Update 1: Evad3ers have released a statement to the jailbreak community, claiming that the safety and security of their users is the most important thing to them and that all speculations about malware being encoded into the jailbreak is simply not true. You can read the full letter over at Evasi0n's site.

Let's just say it's been a pretty bad year for spies and government agencies and an even worse one for the privacy of U.S. citizens. Edward Snowden blew the lid off the NSA's spy program, and the FBI was recently discovered to have the ability to access your webcam any time they want—without triggering the "camera on" light. Yeah, that means those Justin Bieber lip sync videos you recorded weren't just for your private collection.

Snapchat was created for the sole purpose of removing evidence from your mobile that a photo or video ever existed. That way, snoopers can't find any of these questionable selfies in your photo gallery. Of course, there are plenty of ways around this safeguard, but it's still more private than the standard social networking app.

Applications, features, and software running in the background of your Samsung Galaxy Note 2 can drain a significant amount of battery power, even when your smartphone isn't being used. For this reason, smartphone carriers and developers suggest that you turn off Bluetooth, Wi-Fi, and other battery hogging features when they're not being used.

If you're not acquainted with 500px, you should be. One of the more preeminent photography communities out there, 500px takes you through a journey of incredible shots—anything from nature and urban explorations to cities and architecture to the abstract. Whatever your preference is, you can be sure to find it on 500px.

If you are willing to teach online, you might have thought of making online courses. But if you found it too hard, you can start with micro-courses, that can be created in 10 to 30 minutes. Step 1: Define 5-7 Main Points That You Will Cover in Separate Lessons.

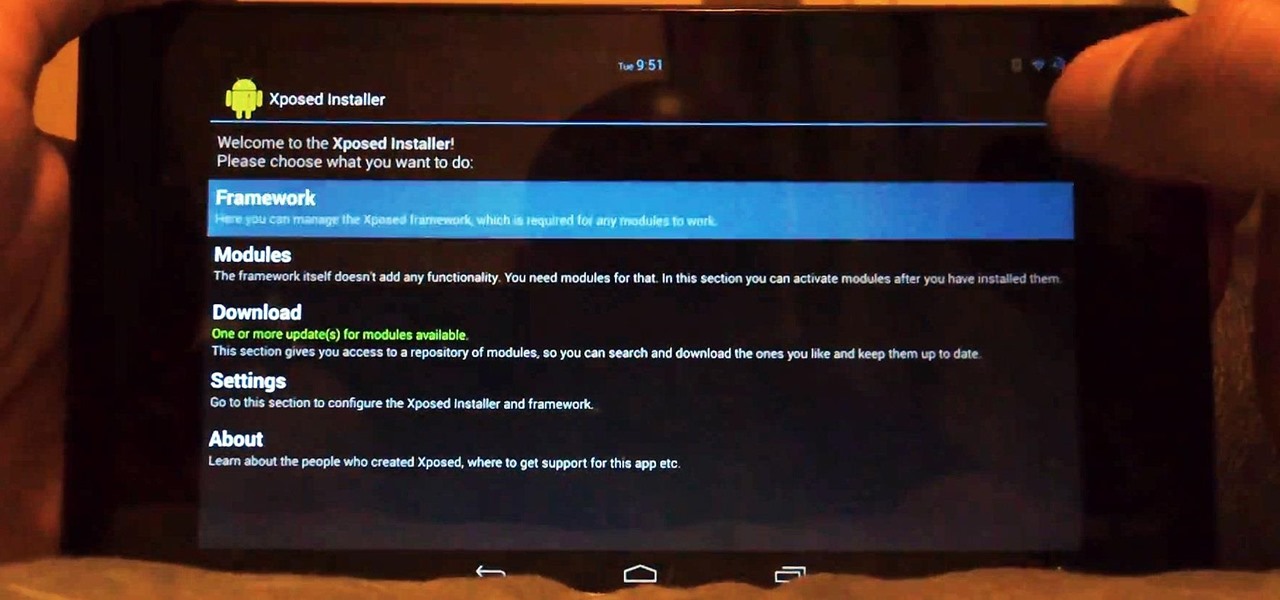
Customization of our Android devices, outside of what Google and mobile carriers allow us to do, used to mandate that our devices were rooted and running a custom ROM.

