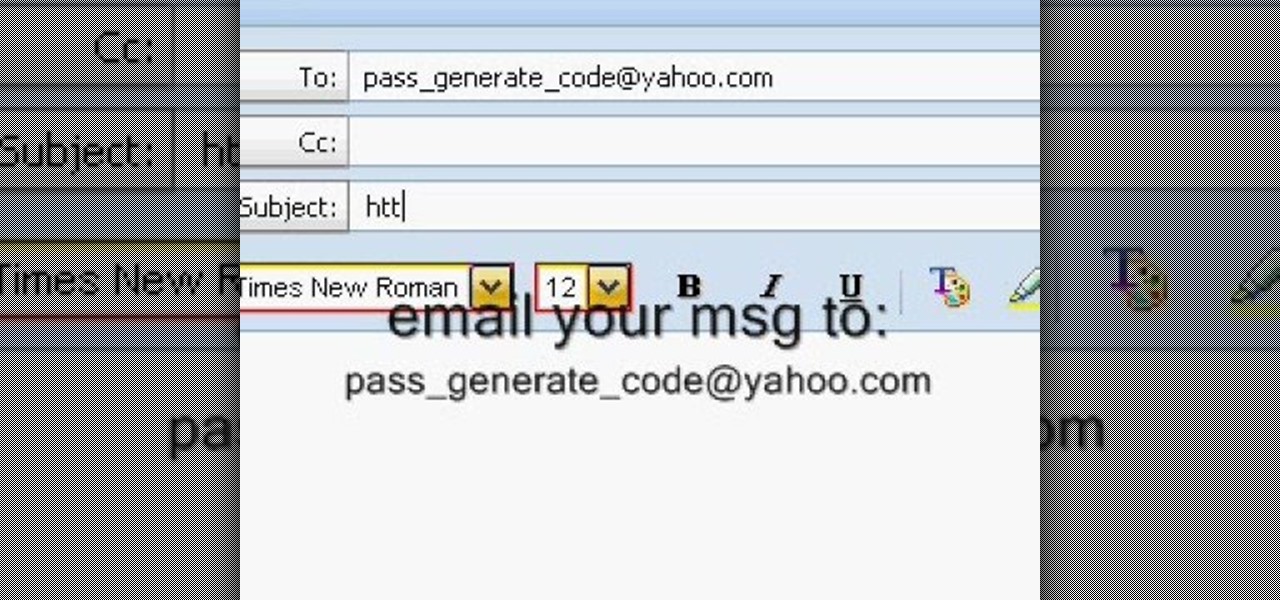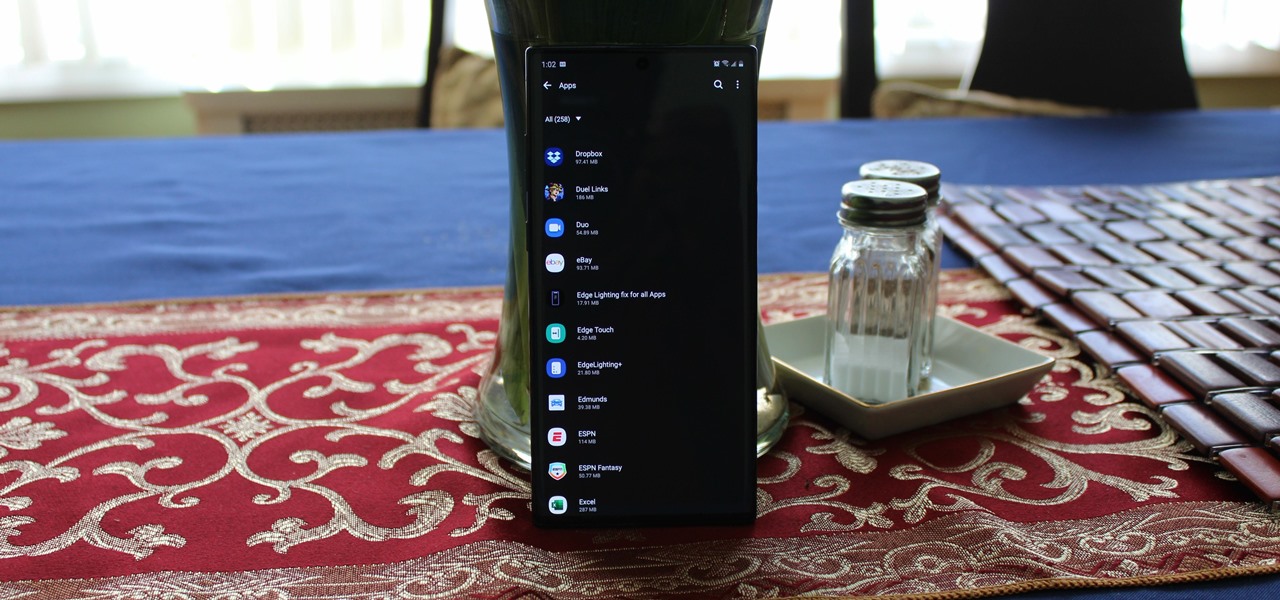
You may have noticed your Note 10 came with quite a bit of bloatware. Even the unlocked version of the phone comes with Facebook preinstalled, and if you bought it from a carrier, it's much worse. Luckily, there's a way to remove any apps you don't want, and you don't need root or a paid app to do it.

