It seemed appropriate that we announce the winner of the first White Hat Award for Technical Excellence on the Academy Awards weekend. This is, in essence, our "Oscar" here at Null Byte. Remember, this contest began on January 4th, 2016 and just recently closed on February 15th. In this contest, I was looking for:

Sup? Today, we'll be learning about for loops in Java: What they are, how they work, and how to create them.
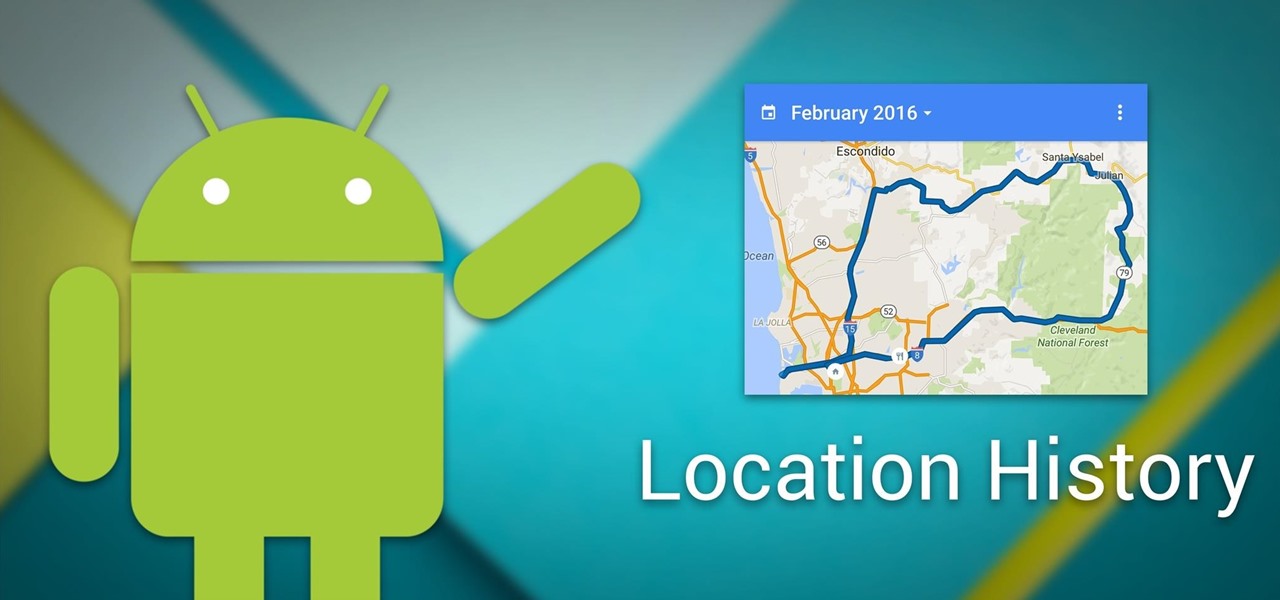
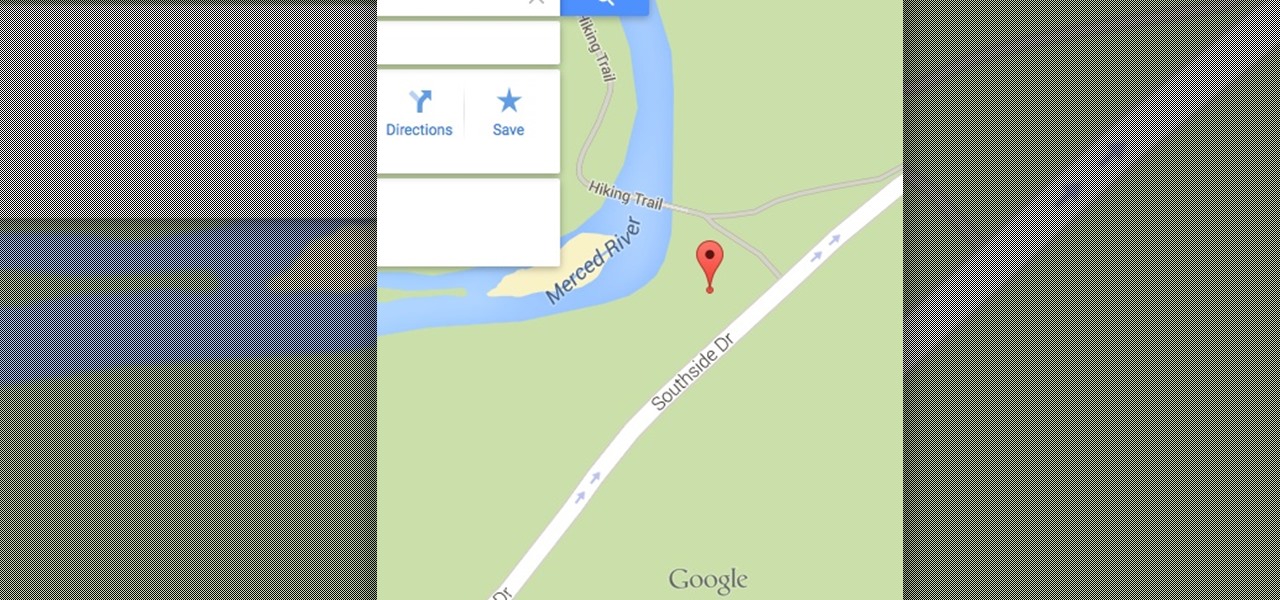
Your smartphone has a GPS chip inside of it that can pinpoint your location down to the nearest 4 