Since its inception in 2007, the Pwn2Own computer hacking contest has been challenging the vulnerability of mobile phones and web-related software. In 2010, the fruit of two full days of hacking came down to the exploitation of the following web browsers: Safari 4 on Mac OS X, Internet Explorer 8 on Windows 7, and Firefox 3.6 on Windows 7. The winners walked away with the successfully hacked computer, plus a cash prize, but they left one Godly browser intact: Google Chrome. Even the savviest ...

FEATURED DOCUMENTARY: Exit Through the Gift Shop, the first film directed by reclusive street-art legend Banksy, is a little puzzle-box of a documentary. It's perfectly designed and pitched to be enjoyable on multiple levels: on one as an entertaining, illuminating mini-history of "street art" and on another - one entirely more convoluted and entertaining - as a light-hearted "up yours" to both street artists and their patrons.

Happy Whore-o-ween! It's that time of year again for ladies to shed their inhibitions, show off the booty, and debase themselves. It's no great surprise that Jersey Shore is 2010's most popular costume choice.

For this prank it will be required to take place within a crowded area, where there are porto potty's frequently used by the public. Under the toilet seat where the you open the lid different types of fireworks need to be placed at the bottom to go off at different times, (When different people come in to use the loo.) You also need to have smoke canisters at the top of the roof of the porto potty to go off to dazzle and confuse the unsuspecting victim and then light one batch of the (non let...

From Major Nelson, Xbox 360's spokeperson: Kinect Pricing: Existing Xbox 360 owners can purchase Kinect and Kinect Adventures for $149.99 (U.S. ERP). Remember, Kinect will work with every Xbox 360 ever made.

False eyelashes really can elevate your look. Don't be intimidated, they are easier to apply than you think. Follow these four simple steps for this fabulous look. Eye Makeup

I've heard some people say that "brown people smell bad!" Ahem. Brown people don’t smell bad! Okay, some do, but so do people of all races and cultures. How a person smells has nothing to do with their race, but rather choices they make. I choose not to smell bad, and take steps to make sure that does not happen. Personally I cannot stand bad smells. It's something that makes me feel sick, so I try my best to make sure that I am not the cause of a certain odor. The following are steps I take ...

In this tutorial you will learn how to create glossy web icons in Illustrator CS2. Very often you will be able to download royalty-free icons from the Internet, but the problem is they are not customized to fit in with your existing web site's design. So creating your own icons is always a good way if you have the time to do it. Make sure to hit "play tutorial" in the top left corner of the video to start the video. There is no sound, so you'll need to watch the pop-up directions. Create glos...

The resume is an essential tool for getting freelance work assignments. A well written article is not enough when trying to secure a freelance or staff position as a writer. Publishers want to see a resume. It gives the writer an outstanding opportunity to introduce themselves and it gives the editor a general idea of who you are, where you've been, and the work you've completed.

