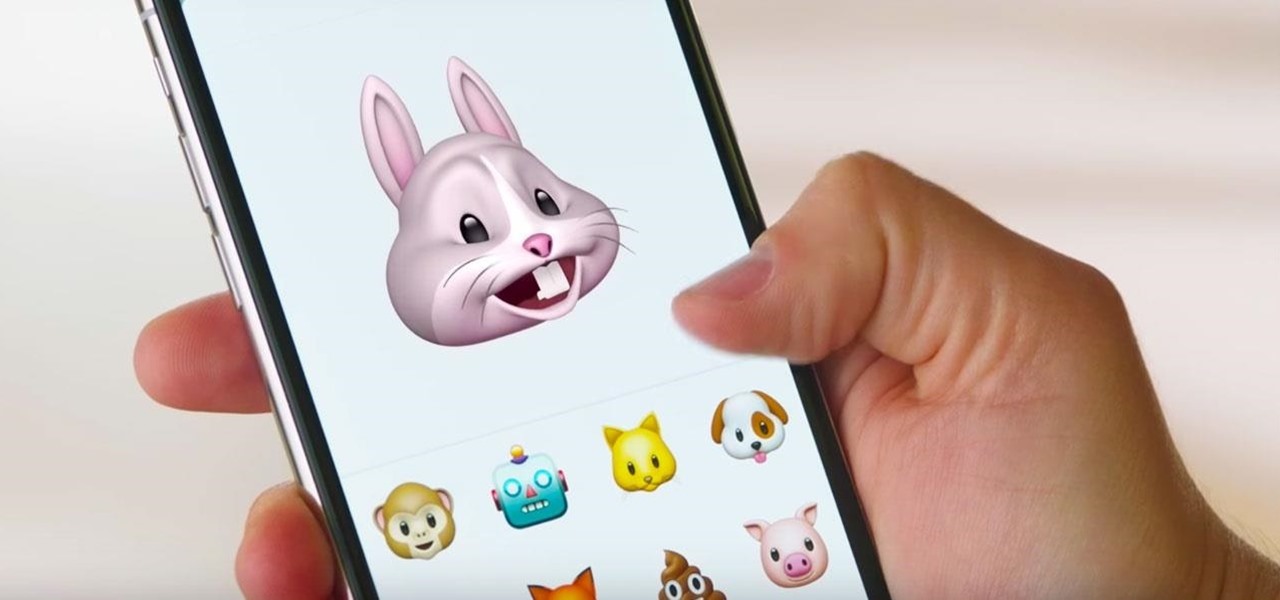
Apple just released its iOS 16.6 update for iPhone on July 24. When you install the new software, it may look like there's not much to it since Apple doesn't include any features in the release notes beyond "important bug fixes and security updates," but a few new features are hiding within.

