First we have to do is to create a new file with the size we want. Then we go to the layer tab in the left and duplicate the existing layer how many times we want (how many frames we want to have the GIF). After this we deselect all the layers by clicking on the eyes on left. Now we click again on one eye to select the layer we want to work with. Be sure to have only one layer selected. Then we can start "playing" with the images and create shapes, faces and so on with all the layers we had c...

There is a lot of stigma around prenuptial agreements but they can be a good chance to work on difficult issues as a couple and make sure you're on the same page. Prenuptial agreements don't have to be a horrible experience and can give a soon to be married couple some peace of mind.

Karma is an idea that exists in the Hindu, Buddhist, Jain, and Sikh religions, which simply holds that all actions have consequences. In other words: karma’s not a bitch, but you might be. If so, here’s how to start sending the world good vibrations. Learn how to store up some good karma for yourself.

How do spammers get your email? You give it to them. Not directly, no — you sign up for an app or service and happily hand over your email to verify your new account, then that app or service sells your email address to marketers who now know what kinds of apps and services you like.

If you're living or staying out in the middle of nowhere or a rural area outside of a big city or town — where there are no reliable cable, fiber, or wireless networks available — how can you get an internet connection? There are several possibilities, but they all come with tradeoffs, which we'll go over in detail.

If it has an internet connection, it's got a huge attack surface for hackers. But what makes your phone even more dangerous is its portability and the collection of sensors it houses that can be just as good at tracking you as the camera and mic.

When you need to type in all caps on a computer, you just press the "caps lock" key. But no such key seems to exist on iOS. The "shift" key appears to work at first but will deactivate once you type one capital letter. Holding down the shift key while you type gets the job done, but it's a pain. While it might not be obvious, enabling caps lock is actually really simple.

Null Byte readers are no strangers to the powers and benefits that come from learning how to code. By knowing only a handful of programming languages and platforms, an intrepid developer can create everything from best-selling apps to spyware in the comfort of his or her own home.

For a hacker, there are a lot of advantages to creating a fake network. One advantage forces nearby devices to use their real MAC address if you happen upon a network that's stored in their preferred network list.

An attacker can repurpose public MyBB forums to act as command-and-control servers. It only takes a few lines of code to configure a MacBook to fetch commands and send responses to any website the attacker desires.

Samsung simplified the interface in its Camera app for the Galaxy S20. It's easier to use for the most part, but now you have to go digging to access certain camera modes. To make up for this, One UI now lets you rearrange the tabs in the Camera app.

Just days ago, Georgio Armani canceled his live show in Milan and opted to stream it instead due to coronavirus concerns. Now, at the start of Paris Fashion Week — shadowed by similar worries — Burberry has launched an augmented reality tool that lets you view the latest high fashion from the comfort of your home.

No operating system is stricken with as many vulnerabilities as Windows, and it's often a race to release the latest patches to fix things. From an attacker's point of view, knowing which patches are present on a Windows machine can make or break successful exploitation. Today, we will be covering three methods of patch enumeration, using Metasploit, WMIC, and Windows Exploit Suggester.

Along with rebranding Magic Leap 1 for enterprise customers, Magic Leap has gifted its developer community with some new toys with a tease of more to come in 2020.

One of my favorite iOS hacks is Type to Siri. This lets you type your queries to the iPhone digital assistant without needing to use your voice. Unfortunately, Type to Siri replaces the typical Siri voice prompt on the Home or Side button, meaning you need to choose between one or the other. That is, until iOS 13.

Android 10 lets you personalize your device by adding a profile picture to your lock screen. Not only will it add your picture or avatar to your lock screen, but it will also add it to the Quick Settings menu. It's a nice touch of customization that makes your device feel like your own.

If you've ever used the Find My iPhone and Find My Friends apps in iOS 12 and below, you may be surprised to hear that those apps have joined forces in iOS 13. Now, instead of two separate apps, they're combined into one convenient package. But what does that mean for you and your privacy and security?

Under the rocket's red glare and the bombs bursting in air, the Statue of Liberty is swaying in celebration this Fourth of July thanks to Snapchat.

Players who have stuck around with location-based game Jurassic World Alive just got a new treat that makes the augmented reality experience even more fun.

After Apple unveiled ARKit 3 at WWDC on Monday, Unity Technologies wasted little time on ensuring its developers can take advantage of it.