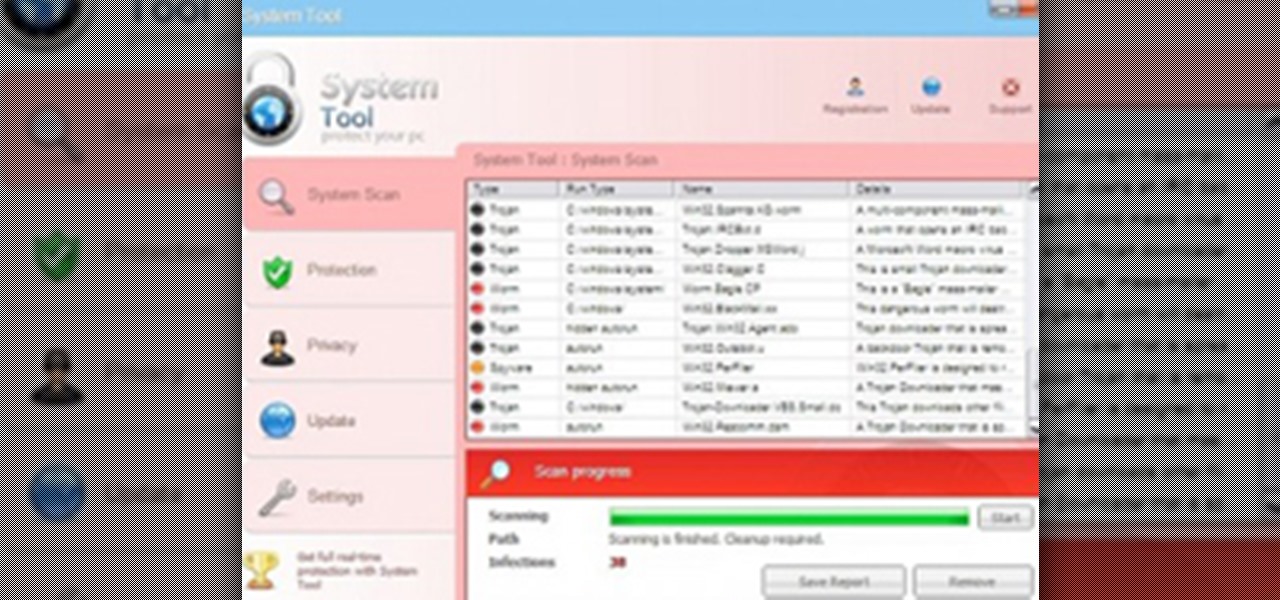
System Tool. It sounds like something your Windows computer might need, but it's the exact opposite.

This week's FIGRR is all about games that are old-new (or new-old, if you like) school. Each celebrates a different vital, yet largely taken for granted, aspect of video game history in the decidedly new-school world of indie games. Their titles betray them. Blocks That Matter is all about blocks. Recettear: An Item Shop's Tale is all about item shops. Neither are particularly sexy aspects of gaming, but both are ubiquitous elements of great games that can stand on their own.

L.A. Noire is the newest Rockstar (GTA4, Red Dead Redemption) game created by Team Bondi ( The Getaway). The game is set in the late 1940’s in Los Angeles. The main character, Phelps, is a war veteran rising through the ranks from police officer to detective. The game is presented in mini episodes (one case per episode) and flashbacks. Once you finish a case, you go straight to the next one. Having played four cases where the character moves from police officer to detective, here are my initi...

Sounds like a false promise à la infomercial or typical spammy web headline—how can a 4.8 ounce gadget aid in weight loss? But, in truth, "who" better to act as a dedicated personal trainer and nutritionalist than the iPhone? The smartphone is completely and utterly tethered to the daily life of the average middle to upper class American. It's reliable and exact. All it needs is a charged battery, the right app, and of course, as with every diet and fitness regime, a user with unwavering self...

How do we really come to the decisions that we make? Is it just flip a coin and hope for the best or is there some underlying procedure that we go through, consciously or unconsciously, that guides our course of action?

Hallelujah, a miracle tool has been released to the world. This Windows/Mac tool is called Spirit and it enables you to jailbreak any iPhone, iPod Touch or iPad quite easily. And Gizmodo is all over it, with an in-depth guide on exactly how to do it.