Need a new way to impress your friends and family? Watch this video tutorial to learn how to solve the Rubik's Cube blindfolded. To solve the Rubiks Cube blindly, use the Pochmann Method. You really need to practice this method to get it down, because there are many things to keep in mind.
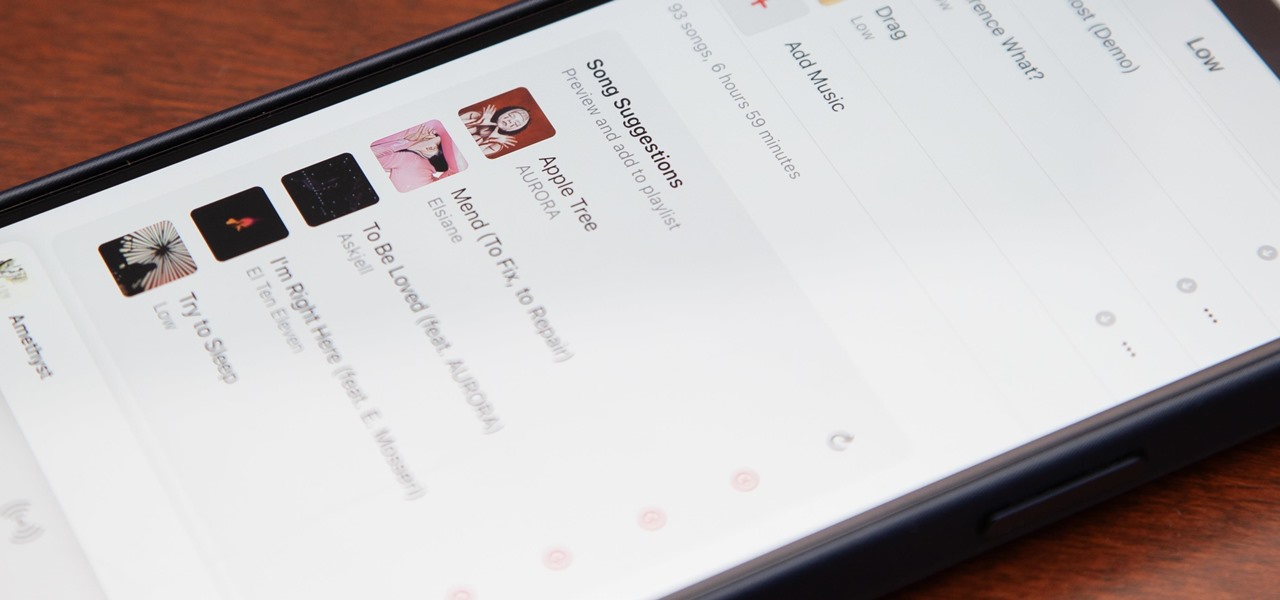
Apple's first big iOS 17 point update for iPhone just came out, and it includes some of the features initially planned for the iOS 17.0 release last September. But there's much more to iOS 17.1 than that — exciting new features and changes are hiding within Books, Music, StandBy, App Store, Lock Screen wallpapers, Apple Wallet, and more.

Apple has a few exciting surprises for you in its latest iOS 16 and iPadOS 16 software updates. Released on Thursday, May 18, version 16.5 includes new features, bug fixes, and security patches, and there are even hints of some big things coming in future software updates for iPhone and iPad.

Welcome back everyone. As many of you know, reconnaissance is extremely important in any successful hack. Without proper reconnaissance, we won't know what we're about to get into, literally.

Welcome back to another tutorial on functions. Last time, we looked inside memory to see what functions looked like in the flesh and all that Assembly was pretty nasty. At least you have some exposure to it. This time, we will be examining how functions work with the stack.

Hi everyone! In the previous part of this series we introduced remote code arbitrary execution via buffer overflows using all of our past experiences.

Welcome back, my nascent hackers! Earlier, I wrote a guide on finding operating system and application vulnerabilities in Microsoft's own security bulletins/vulnerability database. In this tutorial, I will demonstrate another invaluable resource for finding vulnerabilities and exploits by using the SecurityFocus database.

One of the best ways to improve your skills as a hacker is to learn to combine different avenues of attack to achieve success. What if it were possible to get a victim to connect to our machine and execute a chosen payload on our behalf? This is indeed possible with the almighty Metasploit and the aid of a technique known as command injection.

Welcome to my tutorial where Voidx and I will be expanding on my previous article to provide more clarity into the logic of the code.

Welcome back to control structures, part two featuring the three types of loops. Here we go! What Is a Loop?

INTRODUCTION Hello dear null_byters here we go again with our third part of this serie.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Welcome back, my hacker novitiates! Every so often, a MAJOR vulnerability appears that makes millions of systems vulnerable to attack. The most recent, named Shellshock, basically leaves every Mac OS X, Linux, and UNIX system on the planet vulnerable. As nearly two-thirds of all web servers on planet Earth run one of these operating systems (primarily Linux), that's a whole lot of systems out there waiting to be harvested.

The internet has undoubtedly changed the way we work and communicate. With technological advances, more and more people can collaborate on the web from anywhere in the world. But this remote-friendly environment inherently brings security risks, and hackers are always finding ways to exploit systems for other uses.

