When it comes to Easter, I usually dig plastic eggs with money or chocolate inside but hard-boiled eggs shouldn't be missing from the party. And simple hard-boiled eggs won't do. You need to decorate them because we all know bunny eggs are extravagant. What's even better than bunny eggs, though? Spider-bunny eggs.

Not having internet sucks! We do a ton online these days, from working, shopping, studying, and collaborating, to watching fail videos and endlessly clicking through memes.

Streaming video has definitely changed how we watch movies and television shows, but with the constantly growing number of services out there, it can be hard to keep track of who's got what. Who's got Disney now? Starz? Netflix? Who knows. And when you add sites that let you rent or purchase titles, you could spend all evening trying to find something to watch. Here to simplify the process is a service called Can I Stream It?, which lets you search for your favorite movies and TV shows to fin...

Dianne Tice and Roy Baumeister gave a bunch of college students a questionnaire in which the students answered questions about their work habits. In a class which she taught, Tice also assigned a paper with a deadline which she said could be extended and observed which students availed themselves of the option to extend.

One of the main reasons why the Samsung Galaxy S III has dethroned Apple's iPhone 4S as the best-selling smartphone in the world is due to Android's open-source operating system. The vast spectrum of customization that comes with Android has become one of its focal points, allowing n00bs and programmers alike to build and destroy. The open-source OS has allowed rooting and modified ROMs to flourish within Android community. The only problem with this is that rooting and installing your own RO...

With the ever-evolving technology that imbues photography, we are never short of fantastic awe-inspiring shots. Digital cameras can capture things that the naked eye only wishes it could see, like streaking lights, rapid movements, and faraway objects, and it's fairly easy to capture these things if you know the basics.

If you're tired of your roommate stealing your Cheetos out of the pantry or simply want to indulge in something creepy, then keep reading. With the iPhone 5 finally released, many people will soon be selling or giving away their older iPhones. But should they? Instead of ditching your old iPhone, why not use it to engage in some Big Brother type espionage? There are some really awesome ways to use your old iPhone, but spying on people is definitely the most bang for your buck. First, you'll w...

Apple announced earlier this week that the official release date for iOS 6 will be September 19, but why wait when you can get it now? The Gold Master developer version was made available on Wednesday, and it's the same file as the final version that's going to be released to users on the 19th. Anyone can download it, so if you want to avoid being part of the frenzy on Wednesday when everyone else is trying to get it too, it may not be a bad idea to get a head start. A quick note: If you inst...

With the release of Windows 8 right around the corner, if you plan on buying it (or just want to see what it's all about), it's a good idea to take advantage of the free trial before you shell out any money. If you're an Apple user who doesn't have a deep-seated disdain for Microsoft products, this tutorial will show you how to install the Windows 8 preview to try it out on your MacBook. First things first, you'll want to download the Release Preview on Microsoft's website (make sure to save ...

Even though we all know it's a bad idea, a lot of people still use their browser's store password function to keep up with all their accounts. While convenient, this shortcut also makes their passwords very easy to find if you have access to the computer they're stored on.

It may be surprising, but those cardboard toilet paper tubes are dead useful for so many things besides just keeping the circular shape of your TP roll. As shown before, you can make car dash mounts for your mobile phone, but that's just one of the many beneficial uses from a seemingly junk cardboard tube. You probably go through quite a bit of bathroom tissue over the course of a year, especially if you're using it for facial tissues, too. So, the next time you throw away that lonely little ...

Assuming everyone knows of the recent "String of attacks" passed between Obama and Romney, I just want to talk about how useless this entire thing is. I'll try to be as un-biased as possible.

RFID cards are becoming a fairly common way to purchase goods, but they're already widely used to pay fares on buses, trains, subways, and trolleys across various cities. TAP cards are quick and reliable, but it can be a real pain to remember to bring them with you, especially if you weren't planning on using public transportation that day. Luckily, an intrepid tinkerer at Adafruit has managed to find a way to embed an RFID card into her phone, something you're far less likely to leave at home.

Everyone knows that using your phone and driving is illegal, and rightfully so. Tons of people die on the road everyday due to careless people texting or calling someone. Everybody knows that it's wrong, yet everyone still does it anyway.

Remote desktop in windows is set up with these easy to follow steps. First go to your start menu this is in the bottom left corner of your desktop. In the start menu locate your control panel. In the control panel open up your systems folder. Once this is open click the remote tab at the top right of this folder. In this tab you will have the option to check “allow user to connect remotely to this computer.” From here press ok to exit out of the systems folder.Again click the start menu, navi...

Keep you and your family safe by equipping your home to prevent home invasion. Discourage home invasions by being cautious and making a break-in more difficult. Have a plan in the case your home is invaded.

