Welcome back, my fledgling hackers! Over the years, we have examined multiple ways to own, exploit, or compromise a system. On the other hand, we have not spent a lot of time on denial-of-service (DoS) attacks.

When opening a link or sharing a photo, your Android device will bring up a list of possible applications that you can complete the action with. However, some of the apps included you never use or didn't even know existed, and this leads to unnecessary clutter. Fortunately, if you're rooted, there's an easy way to remove apps from the "Open with" and "Share via" lists.

When you're expecting an important call or text, it's pretty annoying to hear or feel your phone go off just to find out it was your reminders app telling you that you need to buy more contact lenses. Not quite as annoying as phantom phone vibrations, but it's up there.

In today's world of social media, there's really only two powerhouses—Facebook and Twitter. And those of you with Twitter accounts know the power of a Tweet. Getting more followers means reaching more people, but the vast majority of Tweeters are following only a handful of Twitterers themselves. Do you ever wonder why them? What's so special about these selected followed users? Is it worth it to follow them, too? That's up to you, but if you're searching for more people to follow, then it's ...
After you launch Outlook 2010 in your computer, you will see the Ribbon strip immediately in the main window. The button for writing a new e-mail is separated from a button for creating new items in the calendar, contact list or task manager. An independent Quick Steps section offers functions allowing you to move a message into different folders, to save it into a calendar as a meeting reminder, to quickly forward it to a chosen person or to more people and to forward it with a FYI note. If ...
You want to know how to get extreme scores in the flash game Pool Practice? This is how. Watch this video tutorial to learn how to cheat in the flash game Pool Practice (01/01/10).

Can't tell if you need sunscreen or a rain poncho? Checking the forecast is a breeze. Learn how to check the weather on your iphone.

New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 616th installment in their series of digital spreadsheet magic tricks, you'll learn how to use the LARGE and SMALL functions to retrieve the 1st, 2nd, and 3rd largest values from a list. You'll also see how to do each of the following:

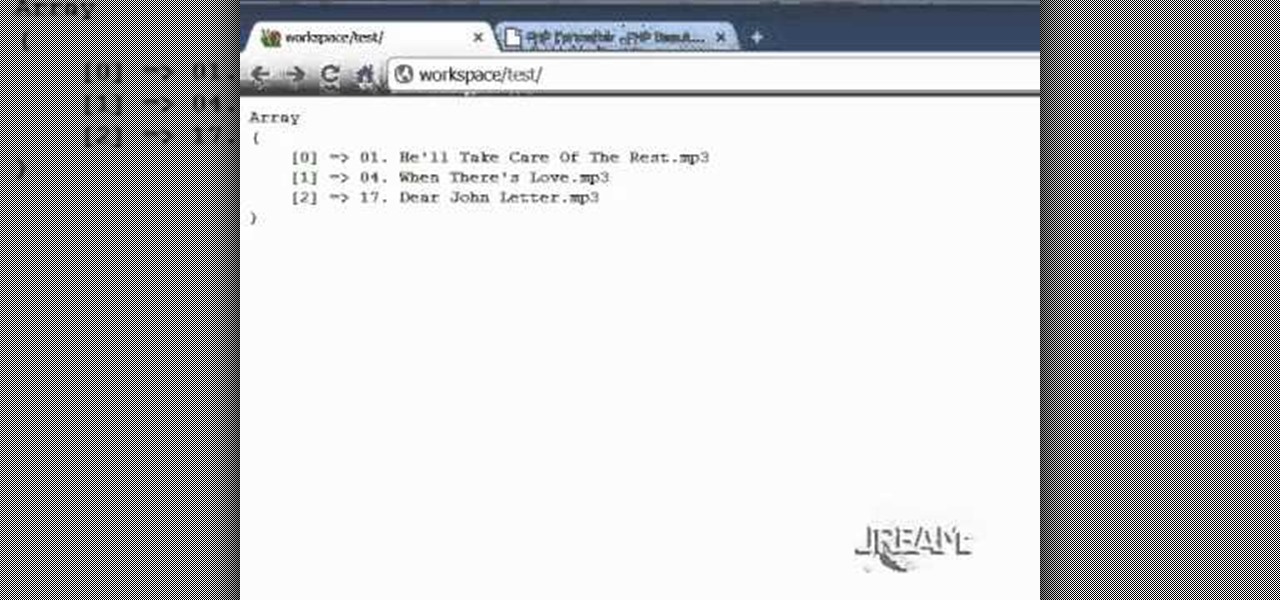
If you're programming with PHP and you generate a list of music files, you'll want to find a way to play them. This video shows how to use the Yahoo Media Player to play the list of mp3s you've created, with your PHP coding.