meters, and this little device stays in your pocket or purse all day. Combine those two facts and you start to realize that your phone knows exactly where you've been during every moment that has passed since you've owned it.
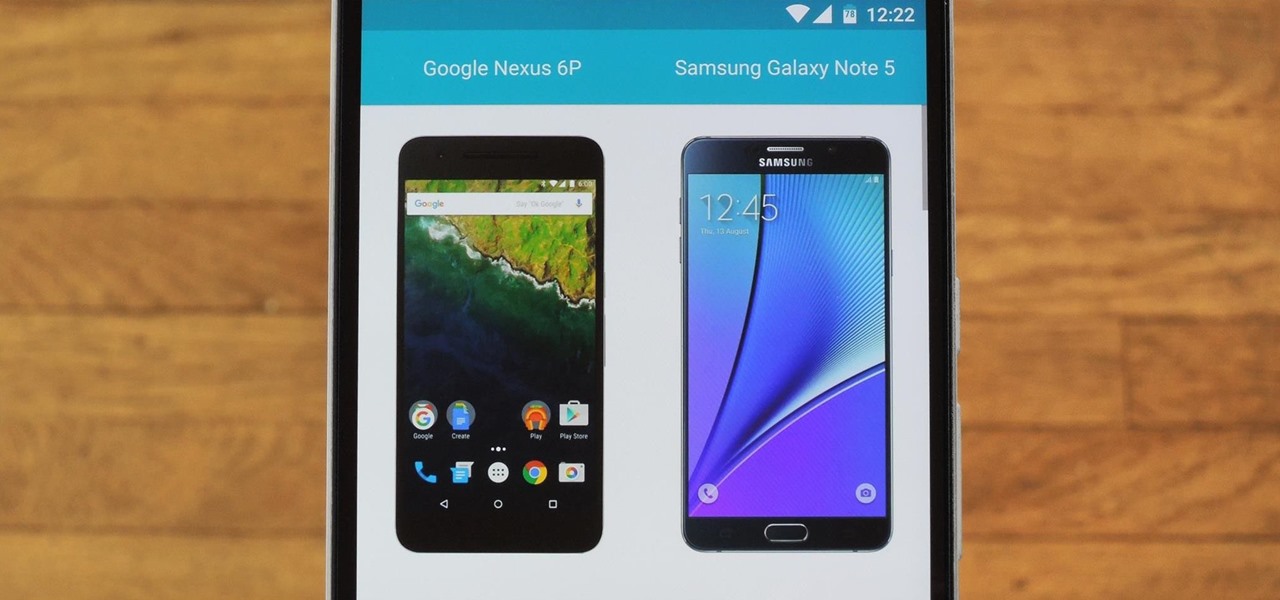
Shopping for a new phone is an entire ordeal. Even when you've narrowed it down to a few choices, comparing the finalists can be difficult, because specs and prices are scattered around on various different manufacturer websites, and if you're trying to do this on your current phone, most of these websites aren't optimized for mobile viewing.

