If you own a Pixel or Nexus device, Project Fi is a great alternative for cellular service outside of the four major US carriers. Project Fi is a Google-managed MVNO, providing service primarily through the T-Mobile and Sprint networks. One of the biggest mysteries on Fi is which network you're connected to at any given time, but there's a simple solution.

Null Byte users have often requested video content, but the question has always been what format would best serve our community. This week, we partnered with Null Space Labs, a hackerspace in Los Angeles, to test the waters by hosting a series of talks on ethical hacking for students in Pasadena Computer Science Club. We invited students and Null Byte writers to deliver talks on Wi-Fi hacking, MITM attacks, and rogue devices like the USB Rubber Ducky.

We're all looking to meet someone, and in this day and age the easiest way to do that is through one of the various dating apps out there. But we can all admit it can get disheartening swiping through all of those people for the frustration of someone not answering your messages after matching. The fact is, we could be missing out on great people just because they don't have time in their busy lives to answer their dating apps every day. Not to mention the fact that we as a society are becomi...

Several recent research studies have pointed to the importance of the microbes that live in our gut to many aspects of our health. A recent finding shows how bacteria that penetrate the mucus lining of the colon could play a significant role in diabetes.

Welcome back everyone! It's been quite a while hasn't it? Today we're going to kick off the second part of the Python training series by introducing modules. We'll start off by explaining what a module is and we'll give an example. So, let's get started!

Welcome back! In our last training session we covered classes and how OOP can make programming/scripting easier. Today we'll be taking a breather and covering something fairly simple, bitwise operators.

Welcome back! In the last round of python training, we talked about tuples and dictionaries. We'll be diverging again and talking about logical operators as well as membership operators. These are used very similiar to booleans, so if you haven't read that, I suggest you do so first.

We've all been there before. Preheated the oven, popped in the cake, and then became distracted by this, that, or the other... until we either smelled burning or had the smoke detector pierce our eardrums.

When I tried to set up an eviltwin for a MitM-constelation in kali 2.0, I couldn't provide internet to the victim. The origin was the brctl bridging. I have read many tutorials but all of them where explained in backtrack and older versions of kali. So i was searching for a solution without using brctl and this solution will be explained now. This will just work on unencrypted wireless-environments.

Hi everyone! In the previous part of this series we introduced remote code arbitrary execution via buffer overflows using all of our past experiences.

As a lover of food, I'm often asked, “If you could only have one food the rest of your life, what would it be?” My answer is always the same: sourdough bread. (Okay, it's not always the same... I usually cheat and say sourdough, fancy cheese, and a good beer.) Admittedly, I'm biased by my own sentimentality. My mother is an expert bread baker, with a major in making sourdough. Her sourdough starter is older than I am, and in all honesty, she's made thousands of loaves, each better than the ne...

Welcome back, my amateur hackers! When you are using and administering Linux, it is important to be conversant in the use of the log files. As you know, log files are the repository for much information about our system, including errors and security alerts.

Being the bearer of bad news is unpleasant; there's nothing more uncomfortable than offering up a spoonful of negativity. Whether you're a supervisor who spends a lot of time interviewing and rejecting candidates, or simply someone who has to say "no" to a friend, it's never fun to break bad news. But sharing unpleasant words or feedback with another person can become less of a burden with a few simple steps.

Greetings. This how-to on hacking Windows 7/8/10 etc. admin account passwords using Windows Magnifier is focused on adding, changing, or deleting an admin level account on a Windows 7/8/10 etc.

You probably already know what you want to do when you grab your phone. More than likely, you're either going to make a call, send a text, or open an app. So why can't you just do that right from your Samsung Galaxy S3's lock screen?

I recently had my iPhone stolen at public park and did everything I could to locate it, but with Find My iPhone disabled (I know, what an idiot) and no exact address to give to the police, I had about a .00000001 percent chance of getting it back.

In this article, I'll be continuing my series on microcontrollers. If you haven't read part one, I'd recommend heading over there and reading it!

For the vast majority of people, coffee is a must-have in the morning. It provides a stimulating effect that not only wakes you up, but sets your mood and attitude for the rest of the day. Personally, I wouldn't get anything done without coffee.

If you've been thinking about changing careers and you have just a little bit of time, The Ultimate 2021 Web Developer & Designer Super Bundle may be just what you need. This is also the perfect time to get it because it's on sale for $34.99, which is 98% off the regular price of $1,886. You'll get 14 courses that offer 39 hours of content on HTML, JavaScript, CSS, and more.

Now that the dust has finally settled on Microsoft's big HoloLens 2 announcement, the company is circling back to offer more granular detail on some aspects of the device we still don't know about.

In 2018, augmented reality went from the vague promise of interesting things in the near future to tangible developments in software and hardware, proving that immersive computing is indeed the future.

Perhaps you've thought about rooting your OnePlus 5, but thought again when you heard SafetyNet would prevent you from using apps like Google Pay, Pokémon GO, or Netflix. Those are valid struggles when you root using traditional methods. There are no such worries when using Magisk, as it masks the fact that your device has been modified.

While hackers have taken advantage of numerous vulnerabilities in Adobe's products to deliver payloads to Windows users via PDF files, a malicious PDF file can also wreak havoc on a Mac that's using the default Preview app. So think twice before double-clicking a PDF open on your MacBook — it might just be a Trojan with a rootkit inside.

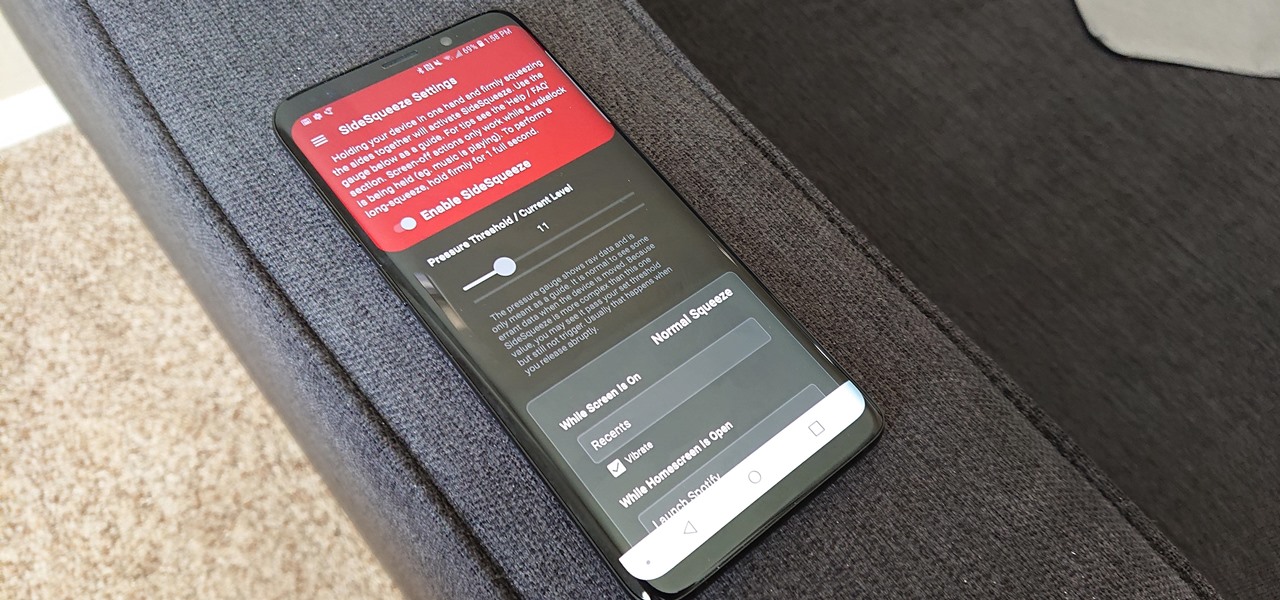
All the Android fans out there undoubtedly remember the squeeze gestures introduced with the HTC U11. Google continued the trend by bringing the gestures to the Pixel 2 and Pixel 2 XL. Thanks to a brand new app, you can now enable similar squeeze actions on your Galaxy S9 or S9+, and even some older Samsung phones.

Android O has finally arrived—well, it's technically a beta version, but that isn't stopping Android enthusiasts from going crazy about it. The first Developer Preview was released earlier today and is available right now to install on Nexus and Pixel devices. While Android O doesn't have an official name or Android number yet (we're betting on "Android Oreo"), Google has released a feature list and a blog post explaining almost all of the new changes and features.

Hello everybody. I'm back with Part-2 of this series. In this part we will be programming in C our server and i will be explaining one more "key concept" so everybody got a better understanding on this.

My first ever post on here was 'Keeping your hacking identity secret' and it did very well, and its not something I see here on null byte. So read along.

Welcome to a tutorial explaining functions. This article will help clarify some things we have already been exposed to such as function prototypes, function calls, return values, etc.

hello hackers,newbies and followers of this great community, after some research here in our community, I noticed that there is not even one tutorial that teach Web Development. We have a lot of tutorials on how to hack web site but many do not know exactly how a web site is composed, then I decided, meeting the community's needs, begin to teach people how to develop web sites.

Hello fellow training hackers. I do not know if many of you are familiar with ruby, but since it is a useful scripting language, that hasn't been covered too much here on Null Byte, I thought why not do some How-tos about it now and then.

Welcome back, my tenderfoot hackers! Well, the first season of Mr. Robot just ended and Elliot and fsociety successfully took down Evil Corp! They have effectively destroyed over 70% of the world's consumer and student debt! Free at last! Free at last! Of course, global financial markets crashed as well, but that's another story.

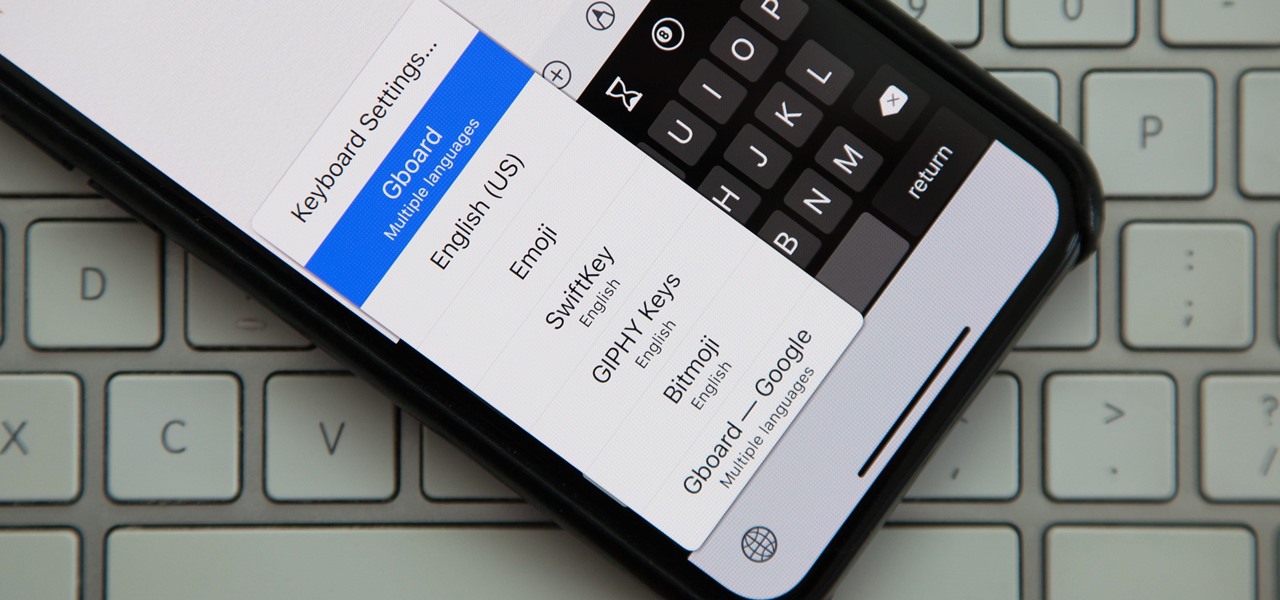
Back in iOS 8, Apple introduced the option to use third-party keyboards on iPhone, and since then, there have been a ton of third-party keyboards available such as Gboard, AudioShot, SwiftKey, Slated, and many more. However, adding and even using these keyboards can be kind of tricky.

Welcome back, my fledgling hackers! Scripting skills are essential is ascending to the upper echelons of the hacker clique. Without scripting skills, you are dependent upon others to develop your tools. When others develop your tools, you will always be behind the curve in the battle against security admins.

Steampunk is a tremendously interesting phenomenon because of its reliance on science fiction, and fiction in general. Steampunk can arguably be broken down into two categories: the fiction, and the aesthetic. Sometimes these categories cross over, but they're often more distinct than most people suspect; that said, the aesthetic is firmly based in works of fiction.

If you can't find the remote for your Android TV or Google TV, don't like using its voice control feature, are sick of using the directional pad to type, or can't get it to work at all, use your smartphone instead. Using your iPhone or Android phone as a virtual remote control can be more convenient, easier to use, and more helpful than the original remote, so it's definitely worth trying out.

The team at NASA is in full mission preparation mode as they prepare to send a new team to the moon for the first time in decades via the Artemis program in 2024.

Facebook Reality Labs chief Andrew "Boz" Bosworth does a lot of hinting and teasing of what's coming next at Oculus, often with only a vague timeline on the horizon.

We've reached the point in the trajectory of augmented reality's growth where AR advertising experiences are becoming commonplace tactics rather than rare experiments.

The past year has revealed a gaping hole of opportunity in the world of business called virtual meetings. Some existing players like Zoom hopped on that opportunity, while others like Skype seemed stuck on the sidelines, and Google Meet just managed to catch up in time to snag some of the shift in remote work.

A stager is a small piece of software that's typically used by malware to hide what's happening in the early stages of infection and to download a larger payload later.