Want to test the security of your WEP WiFi wireless network? In this clip, you'll learn how to use the Backtrack Linux distro and the Aircrack-ng WiFi security app to crack a WEP key. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

By partitioning the hard drive on your Mac computer, you can install multiple versions of Mac OS or install Windows or Linux on the other other partition, increasing your computer's compatibility. This video will show you how to create a new partition quickly and easily on any Mac.

In this clip, you'll learn how to use the Backtrack 3 Linux distro and Aircrack-ng WiFi security app to crack the password to a WEP-protected wireless network. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.
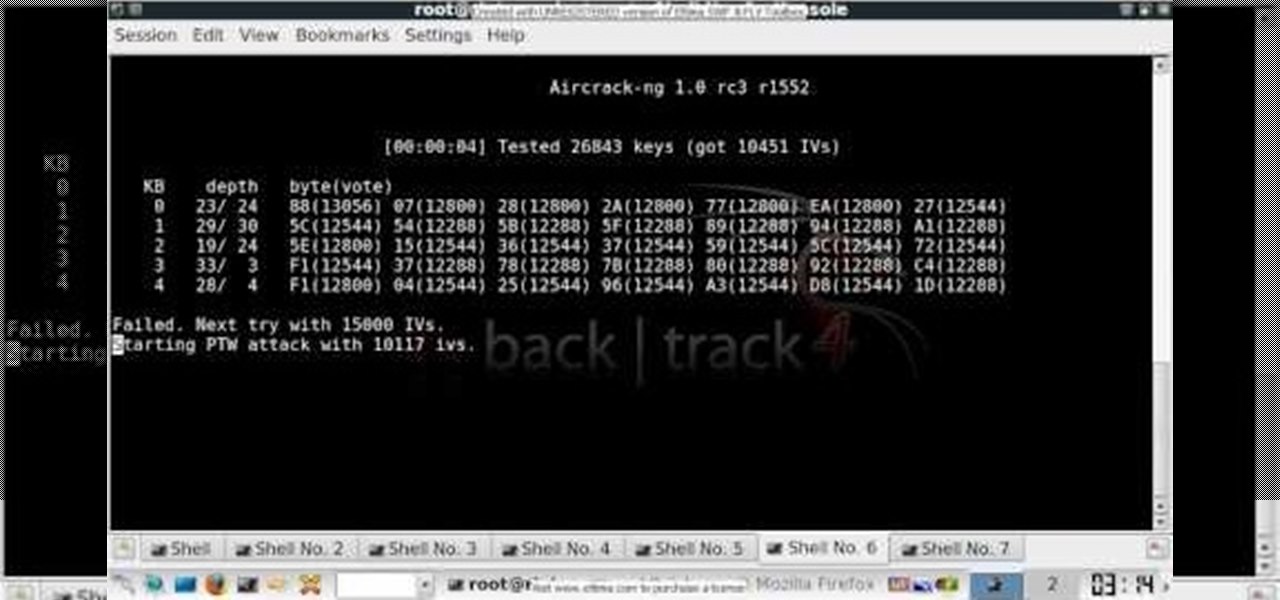
In this clip, you'll learn how to use the Backtrack Linux distro and the Aircrack-ng WiFi security app to crack a WEP key. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

If you have Ubuntu Linux installed, and the GNOME desktop manager, this video will help you navigate the features and functions. Wlakthrough the workspace and see what you can do! If you're a Windows or Mac user thinking about installing Ubuntu, watch these video tutorials and walkthroughs about Ubuntu and compare for yourself before you make the plunge.

Watch this informative video tutorial on how to create shaped photo collages with Shape Collage. Shape Collage is an automatic photo collage maker that creates collages in different shapes in just a couple seconds. You can create picture collages in the shape of a rectangle, heart, text, or logo, with just a few clicks of the mouse.

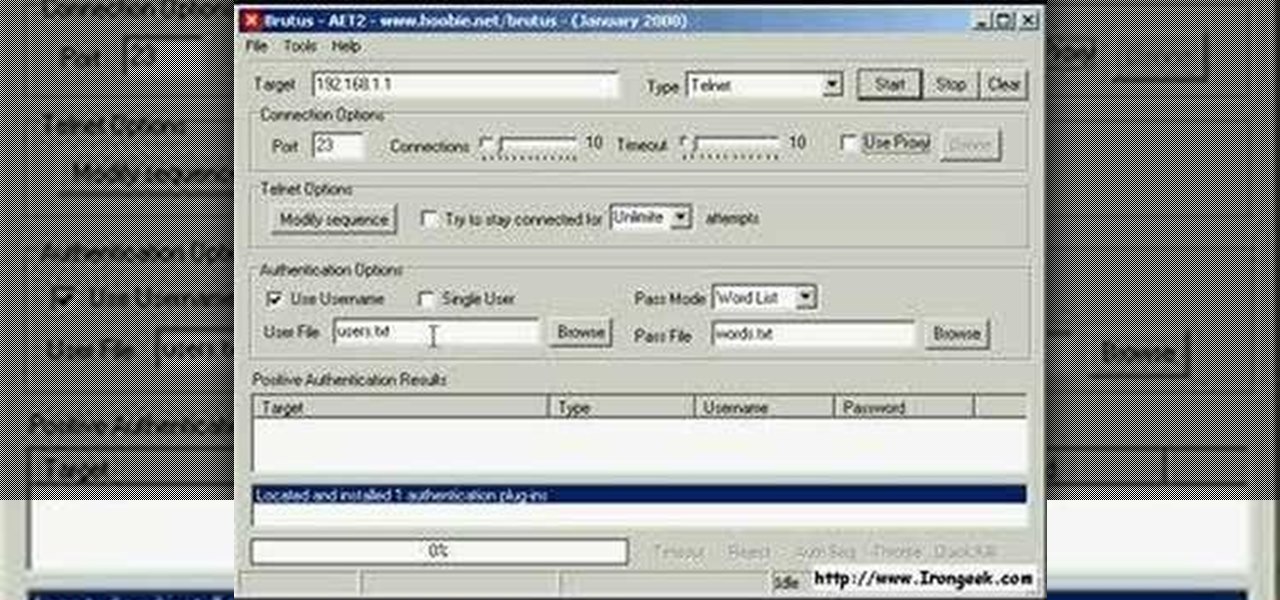
Brutus, first made available in 1998, is one of the fastest, most flexible remote brute-force password crackers you can get your hands on - it's also free. It is available for Windows 9x, NT and 2000. In this video tutorial, you'll learn how to use Brutus to crack a Linux box a running telnet daemon. For more information, and to get started hacking with Brutus yourself, watch this video tutorial.

This video demonstrates how to install Webmin via SSH. Once you've downloaded the Webmin interface package, you'll want to install it onto your serve. In order to do that, you'll need to depackage it. If you're new to Linux or otherwise unclear about how to proceed, then watch this video for step-by-step instructions.

In this instructional video, learn how to transfer files from your Windows PC to your iPhone or iPod Touch using DataCase. Datacase basically converts your iPhone or iPod Touch into a wireless drive that you can access your information on the Mac, PC, or Linux.

A brief overview of the removal of Windows, and the downloading and Installation of Fedora. The end is a montage of screen shots taken during the install.

A how-to on how to share files and folders from Ubuntu to Windows XP and XP to Ubuntu.

Want to create an instrumental or a cappella from a song? Learn how to remove vocals or instruments from MP3s using a freeware program called Audacity for Windows, Mac, and Linux.

Hello again my fellow hackers. I've come to give you some hope for hacking. As we know there are a lot of exploits out in the world and there are websites you can find them on.

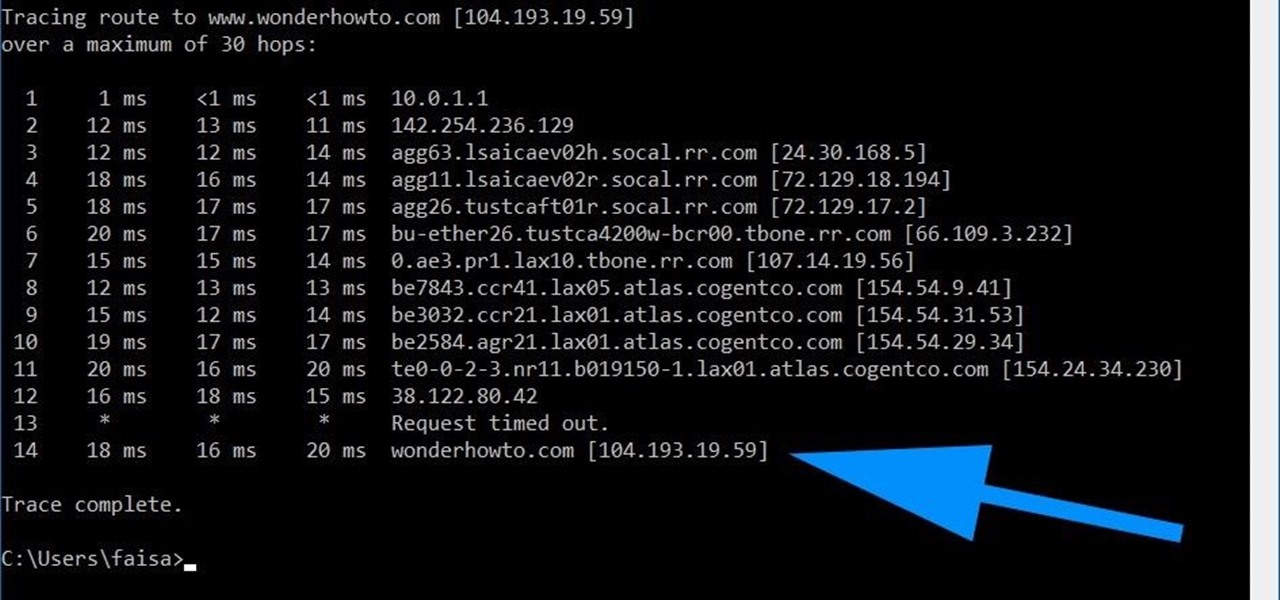
Using a simple trace trick, you can easily look up the IP address and its location for any website. This method uses a command line command to first find the IP address of a given website, and then uses a free online tool to get that IP's location.

Linux is a diverse and powerful operating system that virtually every IT professional must learn and know well. Whether you realize it or not, you have likely already used a Linux device, and learning to design things for it is a key step in any Data Science career path.

The Raspberry Pi is a credit card-sized computer that can crack Wi-Fi, clone key cards, break into laptops, and even clone an existing Wi-Fi network to trick users into connecting to the Pi instead. It can jam Wi-Fi for blocks, track cell phones, listen in on police scanners, broadcast an FM radio signal, and apparently even fly a goddamn missile into a helicopter.

Hello my anxious hackers, the week has started and here we begin a new series that I think will help many here and not only, for those that have the opportunity to follow our tutorials but they are not yet part of the community.

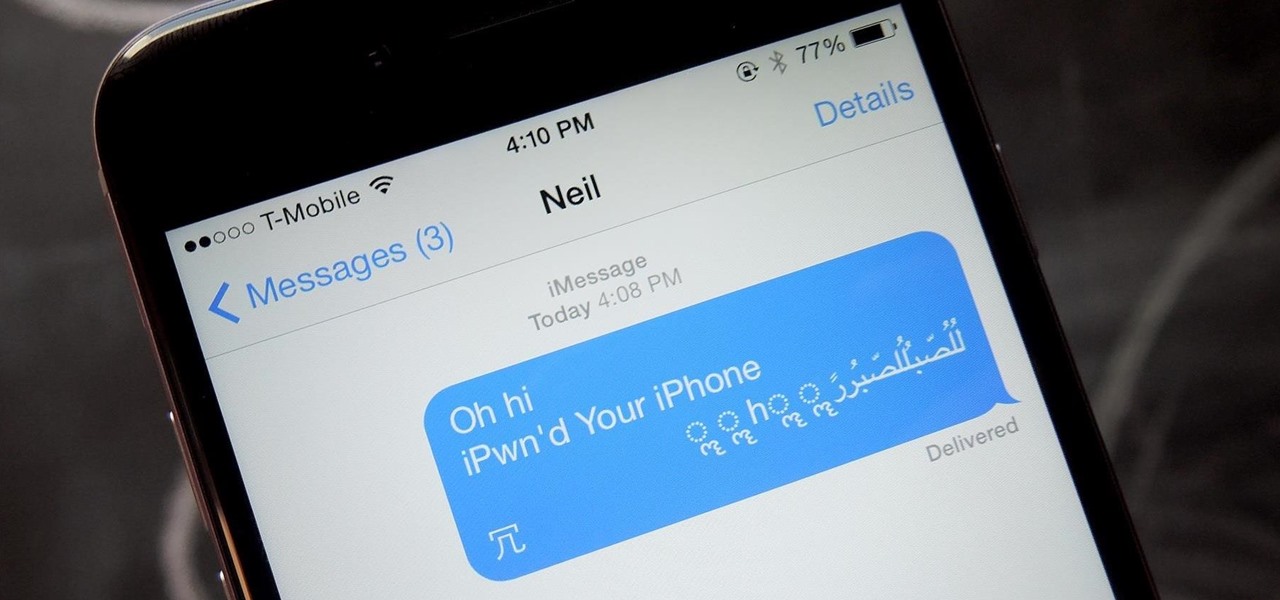
Thanks to a newly discovered iOS exploit, a text message can now ruin your day. It will literally cripple your iPhone, and the worst thing is that anyone with a phone that supports double-byte unicode can do it to you. While it initially sounded like bullshit, we tried it out several times here, and to our surprise, it worked perfectly each time.

Welcome back, my aspiring hackers! Many of you have installed Kali Linux as a virtual machine (VM) using VMware or VirtualBox, while others have installed Kali (or BackTrack) in a dual-boot system. The drawback to installing these hacking systems as a VM is that it then requires an external wireless adapter (your wireless adapter is piped through the VM as a wired device, eth0), but it makes for a great place to test your hacks while honing your skills.

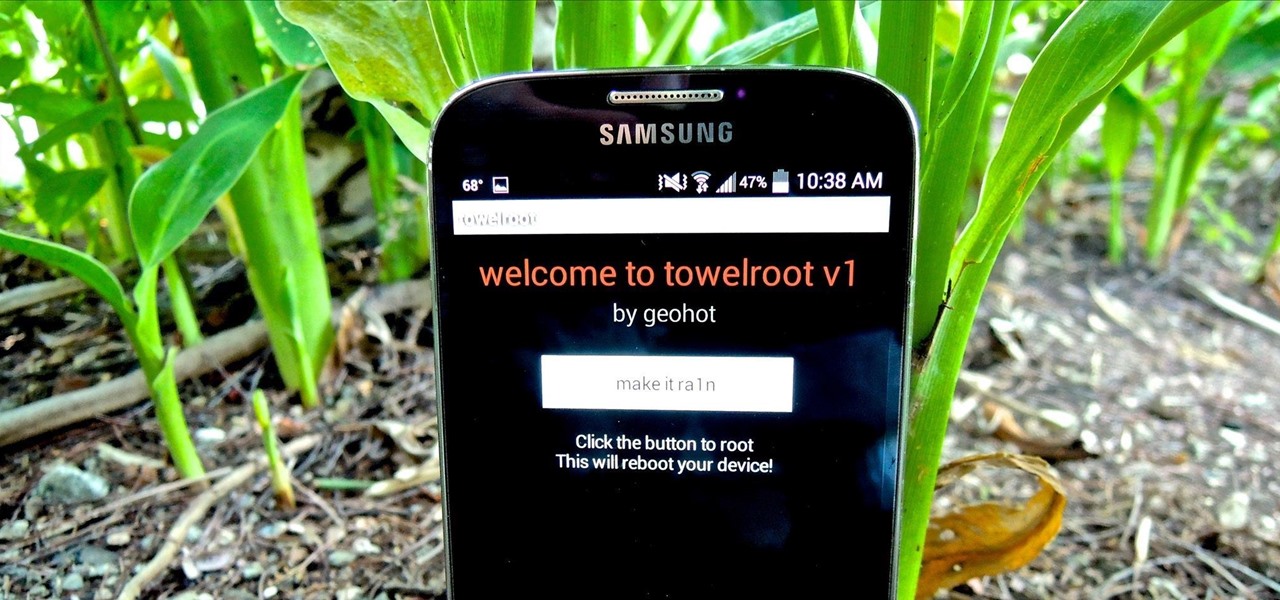
Something pretty awesome happened over the last couple of days. George Hotz, better known as Geohot, the infamous hacker known for jailbreaking iOS and exploiting the Sony Playstation 3, has brought joy to owners of just about all Android smartphones and tablets, especially those on AT&T and Verizon.

If you've haven't had your fill of Apple's security issues in recent weeks, Siri is now the latest to join the slew of problems with the most recent version of iOS (7.1.1).