Welcome to this short and easy tutorial on hacking and DDosing (is that even a word I don't know) anyways lets get started

For most of us regular folk, the only opportunity to relish in the conveniences of a maid is during hotel stays. Personally, I would love to have a maid around to help fold my clothes and sweep up those crumbs that accumulate in the corners of my kitchen, but sadly, I currently live in reality and can't afford that luxury just yet. In real life, I'm on my own.

The high limit thermostat can be found in gas and electric dryers and serves as a safety feature that helps to prevent the dryer from becoming too hot when it’s running. The thermostat is designed to shut off power to the dryer’s heater when the dryer vent is blocked or clogged. The high limit thermostat on your dryer is something that does need to be replaced from time to time. Fortunately, it is a job that you can do on your own with basic tools.

Why do we still need to plug in our phones to charge them? Wireless charging exists, and has for quite some time, but most manufacturers don't include it in their devices. When it comes to the Samsung Galaxy S4, you can buy a QI-compatible wireless charging kit, but between the charging pad and the battery cover, you're looking at around $90 or more.

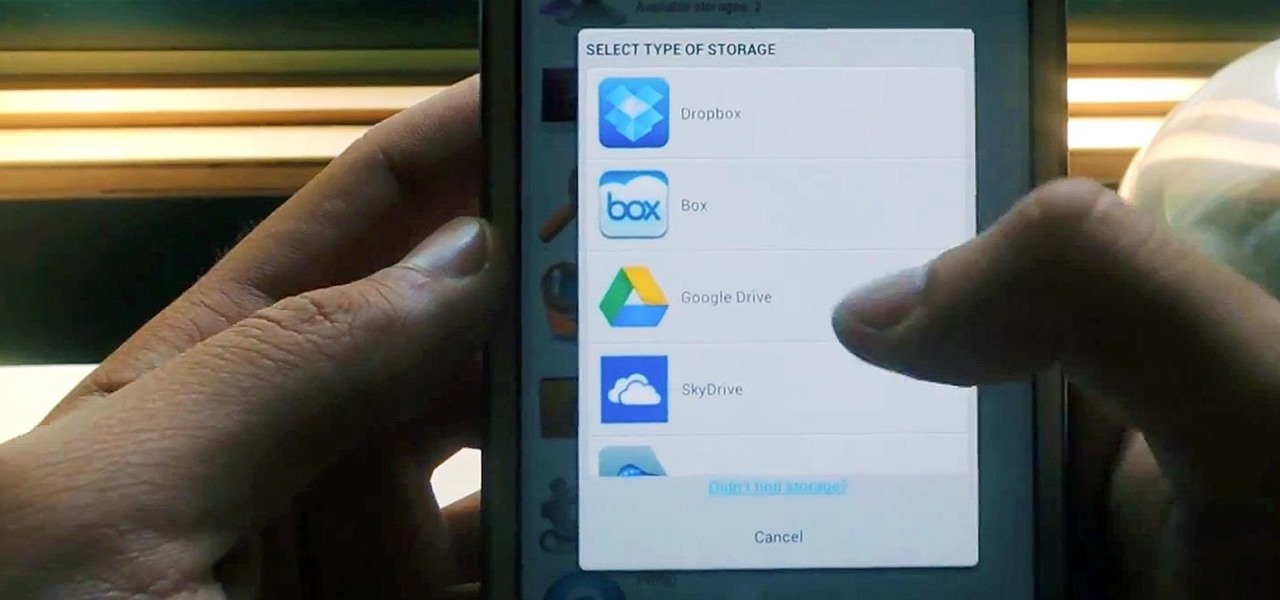
Cloud storage looks pretty good compared to the heavy restrictions that hard drives and other types of external memory carry. The cloud is not only limitless in what it can hold, but it can also easily be accessed from any device that has Internet—your smartphone, work computer, personal laptop, tablet, and more. While accessing a specific cloud storage system like Dropbox or Google Drive may be easy on your Samsung Galaxy Note 2, managing all of them individually can not only get confusing, ...