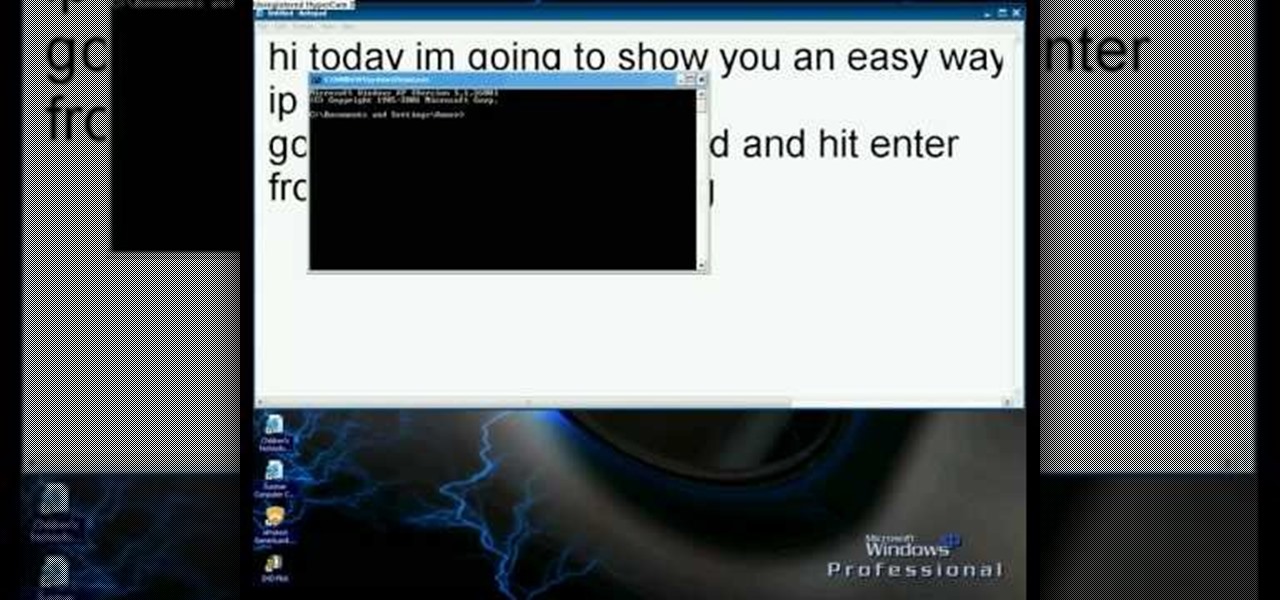
In this video we learn how to find your IP address with the Command prompt. First, go to the start menu on your desktop. Then, find the run box and type in "cmd". After this, hit "enter" and then a black command prompt will show up on your screen. Next, type in "ip config" and then hit the enter button again. Now, a list of information will appear on the black screen. Look down the list to find the IP address listed on the page. Once you have this, you should write down your IP address and th...

In this clip, you'll learn how to make and set up a mailing list with GoDaddy and Mailman. It's easy! So easy, in fact, that this helpful how-to can present a complete overview of the process in just over three minutes. For more information, including detailed, step-by-step instructions, take a look.

Using the Cydia App, you can delete individual calls in your recent caller list. This enables you to delete single calls, line by line, instead of having to clear your entire recent call list.