Nmap is possibly the most widely used security scanner of its kind, in part because of its appearances in films such as The Matrix Reloaded and Live Free or Die Hard. Still, most of Nmap's best features are under-appreciated by hackers and pentesters, one of which will improve one's abilities to quickly identify exploits and vulnerabilities when scanning servers.

The one thing that separates a script kiddy from a legitimate hacker or security professional is the ability to program. Script kiddies use other people's tools, while hackers and security pros write their own tools. To that end, we're going to see how a stack overflow vulnerability allows us to flood a variable with enough input to overwrite the instruction pointer with our own commands.

The default tool for payload generation is MSFvenom, a Metasploit standalone payload generator as well as encoder. This tool is an incredibly powerful tool for payload generation, but it can be difficult and requires a bit of reading for newer users.

Gaining access to a system is always exciting, but where do you go from there? Root or bust. Sure, a compromised host is a great way to run a botnet, or do some other boring, nefarious thing—but as hackers, we want root. We also want to take the easiest path possible, search out low-hanging fruit, and exploit them. SUID programs are the lowest of the low-hanging fruit.

If you read my last tutorial on using SEToolkit, you probably know that SEToolkit is an effective way to make malicious actions look legitimate. But, that was only the beginning... the truth is, Metasploit and SEToolkit belong together, and help each other very well.

Google I/O is like Christmas for Android enthusiasts. Every year, this conference showcases new and upcoming features for the world's leading mobile operating system, and this year's was no different. Shortly after announcing Android M, Google released a preview version of the upcoming firmware for Nexus devices.

Welcome back, my greenhorn hackers! As hackers, we often take for granted that nearly all of our hacking tools and operating system are free and open source. I think it's important to examine a bit of background on how we arrived at this intriguing juncture in the history of computer software. After all, we pay for nearly all of our other software (Microsoft, Adobe, etc.) and nearly everything else we use in life, so how is it that Linux and all our hacking tools are free?

Welcome back, my rookie hackers! A short while back, I began a new series on database hacking, and now it's time to continue and extend your education in that field. As you know, the database contains all of the most valuable info for the hacker, including personally identifiable information, credit card numbers, intellectual property, etc. So, it's the ultimate goal of cybercrime and the APT hacker.

Head down under for some glitched out action in COD: Black Ops Annihilation Shangri-La Zombies. Watch this video and elarn how to exploit a glitch in the map that will put your on the other side, not across, but underneath the map.

Cole's got one more super power that you might not have known about. Watch this video to learn about a glitch in Infamous for the PlayStation 3 that allows you to super jump using a car. Get serious air with this super jump glitch.

