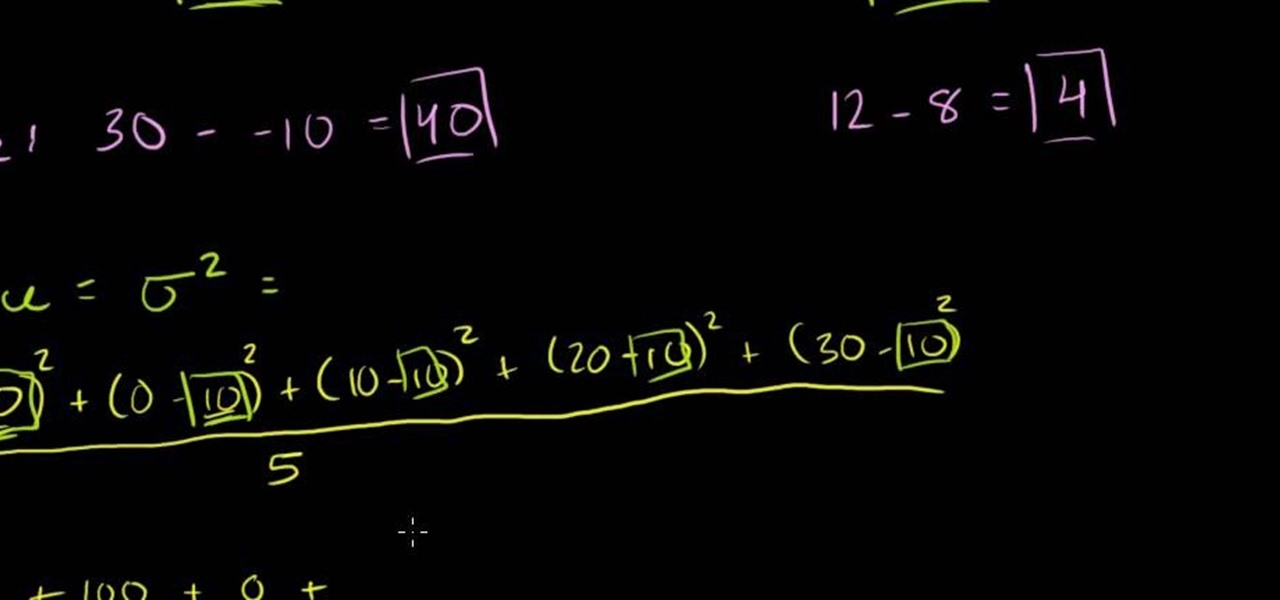
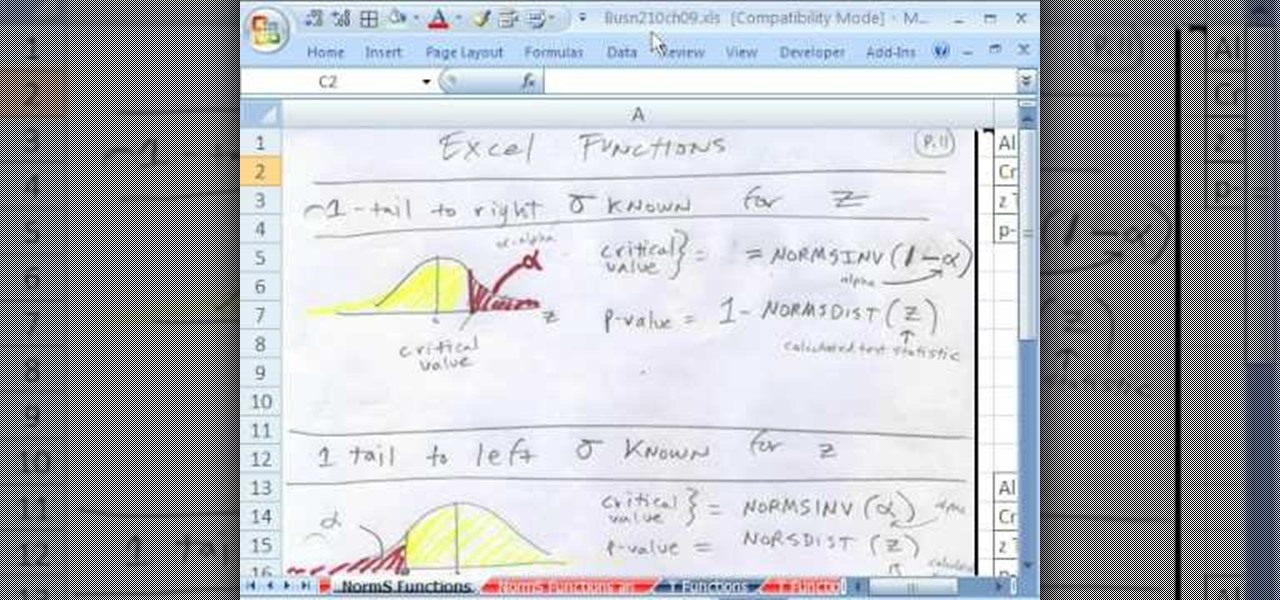
If you use Microsoft Excel on a regular basis, odds are you work with numbers. Put those numbers to work. Statistical analysis allows you to find patterns, trends and probabilities within your data. In this MS Excel tutorial from everyone's favorite Excel guru, YouTube's ExcelsFun, the 89th installment in his "Excel Statistics" series of free video lessons, you'll learn how to use the NORMSINV function for critical values and the NORSDIST function for p-values.
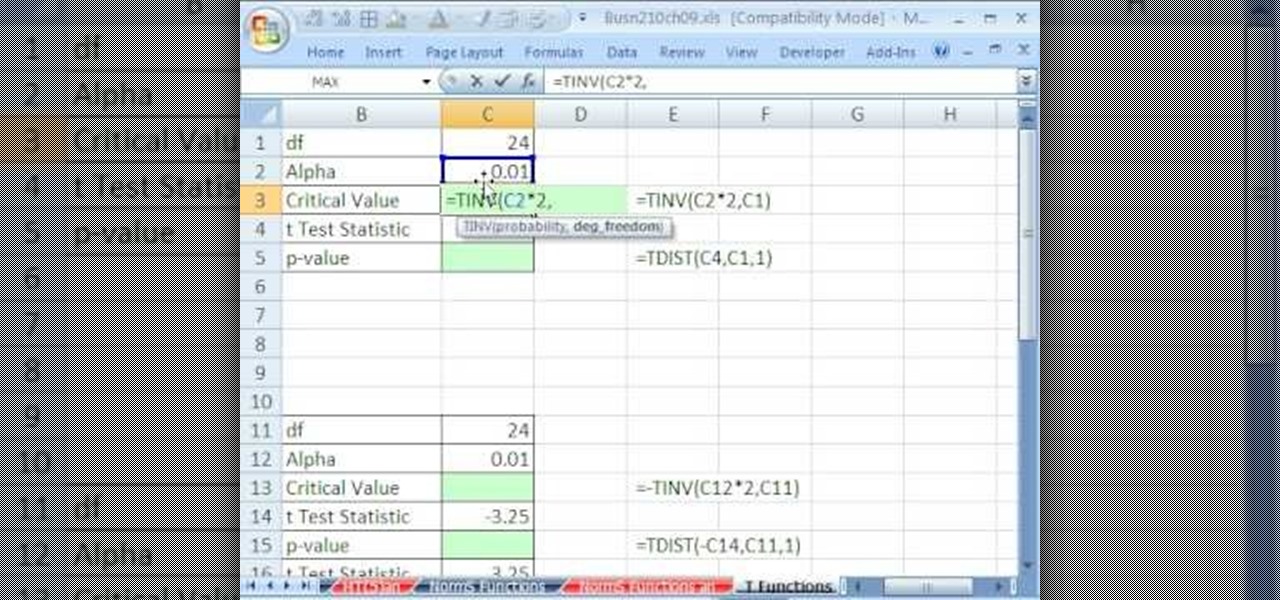
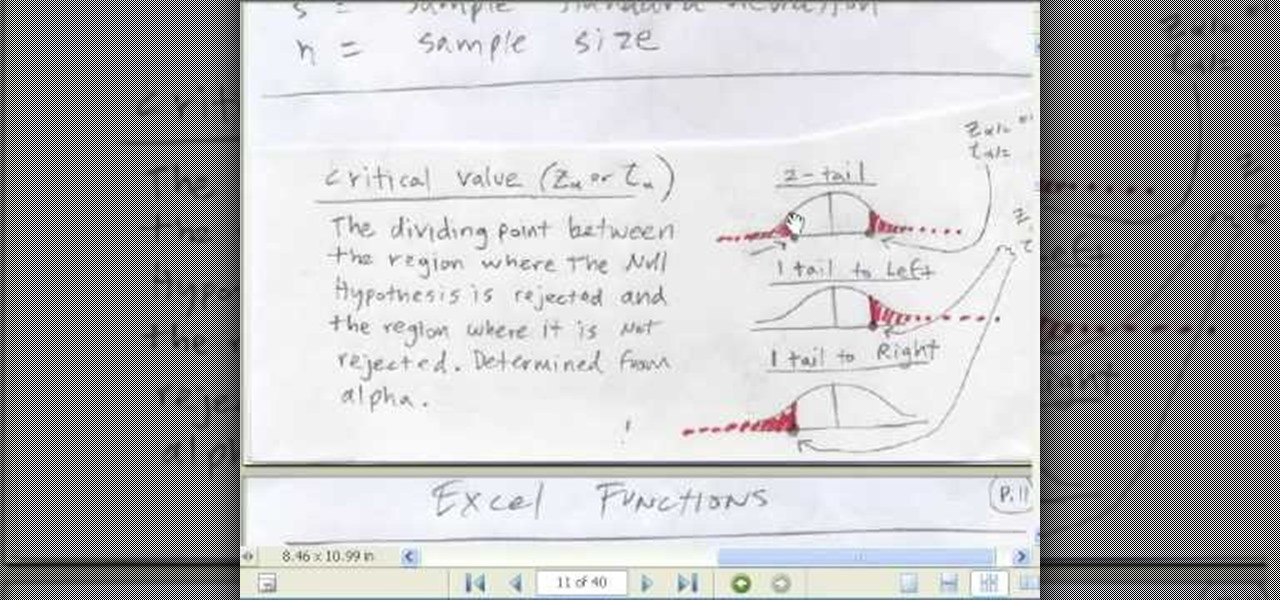
If you use Microsoft Excel on a regular basis, odds are you work with numbers. Put those numbers to work. Statistical analysis allows you to find patterns, trends and probabilities within your data. In this MS Excel tutorial from everyone's favorite Excel guru, YouTube's ExcelsFun, the 91st installment in his "Excel Statistics" series of free video lessons, you'll learn how to use TINV and TDIST functions to find critical values given an unknown sigma value.
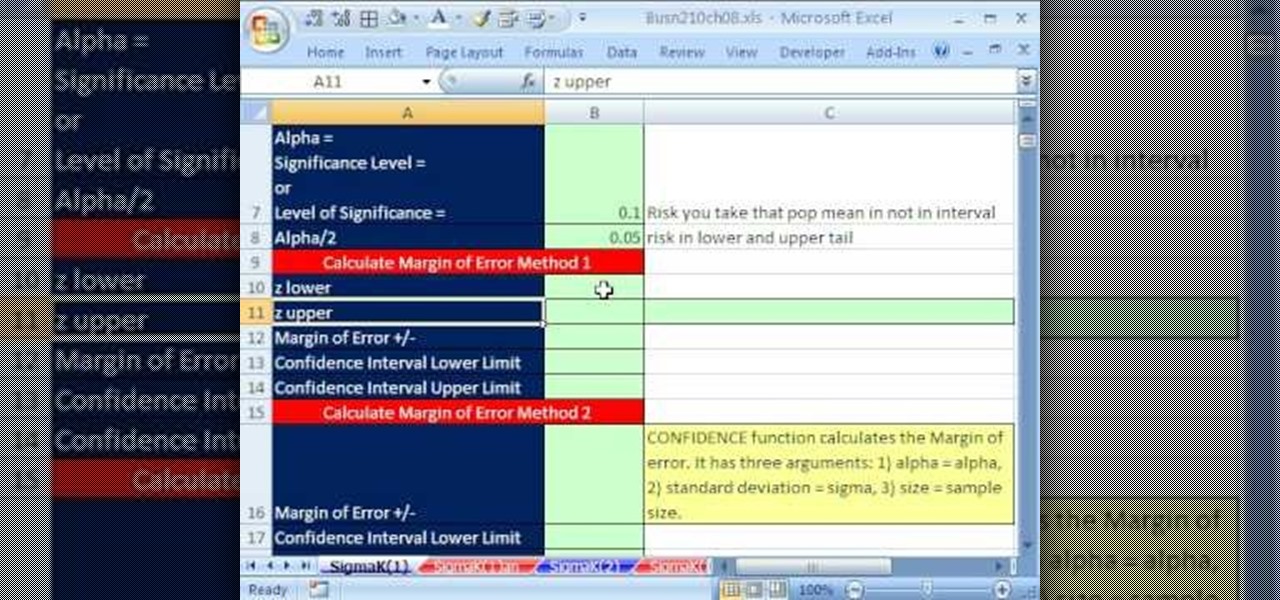
If you use Microsoft Excel on a regular basis, odds are you work with numbers. Put those numbers to work. Statistical analysis allows you to find patterns, trends and probabilities within your data. In this MS Excel tutorial from everyone's favorite Excel guru, YouTube's ExcelsFun, the 80th installment in his "Excel Statistics" series of free video lessons, you'll learn how to construct confidence intervals when the sigma is known known using the CONFIDENCE and NORMSINV functions.
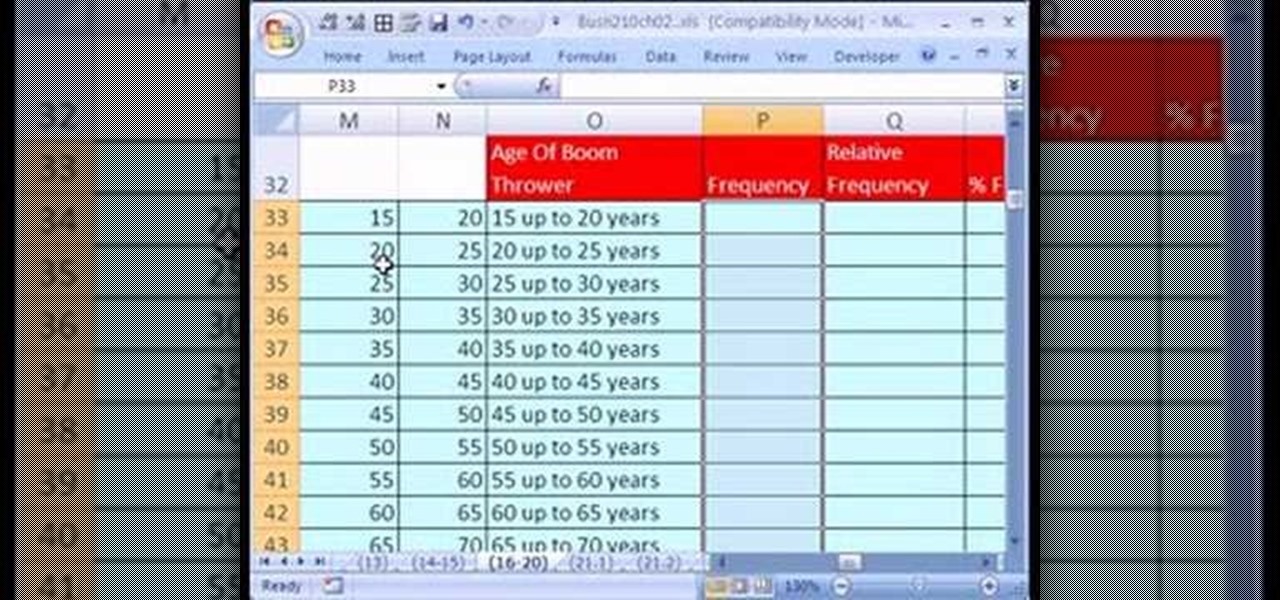
If you use Microsoft Excel on a regular basis, odds are you work with numbers. Put those numbers to work. Statistical analysis allows you to find patterns, trends and probabilities within your data. In this MS Excel tutorial from everyone's favorite Excel guru, YouTube's ExcelsFun, the 21st installment in his "Excel Statistics" series of free video lessons, you'll learn how to build labels and counting formulas for a frequency distribution.
If you use Microsoft Excel on a regular basis, odds are you work with numbers. Put those numbers to work. Statistical analysis allows you to find patterns, trends and probabilities within your data. In this MS Excel tutorial from everyone's favorite Excel guru, YouTube's ExcelsFun, the 87th installment in his "Excel Statistics" series of free video lessons, you'll learn how to use NORMSINV to test a hypothesis with population standard deviation (sigma) known and proportions.
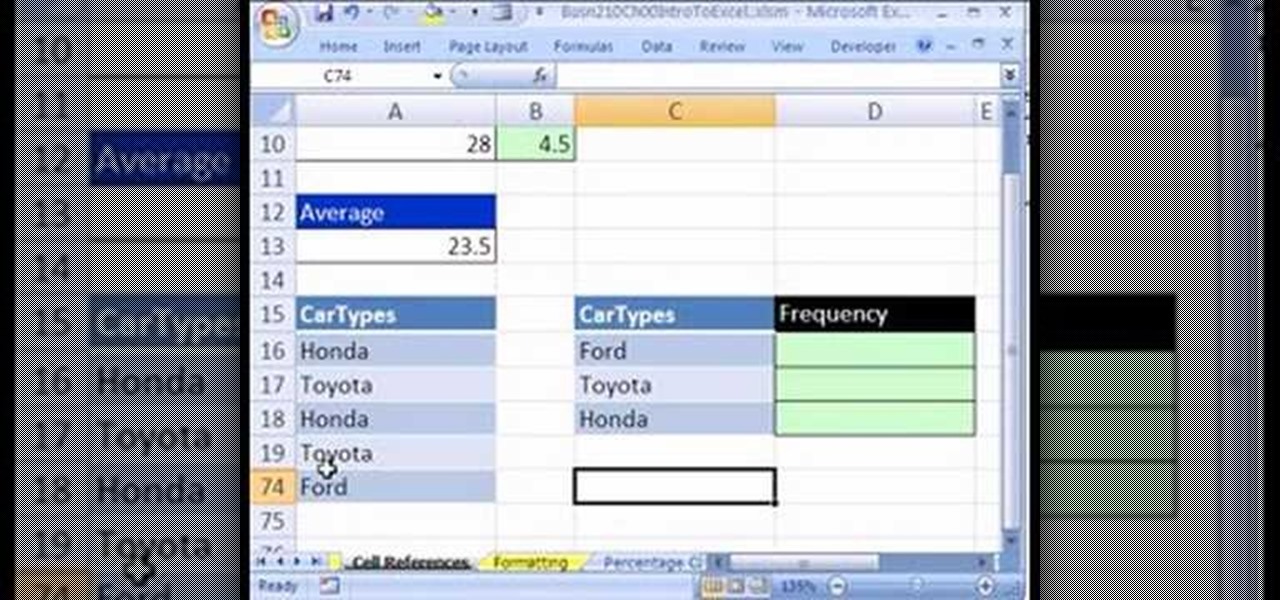
If you use Microsoft Excel on a regular basis, odds are you work with numbers. Put those numbers to work. Statistical analysis allows you to find patterns, trends and probabilities within your data. In this MS Excel tutorial from everyone's favorite Excel guru, YouTube's ExcelsFun, the 5th installment in his "Excel Statistics" series of free video lessons, you'll learn how to use relative and absolute cell references to save time when writing formulas.