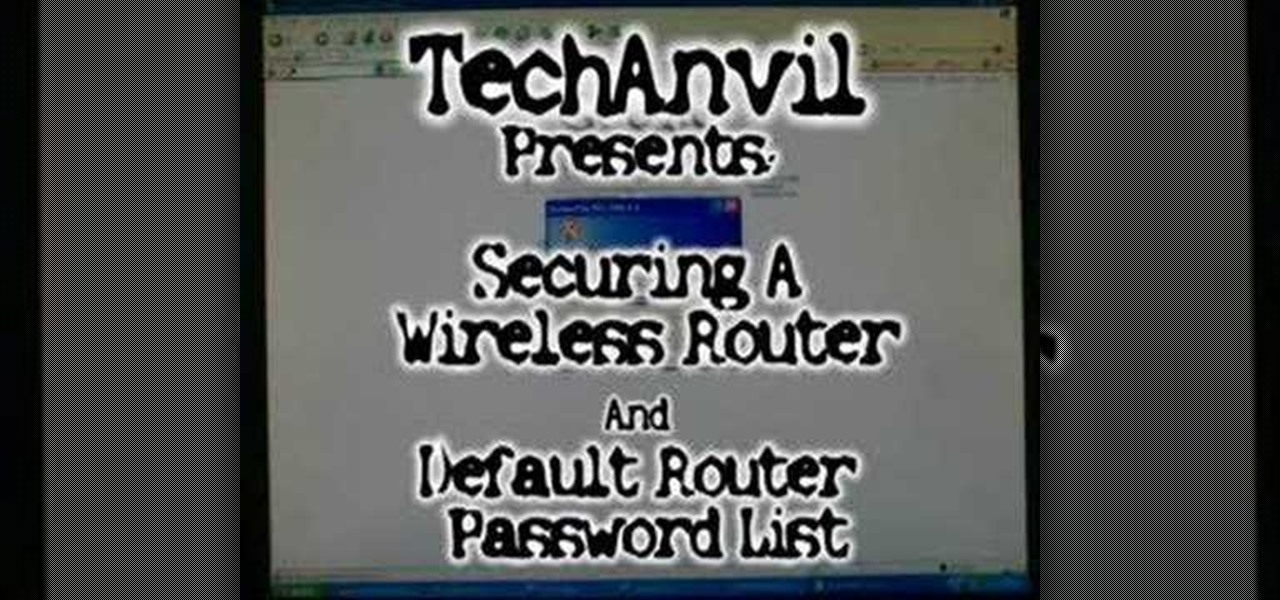
This video walks through basic security configuration for a WRT54G Wireless Router. Also provides a default password list.

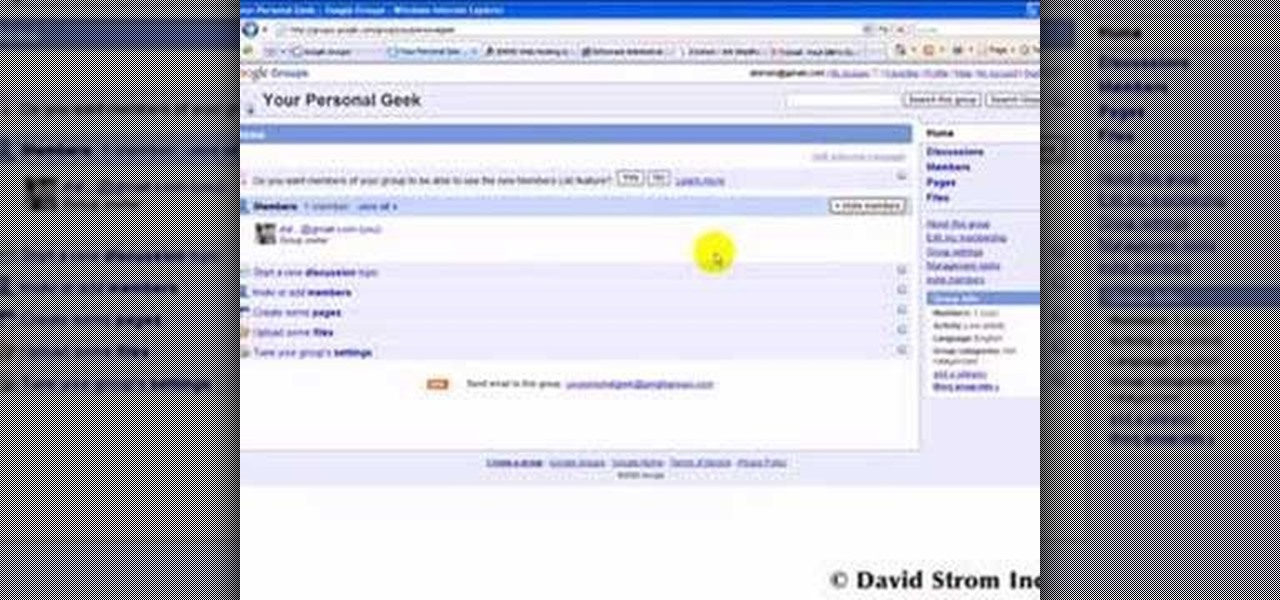
David Strom shows you how to pick from aong Google Groups, Mailman hosted by EMWD.com, and iContact and how to get started with your own mailing list

Brute-forcing is an easy way of discovering weak login credentials and is often one of the first steps when a hacker finds network services running on a network they gain access to. For beginners and experienced hackers alike, it's useful to have access to the right tools to discover, classify, and then launch customized brute-force attacks against a target. BruteDum does it all from a single framework.

One of the coolest things about Android is the massive development community behind it. These developers keep on cooking up new things even after official support has stopped for an older device. It breathes new life into somewhat forgotten devices, which is always great news. With Android 10 out, it's time to see what phones will get the custom ROM treatment.