Apple last month released iOS 17.2, its biggest iPhone software update since iOS 17.0, with 60 new features. Now, as of Jan. 22, we have iOS 17.3. Overall, it's not the behemoth software update that iOS 17.2 was, but it has a few exciting new things you'll definitely want to know about.

There are countless tutorials online that show how to use Netstat and Tasklist to find an intruder on your computer. But with a few PowerShell functions, it's possible for a hacker to evade detection from the almighty command line.

While Jack Daniel's is one of the most iconic brands in the liquor business, when it comes to augmented reality marketing, it's joining a long list of others telling a very familiar story in the growing marketing medium.

The recent pitfalls and media fallout hitting Facebook hasn't stopped the social media giant from looking to the future.

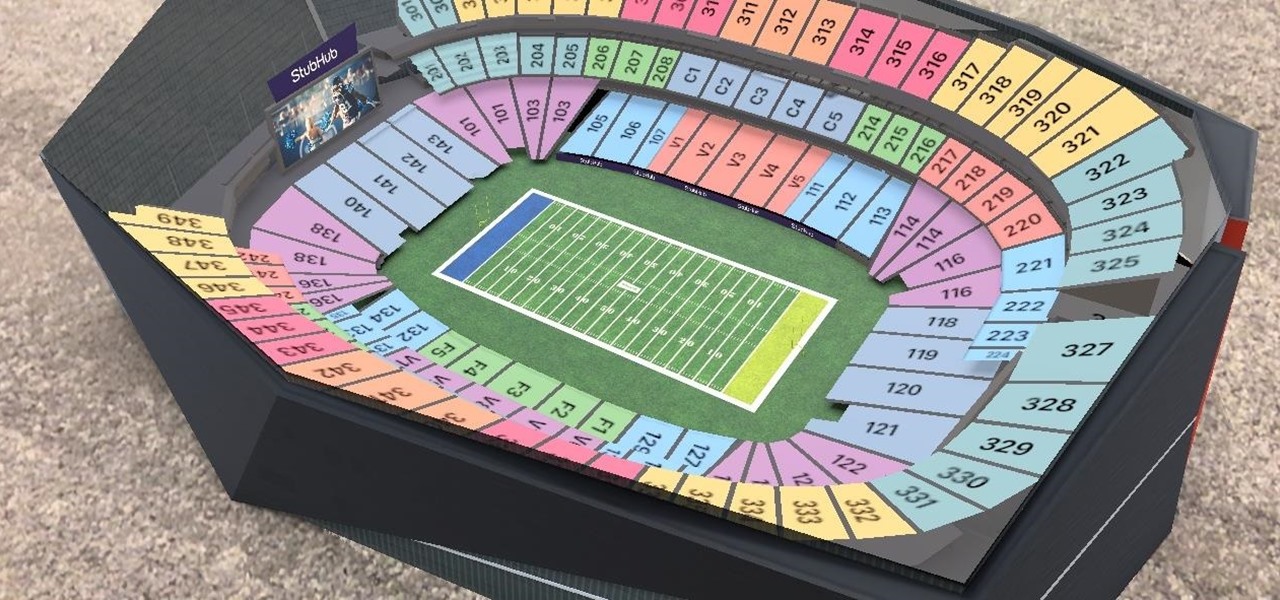
While the Minnesota Vikings have a realistic chance to become the first team to play in a Super Bowl on their home field, there will still be fans attending Super Bowl LII who will be in unfamiliar surroundings.

File inclusion can allow an attacker to view files on a remote host they shouldn't be able to see, and it can even allow the attacker to run code on a target.

When it comes to identifying what's fashionable on the runway, including cutting edge tech that bleeds into the mainstream of style, Vogue magazine stands at the top of the list.

Last month, BMW rolled out its playful take on augmented reality with Snapchat, and now the automaker is bringing that same immersive computing whimsy to iOS directly.

In one of my previous articles, I discussed ShinoBot, a remote administration tool that makes itself obvious. The goal is to see if the user could detect a remote administration tool or RAT on their system. In this article, I'll be demonstrating the use of Pupy, an actual RAT, on a target Ubuntu 16.04 server.