Samsung makes some wonderful phones, but one thing I've noticed is that battery life can start to degrade over time, causing the phone to die a lot faster than it used to. If you've been experiencing this issue, and have asked yourself, "Why does my Galaxy S5 die so fast?" there are a few likely causes—and we've got you covered with troubleshooting tips and simple fixes below.

All across the web, you'll find guides on setting up various apps and mods for your Android device—but while these are certainly useful, they all seem to be working under the assumption that the reader has a certain level of knowledge about Android. For someone that's just getting started with the world's most popular mobile operating system, the basics of Android simply aren't covered as well as they should be.

Five Phases of Hacking:- The five phases of Hacking are as follow:

Greetings fellow hackers. This tutorial is about creating "safe" passwords. This is different from strong passwords. Safe passwords is just creating a password that is not used by someone else or colleague, my definition. But how do you prevent something like this from happening? Of course you won't ask your friend if s|he is using the password you are about to create. Before I show you some of my tele-psychic powers like Professor Xavier, you might want to read this for advice on creating "s...

The Creative Lab at Samsung, also known as their C Lab, is trying to make wearable fitness devices more inconspicuous with its wearable smart belt, the WELT, but that might not be all.

You've probably heard the old joke about how Ford is an acronym for "Found on Road Dead." Well, the Detroit automaker on Monday announced a new and much better way to help you find your parked vehicle, as well as a whole host of other features—just use your smartphone.

In many programs on Linux, you'll come across programs which allow you to specify additional arguments instead of just simply running the program by itself. If you've used the Kali distribution, I'm more than certain you'll have come across these with the command line tools, else if you have been following these tutorials, we have already come across three tools which also use the same technique, i.e. gcc, gdb and wc. How do we do this with C? Let's find out.

A video showing what is alleged to be the new Apple iPhone 7 has appeared online. The uploader of the video claims that it was shot on one of Foxconn's assembly lines.

What's up guys! It's time to discuss strings in more detail. Review

Apple makes it easy to access your favorite and most recently used applications and documents in Mac OS X. You can simply add your favorite apps and folders to the dock, and you can always visit the Apple menu from the menu bar to see a list of your most recently used apps and docs.

Windows 10 universal apps are actually pretty awesome—regardless of if you're using a desktop, laptop, tablet, or convertible, the same app automatically scales up or down to suit your device. Definitely cool, but the Windows Store is pretty bare-bones as it stands, so the downside is that you can't always find a good universal app for every purpose.

Hello, everyone. If you've been following my recent articles, you'll know that I've been rather busy lately working on a project, a rather large one. I've been working with Pheonix750 and Ciuffy to build the Null Byte suite of tools! I got the green light from our admin a while ago, and we've been developing like mad ever since! I'm very excited to launch this project. So, let's start by explaining what it is...

I was bored when I found this piece of literature: ==Phrack Inc.==

In an article published in early-2015 by Peninsula Press, it was reported that the demand and the salaries for cyber security professionals are exploding! They cite that 209,000 cyber security jobs were unfilled last year, and that job postings have increased over 74% in the last 5 years. Job opening are expected to grow by another 53% over the next 3 years. You are definitely in the right field, my tenderfoot hackers! Some researchers are expecting information security jobs to continue to gr...

Hello, fellow hackers. I'm sure we've all seen it somewhere: the undying question of "How do I hack the game so-and-so?" And the answer usually is, "Come back when you actually know how to hack!" But how does one even go about "hacking" a game? What could that even mean?

Welcome Back !! TheGeeks. SQL Injection (SQLI) Part-1

Step aside, vodka—whiskey will soon be the best-selling hard liquor in the United States. The whiskey renaissance has been largely attributed to the current trend for locally- and artisan-produced goods. Local whiskey distilleries are rapidly increasing in number across the nation while bars in every state are including the old-fashioned cocktail on their menus in an attempt to capitalize on the trend (which we can probably thank Mad Men for).

If you're entirely new to smartphones, Android's share menu can seem like a foreign concept at first glance. In reality, it's one of Android's most central and unique features, and with a little experience, it can make your smartphone a lot easier to use.

Welcome back, my nascent hackers! Although my favorite TV show, Mr. Robot, had completed its first season already, I have not completed demonstrating the hacks that Elliot used in the show. (By the way, I can't wait for season 2!)