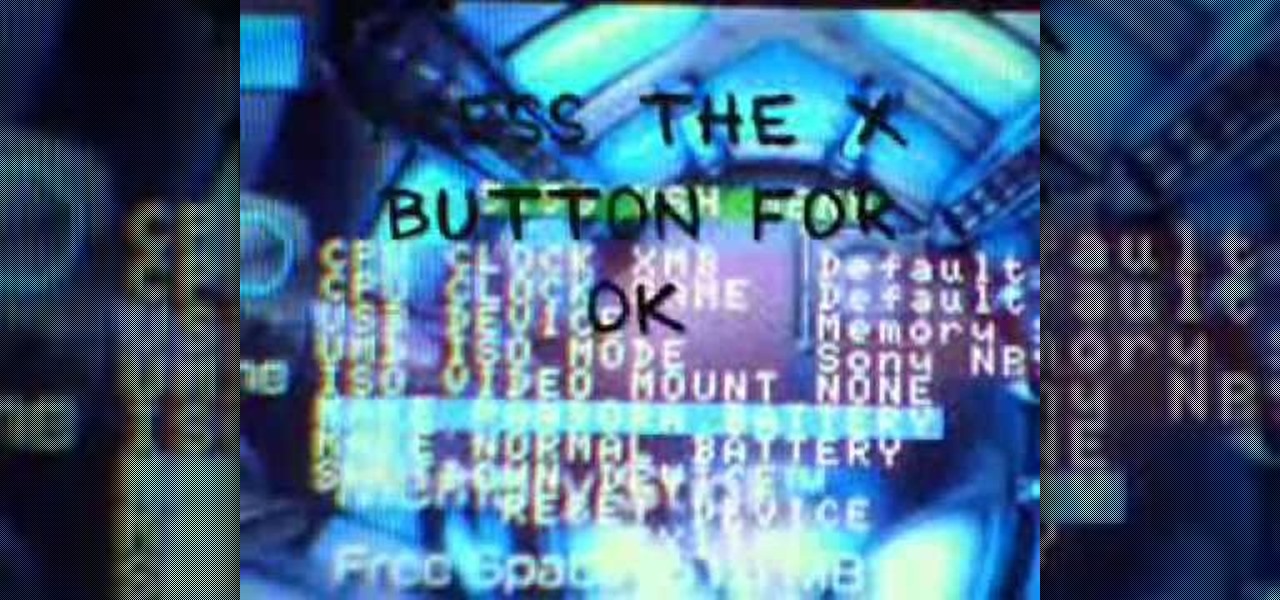
Make a Pandora Battery on 5.50 Gen B (full) 1. Make sure you are running on 5.50 Gen-B (full)

In this how-to video clip instructional series, our expert demonstrates how to fell a tree using either a chainsaw or a rope or both. He informs us about the correct tools to use to cut down a tree and about the safety equipment one needs to fell trees. He also explains the process of cutting down a tree, including planning the felling, planning escape routes, wedging, cutting notches in the tree trunk, using a felling wedge, felling a tree with a rope and a truck cutting down a tree with a c...

In this video tutorial, viewers learn how to refurnish hardwood floors. Using a drum or belt sander, begin by cutting 36 grit abrasive. Then remove all the old finish marks and scratches from the main body of the floor. Using an edge sander, do the same thing. Now vacuum the floor and then repeat the process once again with both sanding machines, except use 50 grit abrasive this time. For the third time, use 80 grit abrasive and 100 grit abrasive for the fourth time. Remember to vacuum each t...

This video is on how to install a Revo forward only (or FOC) for your radio controlled vehicle. For this, you will need to remove your 2.5 or 3.3 Revo transmission from the kit and then I will walk you through the rest. You will basically be removing the front gears and then replacing another gear towards the back. Also, I am using the center differential kit which is easier as you do not have to worry about the gearing on the center differential shaft. If you do not purchase the center diffe...

Build a motor mount out of Lexan by making a template that ensures your plan will work and that you will reduce time, frustration, and re-work. Then, cut out the polycarbonate, mark the cutout on the motor, and assemble it all together on the radio control vehicle.

