When it comes to customizing Android, there's no better way to make it your own than by installing a custom ROM. You gain new features that were not accessible on the stock firmware that came with the phone, and you get complete control over how your system looks and feels. But there's definitely a learning curve.

The first annual Snap Partner Summit kicked off on Thursday in Los Angeles, and with it came some new products announcements, several of which enhance Snapchat's already robust augmented reality powers.

On Monday, Apple unveiled its Apple Card, the company's boldest move yet toward becoming a truly mainstream mobile payments company. And the product has vast implications for our augmented reality future, some of which may not be immediately obvious to many.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.
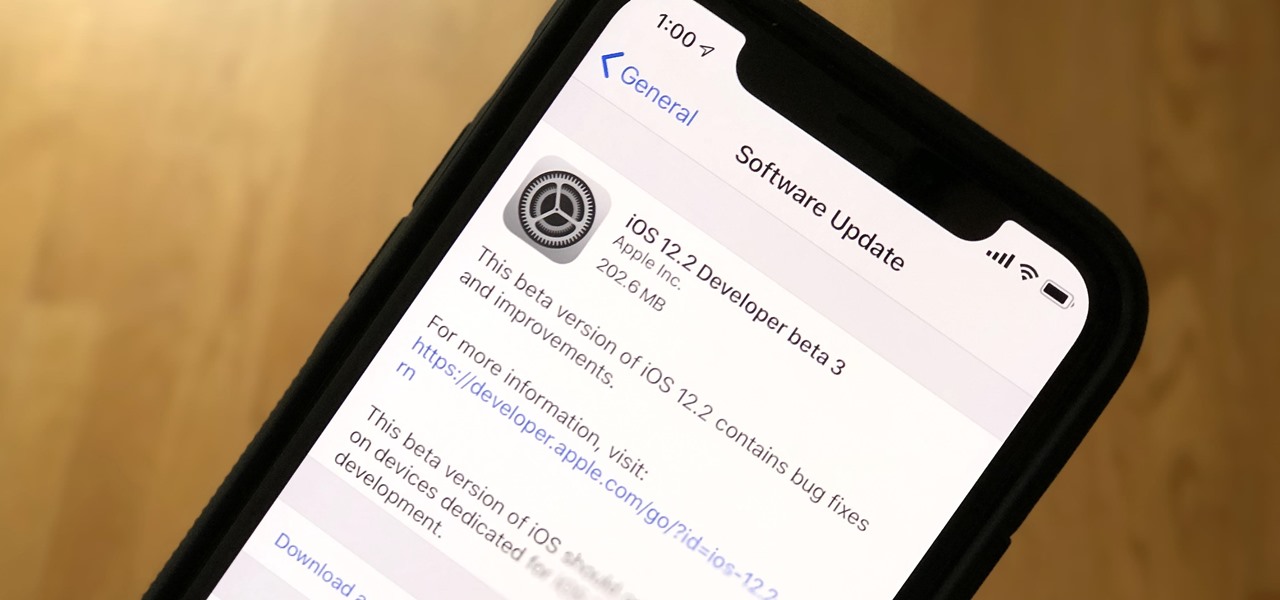
Apple just released the third iOS 12.2 developer beta Tuesday, Feb. 19, fifteen days after the release of iOS 12.2 developer beta 2. Beta 3 fixes an issue with the lock screen, and reintroduces Group FaceTime to beta testers. Overall, iOS 12.2 hosts a wealth of new features as well as bug and security patches.

Intel's RealSense family of depth tracking cameras has a new addition with a different set of sensory capabilities.

You've had your fun swiping, but now it's time to walk away from all of your online dating apps. Whether it's because you found someone you're interested in or just need some time away, it's important to know how to permanently erase your online dating footprint — and that includes deleting your Bumble account.

The Federal Communications Commission (FCC) has cleared a path for Google to move forward with hand-tracking technology that could pose a major threat to Leap Motion.