Being part of the wild frontier is amazing. It doesn't take much to blow minds of first time mixed reality users — merely placing a canned hologram in the room is enough. However, once that childlike wonder fades, we need to add more substance to create lasting impressions.

In a move that confirms previous speculation, Apple has placed a large OLED display order from Samsung for its next iPhone. At 70 million display units, the order is a large one to be sure, but when stacked against previous iPhone sales, it's no wonder the rumors say there won't be enough 2017 iPhones to meet demand.

Today I will show you how to make a metasploit exploit really quickly. This tutorial is mainly applied to stack based buffer overflows and seh buffer overflows exploits .There is a simple way for rop exploits too but I will dedicate a special tutorial on this subject.

It sounded great on the surface when Microsoft announced that existing Windows 7 or 8 users would be able to upgrade to Windows 10 for free, but the execution so far has left a lot to be desired. Upgrading from an existing installation is relatively easy, but when you start with a clean install of Windows 10, you run into some problems.

This is a very adorable looking nail design that I tried a few days back on my valentines day list of 'nails to do' ! It worked out exactly as I had planned , though during the execution it looked as if it may not, and I was happy enough to post this design online and share it with my viewers!

Format strings are a handy way for programmers to whip up a string from several variables. They are designed to save the programmer time and allow their code to look much cleaner. Unbeknownst to some programmers, format strings can also be used by an attacker to compromise their entire program. In this guide, we are going to look at just how we can use a format string to exploit a running program.

The public leaks of NSA tools and information have led to the release of previously secret zero-day exploits such as EternalBlue, which was used in the notorious WannaCry ransomware attack. Despite multiple patches being released, many users have failed to update their systems, so many devices are still vulnerable to these now-public attacks.

The first headset running on the Qualcomm Snapdragon XR2 chipset from an original equipment manufacturer is official.