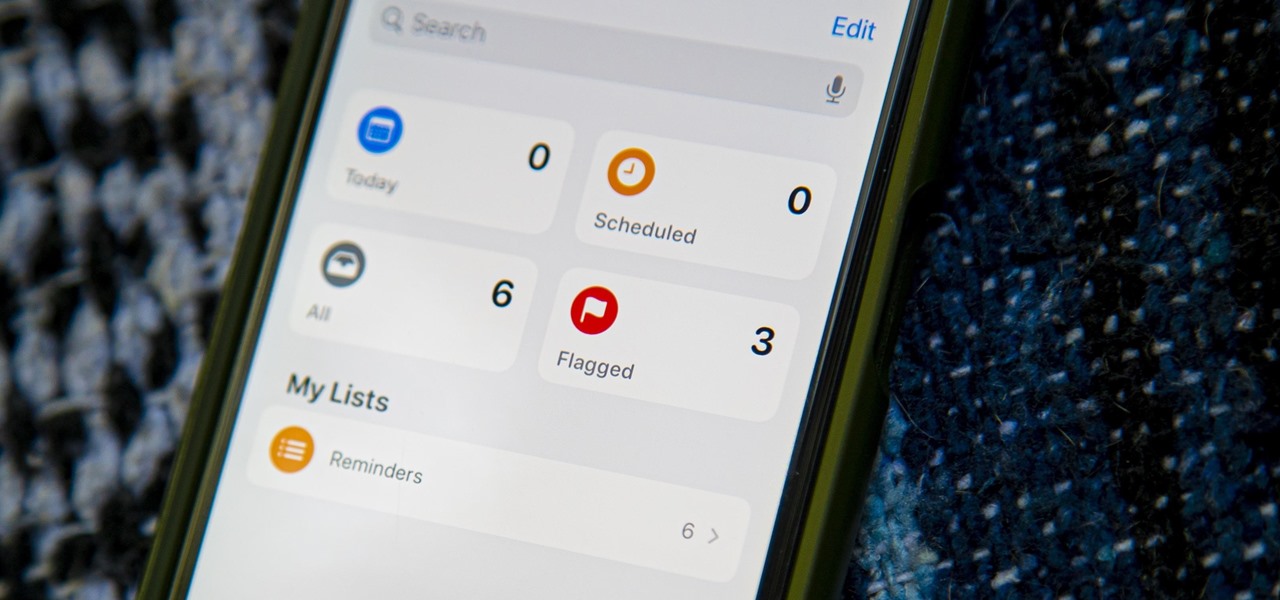
Reminders may have received the biggest update out of all the native Apple apps on iOS 13. Among other things, the new Reminders app now comes packed with smart lists to make it easier find things, and a flagging feature to help you better manage your most important reminders.

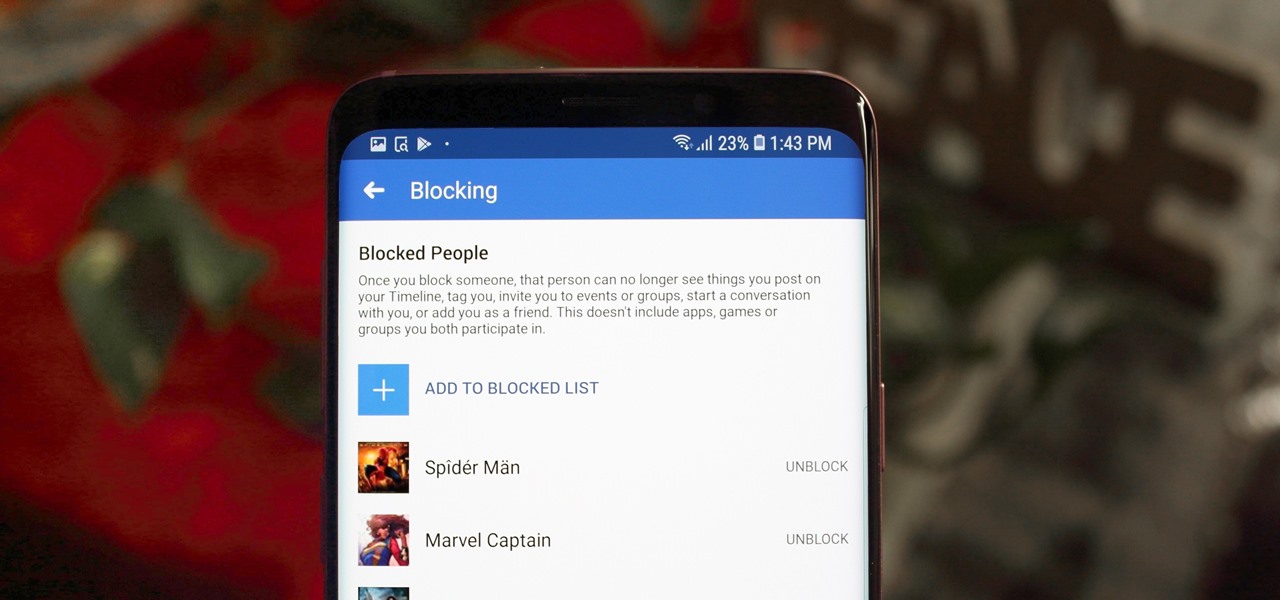
Whether it's an ex you can't stand, that annoyingly political friend of a friend, or good old fashioned trolls, the block feature on Facebook can be a great way to de-stress your feed. It will keep people from contacting you, and it will also prevent them from viewing your profile altogether. It's not just a tool for the full desktop website — in fact, the blocked list is easy to manage right from your phone.

