Welcome back, my novice hackers! New hackers often ask me the same question: "What is the easiest platform to hack?" My response is always the same—it is not a platform, but rather a particular piece of software that is easiest to hack, which is on nearly every client-side system. That software is Adobe Flash Player.

Welcome back, my greenhorn hackers! Congratulations on your successful hack that saved the world from nuclear annihilation from our little, bellicose, Twinkie-eating dictator. The rest of world may not know what you did, but I do. Good job! Now that we hacked into the malevolent dictator's computer and temporarily disabled his nuclear launch capability, we have to think about covering our tracks so that he and his minions can't track our good works back to us.

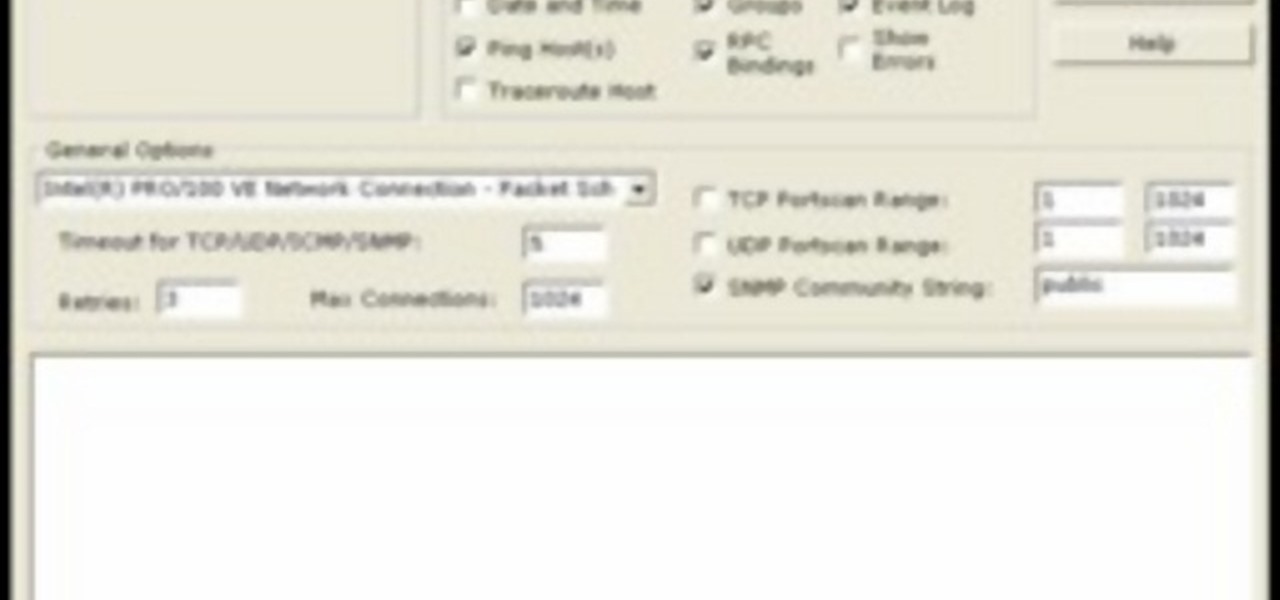
A router is the core of anyone's internet experience, but most people don't spend much time setting up this critical piece of hardware. Old firmware, default passwords, and other configuration issues continue to haunt many organizations. Exploiting the poor, neglected computer inside these routers has become so popular and easy that automated tools have been created to make the process a breeze.

Hello Hackers! Welcome to my 2nd Post: This is a tutorial explaining how to hack android phones with Kali.

Welcome back, my greenhorn hackers! After the disaster that was Windows Vista and the limited and reluctant adoption of Windows 8 and 8.1, Windows 7 has become the de facto standard operating system on the desktop/client.

Welcome back, my hacker apprentices! Several of you have written asking me how you can check on whether your boyfriend, girlfriend, or spouse is cheating on you, so I dedicate this tutorial to all of you with doubts about the fidelity of your spouse, girlfriend, or boyfriend.

In part one of this tutorial we found out that your English teacher is a paedophile, by using a Man in the Middle attack to intercept his internet traffic.