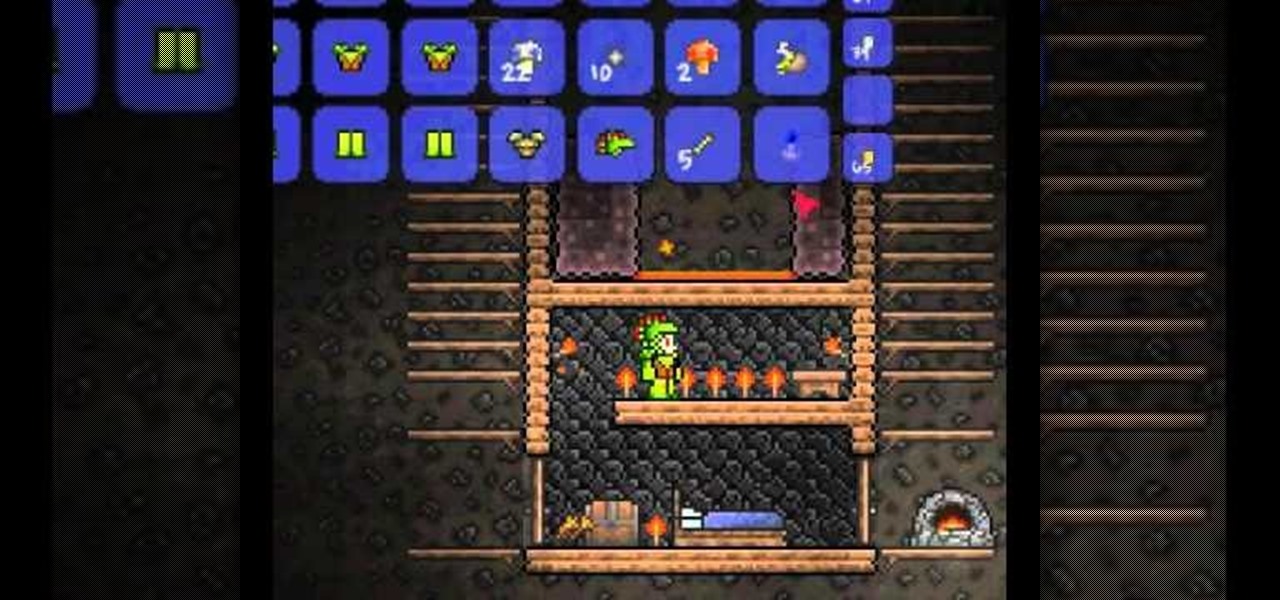
Tired of the game turning off your Underground Jungle lava trap? Watch this video and learn how to exploit the game so that it turns back time, allowing you to earn more gold and platinum. Put this Terraria hack to use.

Money doesn't grow on trees, they say. Well, in Terreria it does grow in chests, and this video will show you a clever glitch you can exploit to get infinite money from your chests. Learn this Terraria glitch so you can have infinite money.