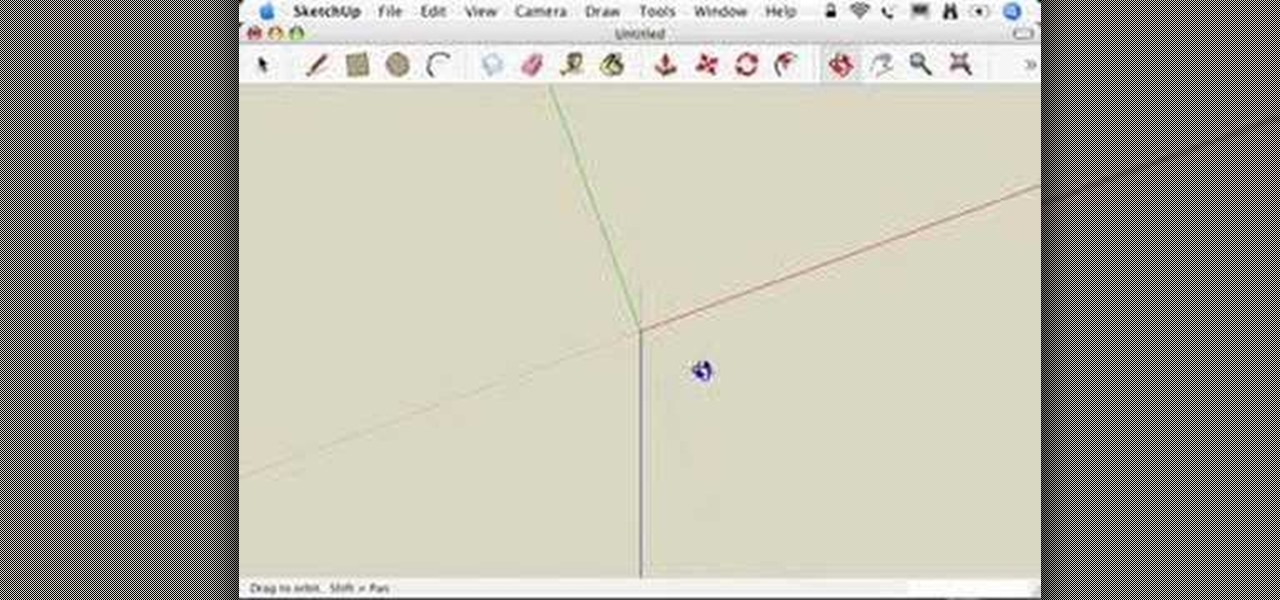
This video series takes you through every step of building a building in SketchUp and is taken from chapter 4 of "Google SketchUp for Dummies" in case you want to follow along. PART 1 explains how to switch to a 2D view to get you ready to build the floor plan. It's a good idea to have accurate measurements of everything you want to build before starting this project. PART 2 familiarizes you with the tools available in SketchUp to help you create your floorplan. PART 3 shows you how to draw t...

Just when everything seemed settled over at Magic Leap, it turns out that the internal tumult is still in play.

Facebook Reality Labs just experienced its first major executive exit since the pandemic began. Hugo Barra has announced that he's stepping down from his position as vice president of VR at Facebook.

Spotlight, Apple's system-wide search feature, lets you search for apps, contacts, messages, webpages, music, notes, and other content that's on and off your iPhone. On iOS, it's known as "Search," and you can access it by swiping your home screen down or swiping open the Today View screen. It's not exactly convenient, but an accessibility feature can unlock Search so you could open it from anywhere.

Your ability to control exposure in the Camera app is much better in iOS 14. Instead of setting the exposure for a single shot, you can also lock an exposure compensation value for an entire session while you take photos and videos. A session ends as soon as you exit the app, but you can also remind your iPhone to use your last used ECV the next time you open Camera.

For some, one of the coolest new features in iOS 14 is the Picture in Picture mode, which had previously only been available on the iPad. With it, you can continue watching a video from an app in an interactive floating overlay window on the home screen or within other apps. But for others, it can be annoying when it appears unexpectedly all of the time, and there's a way to stop it.

Whether you miss the good old days of Telnet or you want to know what hacking was like when security was nothing but an afterthought, Telehack is the game for you. The text-based hacking game is a simulation of a stylized combination of ARPANET and Usenet, circa 1985 to 1990, with a full multi-user universe and player interactions, including 26,600 hosts.

During the Google I/O 2019 keynote, the latest Android Q Beta was released to the public for Pixel smartphones along with 15 other non-Pixel devices. It's the third Developer Preview for Android 10, but it's the first official public beta outside of Google's Pixel smartphones. A new public beta means good things are on the way as the future of Android continues to evolve.

Smartphones are now indispensable when traveling. Domestic and overseas travel alike require food, navigation, translation, and so much more to make work or vacation successful. Gone are the days of lugging multiple tourist books around with you everywhere you go — you need to let your smartphone handle the dirty work.

Silence spreads over these mountains like nothing I've ever felt. If I didn't have Moby blasting in my earphones, there'd probably be no other sounds around. Well, except for someone, Phil probably, murmuring in a nearby tent just low enough to make his words indiscernible.

With just a few taps, an Android phone can be weaponized into a covert hacking device capable of running tools such as Nmap, Nikto, and Netcat — all without rooting the device.