If you're a frequent Snapchatter like myself, you're probably well aware that Snapchat can't stop you or anyone else from taking a screenshot of a photo received. Instead, they notify the sender that a screenshot was taken—a greatly appreciated fair warning when impetuous photographs are involved. However, there is a loophole to this.

Snapchat's self-destructing nature is the perfect way to send funny and potentially embarrassing photos and videos (something Anthony Weiner wishes he knew about). That's why there are currently 150 million Snapchats sent each day. While it may be used for fun, many fail to recognize that there's a dark side to every good thing. While Snapchat claims that the pictures and videos on their application are completely obliterated—not only from the phone, but from the Snapchat server—there are oth...

How to patch a hole in drywall / plasterboard / Sheetrock. Everyone at some stage in their life will need to patch a hole in drywall / plasterboard / sheetrock. Instead of doing some dodgy patchwork, watch this video to see how simple the job is. The steps are as follow in point form. This method is particularly suitable for holes that are larger than about 100mm or 4 inch's in size.

Gaining remote access to a phone isn't only for super hackers and spies. There are plenty of times when the average smartphone user would want to have remote access to their device.

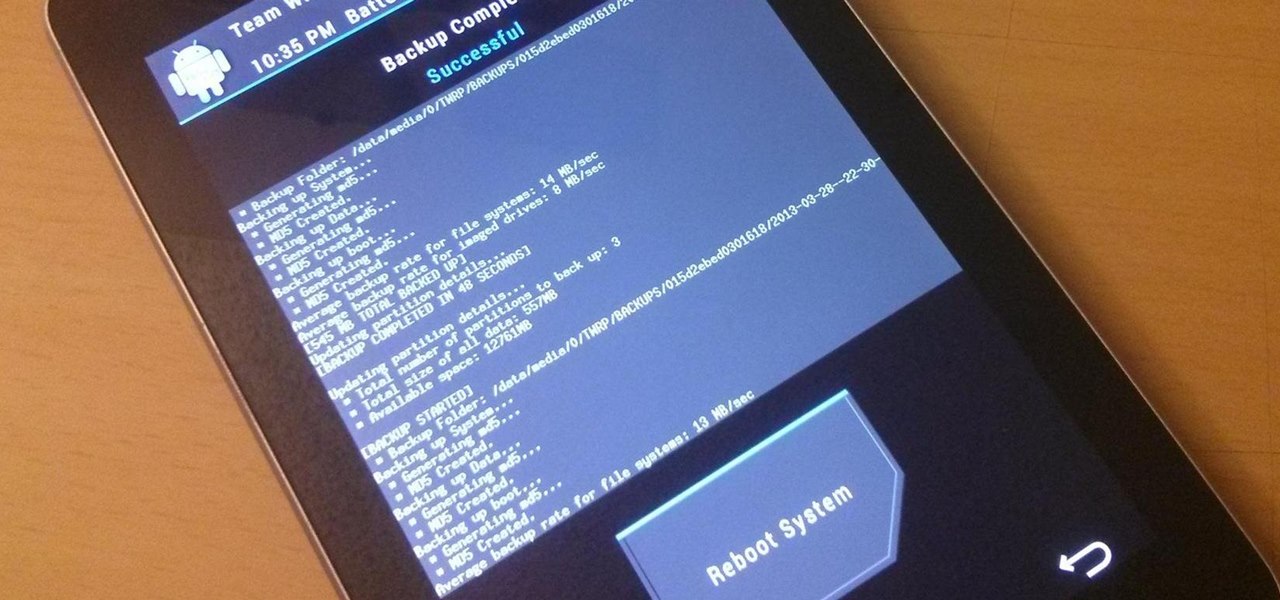
So, you've flashed a bad ROM or ZIP file, and now your Nexus 7 won't boot up. Maybe it just went haywire for no reason. Whatever happened, the bad news only keeps coming—you didn't make a backup of your system, contacts, or apps.