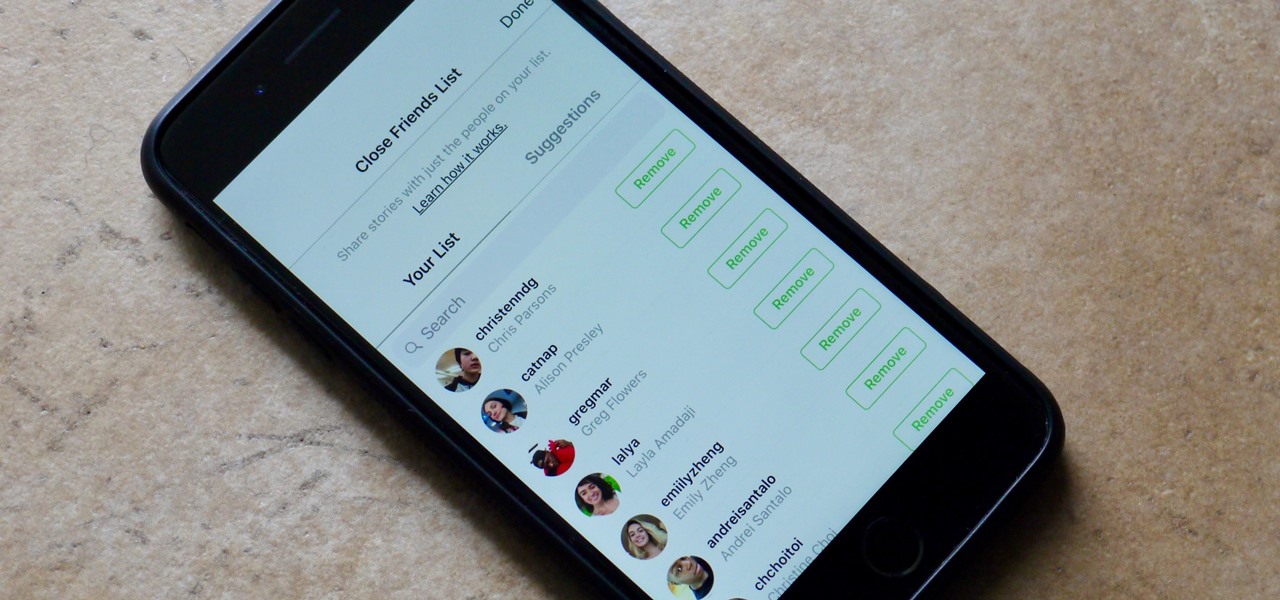
Stories make sharing your day-to-day highlights fun on Instagram. However, other than choosing who to hide stories from, by default, stories don't have much privacy control, especially if your Instagram account happens to be public. Instagram recognizes this flaw, which is what its "Close Friends List" is all about.

It appears a privacy lawsuit that began five years ago is about to come to an end, and you might get some money out of it.

While attempting to hack a web app, there may come a point where the attacker may have to escape the default directory in order to access unauthorized files. This is known as a directory traversal attack. Much as the name implies, this attack involved traversing the servers directories. But in order to move to an unauthorized directory, we need to know where those directories are. Today we'll be building a tool to brute force these directory locations based on HTTP response codes. Before we g...

proxyFinderEnterprise is a tools for find proxylist . in this topic you learn how to use this tools for find a proxy list .

Welcome back! In the last iteration of how to train your python, we talked about functions, and we even made our own! We're going to move on to more types of data arrays (much like lists) in today's discussion.

Welcome back! Sorry for being so quiet, I've been rather busy with this project lately! Anyways, in the last iteration of how to train your python, we covered lists. Today we'll be introducing iteration and the two loops python has to offer, for and while. Also, we'll be covering a couple general use functions. So, let's get started!

