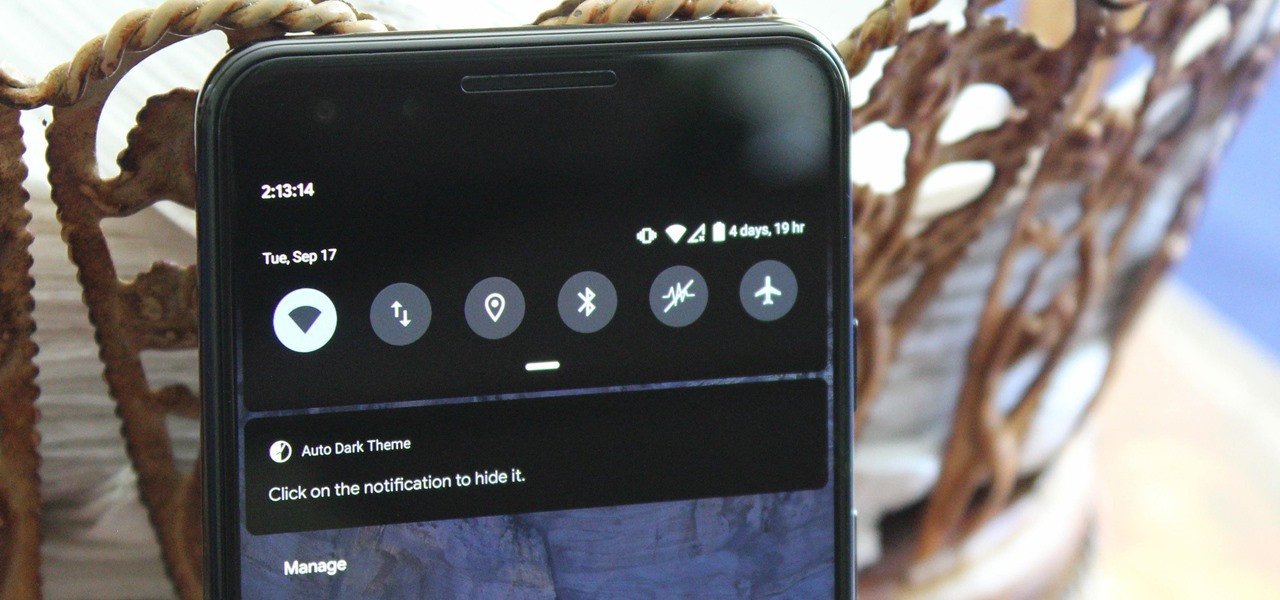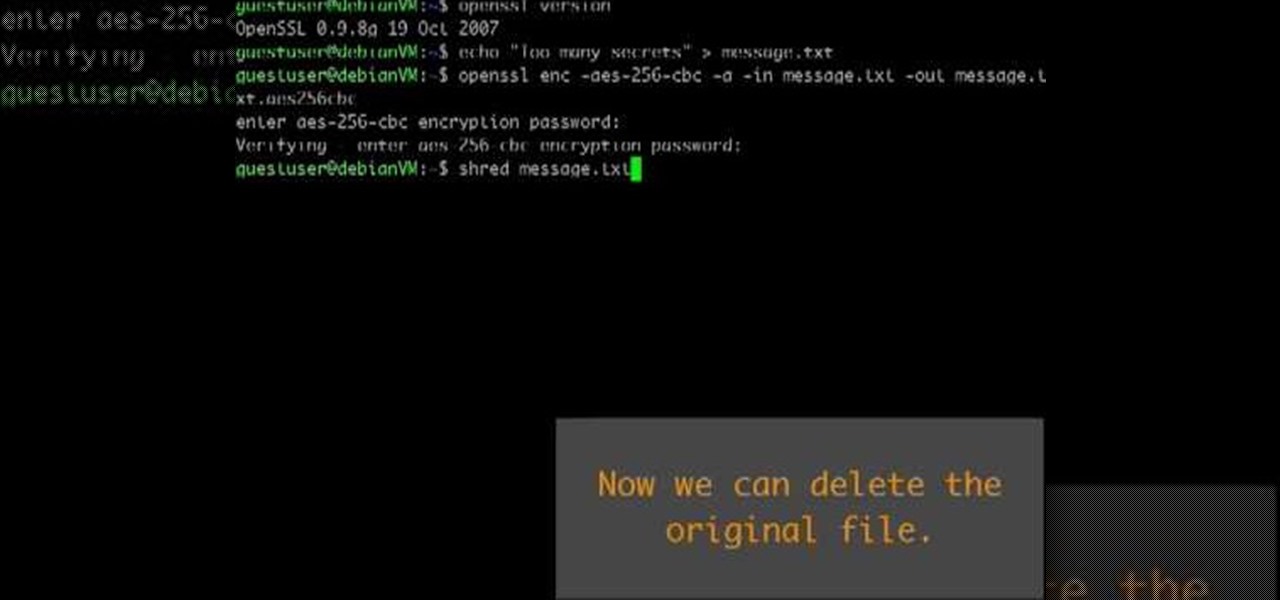
This video shows how to encrypt files with OpenSSL in Debian Linux. First we check if open SSL is installed on the system. If not, install it using packet manager. Next create the file going to be encrypted. Now encrypt the file. In this case AES algorithm in ypher block chaining mode is used. AES is US-government standard and can be considered secure. Now we are prompted for a password. In order for the encryption to be secure, we need to choose a strong password. Now we can delete the origi...