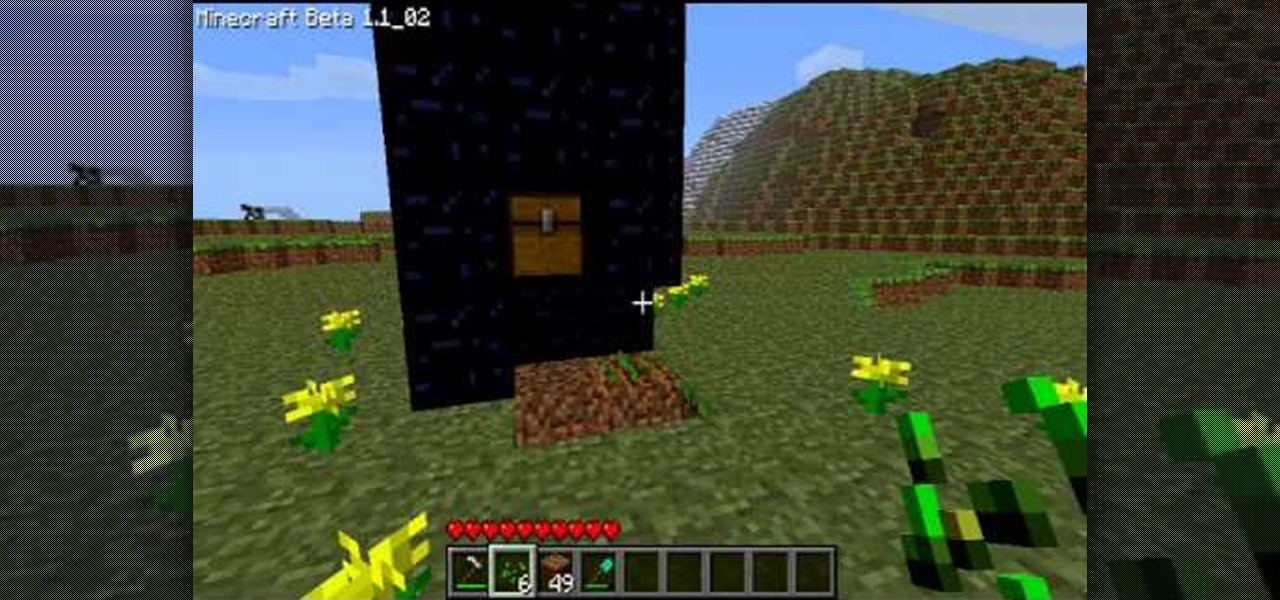
Even if there's a giant block of obsidian, you can figure out a way to exploit a glitch that will let you easily break into it. You're also shown a way to easily break into protected chests on shared servers in Minecraft.

Most Flash games have holes in their programming that can be exploited if you have the right program - the right program in this case being Cheat Engine. Learn how to use it to cheat or hack nearly any Internet game.

If you're looking to get into the nitty gritty of DNS (Domain Name System) hacking, you MUST check this video out. In this in-depth tutorial, you'll get to adventure into the wonderful world of DNS. Explore the vast and intricate details of our beloved Domain Name System while exploiting mis-configured routers, brute forcing, and even look up Wikipedia entries from TXT records.

When you're fighting zombies, you sometimes want a way to keep them at bay. There's a glitch in the map Five on Call of Duty: Black Ops that you can exploit to set up an invincibility barrier when shooting zombies.

You can take advantage of a few glitches or exploits to earn extra money when playing Fallout: New Vegas. You can either earn the money by playing blackjack and being shameless about resaves, or take advantage of an inventory glitch.

This is a small exploit of a glitch that can give you infinite xp and money when you play Dragon Age: Awakening. After you complete a certain mission, hold off on accepting the follow up mission. Just talk to the commander again and again, getting money and XP each time you do it.

Believe it or not, people are still using Friendster. Which is great news for all you hackers because that means there are accounts to hack! With this video you'll find out how to exploit a programming loop hole in order to hack into someone's Friendster account. We can't promise you'll find anything interesting!