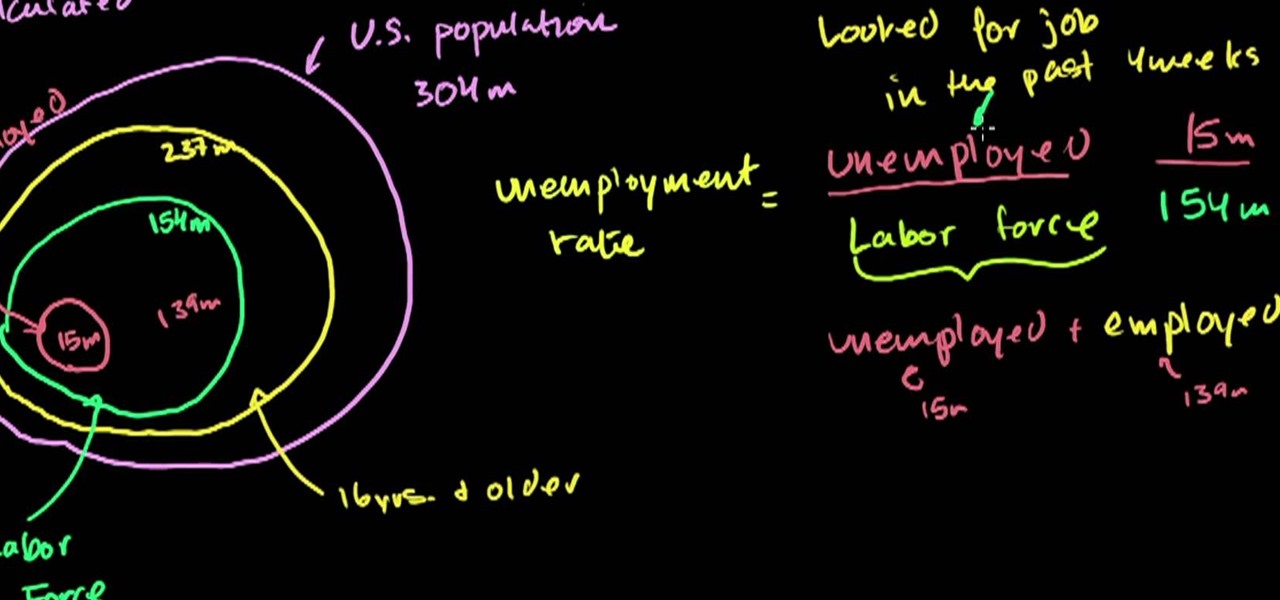
From Ramanujan to calculus co-creator Gottfried Leibniz, many of the world's best and brightest mathematical minds have belonged to autodidacts. And, thanks to the Internet, it's easier than ever to follow in their footsteps (or just study for that next big test). With this installment from Internet pedagogical superstar Salman Khan's series of free math tutorials, you'll learn how to calculate the US unemployment rate given the raw data.