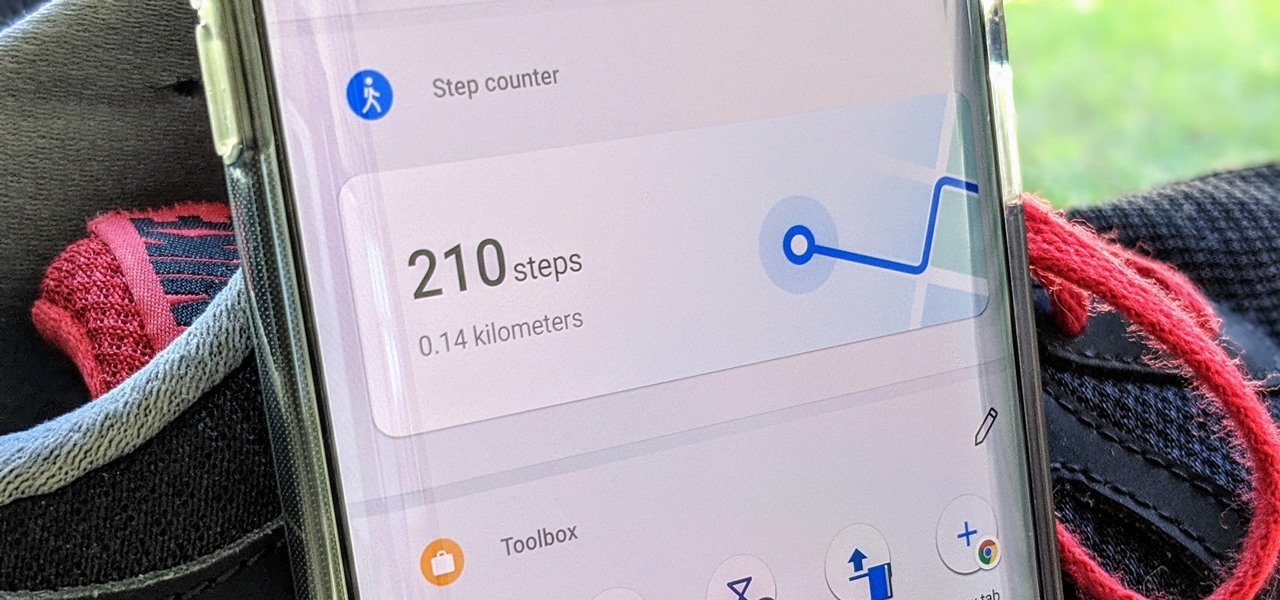
A great way to incorporate a healthy exercise routine is by taking lots of steps throughout the day. While most smartphones can track and report your steps via a third-party app, you can check them right from your home screen if you have a OnePlus phone.

Business owners and marketeers are diverting from traditional marketing techniques, including billboards, radio and TV advertising, brochures, and any other outdoor promotions, to cheaper but effective Internet marketing strategies. Under the new arrangement, business owners reach out to the final consumers through advertising on the World Wide Web.

Advances in technology continue to make our lives easier and more convenient. If you want to send fax, for instance, you no longer need to own a fax machine. You can easily and quickly send fax directly from your computer in one of several methods, including via an Internet fax service provider or using Windows built-in Fax and Scan tools. Read on how to use an Internet fax service, one of the faster faxing methods, to send fax messages from your PC.

You have some hip hop dancing experience but now you are ready to develop some new moves and routines. Learn advanced hip hop funk choreography from a professional instructor in this free dance video series. Perform the hip hop "head toss with roll" move - Part 1 of 15.

Sponge balls are a very cool magic effect. But you will have to master palming first. You will get very good reactions. The best part is that you can simply keep them in your pocket. Here is how to start.

The abdominals can be considered one of the best signals of fitness and strength and is one of the most sought-after muscle groups to develop by both men and women. While the abdominals are very desirable, it can be one of the most difficult areas to distinguish and maintain. This article's purpose is to give you the hard truths, advice, and workout for gaining a hard body and new look.

Sometimes a person can feel life is getting you down - you don't feel productive, or there's not enough hours in a day to do everything you need. You might not feel motivated to get up in the morning or to go to work anymore, and sometimes one might ask oneself "Is this all there is to life?"

Choosing a nanny or au pair for your children is a process that should be organized and performed carefully, to ensure you find someone who can be trusted, will contribute significantly to the development of your child and integrate well into your family.

No one likes it when random people wander into your home and mess things up, which is why it behooves you to hide your things from even the most prying eyes with builds like this totally invisible, 2x2, piston-operated door with no visible redstone either inside or outside. The story of Goldilocks and the Three Bears may have gone differently if they would have had one of these babies installed in their home: I did a tutorial for a piston-powered trapdoor and many people wanted to know how to...