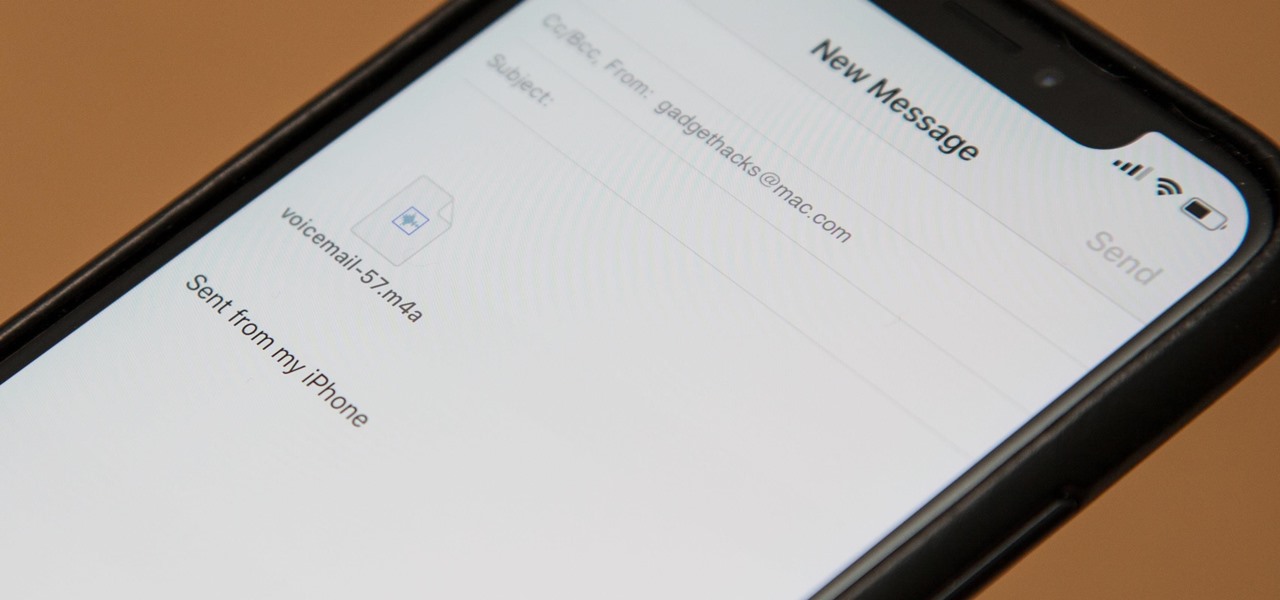
Eventually, your voicemail inbox on your iPhone will get full, and you'll have to delete some messages in order to make way for new ones. If all the voicemails you currently have are super important, you're not going to want to delete them before saving them first, of course. Luckily, this is a super simple task, and you can even forward them to someone else if needed.

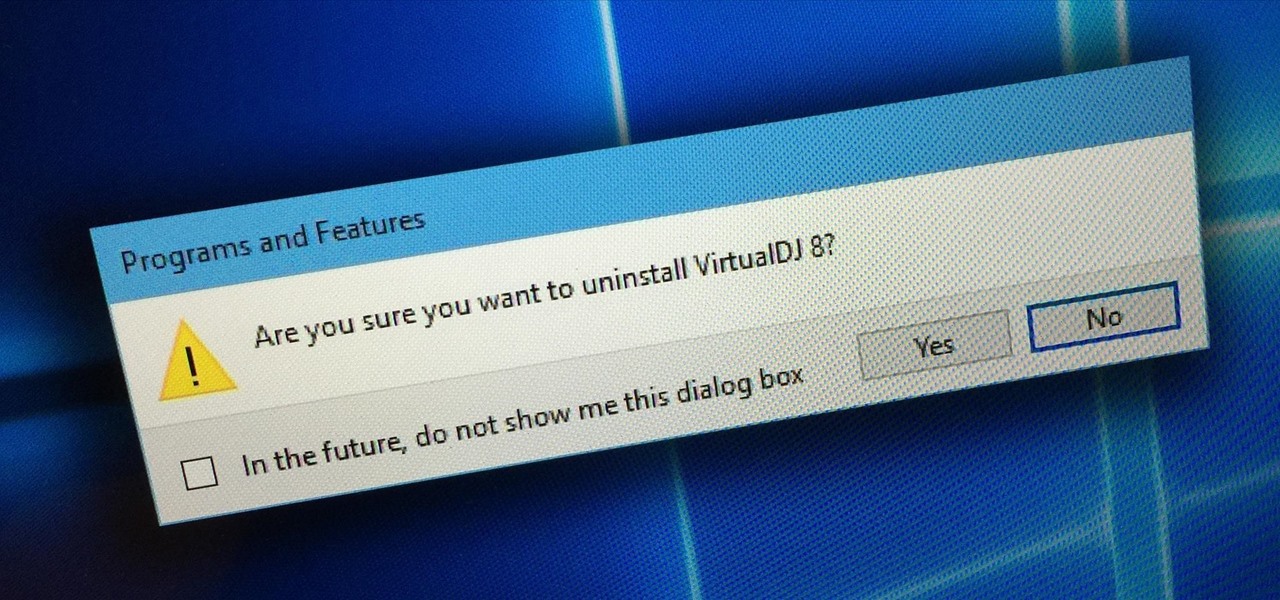
Uninstalling programs in Windows is not the nicest procedure. Some programs bundle a nice uninstaller with them which helps to ease the process. Other programs, mainly those that utilize the Windows Installer technology, begin the uninstall process right away. This can potentially be problematic for users who are trigger-happy with the mouse.

