Welcome back, my newbie hackers! We've already saved the world from nuclear annihilation and covered our tracks afterwards, but the world is still threatened by a malicious, megalomaniacal dictator with missiles and nuclear weapons.
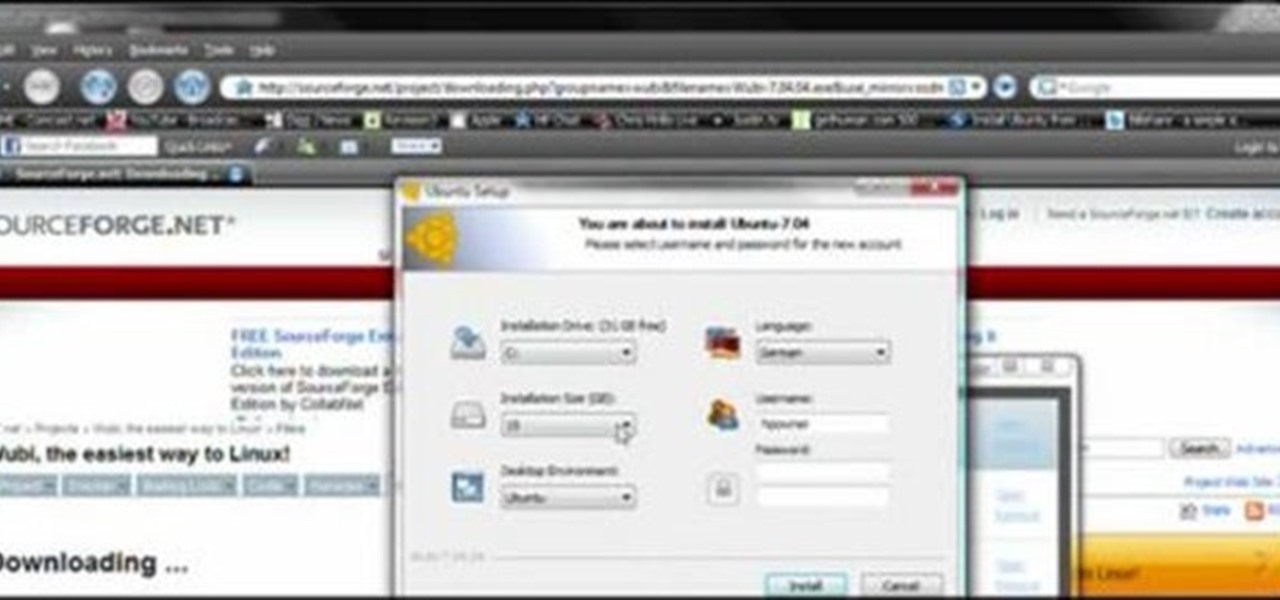
This is a easier way to install Ubuntu with out having to partition your hard drive. Wubi (www.wubi-installer.org) allows you to boot into Ubuntu by saving a file to the boot folder in Windows Vista or Windows XP. You can always uninstall Ubuntu easily without any complications to Windows Vista or Windows XP. This is not VM ware.

One of the best ways to improve your skills as a hacker is to learn to combine different avenues of attack to achieve success. What if it were possible to get a victim to connect to our machine and execute a chosen payload on our behalf? This is indeed possible with the almighty Metasploit and the aid of a technique known as command injection.

When using Linux, we often need to install new software, a script, or numerous large files. To make things easier on us, these files are usually compressed and combined together into a single file with a .tar extension, which makes them easier to download, since it's one smaller file.
Hello Null-Byte community. First off: this my first post here on Null-Byte. Some of you may have already seen me in the comment section, to all others: Hi, I'm the new guy.

Researchers at the cyber security firm Zimperium have recently uncovered a vulnerability in roughly 95% of Android devices that has the potential to allow hackers to take total control over your phone with a simple picture message (MMS). The gritty details of this exploit have not been made public yet, but hackers now know the general framework for this type of attack, so you can be certain that they'll hammer out the details in no time.

Welcome back, my amateur hackers! When you are using and administering Linux, it is important to be conversant in the use of the log files. As you know, log files are the repository for much information about our system, including errors and security alerts.

Welcome back, my amateur hackers! Over the course of the next year, we will be developing our own zero-day exploits. In my first article in this series, I introduced you to buffer overflows, which are the source of some of the most lethal exploits, particularly the "remote code execution," so we are focusing our exploit development here on a buffer overflow.

Welcome back, my hacker novitiates! A short while ago, I introduced you to regular expressions. Regular expressions are a language that is particularly useful for finding complex text patterns in streams of data.

A security analyst has discovered a flaw in Chromecast's initial setup process that allows would-be hackers to assume full control over the online streaming device.

Welcome back, my aspiring hackers and those who want to catch my aspiring hackers! As most of you know, this series on digital forensics is inspired by the motivation to keep all of you all out of custody. The more you know about the techniques used by law enforcement and forensic investigators, the better you can evade them.