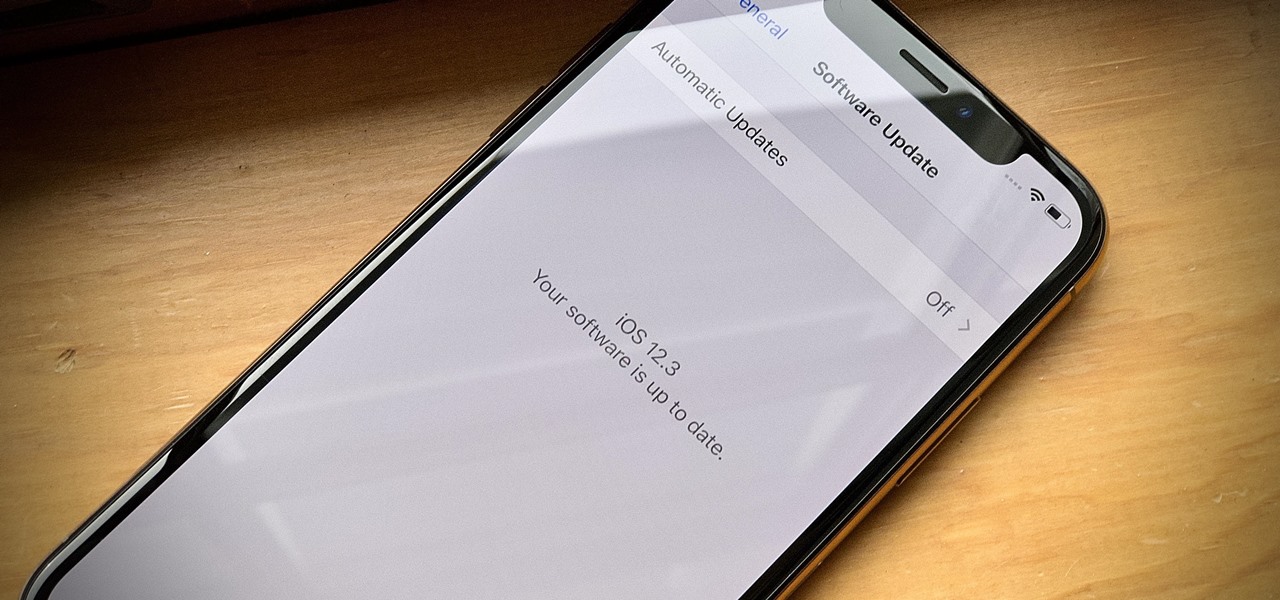
Eight days ago, Apple pushed out iOS 12.3 public beta 4 for anyone who wants to try it out. Now, there's a new version, iOS 12.3 public beta 5, released May 7, less than an hour after the developer software update. Just like it's developer version, the fifth iOS 12.3 beta for the public is a simple update with seemingly under-the-hood changes only.

So far, the iOS 12.3 public betas have been on the heels of the developer betas by just over a day each time, but not anymore. Apple just pushed out iOS 12.3 public beta 4 today, April 29, just hours after the same dev version came out, meaning it's only been six days since iOS 12.3 public beta 3 was released.

Arthur van Hoff, former CTO and co-founder of Jaunt, is taking his immersive content talents to Cupertino.

Silence spreads over these mountains like nothing I've ever felt. If I didn't have Moby blasting in my earphones, there'd probably be no other sounds around. Well, except for someone, Phil probably, murmuring in a nearby tent just low enough to make his words indiscernible.

Users are often the weakest link when probing for vulnerabilities, and it's no surprise they can be easily fooled. One way to do this is called clickjacking. This type of attack tricks the victim into clicking something they didn't mean to click, something under the attacker's control. Burp Suite contains a useful tool called Clickbandit to generate a clickjacking attack automatically.

The Raspberry Pi Zero W and Pi 3 Model B+ include integrated Wi-Fi, Bluetooth Low Energy, and more than enough power to run Kali Linux. They sound like perfect all-in-one penetration testing devices, but the lack of support for monitor mode and packet injection usually meant buying a supported Wi-Fi adapter. Now, it's possible to use monitor mode on the built-in Wi-Fi chip with Nexmon.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

Over the years, Magic Leap's long-cultivated shroud of mystery led some onlookers to buy into the company's dream before even trying the device, while for others, the secrecy seems to have stoked the kind of resentment and overcorrecting critique usually reserved for the mighty Apple.

Smartphones and laptops are constantly sending Wi-Fi radio signals, and many of these signals can be used to track us. In this guide, we'll program a cheap IoT device in Arduino to create hundreds of fake networks with common names; This will cause nearby devices to reveal their real trackable MAC address, and it can even let an attacker take over the phone's data connection with no warning.