Hackers have stolen over 225,000 Apple user's account information from countries all over the world—including the United States, China, and France—in what many are reporting to be the biggest known Apple hack in history.

Unless you've been living under a rock or ignoring recent news headlines, Ashley Madison, the dating site for married people (or individuals in a committed relationship) has recently been hacked. Millions of their users are shitting their pants, and for good reason, as all of those accounts have just been leaked.

It's official: The next version of Android will be code-named "Marshmallow," and we're getting a whole number bump to version 6.0. Lots of exciting new changes are coming to the world's most popular operating system, including a "Now on Tap" feature that will give you relevant information about any screen at the press of a button.

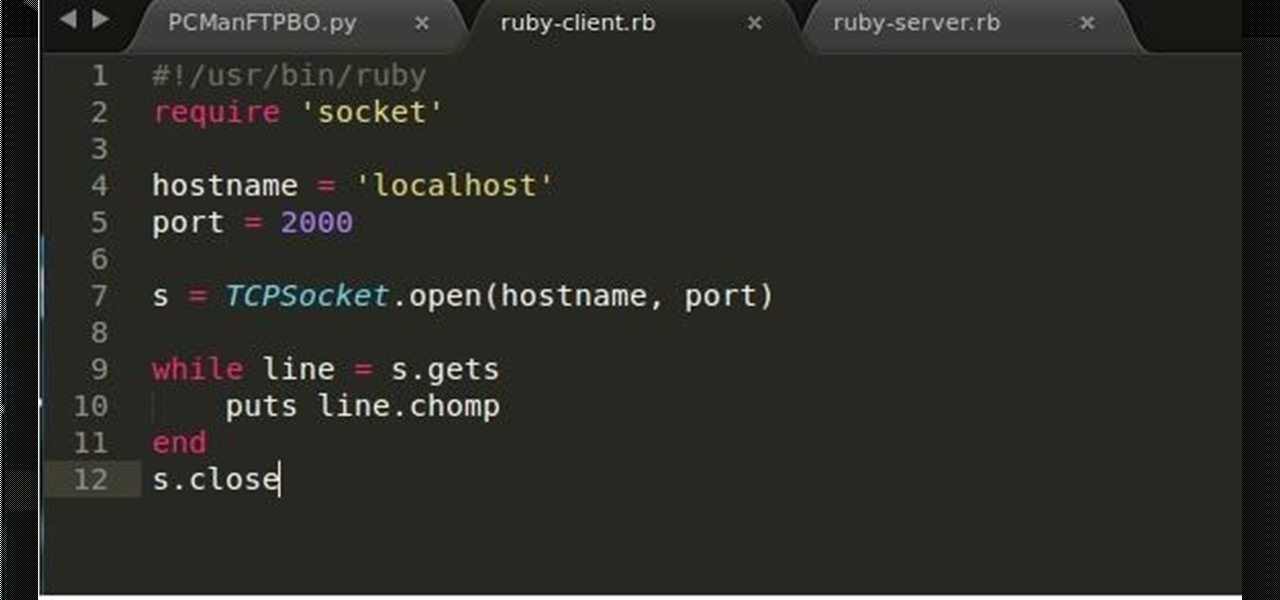
Recently, I've been learning Ruby as a second scripting language. But one topic I never covered with the many lessons online were sockets. So I did some research and came up with a very simple client/server connection that sends a string over the socket.

From day to day, it can be difficult to remember everything that's required of you. I tend to forget exactly where it is I'm supposed to be during my busiest moments, and it's even easier to delete each day's events out of your brain when there's so much else that dominates your mind. Yet taking the time to remember exactly what it is that happens during each of our days can be a vital part of our memory—and with nothing more than 15 minutes, we can strengthen our brains and remember more tha...

As familiar as it may look at first glance, there are still tons of subtle changes in Windows 10. Many options that existed in past versions have been moved, and virtually every system menu received at least a small visual makeover.