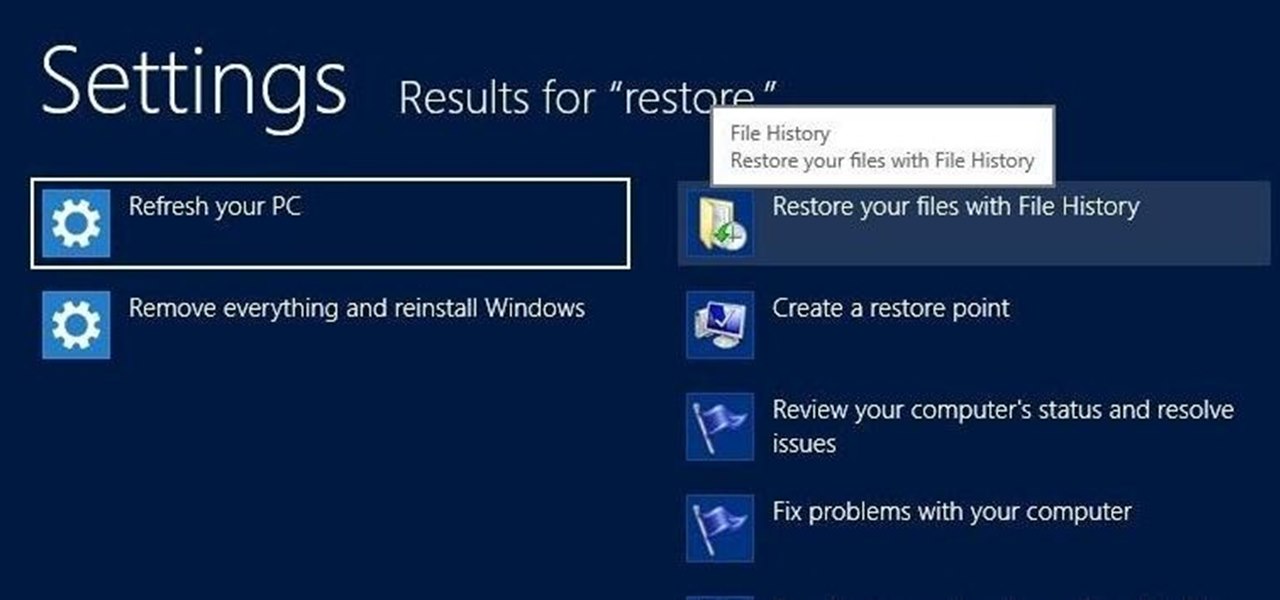
There is nothing worse than losing valuable information or programs on your computer. And if you've ever accidentally deleted a file or document, you know how agonizing that entire process can be.

Samsung does a good job of making their devices fairly open, and the Galaxy S3 is no different. There are numerous way to root a device, but sometimes the jargon and steps can be a little intimidating for new rooters, and even pro rooters.

If you're the type of person who constantly uses multiple tabs in your browser, you know how annoying it is when one of them starts playing unwanted music or video.

I get advice from my friends on a lot of things in life—cool video games, movie reviews, and feedback on my choices in women. Friends can be very helpful in filtering out some of the excess noise and are more likely to give you suggestions you can relate to.

Self-restraint is one of the hardest thing to do. I'm a world-class procrastinator, and one of the biggest causes for my procrastination is my iPhone. Temple Run 2 was probably the best and worst thing that could have happened to me.

We share links on an almost daily basis, usually not even thinking twice about it. Whether you're sending a funny cat video to your sister, or letting your coworker know where to go to download relevant files, there are plenty of reasons you might be giving someone a URL.

On the iPhone, the Reminder app is a great way to keep track of your to-do list. I use it for a bunch of crap I forget, like picking up a must-have item at the store or calling or emailing my friends back.