Amazon makes it exceptionally easy to purchase anything you want in just a few minutes. From textbooks for school to live ladybugs, its more surprising when you can't have something delivered to your doorstep in a few day's time.

Accessing and getting in touch with your favorite contacts has never been easier thanks to the "Friends" feature on the Apple Watch. However, this only applies to users who are running watchOS 2.2.2 and lower. When Apple issued watchOS 3, the "Friends" option was completely removed. So if you're running watchOS 3 or higher, you won't be able to follow these instructions.

When you hear a song you like but can't quite catch enough of its lyrics, it can be nearly impossible to search for it online. That's where Shazam comes in. For the past decade, they've been making music easier for us to identify by analyzing a track's acoustic footprint, requiring only a few seconds of audio for accurate identification.

As soon as you plug a set of headphones into a Samsung Galaxy series device, a bar pops up in the notification tray that lets you select from a list of "recommended apps" for earphones. It's a convenient little feature that shows the apps you're most likely to use based on previous activity.

What separates the work habits of the ultra-productive from us mere mortals struggling to check items off our never ending to-do lists? While the answer to that question is by no means simple, one undeniable factor in their success is a clearly defined, highly organized workflow.

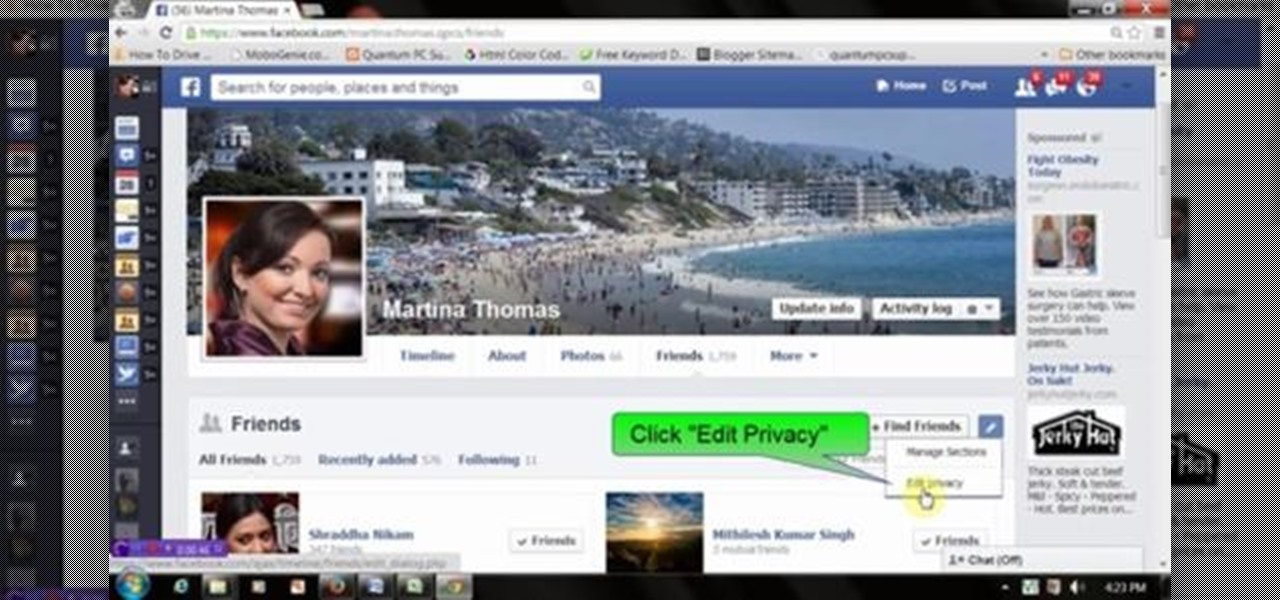
This video will show you how to hide friend and follower list on Facebook. If you set "Friends" your friend information will be invisible to those who are not your friends. Watch the video and follow all the steps. Employ the technique in your Facebook account.