Things that are supposed to make life easier for developers and users are often easy targets for exploitation by hackers. Like many situations in the tech world, there is usually a trade-off between convenience and security. One such trade-off is found in a system known as Distributed Ruby, which can be compromised easily with Metasploit.

Welcome back, my rookie hackers! Now that nearly everyone and everyplace has a computer, you can use those remote computers for some good old "cloak and dagger" spying. No longer is spying something that only the CIA, NSA, KGB, and other intelligence agencies can do—you can learn to spy, too.

If you're one of those crazy completionists who just has to find and exploit every glitch in every game that you get, you've found friends here. This video will show you how to find and exploit one wall glitch in the Atacama Desert level of Battlefield: Bad Company 2 for the XBox 360.

You would think that with each major iOS update, there'd be fewer ways to bypass the lock screen. Unfortunately, Apple's developers have consistently failed every year since 2013 in this department, leaving open lock screen exploits for iOS 7, iOS 8, and now the latest iOS version, iOS 9, with each exploit being discovered within days of the OS release.

NMAP is an essential tool in any hacker's arsenal. Originally written by Gordon Lyon aka Fydor, it's used to locate hosts and services and create a map of the network. NMAP has always been an incredibly powerful tool, but with it's newest release, which dropped mid-November of last year, they've really out done themselves.

Researchers at the cyber security firm Zimperium have recently uncovered a vulnerability in roughly 95% of Android devices that has the potential to allow hackers to take total control over your phone with a simple picture message (MMS). The gritty details of this exploit have not been made public yet, but hackers now know the general framework for this type of attack, so you can be certain that they'll hammer out the details in no time.

If you want to die in style, check out this video for a tutorial on how to use the javelin to serve as a martyrdom utility!

Here's a fun hack! In this clip, we learn of a bug that will permit you to circumvent the passcode lock screen on any iOS 4.1 iPhone 4. For detailed, step-by-step instructions, and to get started using this exploit yourself, watch this video guide.

This guide is written for anyone who is practicing his penetration skills using the Metasploitable 2. The problem that we are facing here is that we have to penetrate to Metasploitable 2 and when this happens we understand that we are not logged in as root but as a user with less privileges!

Welcome back, my novice hackers! In this continuing series on Metasploit basics, let's next look at a module that many aspiring hackers find useful—autopwn.

Welcome back, my newbie hackers! We've already saved the world from nuclear annihilation and covered our tracks afterwards, but the world is still threatened by a malicious, megalomaniacal dictator with missiles and nuclear weapons.

GamingGuy118 shows a live walkthrough of glitches & tricks for Modern Warfare 2 on Favela. Watch step by step how to use a variety glitches & tricks during gameplay for Modern Warfare 2 on Favela. Strafe jump like a pro, learn the Elevator trick, find the perfect sniping places, and earn a lot of points. Learn the tricks to accessing untouchable positions. Exploit glitches to take out your enemies and render yourself untouchable. Hover a mile above the ground and take down your opponents. Fol...

For Infinity Exists Full Disclosure's first Website Hacking episode, we demonstrate how to exploit a security vulnerability occurring in a website's database to extract password hashes. Sql (Structured Query Language) is a computer language designed for the retrieval and management of data in a system's database. The Attack, known as Sql Injection, manipulates Sql statements before they are sent to the Sql Server, allowing the Attacker to create, change, or retrieve data stored in the database.

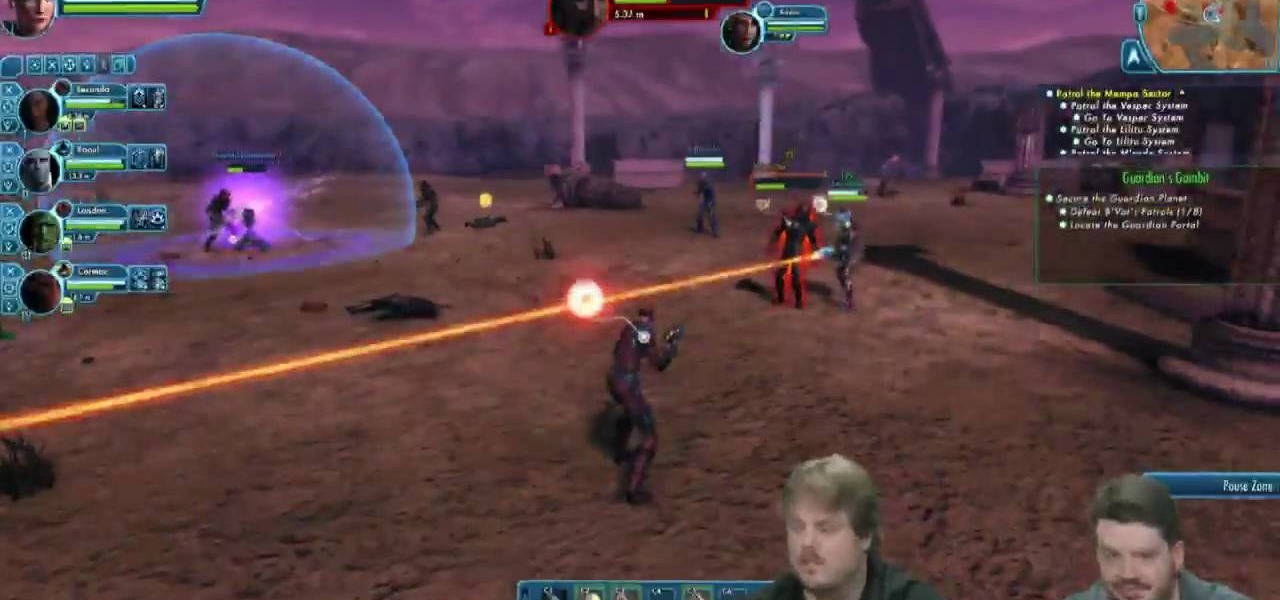
Don't be just another red shirt! Here's a detailed tutorial showing you how to engage in ground combat when exploring a planet. Make sure you've equipped the right weapons and know how to use their expose and exploit functions!

Nmap is possibly the most widely used security scanner of its kind, in part because of its appearances in films such as The Matrix Reloaded and Live Free or Die Hard. Still, most of Nmap's best features are under-appreciated by hackers and pentesters, one of which will improve one's abilities to quickly identify exploits and vulnerabilities when scanning servers.

When attempting to compromise a target, we want as much control as possible over the victim. Metasploit's meterpreter allows us to have immense control over the victim, the only issue is that sometimes we can't land a meterpreter. We may only be able to land a standard shell, but fear not, there is a way to upgrade our shell into the all powerful meterpreter!

Welcome back, my fledgling hackers! If you're like most aspiring hackers, at one time or another you've probably spent too much time playing Call of Duty and not enough time preparing for your final exams.

Head down under for some glitched out action in COD: Black Ops Annihilation Shangri-La Zombies. Watch this video and elarn how to exploit a glitch in the map that will put your on the other side, not across, but underneath the map.

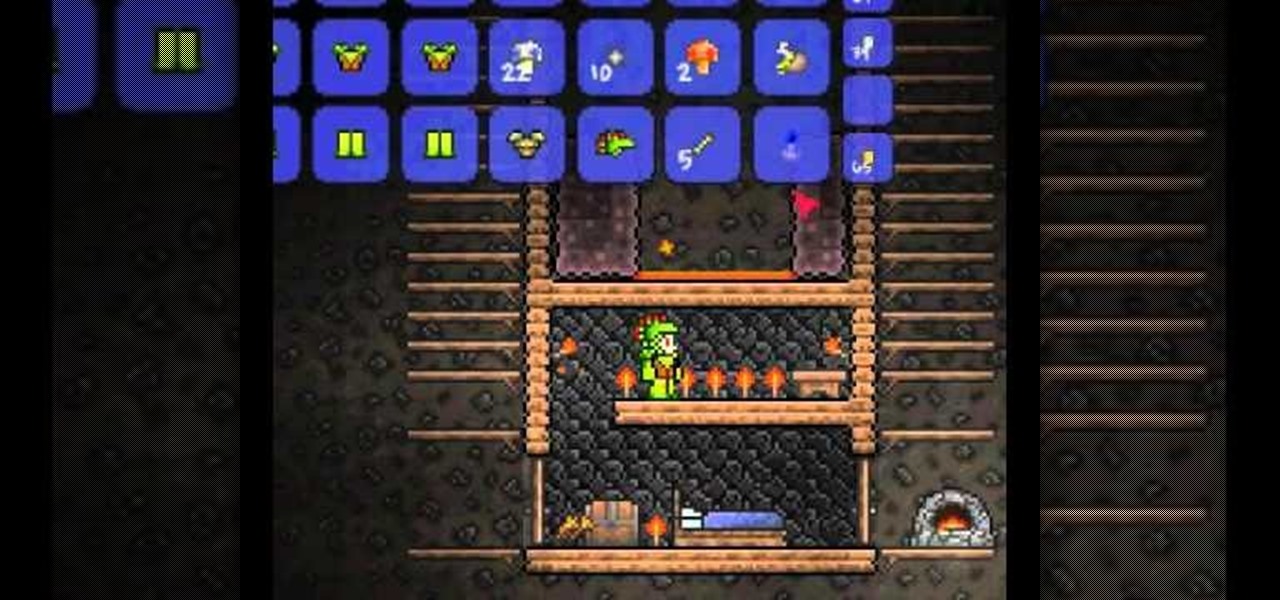
Tired of the game turning off your Underground Jungle lava trap? Watch this video and learn how to exploit the game so that it turns back time, allowing you to earn more gold and platinum. Put this Terraria hack to use.

Money doesn't grow on trees, they say. Well, in Terreria it does grow in chests, and this video will show you a clever glitch you can exploit to get infinite money from your chests. Learn this Terraria glitch so you can have infinite money.

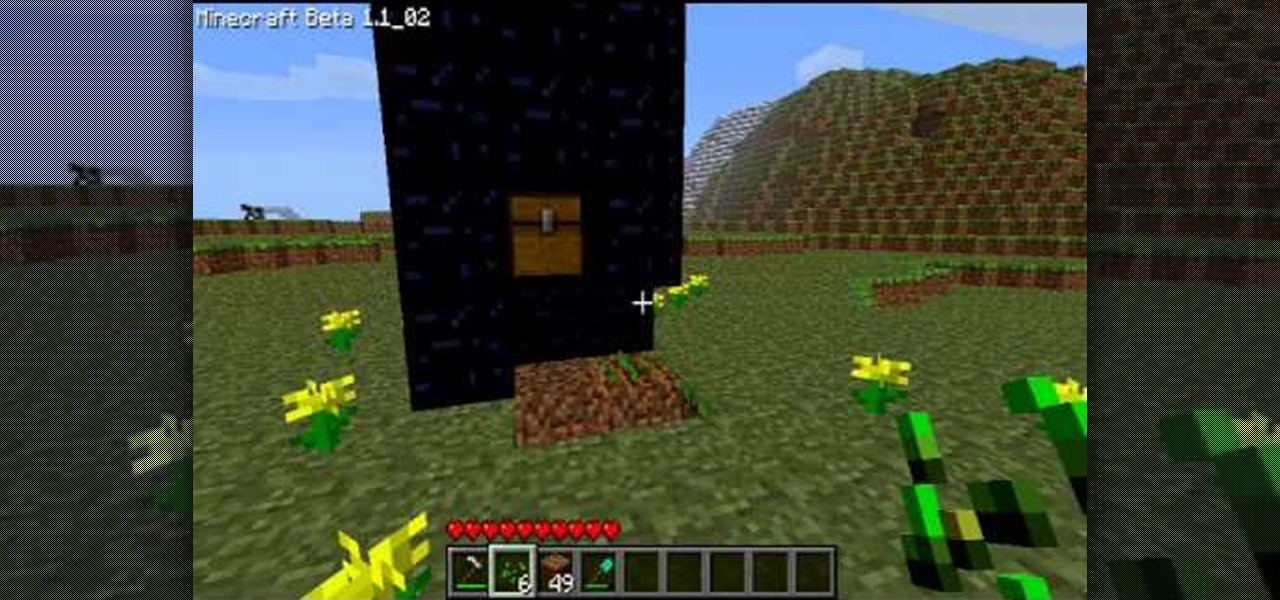
Even if there's a giant block of obsidian, you can figure out a way to exploit a glitch that will let you easily break into it. You're also shown a way to easily break into protected chests on shared servers in Minecraft.

When you're fighting zombies, you sometimes want a way to keep them at bay. There's a glitch in the map Five on Call of Duty: Black Ops that you can exploit to set up an invincibility barrier when shooting zombies.

This is a small exploit of a glitch that can give you infinite xp and money when you play Dragon Age: Awakening. After you complete a certain mission, hold off on accepting the follow up mission. Just talk to the commander again and again, getting money and XP each time you do it.

Believe it or not, people are still using Friendster. Which is great news for all you hackers because that means there are accounts to hack! With this video you'll find out how to exploit a programming loop hole in order to hack into someone's Friendster account. We can't promise you'll find anything interesting!

In this video tutorial, a CEH-certified Ethical Hacker will teach you how to exploit the old netbios remote IPC$ share while also demonstrating the beginning stages of a successful network security audit. For more

Take a look at this instructional video and learn how to install the Twilight hack for you Wii. The twilight hack is an exploit that reads a elf file off the root of your secure digital (SD) card. To start up this hack, you'll need to load the Zelda: Twilight Princess game before you can run any unofficial software.

Do you play basketball? Take a look at this instructional video and learn how to steal the ball on the court with Kansas senior point guard Russell Robinson. To this you, first you need to apply pressure. As you do this you force your opponent to make mistakes and this will give you a window of opportunity to exploit the situation. Keep in mind that you need to maintain defensive principles.

Lock screen exploits are becoming increasingly common in the mobile world. Four weeks ago there was the iPhone 5 passcode bug (which just got fixed yesterday...kinda). Then there were a couple lock screen bugs on the Samsung Galaxy S3 two weeks ago.

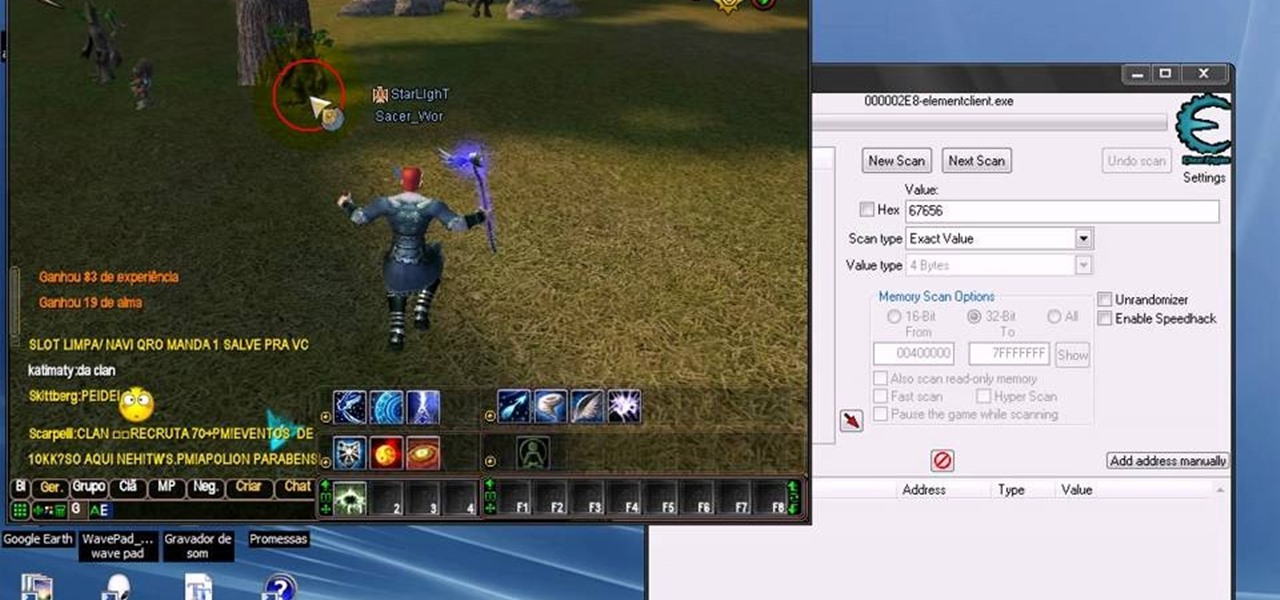
Tired of grinding out endless, boring quests for meager returns when you're playing Perfect World International? Want to rocket to high level and immense piles of treasure immediately? Cheat Engine is your answer! This free game hacking program frees you from having to hunt for cheat codes or exploit glitches to get ahead in PWI. Just follow along with this easy and quick hacking tutorial, which shows you how to use this program to change many of the values of your character and in the game.

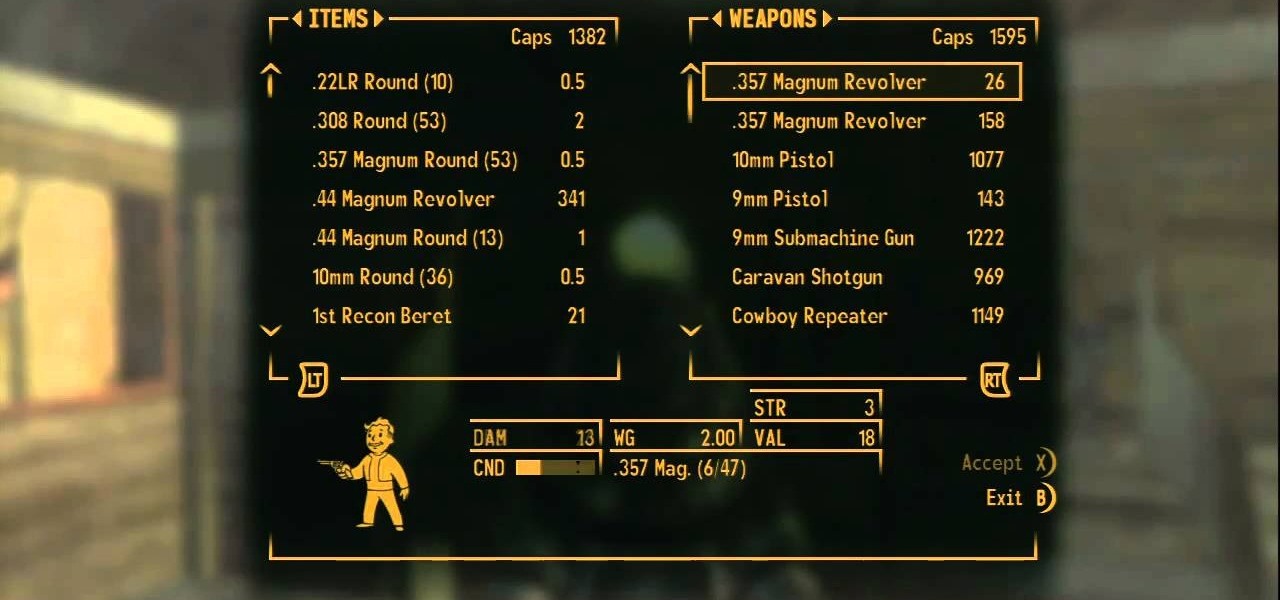
An old glitch seems to have carried itself over from Fallout 3 right into Fallout New Vegas! Not surprising as they used the same game engine and resources, but regardless of that, you'd think that the Q&A team would have caught it. In this video you will learn how to exploit this glitch by purchasing a cheap item and then selling it back for more than the original price over and over and over again. Details in the video!

Have you ever wondered how sumo wrestlers are able to obtain and maintain such massive figures? Joseph Stickland, an applied clinical nutritionist, will explain to you exactly how a sumo wrestler is able to do this. Joseph will also explain the health detriments and the dangers to this type of lifestyle. Joseph explains that sumo wrestlers will skip breakfast, exercise, eat massive amounts of calories, (10,000 calories at least) for lunch, take a nap, and then have another mega calorie meal f...

There's an easy way to get more money in Happy Island, and the answer is Cheat Engine. With CE, you can easily earn more money, so start hacking today!

Stick Wars hacks, cheats, glitches. How to hack the flash game Stick Wars from Addicting Games. Watch this video tutorial to learn how to hack Stick Wars with Cheat Engine (09/27/09).