There are very, very few things better than a solid Hobbit songI mean, I was almost brought to tears when Pippin busted out this one in The Lord of the Rings: Return of the King.

There's a lot going for the Samsung Galaxy Note 2—smart screen rotation, huge HD display, great rear camera—which makes it an awesome device for reading, watching videos, and taking pics. But all of those luxuries will end up hogging up your internal memory, which is one of the few things the Note 2 could use some help in. The device comes with 16 to 64 GB of internal storage, depending on your model, with the option of adding a microSD card for more space. Only problem is, everything automat...

Social media is where we post our thoughts for the world to see, but sometimes a little more exclusivity is needed. And that's where Scrambls comes in.

Last year, Lytro released their first light field camera to help photographers have more control over focusing. This innovative and revolutionary camera allows users to change the depth of focus of a photograph after the picture is taken.

Microsoft's updated web browser, Internet Explorer 10, has only been out for a few days on Windows 8, and there is already a storm of controversy surrounding its launch.

There is no better example of a risk-versus-reward scenario than jailbreaking your iPhone or rooting your Android phone. While both jailbreaking and rooting undoubtedly has its advantages, this possibility of something going wrong and you ending up with a 500-dollar doorstop is never too far out of mind.

One of the greatest consoles ever to exist in the world of gaming is the PlayStation 3, which even lets you do a million different things unrelated to games. But no matter how big of PS3 fan you are, you have to admit that the internal browser is not the greatest. Far from it. While you can access most websites from the PS3, a lot of those site's functions are limited, including Facebook. After reaching over one billion users earlier this month, Facebook is undoubtedly one of the most popular...

Having all of your stuff in the cloud is super convenient if you want to access it on multiple devices, or if you want a backup in case it gets lost or wiped. The biggest downside with services like Dropbox, though, is security. With everything sitting there in one place, the last thing you want is for someone to break in.

Robert Templeman from the Naval Surface Warfare Center in Crane, Indiana and several of his friends from Indiana University recently developed an Android application that is capable of gathering pictures and videos from mobile devices in order to reconstruct a user's environment in 3D. The malware would come coded inside of a camera application that the user would download. The malware, called PlaceRaider, would then randomly take pictures throughout the day and carefully piece them together ...

With iOS 6 coming out yesterday, there were bound to be plenty of glitches. iPhone users filled Apple's forums with complaints, with battery drainage issues leading the way. Many users complained of rapidly increasing battery drainage after updating to iOS 6, specifically with the iPhone 4S.

With the release of Windows 8 right around the corner, if you plan on buying it (or just want to see what it's all about), it's a good idea to take advantage of the free trial before you shell out any money. If you're an Apple user who doesn't have a deep-seated disdain for Microsoft products, this tutorial will show you how to install the Windows 8 preview to try it out on your MacBook. First things first, you'll want to download the Release Preview on Microsoft's website (make sure to save ...

If you've got more than one computer, it can be a huge pain to switch form one to the other. Between files, settings and apps, it can take a while to transfer everything—and if you're running different operating systems, it's even worse. Image by Onion

Tethering your Android phone basically turns it into a mobile hotspot, allowing you to funnel a 3G or 4G internet connection from your phone into your PC or laptop via USB. As you might expect, phone carriers brought the hammer down in an effort to stop users from getting around the fees they charge to normally allow you to do this.

Do you own an HP printer? If so, it may be vulnerable to malware attacks. Researchers at Columbia University discovered that 25% of Hewlett-Packard printers have significant vulnerabilities that put your printer in danger from hackers—even your home. With a budget of just $2,000, researchers Salvatore Stolfo and Ang Cui were able to hack into the printers using remote firmware to install malware, and in some cases even cause the printer to catch on fire. The main issue is with the printer's c...

Today I would like to share a few data about painting on silk with all the creative readers. The knowledge comes in handy if you want to give a homemade gift or even try to sell a few of your masterpieces.
An amazing amount of news this week; new proposals and new agreements have sprung up. But so has our "need" to spread our presence. The military warns of another war, while 26 congressmen decry the use of drone strikes. Read on: