
ARKit 101: How to Launch Your Own Augmented Reality Rocket into the Real World Skies
Have you been noticing SpaceX and its launches lately? Ever imagined how it would feel to launch your own rocket into the sky? Well, imagine no longer!


Have you been noticing SpaceX and its launches lately? Ever imagined how it would feel to launch your own rocket into the sky? Well, imagine no longer!

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

Apple has tools built into iOS to help parents monitor the iPhone habits of their children. However, those same tools can be used by everyday iPhone owners to both hide apps they don't care about, as well as restrict features they don't need or that infringe on privacy. Whether you fit into one category or the other, all iPhone users can benefit from the "Restrictions" feature.

In one of my previous articles, I discussed ShinoBot, a remote administration tool that makes itself obvious. The goal is to see if the user could detect a remote administration tool or RAT on their system. In this article, I'll be demonstrating the use of Pupy, an actual RAT, on a target Ubuntu 16.04 server.

Walsh, a new community under construction on 7,200 acres of former ranch land near Fort Worth, Texas, will one day contain 15,000 homes.

The Raspberry Pi is a credit card-sized computer that can crack Wi-Fi, clone key cards, break into laptops, and even clone an existing Wi-Fi network to trick users into connecting to the Pi instead. It can jam Wi-Fi for blocks, track cell phones, listen in on police scanners, broadcast an FM radio signal, and apparently even fly a goddamn missile into a helicopter.

UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found at my blog, here - https://techkernel.org/2015/12/19/embed-metasploit-payload-in-apk-manually/

One of Android's biggest strengths, when compared to other mobile operating systems is its open file structure. Google introduced a built-in file manager with Marshmallow that provides basic file management, but like with most apps on Android, there are alternatives. Third-party file managers are readily available, providing deeper access and control of all your files.

Welcome back, my greenhorn hackers, and happy New Year! Now that your heads have recovered from your New Year's Eve regaling, I'd like to grab your attention for just a moment to preview 2015 here at Null Byte. I hope you will add your comments as to what you would like to see, and I'll try to honor as many requests as I can.
Canvas fingerprinting is the web's trickiest privacy threat, but it's not impossible to stop. With all the media attention it's gotten lately, it's time we lay out exactly how to detect and prevent this invasive tracking technique.

Anyone who has rooted their Android device has likely used a tool called Android Debug Bridge, better known as ADB, at some point during the process. For most, that is their only interaction with the ADB, but to be a true Android power user, you need to really know the tools at your disposal.

Many of my aspiring hackers have written to me asking the same thing. "What skills do I need to be a good hacker?"

If I were to lose access to the entire internet for the rest of my life, one of the websites I would miss the most would have to be Wikipedia. Wikipedia has ended countless arguments, informed me of how old and single some of my favorite actresses are, and helped me brush up on thousands of historical topics.

DBAs, developers and designers are often tasked with building and managing databases. Especially when the database has been developed by someone else, you have little to no insight into the database structure. Join Quest Software to learn more about Toad Data Modeler and its features that provide:

In this video tutorial, viewers learn how to clear their cache in Internet Explorer. Begin by opening the web browser. Then click on Tools from the top menu and select Internet Options. In the General tab under Browsing History, click on Delete. When the Delete Browsing History window opens, click on Delete Cookies and click OK. To automatically clear cookies, click on Settings under Browsing History and check Every time I visit the web page. Then finish by clicking OK. This video will benefi...

In this Software video tutorial you will learn how to rip music from MySpace using your PC Audacity program. Go to Jerx. Open up Audacity, press 'record' and select 'stereo mix'. After the song is over, click 'stop recording'. Then edit the beginning and end of the song. You have to then export it as MP3 or whatever else you like. For this click on 'file' and scroll down and select 'export as MP3'. Give it a name and click 'save'. In the next window that pops up, fill in the relevant data lik...

Using your laptop you can set up a wireless internet connection at home. You will not need a wireless router to do this. You can turn your computer into a wireless internet access point and set up a local network to which other computers in your home can connect. This feature is recommended for those who have no existing network setup. If you simply have a computer connected to the internet then you would be not needing this. Go to your system preferences and select sharing. Click on the inte...

In this video tutorial, viewers learn how to recover and restore deleted files using Recover. Recover is a freeware data recovery program. Recover recovers files deleted from your Windows computer, Recycle Bin, digital camera card, or MP3 player. Start by selecting the type of file. Continue by inputting the information. It will then take an hour to scan the drive for the deleted files. Once finished, it will display all the deleted files. The green files are recoverable and the red files are...

This video demonstrates how one can makes a homemade paint ball caddy on the cheap. The presenter uses a gallon sized kitty litter bucket. The presenter only spends $8.00 on the kitty litter bucket at Costco and it will hold at least two bads of paint balls. The presenter demonstrates how he added another screw top lid to the kitty litter bucket. By simply cutting a circle the same size as an existing screw lid and then super gluing the lid inside the kitty litter bucket, you have a secure se...

Here are some simple and easy to follow, step-by-step instructions for installing PSP Infcat and PSP Mugen on your Sony PSP. Make sure you get 1.50 core/php for your PSP version. The video is for Fat and Slim and has not been tested on PSP 3000 & PSP Go, because one does not exist. Leda will also be needed.

This innovative handset makes user convenience its priority. Created with the aim of overcoming the limitations of existing mobile phones, every function is available through a flexible layout of navigation keys. Fixed keypads are a thing of the past with the LG KF600 Venus cell phone.
This innovative handset makes user convenience its priority. Created with the aim of overcoming the limitations of existing mobile phones, every function is available through a flexible layout of navigation keys. Fixed keypads are a thing of the past with the LG KF600 Venus cell phone.

This innovative handset makes user convenience its priority. Created with the aim of overcoming the limitations of existing mobile phones, every function is available through a flexible layout of navigation keys. Fixed keypads are a thing of the past with the LG KF600 Venus.

ICELED UFO is a complete automotive underbody lighting kit consisting of four ICELED tubes, an advanced Electronic Control Unit and a wireless Infrared handset that allows the entire system to be remote controlled from inside or outside the car. The ECU can independently address all the pixels in the tubes allowing them to project patterns ranging from complex all the way down to a single color on the ground. The ECU also provides ICELED data for synchronous control of additional ICELED light...

When you're sharing a printer, dealing with cables and networking can be a hassle. Having a printer with built-in wireless or using a wireless conversion kit for standard printers, allows easy sharing of your printer with multiple computers.

This 3D software modeling tutorial series shows you step by step how to create a suitable model for Google Earth within SketchUp. The series will start by showing you how to export data from Google Earth to use for reference, how to build and optimize the modle, texture it in Photoshop or Picasa and export and load it to Google Earth.
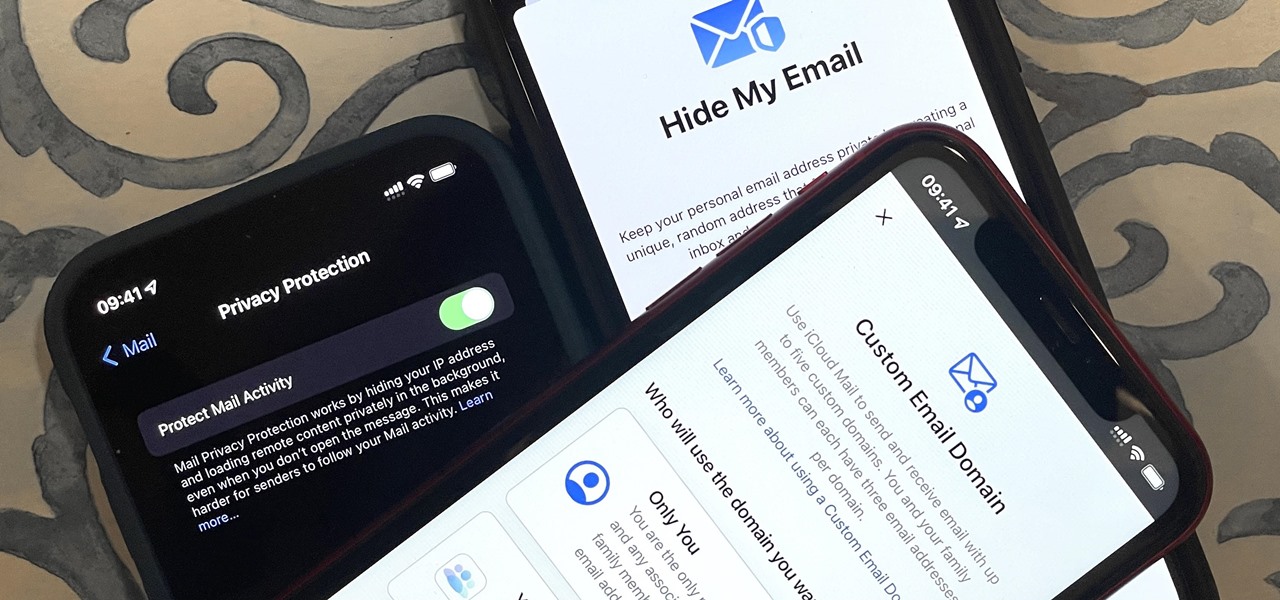
Privacy is a growing concern in the tech industry, but Apple has fallen behind many of its peers when it comes to email security. Fortunately, iOS 15 changes that. Your email address is the key to a vast amount of personal information, not to mention a stepping stone into your other online accounts, so it's great to see new features for iPhones that protect email accounts and their contents.

On Friday, the Tokyo Olympics finally kicked off after massive delays and complications due to the pandemic.

The ability to browse the web in coffee shops, libraries, airports, and practically anywhere else you can imagine is more than convenient, but convenience has risks. Using public Wi-Fi allows others to spy on you easily. Even your own internet service provider can see every website you've ever visited. Don't fall into the trap of protecting your identity, data, and devices after it's too late.

Over the past three years, Epic Games has raised billions of dollars in funding on the success of Fortnite as well as Unreal Engine, one of the top 3D engines available for developing games and AR experiences.

To assist developers and researchers in their efforts to create apps and services for automobiles, Volvo Cars has launched a new Innovation Portal with useful new tools and assets.

Effective communicators are always in high demand in every industry. Whether your team is building the next billion-dollar app or you have a giant data set in front of you for filtering, communicating with your team is essential.
One thing about the small round little Pixel Buds — they might get lost easily if you have a terrible habit of misplacing stuff. Or worse, imagine someone taking a liking to them a little too much and stealing them when you aren't looking. Google thought ahead about these issues, so just like your smartphone, you can track your wireless earbuds from anywhere with ease.

VPNs add a protective layer between your data and your internet service provider (ISP) or bad actors (hackers), so it makes sense they've become so popular lately. Probably the most common one of these is NordVPN, so we explored its mobile app to find all the options worth checking out.

Now that more people are working from home on unsecured networks and personal devices, hackers are having a field day accessing everything from private browsing histories to personal banking information. A virtual private network (VPN) is the first and most important line of defense when it comes to protecting all of your devices from digital intrusions, but not all VPNs are created equal.

In the coming years, artificial intelligence (AI) will revolutionize every facet of technology and business. AI researchers are in high demand. Salaries in this field are regularly in the hundreds of thousands of dollars.
Apple released the second developer beta for iOS 13.6 today, Tuesday, June 9. This update comes one week after the release of its first developer and public betas, previously called iOS 13.5.5, as well as the general release of iOS 13.5.1. Apple's first 13.5.5 beta introduced evidence for Apple News+ audio support.
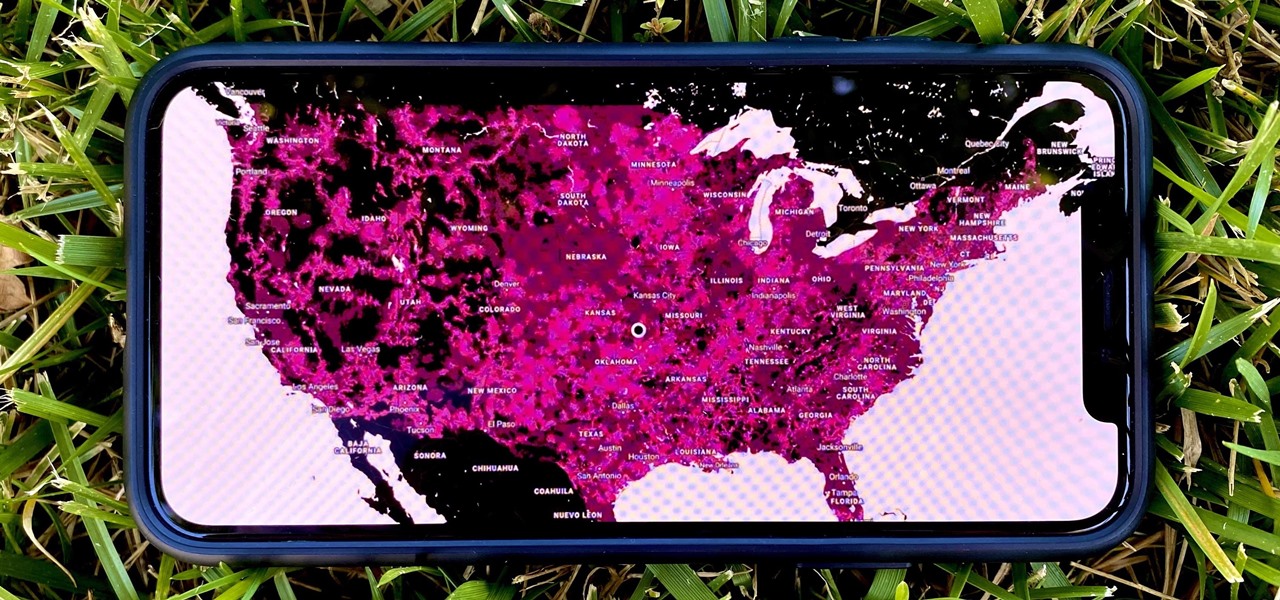
In 2009, 4G LTE networks rolled out in Stockholm and Oslo, replacing 3G as a better upgrade to the mobile data technology that gives us the broadband speeds we have on our mobile devices. Over a decade later, and we have the latest, next-generation wireless network technology among us, 5G, but can you even use it?
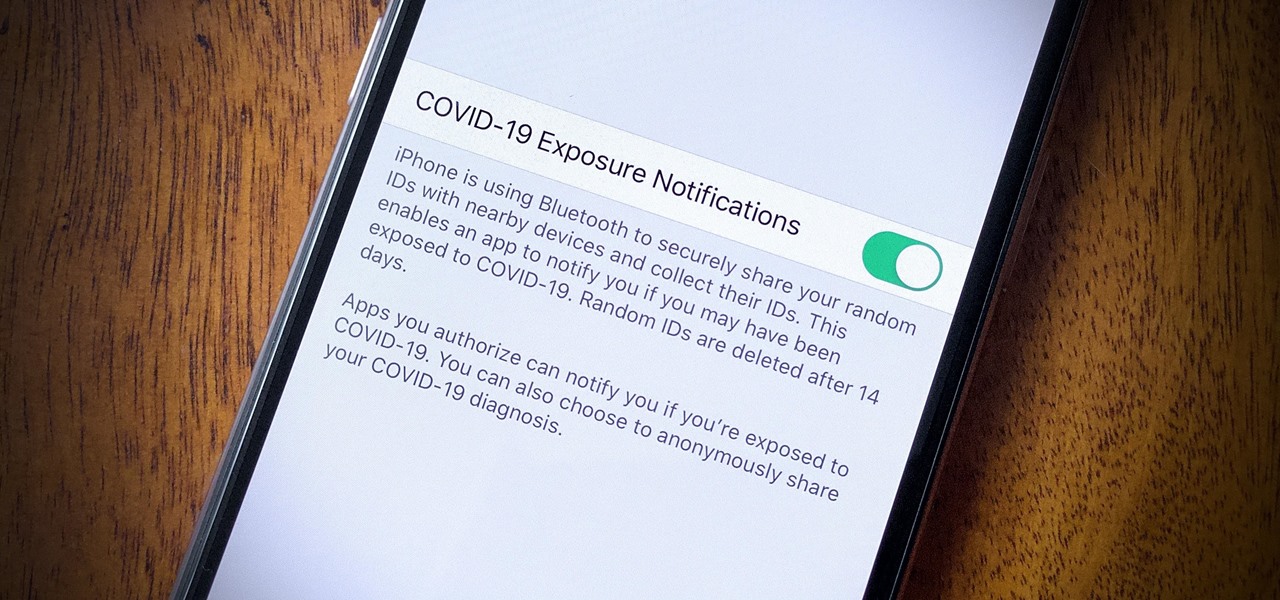
In iOS 13.5 and later, developers can create and release contact tracing apps for iPhone, which could help slow the spread of the novel coronavirus in the U.S. With these apps comes COVID-19 exposure notifications, which you may or may not want to receive. If you don't want to get these alerts, you can disable them.

Wi-Fi networks come in two flavors: the more common 2.4 GHz used by most routers and IoT devices, and the 5 GHz one offered as an alternative by newer routers. While it can be frustrating to attack a device that moves out of reach to a 5 GHz Wi-Fi network, we can use an Alfa dual-band adapter to hack Wi-Fi devices on either type of network.