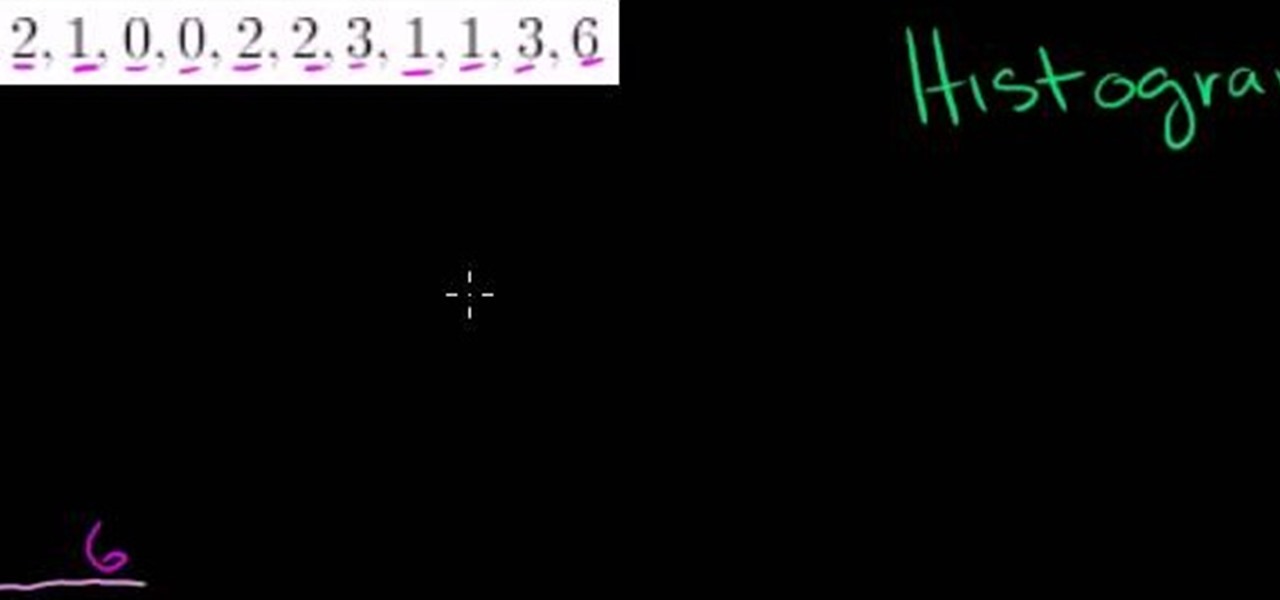
From Ramanujan to calculus co-creator Gottfried Leibniz, many of the world's best and brightest mathematical minds have belonged to autodidacts. And, thanks to the Internet, it's easier than ever to follow in their footsteps (or just study for that next big test). With this installment from Internet pedagogical superstar Salman Khan's series of free math tutorials, you'll learn how to create a simple histogram chart.