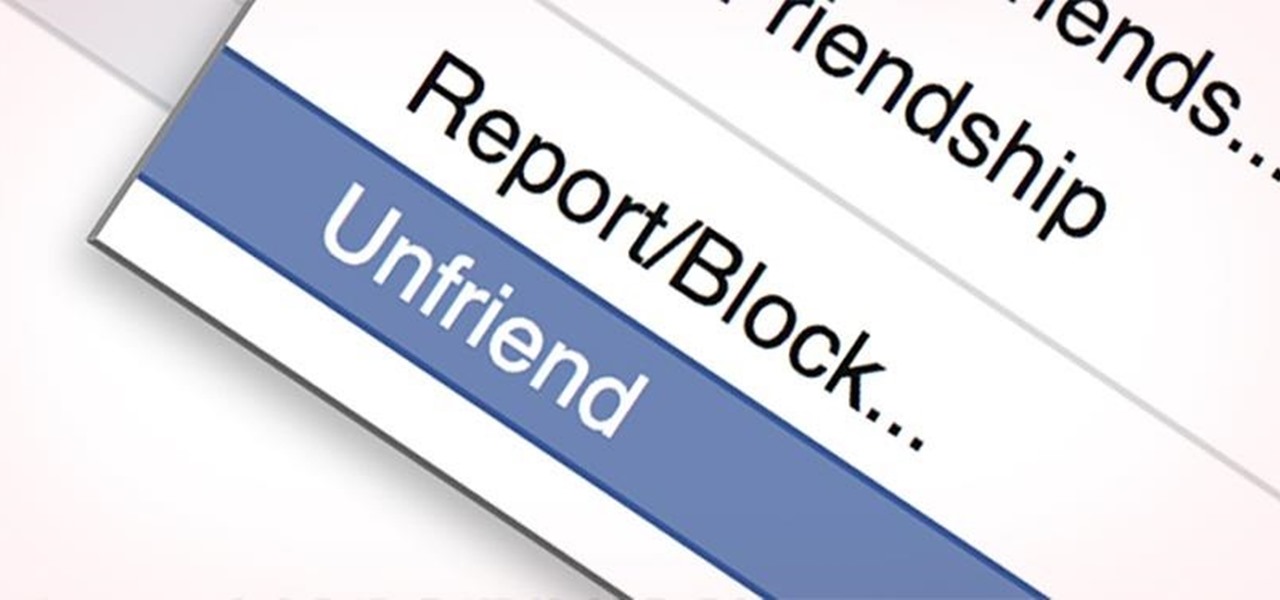
Admit it: you haven't talked to more than 70 percent of your Facebook friends in the last year. Whether you barely know the names crowding your friends list, or have vague memories of high school Spanish class with them, Facebook friends are easy to find and difficult to get rid of.

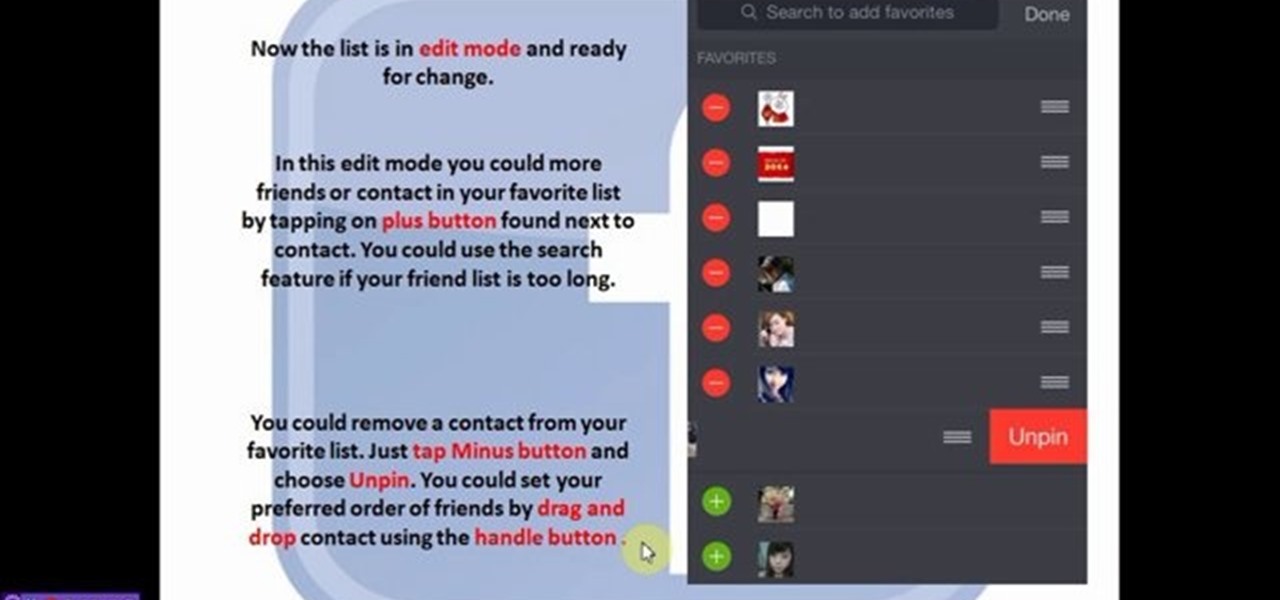
You could pin your favorite friends on top of chat list. This will save your time of searching to chat with your favorite friends. This feature is available for IOS and Android phone only. Follow the video and do it yourself.