Developed by Open Whisper Systems, Signal is a free, open-source encrypted communications app for both mobile and desktop devices that allows users to make voice calls, send instant messages, and even make video calls securely. However, a vulnerability was recently discovered for the desktop version that can be turned into a USB Rubber Ducky payload to steal signal messages with a single click.

The iOS App Store is a big place, offering over two million applications in total. However, there are actually some apps you can and should install on your iPhone that the iOS App Store doesn't include. And no, these apps do not require any difficult jailbreaking or complicated sideloading techniques — they are really simple to install.

While installing the new Android 9.0 Developer Preview is fairly easy if you're using a Windows machine, it's a little trickier if you want to use macOS instead. To help you get the latest Android OS on your Google Pixel phone, we'll break down the whole process so using your Mac can be as simple as Windows.

With Virtual Network Computing, you don't need to carry a spare keyboard, mouse, or monitor to use your headless computer's full graphical user interface (GUI). Instead, you can connect remotely to it through any available computer or smartphone.

An attacker with shell access to a Linux server can manipulate, or perhaps even ruin, anything they have access to. While many more subtle attacks could provide significant value to a hacker, most attacks also leave traces. These traces, of course, can also be manipulated and avoided through methods such as shell scripting.

When hacking into a network during a penetration test, it can sometimes be useful to create your own wireless AP simply by plugging a Pi into an available Ethernet port. With this setup, you have your own backdoor wireless connection to the network in a matter of seconds. Creating an AP is also helpful while traveling, or needing to share a connection with a group of people.

Imagine for a moment that a VPN is like putting on a disguise for your computer. This disguise works to change your IP address, secure your traffic with encryption, and mask your location to bypass regional restrictions. This makes it a helpful tool for both whistleblowers and journalists. VPNs are also built into the well-known Tor Browser.

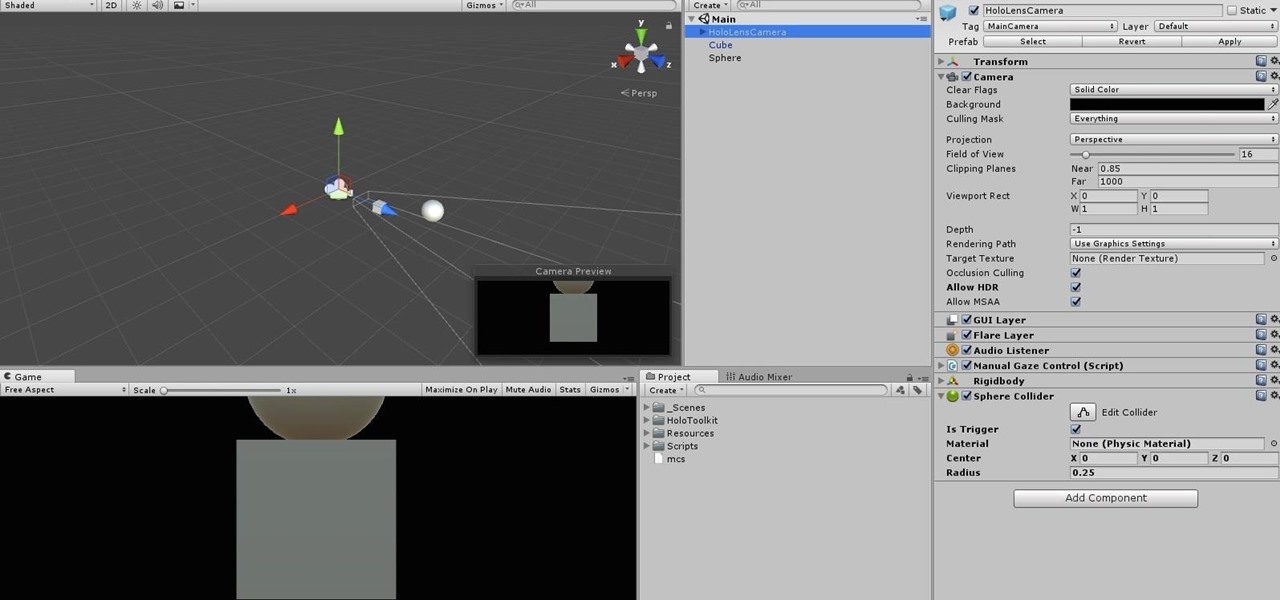
When making a convincing mixed reality experience, audio consideration is a must. Great audio can transport the HoloLens wearer to another place or time, help navigate 3D interfaces, or blur the lines of what is real and what is a hologram. Using a location-based trigger (hotspot), we will dial up a fun example of how well spatial sound works with the HoloLens.