Last time, we looked at archaic cryptography, so you should have a basic understanding of some of the concepts and terminology you'll need. Now, we'll discuss one of the most important advances in computer security in the 20th century—public key cryptography.

If you're a frequenter of Null Byte, I bet you have at least some interest in information security. Furthermore, you have a hobby that if applied in certain ways, will get you arrested. I've received quite a few messages from the community here about federal cybercrime law and how it applies to them, so I decided to get together with my lawyer to come up with some answers.

If you're hungry, eat now, because this list is probably going to put you off consuming vittles for so long that you'll end up looking like the love child of Nicole Richie and Skeletor. Now that you've been officially warned, help me count down the ten most WTF food items on this beautiful blue marble we call Earth.

Here's something fun for the Null Byte community to do—a coding competition! This week, I wanted to get everyone involved by offering you all a nice library of possible program types to choose from and try to code. At the end of this competition, all of the submitted programs will be reviewed by the community and myself. The coder that receives the most votes will be dubbed THE BEST.

How did it happen? How did your ultra-secure WPA password on your wireless network get broken into? Well, you might have just found yourself at the mercy of a cracker.

Apple is famous for their easy to use consumer software such as Garage Band and iMovie. However, I've found their apps a little hard to use. Why?

Here's a nasty little Null Byte. An open redirect vulnerability was found in both Facebook and Google that could allow hackers to steal user credentials via phishing. This also potentially allows redirects to malicious sites that exploit other vulnerabilities in your OS or browser. This could even get your computer flooded with spam, and these holes have been known about for over a month.

If you've ever wondered how software pirates can take software and crack it time and time again, even with security in place, this small series is for you. Even with today's most advanced methods of defeating piracy in place, it is still relatively easy to crack almost any program in the world. This is mainly due to computer processes' ability to be completely manipulated by an assembly debugger. Using this, you can completely bypass the registration process by making it skip the application'...

Zynga just added another game to their Zynga with Friends series called Scramble with Friends. If you've ever played Boggle, it's basically the same thing, but is dedicated to playing your buddies just like Words with Friends or Hanging with Friends.

With the purchase of my latest computer, installing Linux turned into a nightmare from Hell. The graphics drivers are probably the biggest issue that anyone with a newer computer will run into when installing Linux. AMD and NVIDIA are the dominant ones on the market, both of which have awful support.

Having an SSH or Secure SHell to tunnel your traffic through is something we have talked about many times at Null Byte. As we know, it allows us to securely route and encrypt our traffic through a remote server, effectively anonymizing us and protecting our traffic from all forms of analysis—simultaneously. We have gone over how to make a home SSH tunnel. However, the question has come up, "How can I get an SSH tunnel to somewhere other than my computer?" This would be useful in a situation w...

Skype is a great service. It allows a free solution for VoIP to VoIP calls, and cheap VoIP to landline calling. However, a very disturbing, little known fact that might push you away from Skype does exist. If you closely read the terms of service agreement, it clearly says that Skype is allowed to decrypt your messages whenever they please. Here at Null Byte, we tend to enjoy our anonymity, don't we?

Friday's Community Byte was weird. The intent was to do a HackThisSite mission, but upon time to begin, everyone in there was programming without my assistance, with the help of Sol Gates. This is great! It's really awesome that everyone enjoys programming that much and will make the effort to learn even when I am not present. So, a tip of my hat to Mr. Sol Gates and the rest of you fine people.

Part 2 Welcome back! In my last post I talked about the exterior aspects and techniques of building a great looking house, and now we shall focus on the interiors.

REVENANT n pl. -S one that returns 61 points (11 points without the bingo)

Your IP (Internet Protocol) address is your unique ID on the internet. It's synonymous with your home address. Anyone in the world can contact your computer through its IP address, and send a retrieve information with it.