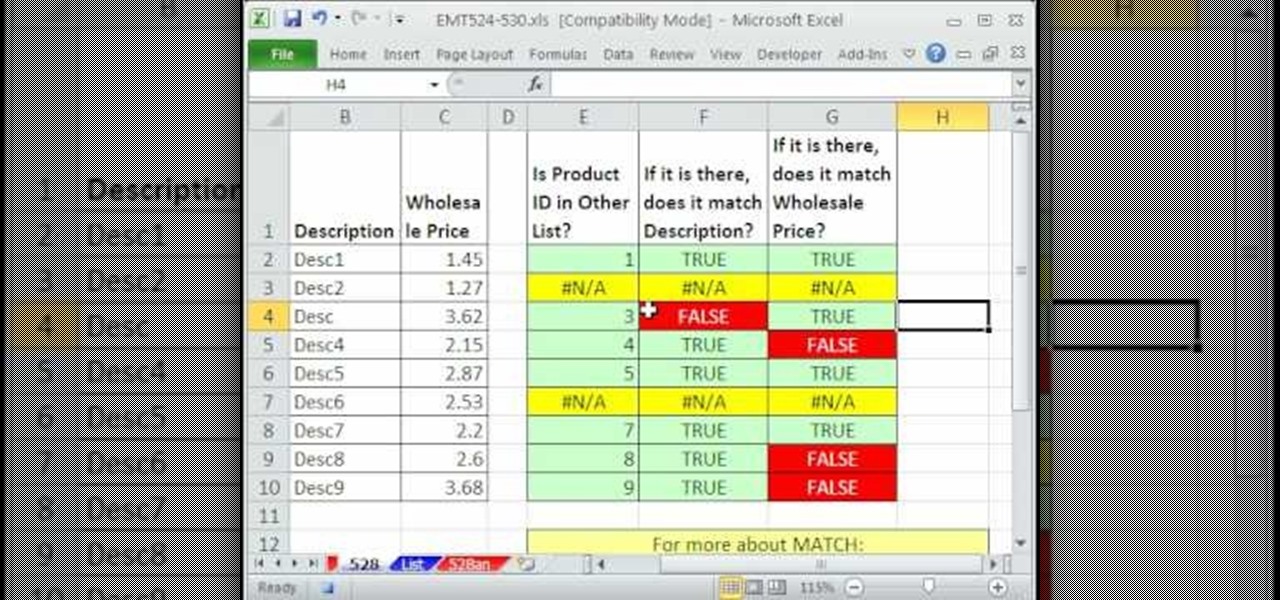
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 528th installment in their series of digital spreadsheet magic tricks, you'll learn how to check two data sets (lists & tables) to see if there are discrepancies using the MATCH and VLOOKUP functions.