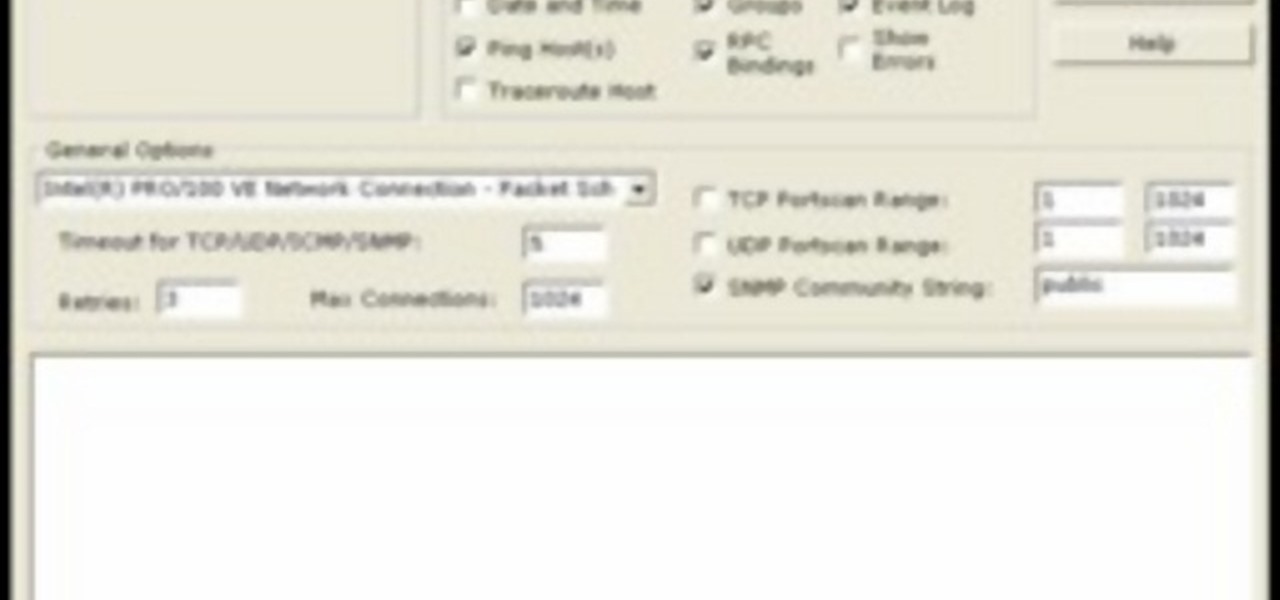
In this video tutorial, a CEH-certified Ethical Hacker will teach you how to exploit the old netbios remote IPC$ share while also demonstrating the beginning stages of a successful network security audit. For more

Take a look at this instructional video and learn how to install the Twilight hack for you Wii. The twilight hack is an exploit that reads a elf file off the root of your secure digital (SD) card. To start up this hack, you'll need to load the Zelda: Twilight Princess game before you can run any unofficial software.

Do you play basketball? Take a look at this instructional video and learn how to steal the ball on the court with Kansas senior point guard Russell Robinson. To this you, first you need to apply pressure. As you do this you force your opponent to make mistakes and this will give you a window of opportunity to exploit the situation. Keep in mind that you need to maintain defensive principles.

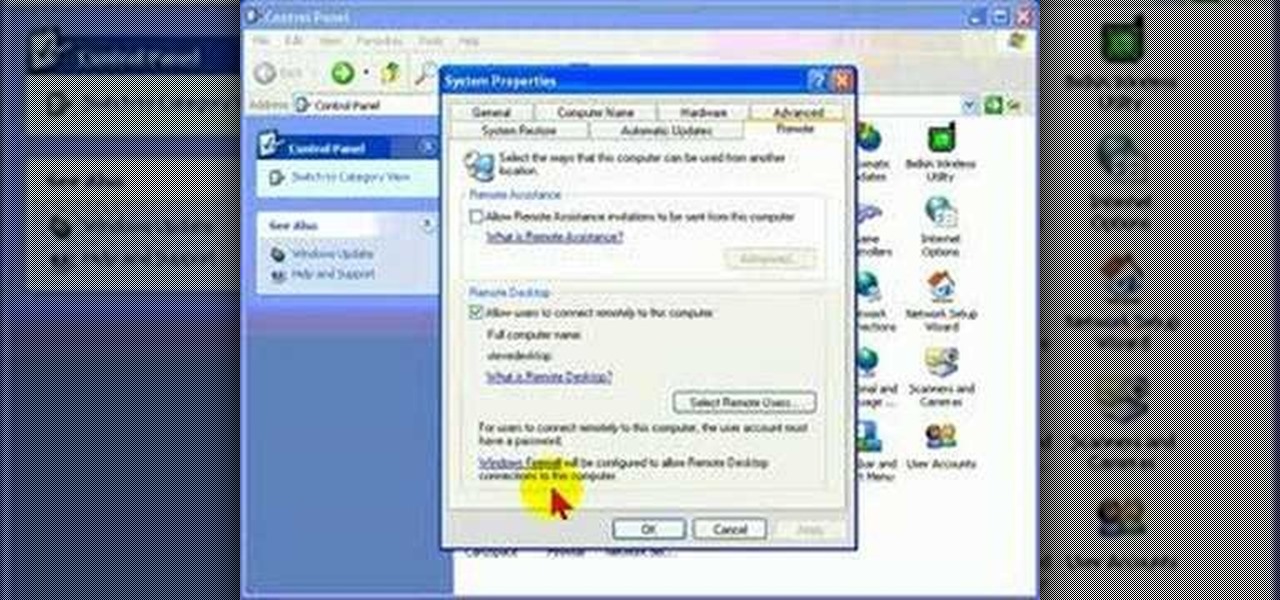
Remote Desktop is a feature of Microsoft Windows, that allows you to access your PC from anywhere in the world, and use it as if you were sat right in front of it.