Perhaps you've thought about rooting your OnePlus 5, but thought again when you heard SafetyNet would prevent you from using apps like Google Pay, Pokémon GO, or Netflix. Those are valid struggles when you root using traditional methods. There are no such worries when using Magisk, as it masks the fact that your device has been modified.

Performance and stability improvements, as well as new features, are just some reasons to install iOS 12, but new changes mean new battery health challenges. It can be difficult to boost battery life while taking advantage of everything this update has to offer. Luckily, there are plenty of ways to avoid unnecessary battery drain when using iOS 12 on your iPhone.

All phones (yes, iPhones too) slow down over time. As your device gets bogged down by various apps and you begin to run out of storage, it's just an inevitability. That doesn't make it any less frustrating ... I mean, is there anything more annoying than a slow phone? My answer: No. Of course not. It's the single most annoying thing ever.

Having a dropped call can be incredibly frustrating, especially when you look down and see that your iPhone has full reception. While there's any number of issues that can cause this, one common and often overlooked issue is your iPhone failing to switch cell towers as appropriately needed.

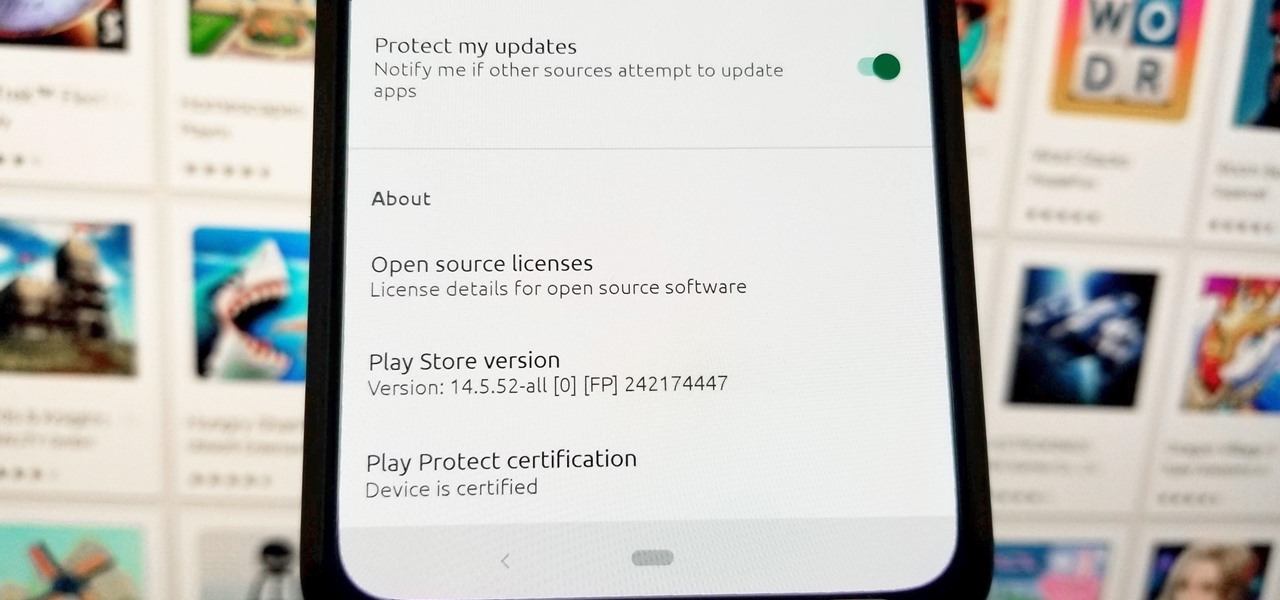
What you see when you open the Play Store is completely dependent on your country settings. Search results and top charts are specific to each region and there are lots of popular apps and games that simply won't show up unless your Play Store country matches up.

As the official release of iOS 12 nears closer each day, Apple continues to update its betas. The company released the fourth beta of the upcoming software to developers Tuesday, July 17, exactly two weeks after the release of the third developer beta which came out just a few days before the second public beta.