Welcome back, my budding hackers! In my continuing effort to build your basic Linux skills for hacking, I want to show you how to build a secure "tunnel" to MySQL.

For a photo- and video-sharing app based around privacy, Snapchat sure has a lot of security holes floating around. At one time, you were able to take screenshots of Snapchats in iOS 7 without the sender knowing, which is something that you can still do on rooted Android devices.

Welcome back, my tenderfoot hackers! This is the third installment of my series on basic Linux skills that every hacker should know. Although some hacking tools are available for Windows and Mac, every real hacker uses Linux—for good reason.

Even though iOS 6.1 was only released a couple of weeks ago, hackers released evasi0n a couple days after. Evasi0n, the only iPhone 5 jailbreak currently on the market, is the most popular jailbreak in history—with nearly 7 million iOS devices already hacked in the mere four days after its release. Well, now it seems that iOS 6.1 is being taken advantage of again, this time with a simple exploit figured out by YouTube user S1riOS6, which lets you bypass the lock screen on an iPhone running iO...

I spent hours writing a guide on how to record a screencast, or record what is on the desktop, and convert it. I then found out that this is much simpler & faster and doesn't even involve opening the commandline.

hey everyone i wish that u can help me so ! i was trying this exploit

When it comes to coffee, some people just like perfection. Most would agree that the best cup of coffee comes from home, after roasting your own green coffee beans. But not everybody has the time or money to have complete control over their coffee's flavor. Roasting via stovetop or oven produces mélange (not quite perfection), and home roasters can be pricey.

"How do I install Arch Linux?" That question was bound to come up eventually. And with me using Arch, it's no coincidence that all of you want to use it as well. Arch is arguably the best Linux distro available. Distros that come close are Gentoo and some aspects of Ubuntu, but Arch is meant for building your OS from the inside out. Arch is built around minimalism, so you won't get anything by default. It doesn't even come with sound!

Here's a fun hack! In this clip, we learn of a bug that will permit you to circumvent the passcode lock screen on any iOS 4.1 iPhone 4. For detailed, step-by-step instructions, and to get started using this exploit yourself, watch this video guide.

Before attacking any website, a hacker or penetration tester will first compile a list of target surfaces. After they've used some good recon and found the right places to point their scope at, they'll use a web server scanning tool such as Nikto for hunting down vulnerabilities that could be potential attack vectors.

One of the things that sets a seasoned hacker apart from the script kiddies is the ability to effectively sneak past antivirus defenses when executing an attack. One way to do this is to use custom shellcode in an exploit. Not everyone is an expert at writing shellcode, but luckily there's an easy way to do this that is both quick and effective.

After a long hiatus, we shall once again emerge from the shadowy depths of the internet to build an exploit. This time, we'll be looking at how to defeat a non-executable stack by using the ret2libc technique — a lean, mean, and brilliant way of exploiting a stack overflow vulnerability.

Hi guys. Hope you all had a good Christmas , today i have a tutorial for you.

Hello fellows nullbyters, first of i will start saying that im addicted to this community, i feel the challenge growing up so fast, all the newbies, amateurs,advanced and professionals hackers around trying their best to help the community, badly but we got some script-kids too but anyway, today we are going to learn how to install and use clanAV in kali linux.. INTRODUCTION

Welcome back, my hacker apprentices! In recent weeks, the revelation that the NSA has been spying on all of us has many people up in arms. I guess I take it all in stride as I just assume that the NSA is spying on all of us—all of the time. Don't get me wrong, I don't condone it, but I know the NSA.

I use Google Chrome every day for my browsing needs, and I had no idea they were hiding something from me. So, I was pretty surprised to see that Chrome has an entire hidden experimental add-ons section. There are add-ons that work for Mac, Windows, Linux, and Chrome OS, so there's something for everybody.

Regardless of whether you're an aspiring or established coding pro, knowing just one or two programming languages and platforms is no longer sufficient if you want to be truly competitive in an increasingly popular and lucrative field. But before you spend an excessive amount of time mastering six new platforms, do yourself a favor and master Linux.

A lot of time can be wasted performing trivial tasks over and over again, and it's especially true when it comes to hacking and penetration testing. Trying different shells to own a target, and testing out privilege escalation commands afterward, can eat up a lot of time. Fortunately, there is a tool called One-Lin3r that can quickly generate shells, privesc commands, and more.