In the U.S., smartphone users spend more time on Facebook and Instagram than on any other app. If this sounds surprising for any reason, it shouldn't. Anyone that's browsed Instagram in a moment of boredom knows that a few minutes can quickly turn into an hour down a rabbit hole filled with Likes, Follows, and straight-up lurking.

Saying that I was obsessed with Pokémon as a child would be a serious understatement, and even though I'm not the Pokémon fanatic I once was doesn't mean I don't love playing still. However, I do often find myself dumbfounded by all of the new features and characters in each generation.

Last year, Apple debuted a feature that allows families to share iTunes and App Store purchases across their various accounts. Us Android users, on the other hand, have to buy separate copies of apps for each of our accounts—well, at least from an official standpoint.

Hi guys. I'm here to go for level 7 now lets get it start but i apologize u all that i posted this very late but now lets rock:

The Ring/Silent switch on the side of the iPhone has always had one purpose—to toggle ring mode/silent mode. But in iOS 9, Apple gave us another choice, and that's locking the orientation of the screen.

Welcome back, my hacking friends. We use our smartphones every day, for business, socialization, and leisure. The number of iPhone users is increasing in dozens of millions every year, with a whopping 63.2 million users in 2014 alone. That's a lot of users.

These days, there is no shortage of ways to exchange files to and from friends and family: text messages, email, Bluetooth transfer, and cloud services are just a tiny sliver of what you can use to share music, photos, videos, and more.

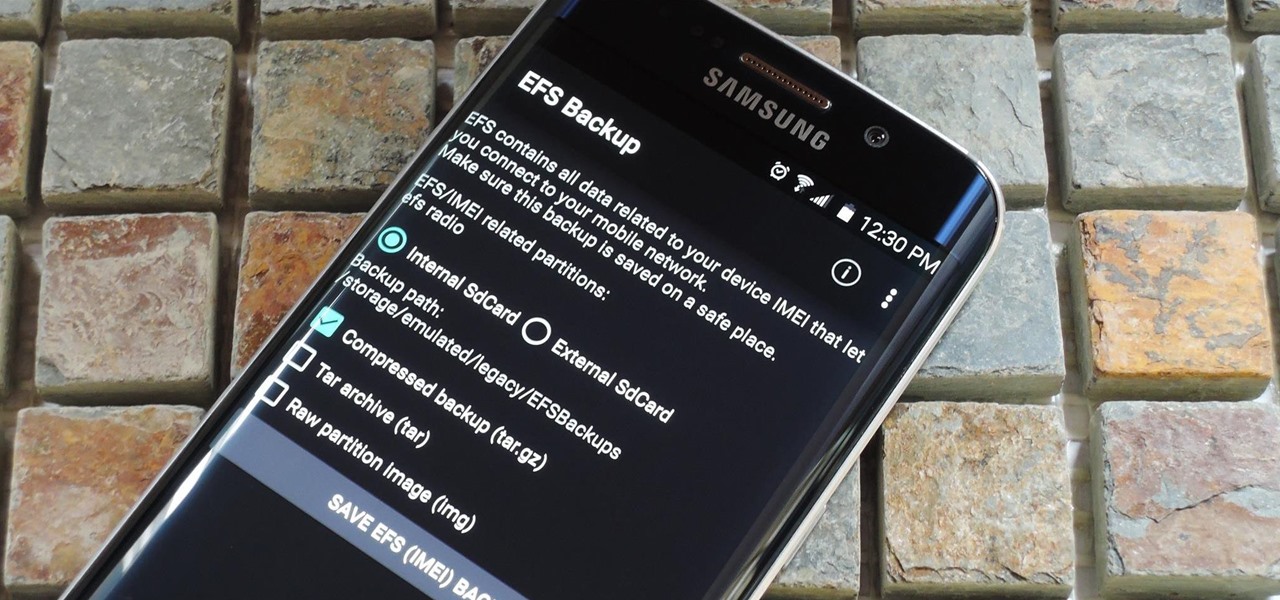
The EFS partition on modern Android phones houses the unique IMEI for your device, which is essentially an identification number that lets you connect to mobile networks. But sometimes, when you're flashing ROMs or restoring backups in custom recovery, the EFS partition can become corrupted, which will prevent your phone from connecting to any type of mobile network.

Google's Chrome browser is evolving into a very powerful platform. Not only can it be used to view your favorite website or mirror tabs to your Chromecast, but now that it has an App Engine, more powerful tools can be run within Chrome.