For SQL injection, the next step after performing reconnaissance and gathering information about a database is launching an attack. But something seems off .. in the real world, it's usually not quite as simple as passing in a few fragments of SQL code to an input field and seeing all that glorious data displayed right in the browser. This is when more advanced techniques are needed.

On Tuesday, at Google's I/O developer conference, the company announced a huge update to its ARCore augmented reality toolkit that matches the latest features of ARKit, and surpasses Apple's AR platform via support for shared experiences.

The business of enabling the development of augmented reality experiences appears to be as lucrative as AR app development itself.

A report from app data firm Sensor Tower reveals that more than 13 million ARKit apps have been installed on iPhones and iPads within the first six months since the toolkit launched with iOS 11.

Smartphones are like high tech buckets that collect our personal information through constant use. This has some obvious benefits, like getting a more personalized experience with our devices. On the other hand, this data is a tempting target for bad actors looking to make a buck at the expense of your privacy.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

As the level of data being generated grows exponentially, past the Information Age and into the coming Hyper-Information Age of immersive computing — as resistant as many of us are to the idea — personal data security is becoming a necessary consideration in our everyday lives. Recognizing this, Mastercard, Qualcomm, and Osterhout Design Group have teamed up to show what secure shopping could look like in the very near future with iris authentication.

Due to the overnight success of smartphones, millions of people are connecting with others. Currently, over 15 million text messages are sent every minute worldwide. Most of this communication is happening in the open where any hacker can intercept and share in the discussion unbeknownst to the participants. However, we don't need to communicate insecurely.

Apple took a giant step forward in terms of user customization with the new Control Center in iOS 11. With an improved design, buttons you can pick and choose from, and even a new default Cellular Data toggle, it's definitely a better iPhone experience. However, Apple also took a giant step backward with the confusing Bluetooth and Wi-Fi toggles.

Every year, football fans get excited about the next crop of blue chip prospects joining their teams, from five-star high school recruits graduating to college to first-round rookies drafted into the NFL.

Spotty cellular reception is a fact of life that we all have to deal with, especially when you're traveling. For those of us who rely on our smartphones for navigation, driving through areas with bad mobile data service can be a cause for major headaches.

Demand for Tesla's driverless features as well as its ultra-long battery ranges and a reputation for offering the best-in-class electric car driving experience helped Tesla see a 32% surge in its value as a brand, topping out at $5.9 billion in the BrandZ Top 100 Most Valuable Global Brands study, released June 5.

This week in Market Reality, we see two companies capitalizing on technologies that contribute to augmented reality platforms. In addition, industry mainstays Vuzix and DAQRI have business news of their own to report.

Whether you're a professional mechanic, a hobbyist, or someone who just wants to know why their check engine light came on, your Android device and an OBD-II adapter can provide insight as to what's going on with your car. Most adapters sell for less than $10, and once you plug it into your vehicle, you'll just need a good app to help you make sense of all the data it can gather.

The V20 is an amazing phone from LG powered by Android. Packing impressive features such as a removable battery, expandable storage, and the latest Android version straight out of the box, the V20 is a tough phone to beat.

If your phone has an unlocked bootloader, you can use Fastboot commands to flash factory images. That may sound like a bunch of technical jargon, but when it comes down to it, this is the best method for updating a rooted device, fixing a bricked phone, reverting to stock, or even getting new Android updates before everyone else.

As we reported first here on Gadget Hacks, the Google Pixel and Pixel XL have unlockable bootloaders, with the exception of models purchased from Verizon. This means that once the TWRP custom recovery is installed, you can flash ZIPs and even root your device in a few taps—as long as you unlock the bootloader beforehand.