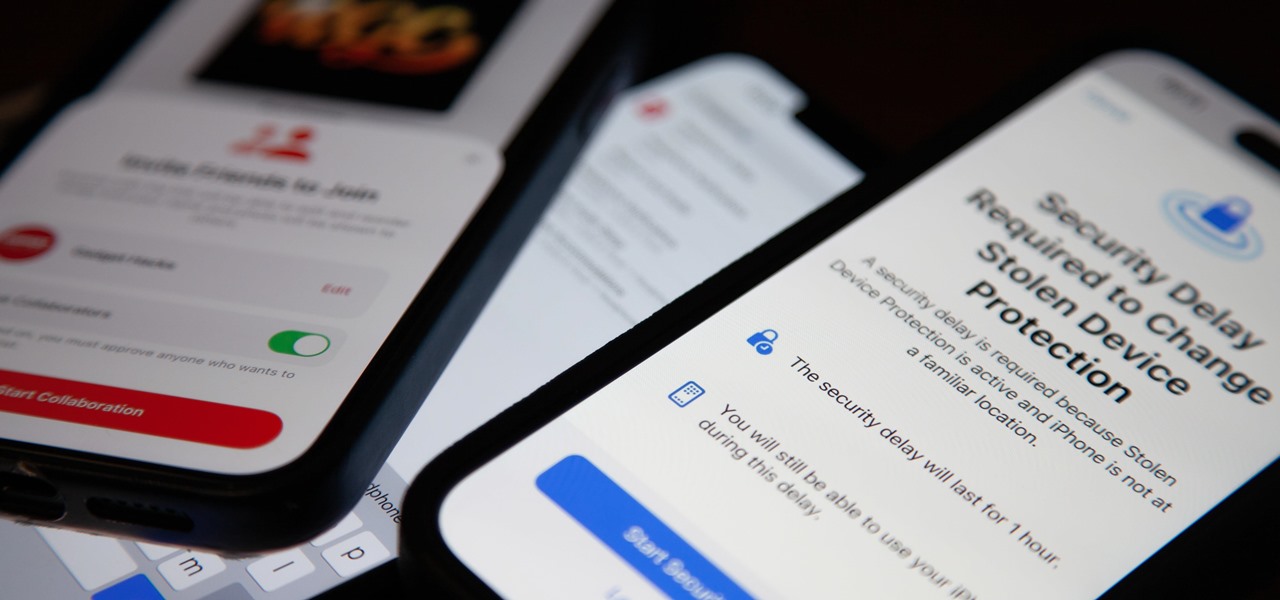
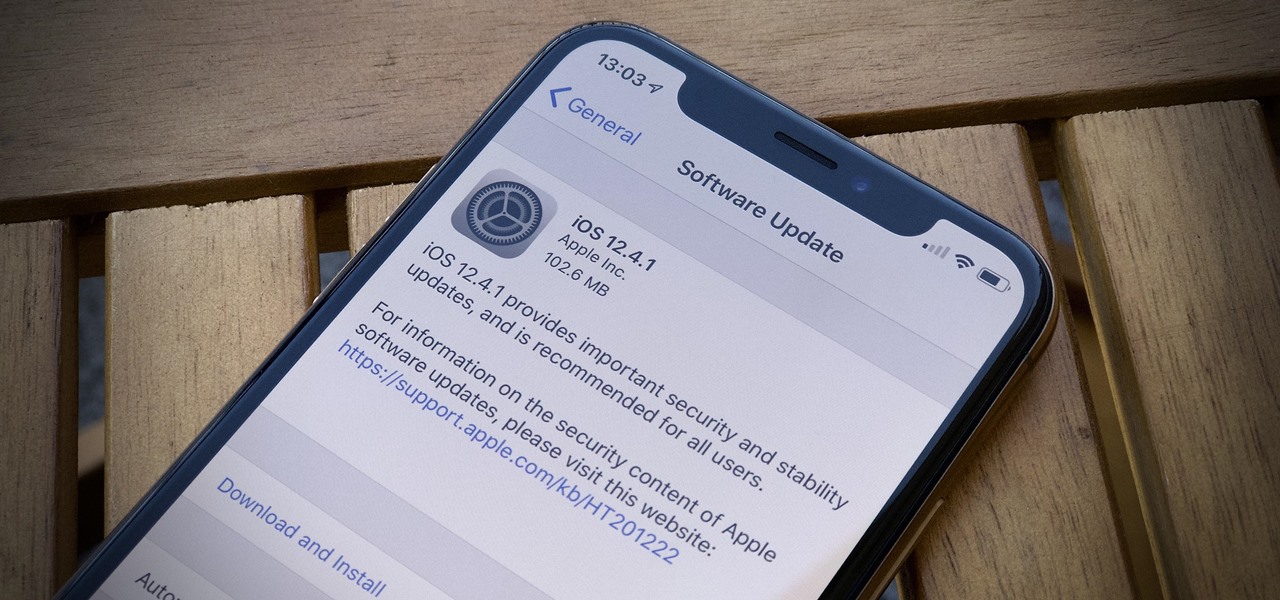
While all eyes might be on the next beta release for iOS 13, Apple is still pumping out updates for iOS 12. The company released iOS 12.4.1, the first update since iOS 12.4, on Aug. 26. The latest update includes a patch for the jailbreak vulnerability recently discovered in 12.4. One month later, on Sept. 26, iOS 12.4.2 came out for older iPhone models.

On Monday, the world watched in horror as the historic Notre Dame Cathedral went up in flames in Paris.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

With an ordinary birthday card, we can introduce a physical device which contains malicious files into someone's home and deceive them into inserting the device into a computer.

Continuing its unrelenting (and mostly successful) campaign against Snapchat, on Tuesday, Facebook announced the addition of "World Effects" to its Messenger app.

With the advent of ARKit, apps that can place virtual furniture in a real room have become nearly a universal practice for furniture retailers, with Pottery Barn being the latest to join the fray.

Apple CEO Tim Cook told us that augmented reality would change everything, and now we have a better idea of exactly what he meant.

Ever since the planet went crazy trying to find augmented reality creatures in Pokémon GO, we've been waiting for the next virtual object game capable of delivering a similar hit. And now, we might finally have one coming, direct from the magical world of Harry Potter.