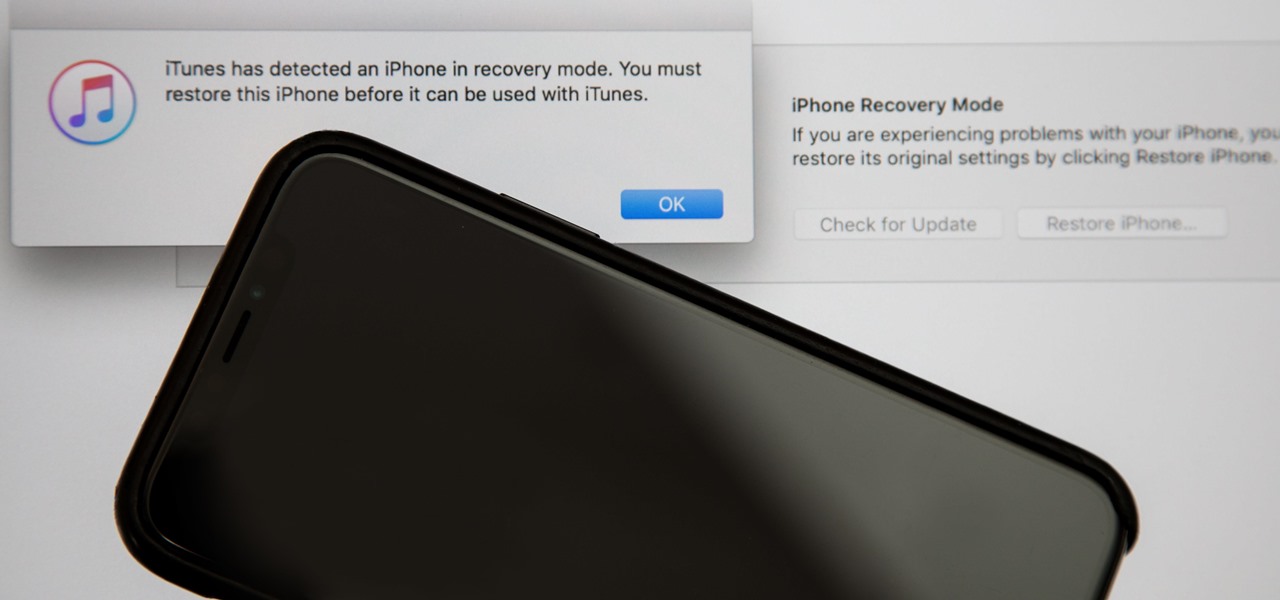
Following in the iPhone X's footsteps, the iPhone XS and XS Max, as well as the iPhone XR, have all ditched the iconic Home button last seen on the iPhone 8 and 8 Plus, which is one giant leap toward Jony Ive's ultimate vision of an iPhone that's a clean slab of glass. However, without the Home button, a lot of tasks have changed, most notably, entering and exiting DFU mode in iTunes.

The road to becoming a skilled white hat is paved with many milestones, one of those being learning how to perform a simple Nmap scan. A little further down that road lies more advanced scanning, along with utilizing a powerful feature of Nmap called the Nmap Scripting Engine. Even further down the road is learning how to modify and write scripts for NSE, which is what we'll be doing today.

While numerous examples exist of hospitals deploying the HoloLens to assist doctors, surgeons, medical professionals, and students while treating patients, California's Lucile Packard Children's Hospital Stanford is actually using the augmented reality headset to improve the patient's experience.

Cable TV network Nickelodeon is looking to break new ground with a new series that will be experienced in virtual and augmented reality.

There's actually more to the dialer screen on your OnePlus than meets the eye. Besides its obvious purpose of calling people, there's a vast array of secret codes that you can input to troubleshoot your device, in addition to revealing important information, making anonymous phone calls, and so much more.

Android 9.0 Pie is now available to install on Google's own Pixel devices and a select few other phones. In the new release, there's a fairly hidden setting that lets you enable a system-wide dark theme that changes the look of your Quick Settings panel and other menus.

This year's big iPhone update, iOS 12, aims to solve many of the issues that arose during iOS 11's controversial, buggy tenure. With that in mind, it may be tempting to jump on board the new software immediately and leave iOS 11 in the dust for good. Here are some reasons why you might want to reconsider joining the iOS 12 beta.

Just in time for the release of Pixar's highly anticipated sequel, AR Emoji based on characters from The Incredibles 2 have arrived for Samsung Galaxy S9 and S9+.