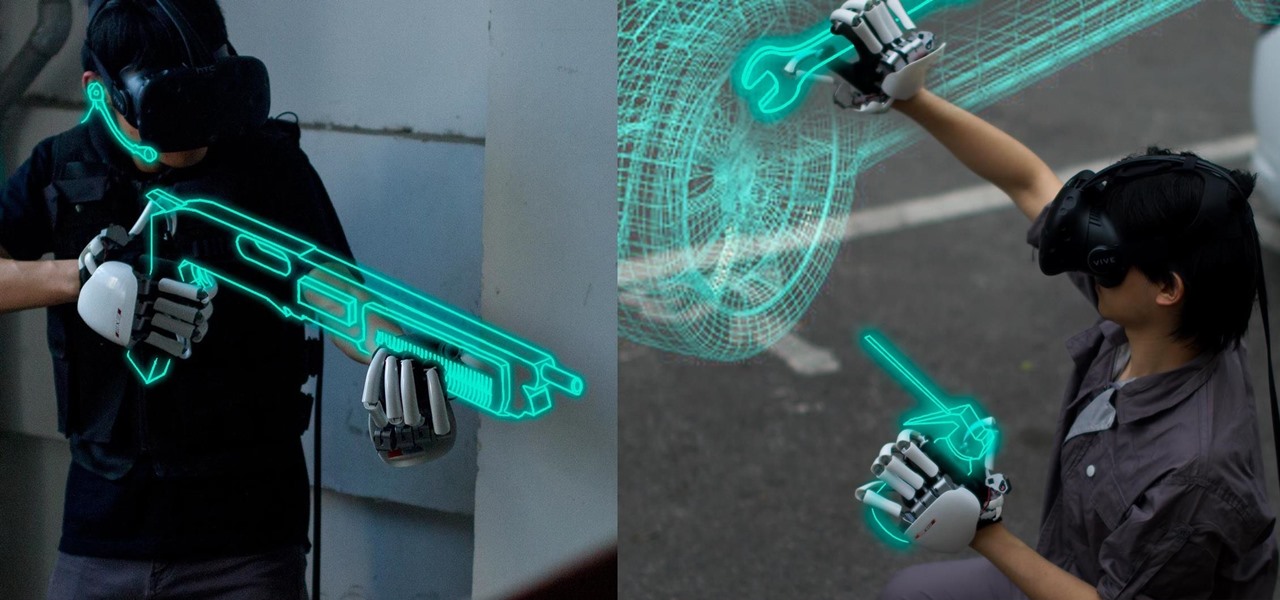
One of the disadvantages of the digital world is that you can't pick it up and touch it. While that can feel like less of a problem in virtual reality, where you're already holding controllers, mixed reality environments—like the one you'd experience in Microsoft's HoloLens—suffer from a lack of physical connection with the digital objects that appear in your real world. Dexmo aims to solve that problem with a relatively intimidating new controller that encompasses your hands.

Microsoft's HoloLens is certainly a leap into the future of mixed reality interfaces, but it's not without drawbacks.

Welcome back everyone. I apologize for the lack of training articles, but I've been rater busy lately. I've recently picked up a second job and my college courses are now back in session, so I'm a bit strapped for time.

Hello there! This will probably be the final tutorial on functions where we will be looking over a method called pass by reference. This technique allows us to modify large amounts of data without the overhead and return multiple values. Let's go!

Hello friends. This is actually my first how to.

Hey readers! This tutorial will be the entry point for the introduction of buffer overflows. Something like requesting user input is a very common place for vulnerabilities to pop up and we will definitely have fun while trying to make programs crash. But for now, let's start with how we can get input from a user.

Windows 10 definitely has a sleek and modern look to it, but some of these visual changes have been made at the expense of functionality. For instance, the slider that appears when you click the volume icon in your notification tray now sports a completely minimalist look that lacks the quick link to the full volume mixer from past Windows versions.

If your iPhone can't last a full day without being recharged multiple times, something's wrong—but it might just be working harder than it needs to.

Flashing people in an oversized trench coat is both old-fashioned and exhausting (and also very illegal). But like the evolution from school-yard bullying to cyber-bullying, it seems as if the new trend is "cyber-flashing" (it's even has an official hashtag). In the U.K., police are now investigating what they are calling the first cyber-flashing case.