Greetings. This how-to on hacking Windows 7/8/10 etc. admin account passwords using Windows Magnifier is focused on adding, changing, or deleting an admin level account on a Windows 7/8/10 etc.

Welcome back, my aspiring hackers! One of those areas of Linux that Windows users invariably struggle with is the concept of "mounting" devices and drives. In the Windows world, drives and devices are automatically "mounted" without any user effort or knowledge. Well, maybe a bit of knowledge. Most Windows users know to unmount their flash drive before removing it, but they usually think of it as "ejecting" it.
Looks like someone created a remote exploit using javascript. Pretty scary stuff o.o. Intel Core2Duo cpu cache controller bug PoC | Inj3ct0r - exploit database : vulnerability : 0day : shellcode.

Welcome to the sixth Community Byte for coding in Python and beating the challenges presented to us by HackThisSite. These sessions are created to bring our community together, to learn from each other, and essentially grow together. Everyone is welcome, from novice programmers to aspiring hackers.

Back when I was a Windows user, I know I'm not the only one who has experienced password loss—that moment where you just can't remember your password. Sometimes it happens to the best of us. So, how can we get into the system without paying a local geek or geeksquad to do it? First, we have to look into how Windows stores their passwords.

Blip TV user Mr. Root teaches you how to mount an ISO image file using the Unbent Linux terminal. To do this and have access to the files inside of an ISO, without unarchived it, start the terminal. Type in dirk CD. Make sure the ISO image is on your desktop. Then type in sud o mount -o loop -t iso9660 and then the name of your image file, followed by CD/. This will create a new disk drive, which can be seen on the desktop. You can explore that disc like a real one. To unmounted your image, s...

Here is the answer to the question that a lot of people have asked lately, "How does one install Linux Ubuntu on Windows without causing any modifications in the original boot record of the PC?" Software wiz-kid Matt Hartley walks the viewer through a step-by-step process of installing Ubuntu on a Windows-driven computer. The secret is to download Ubuntu to a CD instead of downloading and installing it directly on the hard drive of one's PC. This also ensures that the Ubuntu is easy to delete...

If you are interested in installing Ubuntu on your Samsung Galaxy Tab 10.1 Android tablet. You can download Ubuntu and ADB here. Root Ubuntu Linux on top of your Android OS with Ubuntu running like a virtual machine.

Need to print something but you're on the go and only have your smartphone or iPad with you? No worries! This tutorial shows you how to use a little app called Dropbox to print to your home printer anywhere, anytime, with any mobile device. Print THAT!

Learn a quick fix that'll patch up your slow Internet connection on Ubuntu Linux 7.10

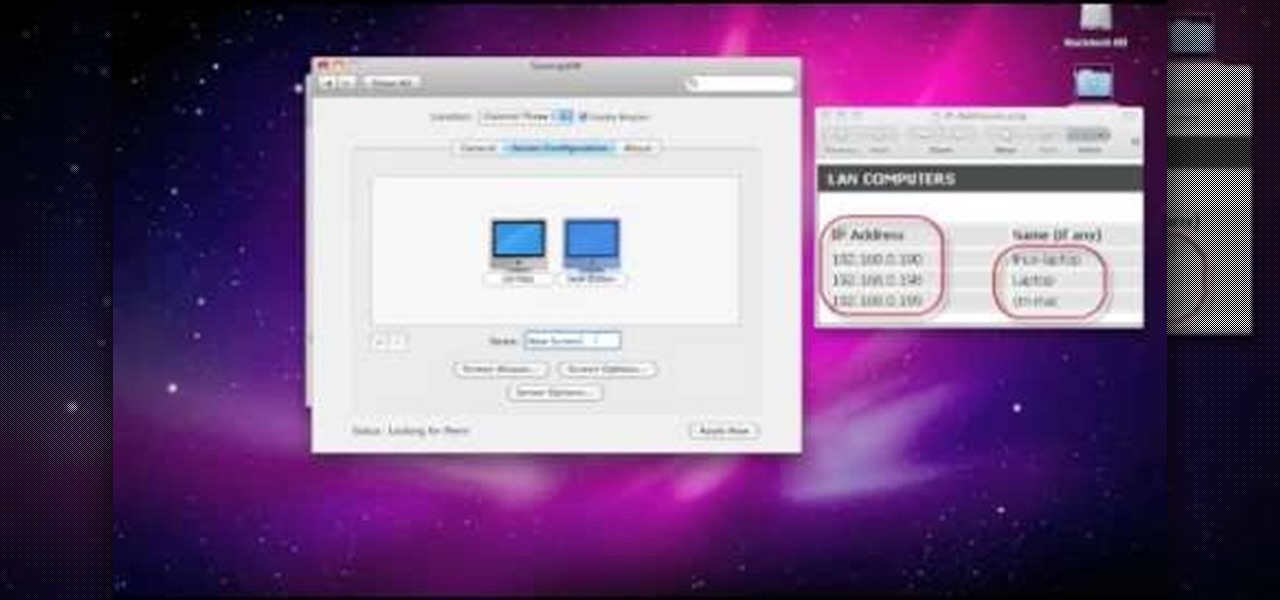
Two computers, two displays...one keyboard and mouse. Molly Wood from CNET shows you how a free software app (Synergy) can make beautiful music between PCs, Macs, and even Linux.