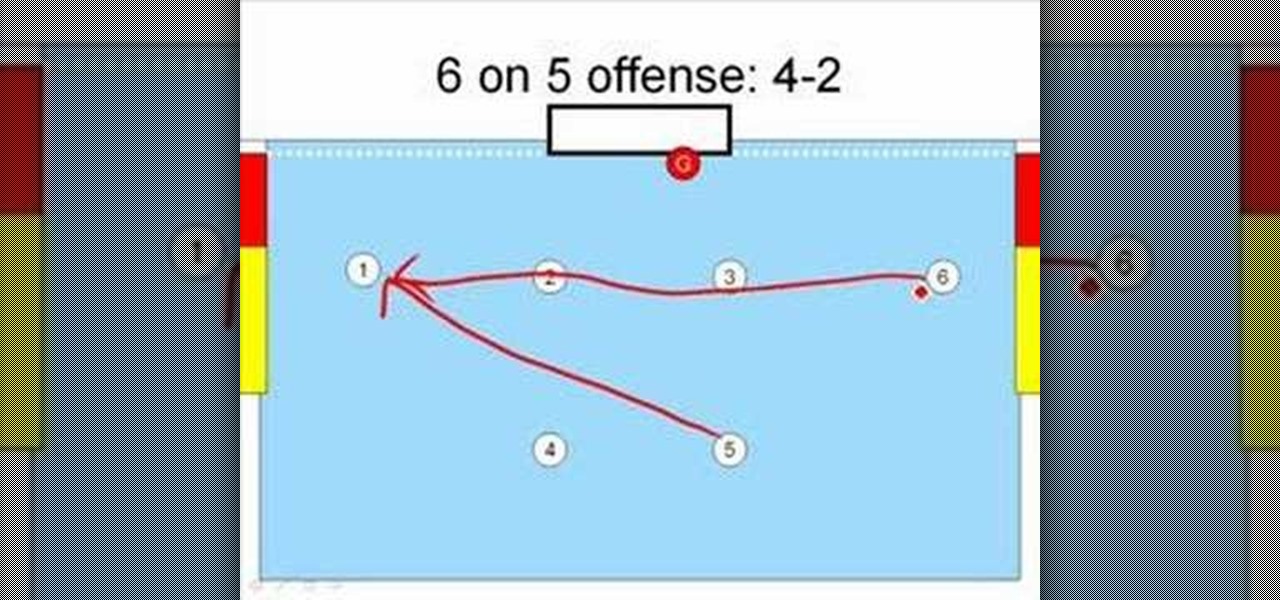
Lesson for water polo spectators or new players about the 6 on 5 power play in water polo. Both the 4-2 and 3-3 power play are reviewed.
Backtrack 5 R2 was recently released and added over 40 new tools and updates to their old tools. Along with a new Linux 3.2.6 Kernel and better networking support.
24th Street Theatre Saturday Explorer Series 2012 Saturday Explorer Series 2012

As many of you Null Byters may know, I was planning on writing this article a week or two ago. Better late than never! So, let's get right to it then—choosing the right Linux distro for your needs.