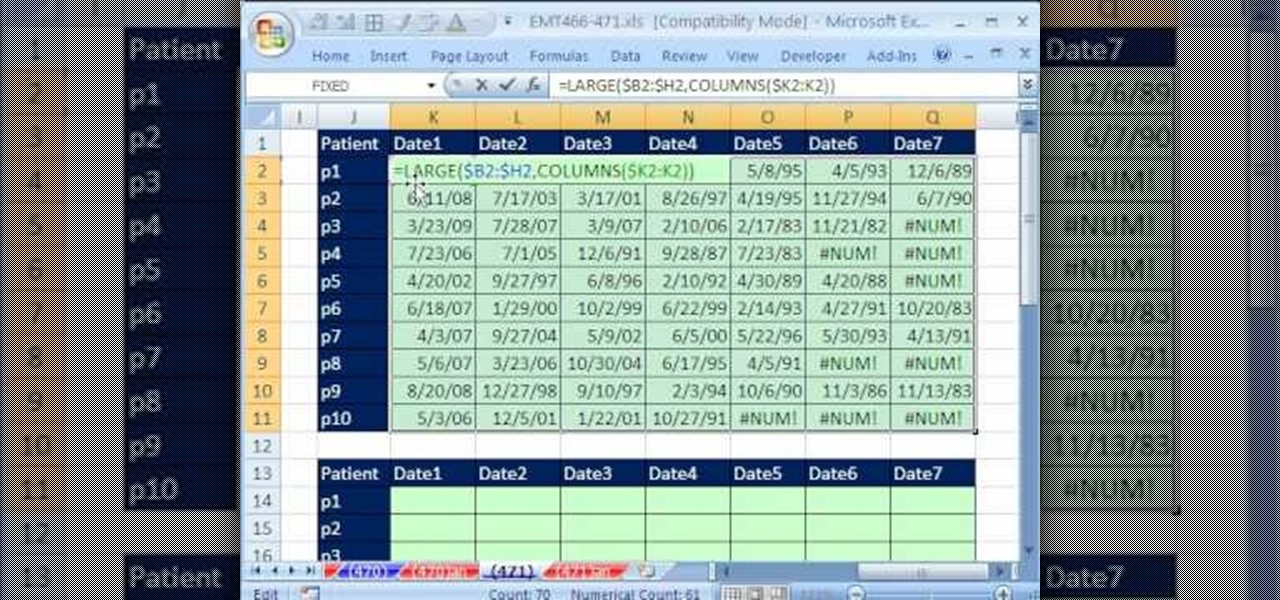
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 471st installment in their series of digital spreadsheet magic tricks, you'll learn how to sort horizontally with 3 different formulas that use the LARGE, SMALL, COLUMNS, IFERROR and IF functions.

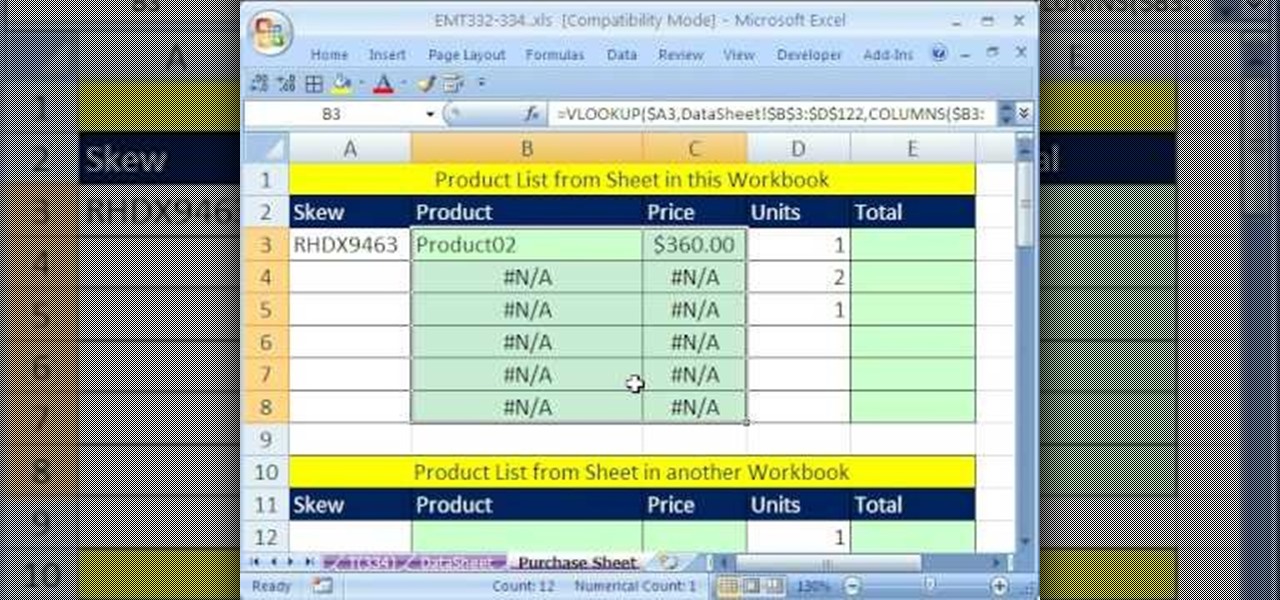
New to Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this Excel tutorial from ExcelIsFun, the 334th installment in their series of digital spreadsheet magic tricks, you'll learn how to use VLOOKUP & data validation to make an invoice when the product list is on a different sheet or different workbook.