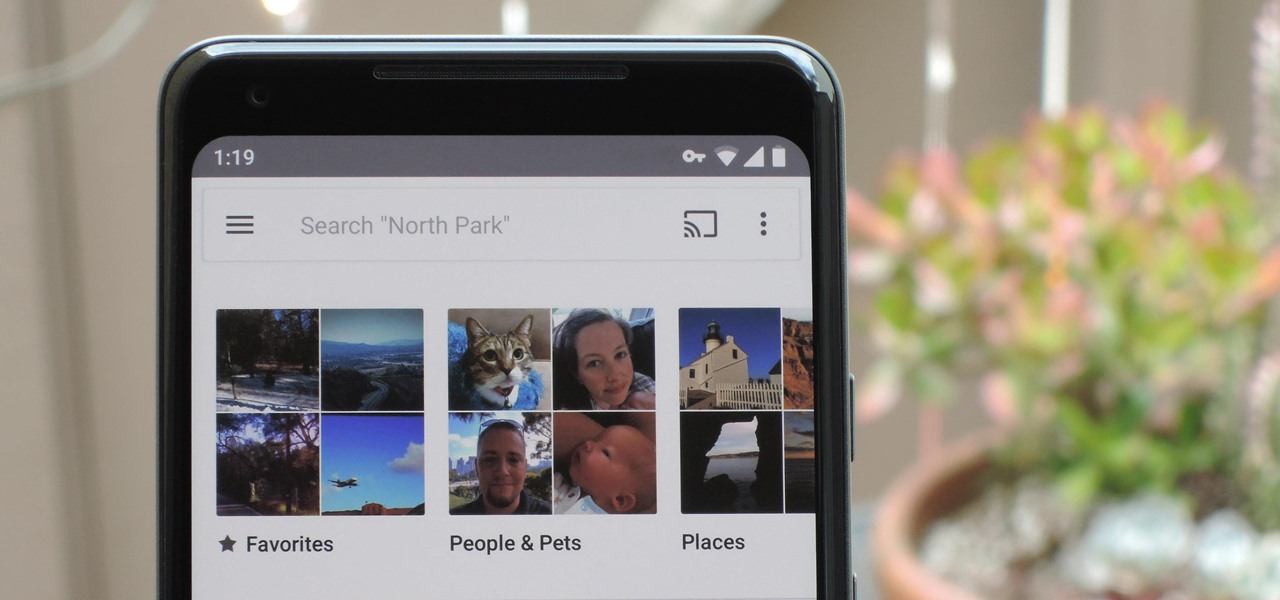
Google Photos is a fantastic service, giving you unlimited storage on either your Android or iPhone. With all this free space, some pictures can get lost in the shuffle. Fortunately, Google will now let users "Favorite" pictures — whereupon they're automatically put in their own standalone album.

The iOS App Store is a big place, offering over two million applications in total. However, there are actually some apps you can and should install on your iPhone that the iOS App Store doesn't include. And no, these apps do not require any difficult jailbreaking or complicated sideloading techniques — they are really simple to install.

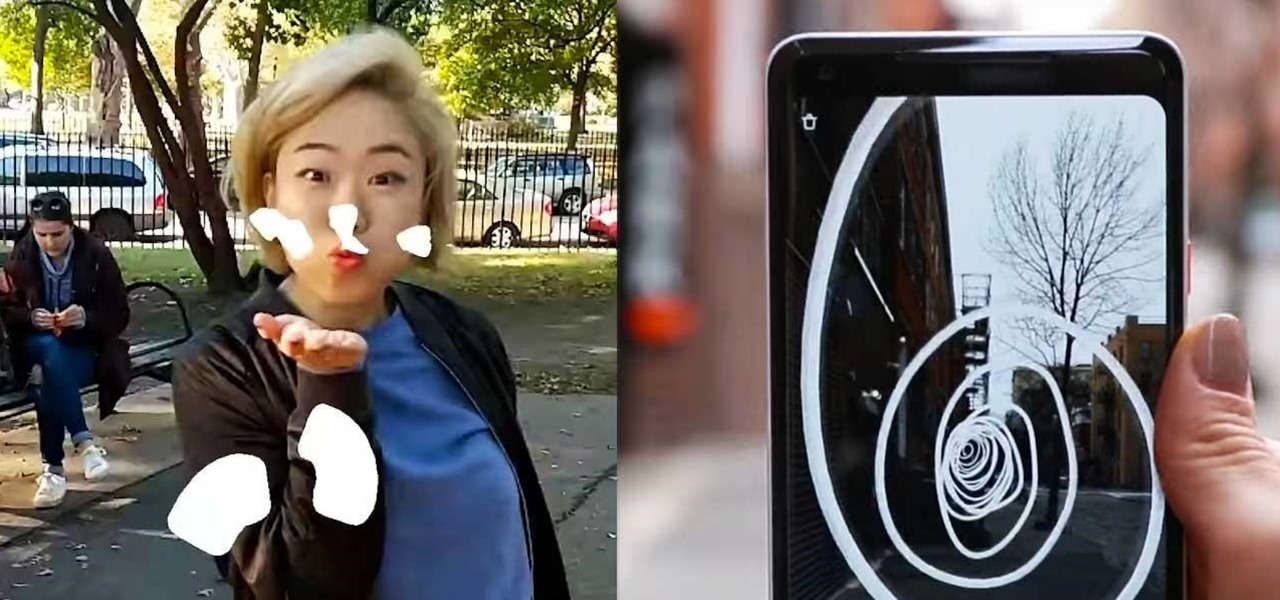
As part of its ARCore push this week, Google has promoted Just a Line from one-time AR experiment to a full-fledged app.