While SSH is a powerful tool for controlling a computer remotely, not all applications can be run over the command line. Some apps (like Firefox) and hacking tools (like Airgeddon) require opening multiple X windows to function, which can be accomplished by taking advantage of built-in graphical X forwarding for SSH.

It's easy to run Kali Linux from a live USB on nearly any available computer, but many publicly accessible laptops and desktops will be locked down to prevent such use. School, work, or library PCs can be secured with a BIOS password, which is often an easily recovered default password. Once you have access, though, you can use a USB flash drive to run Kali live on any PC you find.

Connecting to your headless Raspberry Pi on the go typically requires a network connection or carrying around bulky peripheral hardware like a screen and keyboard. With the help of an old-school connecting standard, though, you can log into your Pi from any computer using a simple cable. If you don't have a power source, you can also power your Linux distro over the cable at the same time.

Some of us woke up at the KRACK of dawn to begin reading about the latest serious vulnerability that impacts the vast majority of users on Wi-Fi. If you weren't one of those early readers, I'm talking about the Key Reinstallation Attack, which affects nearly all Wi-Fi devices.

This guide is written for anyone who is practicing his penetration skills using the Metasploitable 2. The problem that we are facing here is that we have to penetrate to Metasploitable 2 and when this happens we understand that we are not logged in as root but as a user with less privileges!

Video: . Hi, this is a quick demo about how to backdoor executables (software) sent over HTTP using MITMF, backdoor factory

Welcome back, my amateur hackers! Many of you here are new to hacking. If so, I strongly recommend that each of you set up a "laboratory" to practice your hacks. Just like any discipline, you need to practice, practice, and practice some more before you take it out to the real world.

Welcome back, my hacker apprentices! Several of you have written asking me how you can check on whether your boyfriend, girlfriend, or spouse is cheating on you, so I dedicate this tutorial to all of you with doubts about the fidelity of your spouse, girlfriend, or boyfriend.

We're officially seeking Null Byters on a weekly basis who are willing to take the time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (IF up to par, of course). There is no need to be intimidated if you fear you lack the writing skills. I will edit your drafts if necessary and get them looking top-notch! You can write tutorials of any skill level, about anything you feel like sharing that is ...

Something that can shy a user away from making the switch to Linux is not having the option to go back to Windows. Luckily, there are solutions like dual-booting, where you can have both OS's installed right next to each other. However, Windows 8 appears as if it will block dual-boots with its neo-space BIOS that have been developed. Sneaky-sneaky. Windows users could still throw in a Linux live CD to try out Linux, but what does a Linux user do when they need something from Windows?

From the Fallout 3 SuperGuide on MyCheats. MyCheats staff writer Mike Nelson talks about his favorite exploits and tricks in Fallout 3.

In this installment from the Unorthodox Hacking series of computer security videos, you will explore a few of the areas in Windows that most Sysadmins don’t even know exist. See how to become Local System through the Task Scheduler and abuse long filenames. Take a look at some of the features within Windows—registry—that many system administrators don't know exist with this hacking how-to.

Few Bluetooth users realize that Bluetooth headsets can be hacked or otherwise exploited to a remote attacker the ability to record and inject audio through the headset while the device is not in an active call. SANS Institute author and senior instructor Joshua Wright demonstrates, and explains, the security vulnerability in this how-to. For more information, including step-by-step instructions on how you can replicate this hack yourself, take a look.

Of course, you'll want other people to be able to interact with your program. Linux sets up a command shell automatically, but if you're programming with Python on a Windws machine, you'll need to do it manually - and this video shows you how.

Python can be used for games, websites and operating system GUIs; and you can work with it on PCs, Macs or Linux machines. This tutorial shows you how to install the compiler and get started teaching yourself how to program in Python.

In this video tutorial, we learn how to use the greenpois0n jailbreak tool to jailbreak an Apple mobile device running iOS 4.1 from a Microsoft Windows (or GNU/Linux) PC. For detailed, step-by-step instructions, and to get started jailbreaking your own iOS 4.1 iPhone, iPod Touch or iPad, watch this hacker's how-to.

In this tutorial, you'll learn how to share a single keyboard and mouse across multiple Windows, Mac or Linux computers with an application called Synergy. It's an easy process and this video presents a complete guide. For more information, including a full demonstration and detailed, step-by-step instructions, watch this helpful home-computing how-to.

In this clip, you'll learn how to set up and use Synergy to control multiple Windows, Mac or Linux computers from a single keyboard and mouse. For more information, including a complete demonstration, and detailed, step-by-step instructions, as well as to get started using this trick yourself, take a look.