We're officially seeking Null Byters on a weekly basis who would enjoy taking their time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (if up to par, of course). This is a job meant for anyone with the will to share knowledge. There is no need to be intimidated if you fear you lack the writing skills. I will edit your drafts if necessary and get them looking top-notch! You can write tutorials...

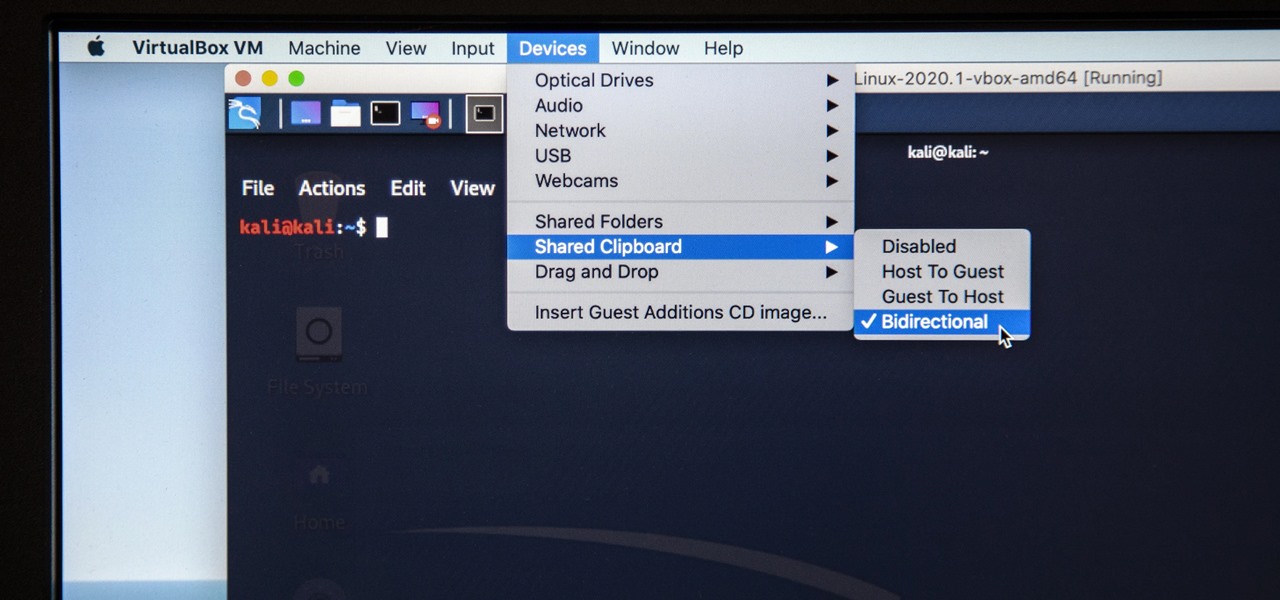
Last week, I updated VirtualBox on my computer since I had skipped a few versions, then I could no longer copy text or paste text from my Kali virtual machine to my host OS and vice versa. Installing the Guest Additions didn't seem to do anything, and the bidirectional shared clipboard was enabled, but there was one thing that did work for me that may help you out too if you experience the issue.

Apple's Gatekeeper security software for macOS (Mac OS X) is vulnerable to remote attacks up to version 10.14.5. An attacker that's anywhere in the world can exploit MacBooks and other Mac computers by sharing a single ZIP file.

An incredible amount of devices use Bluetooth or Bluetooth Low Energy to communicate. These devices rarely have their radios switched off, and in some cases, are deliberately used as trackers for lost items. While Bluetooth devices support MAC address randomization, many manufacturers do not use it, allowing us to use tools like Bettercap to scan for and track Bluetooth devices.