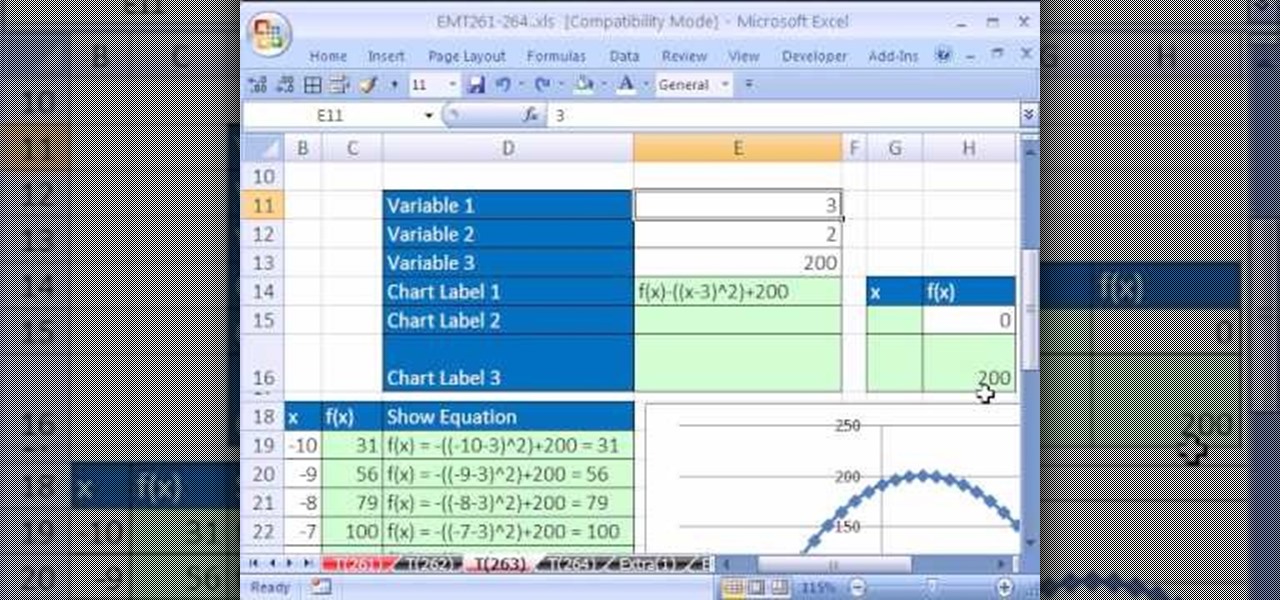
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this Excel tutorial from ExcelIsFun, the 263rd installment in their series of digital spreadsheet magic tricks, you'll learn how to create a completely dynamic math equation system (function of x) with formulas, data points, charts and chart labels.

From Ramanujan to calculus co-creator Gottfried Leibniz, many of the world's best and brightest mathematical minds have belonged to autodidacts. And, thanks to the Internet, it's easier than ever to follow in their footsteps (or just study for that next big test). With this installment from Internet pedagogical superstar Salman Khan's series of free math tutorials, you'll learn how to use statistical range, variance and standard deviation to measure dispersion in a data set.

Network mapping lets PC users organize multiple computers into a system that provides informational data access. This video tutorial shows how to set file sharing permissions and assign users designated privileges within a network. Establishing a network provides functionality within a workplace and facilitates virtual communication among users.

In this video one of the ultimate iPhone hackers, Jonathan A. Zdziarsk, demonstrates how to use a forensics toolkit to recover deleted text messages on an iPhone. But wait - there's more! Not only can you access text messages, but almost any other data on an iPhone as well. We can't be responsible for what you find though!

Accidentally deleted your address book? Got some sneaking suspicions you want to clear up? Got something to hide - permanently? In this video you'll learn what hardware and software you need and how to use it to recover deleted text messages, or, conversely, how to delete data permanently from your SIM card. Don't worry - we won't judge.

This shows a step by step method for using the Wii controller to output MIDI control to Apple Logic Pro and "conduct" MIDI with the Wii stick! This is a way cool Wii hack that makes the bluetooth controller work with Logic. You need to install another program to receive and control the data.

Here's a demo which shows a way to produce WAV sound files with TEXT using Photoshop or any photo editing software.

The Nessus vulnerability scanner, is the world-leader in active scanners, featuring high speed discovery, configuration auditing, asset profiling, sensitive data discovery and vulnerability analysis of your security posture. Nessus scanners can be distributed throughout an entire enterprise, inside DMZs, and across physically separate networks. In this network security video tutorial, you'll learn how to hack a network using Nessus 3.

Using morphs to pre-process UVs is a great trick for any version of modo. You can leverage the embedded morph data to massage a model in 3D prior to UV projection. If that doesn't make sense, watch the video and learn how to pre-process UVs using morphs in modo.

Learn how to use MapForce to map or transform XML data in a visual way, creating XSLT 1.0 or 2.0 transformation stylesheets, XQuery 1.0 documents, or program-code in Java or C# in this tutorial, which demonstrates a simple mapping from one XML schema to another. Take a look!

In this ASP.Net video lesson, you will learn how to display data in your ASP.NET 2.0 Web applications through some of the new databound controls.