This video will guide you how to disable or delete recent document list in MS Word 2007. The same procedure is also applicable for MS excel also. Follow the steps and employ the technique in your PC.

We know that Facebook is a very useful social media sites. This video will help you how to hide friends list on Facebook from others.

Just in time for Hanukkah! my easy vegan latke recipe (potato pancakes). You can find the full printable recipe here or you can watch me make them on YouTube in the video below. You'll find the ingredient list below the video.

The NSA's massive internet spying efforts will continue. In President Obama's latest press conference, he went public to (in so many words) say that the NSA's spying efforts will continue uninterrupted. This, coming just weeks after the Amash Amendment which would have defunded the program, was narrowly defeated in the House (you can check if your congressmen voted against it here).

Thousands of Android users have been disappointed to learn that getting the latest firmware update isn't as easy as it sounds. Some really popular phones like the Samsung Galaxy S III just started getting the Jelly Bean upgrade, with the update continuing to roll out over the next couple of weeks overseas. All of the stateside S3 users will have to wait even longer for Android 4.1.

It seems like there's never any breaks in air travel when it comes to money. The airfares just keep rising, and now most major airlines charge for all checked baggage, so carry-ons are the way to go. But you need to know how to take it easy with your packing list. Pack light and travel without the burden of that extra $15 or more per bag.

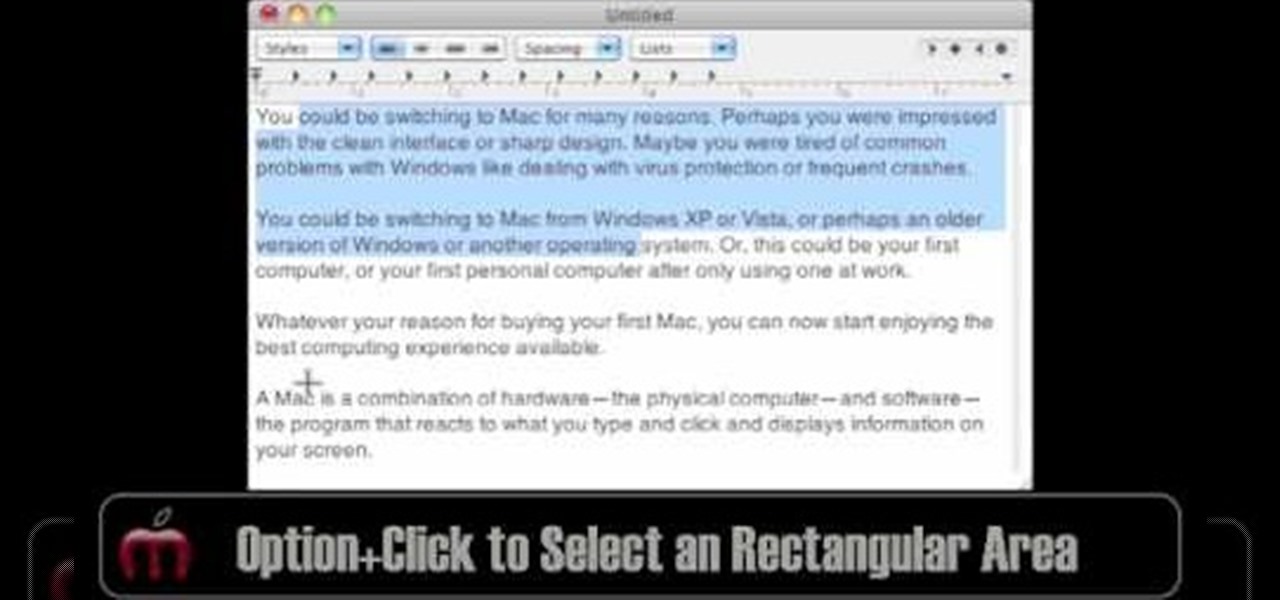
In this video, Gary from MacMost demonstrates how to select items on a Mac computer. He explains that there are different ways of selecting items, both with the mouse and with the keyboard. Click to select a single item, and click an empty space to clear the selection. Hold Command or Shift to add to a selection or remove items from the selected group. Drag around an area to select multiple items, and use Command and drag to add more areas. To select items in a list, click to select a single ...

Need to leave town earlier or later than planned? Flying stand-by is not as simple as it used to be. Learn how to fly stand by - you never know when it may be necessary.