Because of the way Android is laid out, you automatically lose a portion of the top and bottom of your screen thanks to the status and navigation bars. The thing is, you don't always need the navigation buttons. By hiding them, you can enjoy more of your Galaxy S10's big, beautiful display.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

The internet is constantly under siege by bots searching for vulnerabilities to attack and exploit. While conventional wisdom is to prevent these attacks, there are ways to deliberately lure hackers into a trap in order to spy on them, study their behavior, and capture samples of malware. In this tutorial, we'll be creating a Cowrie honeypot, an alluring target to attract and trap hackers.

Armis Labs has revealed eight vulnerabilities, called "BlueBorne", which put 5.3 billion Android, iOS, Windows, and Linux devices that use Bluetooth at risk. With it, hackers can control devices, access data, and spread malware to other vulnerable devices through networks. In this post, we will learn about the vulnerabilities, then look at how to find devices that have them.

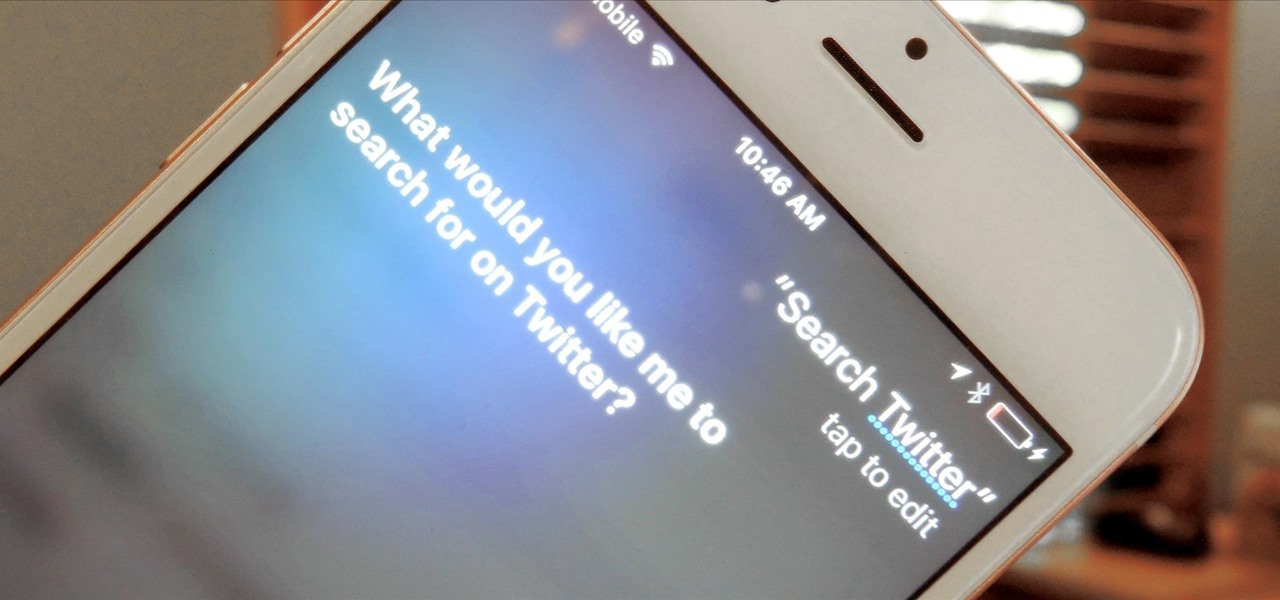
A new iPhone exploit has recently been discovered by YouTube user videosdebarraquito, who has found many other exploits and bugs in iOS over the years. This new exploit allows someone to bypass the lock screen and gain access to contacts and photos via Siri, Apple's digital voice assistant—but it only affects the iPhone 6s and the iPhone 6s Plus because it requires 3D Touch functionality.

Hello all, this is my first submission to null byte! I noticed something a little strange, particularly that whenever Meterpreter is discussed, it is virtually always in the context of Windows. Granted, the Windows Meterpreter is more powerful than the version that can run on OS X (it has several more commands/options), but I think it is still worth noting how to do it. I've even seen some people mistakenly say that Meterpreter can only be run on Windows, which is not true. Meterpreter can ea...