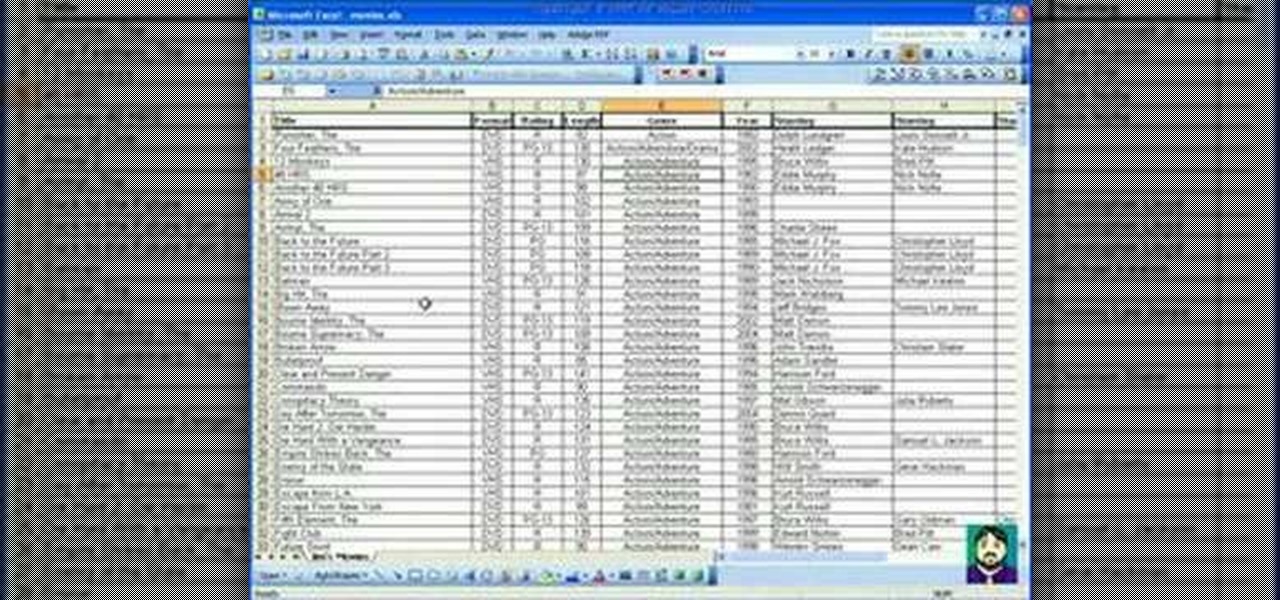
How to use Microsoft Excel as a simple database and how to organize and sort data on the fly.

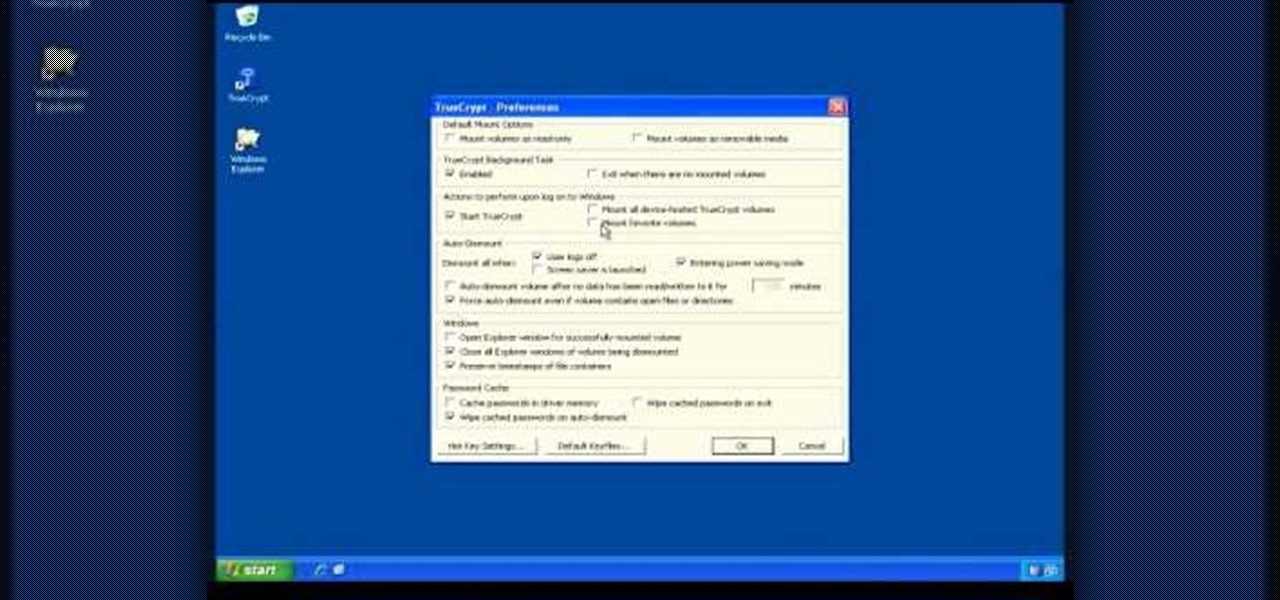
How to use or mount a TrueCrypt volume to access the data that you have encrypted with the program.

You don't need to work in the accounting department of a Fortune 500 company to use and appreciate Microsoft Excel. Although primarily associated with a wide variety of functions pertaining to accounting and finance, Excel is actually an incredibly powerful and multifaceted platform that can be found at the heart of many large-scale analytics environments.

As protests surge in the wake of George Floyd's murder by a Minneapolis police officer, powerful photographs and videos from the demonstrations have gripped the world, putting our nation's very real and very justifiable widespread civil unrest out into the digital world. Unfortunately, these pictures could put you or others in danger if precautions aren't taken before uploading them online.

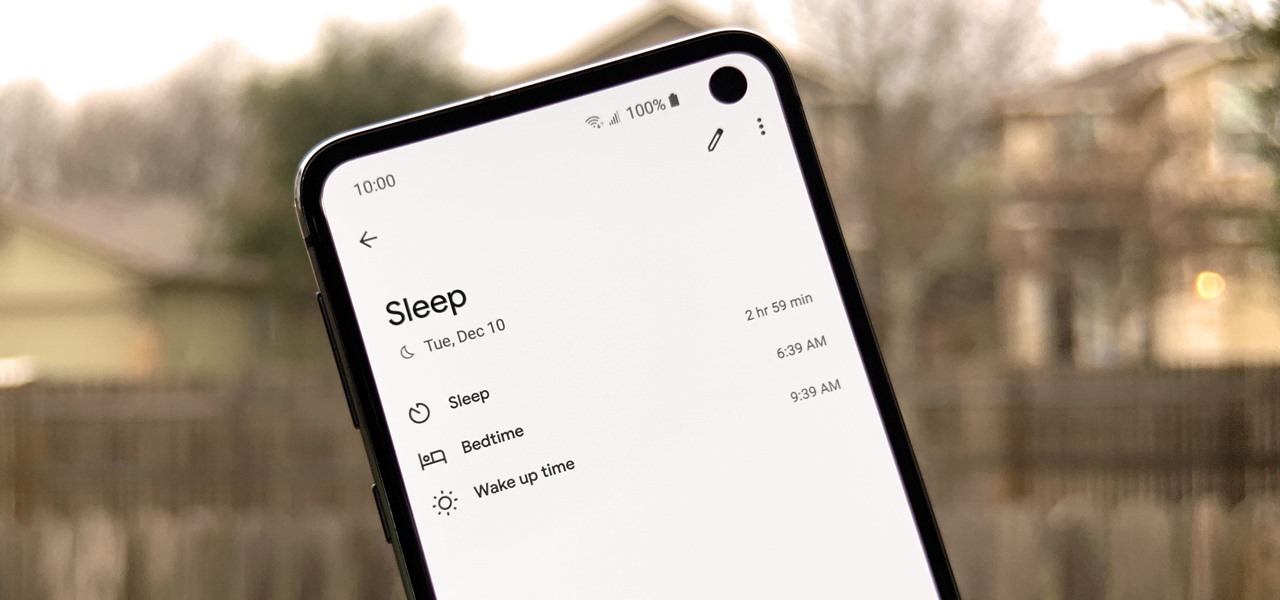
When trying to get fit, something that can easily be overlooked is your overall sleep quality. Your body needs sleep to recharge and it helps to maintain a healthy lifestyle, there's no denying it. Luckily, Google Fit can help you track your sleeping habits without having to jump through any hoops along the way.

All of the new iPhones from 2018 were released with dual-SIM support, but none of them were capable of actually using the eSIM in iOS 12, only the physical nano-SIM. But on iOS 12.1 and later, you can finally take advantage of eSIM so you can have, say, a business and personal plan on your iPhone XS, XS Max, or XR at the same time.

Net neutrality is dead and your internet service providers can collect all the data they want. While VPNs are a great way to protect some of that privacy, they're not perfect. There is another option, though, called Noisy, which was created by Itay Hury. It floods your ISP with so much random HTTP/DNS noise that your data is useless to anyone even if they do get it.

With the rise of website encryption (TLS), sniffing passwords from network activity has become difficult. However, it's still possible to quietly exfiltrate a target's network traffic in real time to extract passwords and sensitive information. Pertaining to macOS, there are two methods for retrieving traffic from a backdoored Mac.

Your email inbox is a treasure trove of personal data. The people you contact, your writing style, which messages you flag as spam — all of this information and more can be used to paint a clear picture of you. Google knows this as well as anybody, so they use this data to constantly improve your experience in Gmail.

Passwords stored in web browsers like Google Chrome and Mozilla Firefox are a gold mine for hackers. An attacker with backdoor access to a compromised computer can easily dump and decrypt data stored in web browsers. So, you'll want to think twice before hitting "Save" next time you enter a new password.

Unlike many browsers, Firefox gives a lot of control to the user. By default, Firefox does a great job of balancing security and performance. However, within the app's settings, you can modify options to shift this balance in one direction or another. For those looking to shift it toward security, here are few suggestions.

As of 2016, there are approximately 1.85 billion Android smartphones worldwide. This growing popularity has led to an increasing number hacks and cyber attacks against the OS. Unfortunately, Android users need more protection than what is offered by Google. The good thing is that there are a number of options available.

As smartphone users, we live in dangerous times. The value of phones continues to rise, making them prime targets for thieves. In 2015, the FCC estimated that one million phones are stolen each year, and with several devices starting to hit the $1,000 mark now, these numbers are sure to rise. But what do you do if you fall victim to phone theft?

Most of us skip through documents like privacy policies and EULAs (end-user license agreements) because they're long and boring. But, as Congress just passed the SJR34 bill in early April, you're probably a little concerned about your personal data, so we summarized the privacy policies for major ISPs and mobile carriers in the US.

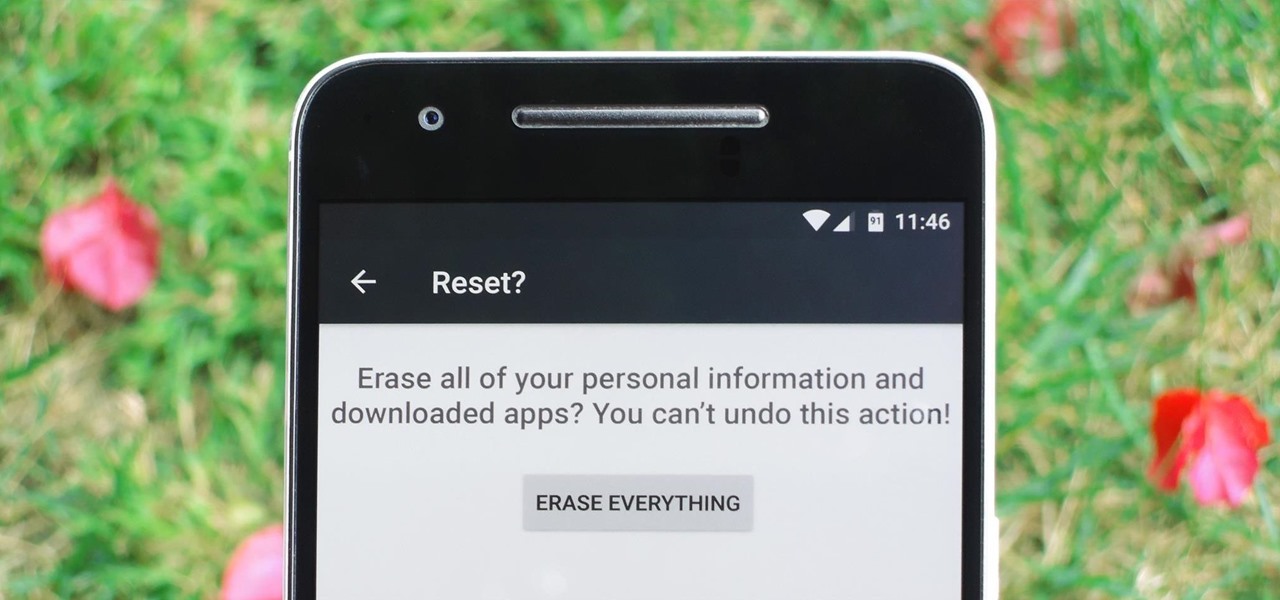
Whether you're performing a factory reset to get your device ready for sale or trade-in, or you're wiping your device in the hopes of fixing software issues, there's a right way and a wrong way to go about it. Sure, it seems like a simple task on the surface, but if you're not careful, you could end up wasting a lot of time or losing precious data.

What's up readers? Today I'll be introducing to you a new vulnerability called the Format String vulnerability (in case you missed the title). It won't be much, just a little motivation to keep you guys going. A little teaser, if you may.

Video covering how to set up a Venn diagram. The video covers how to draw the diagram and then look at a set of data and place the data in the correct part of the Venn diagram. The sample problem is as follows.

This is a short explanation and tutorial on how to grab saved passwords from Google Chrome, ideally from a meterpreter session. The idea behind this is to understand how saved passwords work and how to keep them safe. Let's have some fun :D Understanding Google Chrome Saved Passwords