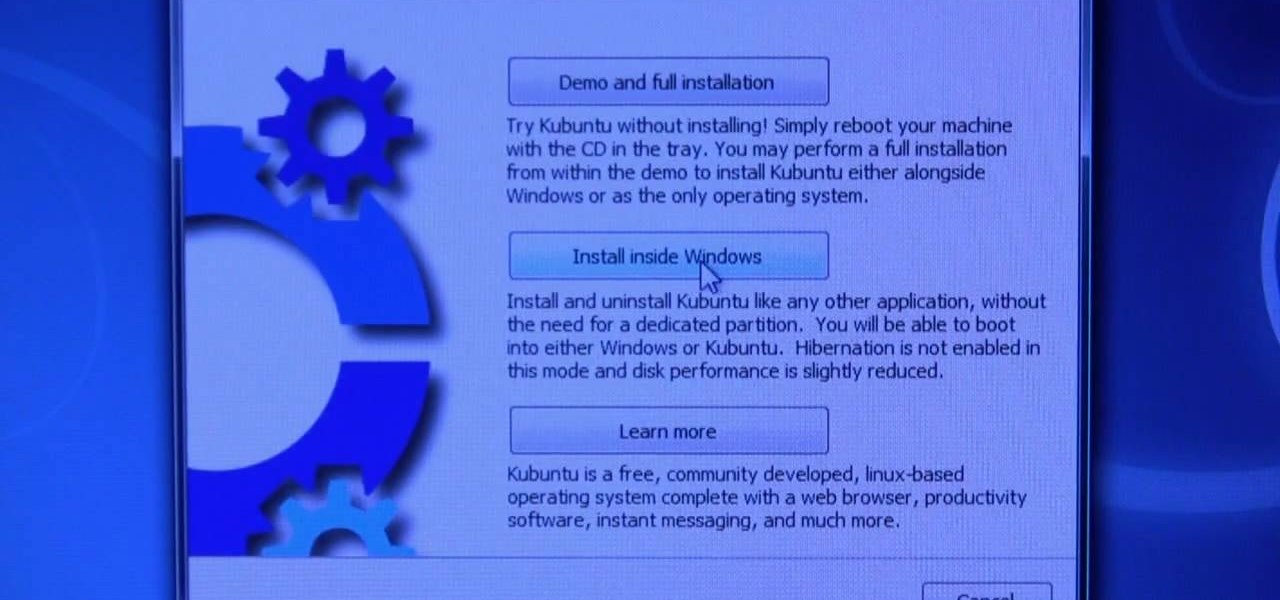
This video describes basics about using Wubi installer for Ubuntu in Windows operating system.Wubi installer is usually used for Ubuntu family distribution installations.You can download Wubi installer from the Internet and then it will install all desired distribution automatically or you can run installer from CD or DVD.In this example Wubi is installed from Kubuntu live DVD.After inserting DVD into your computer's disk drive autoplay function offers to run Kubuntu installer. If you don't h...
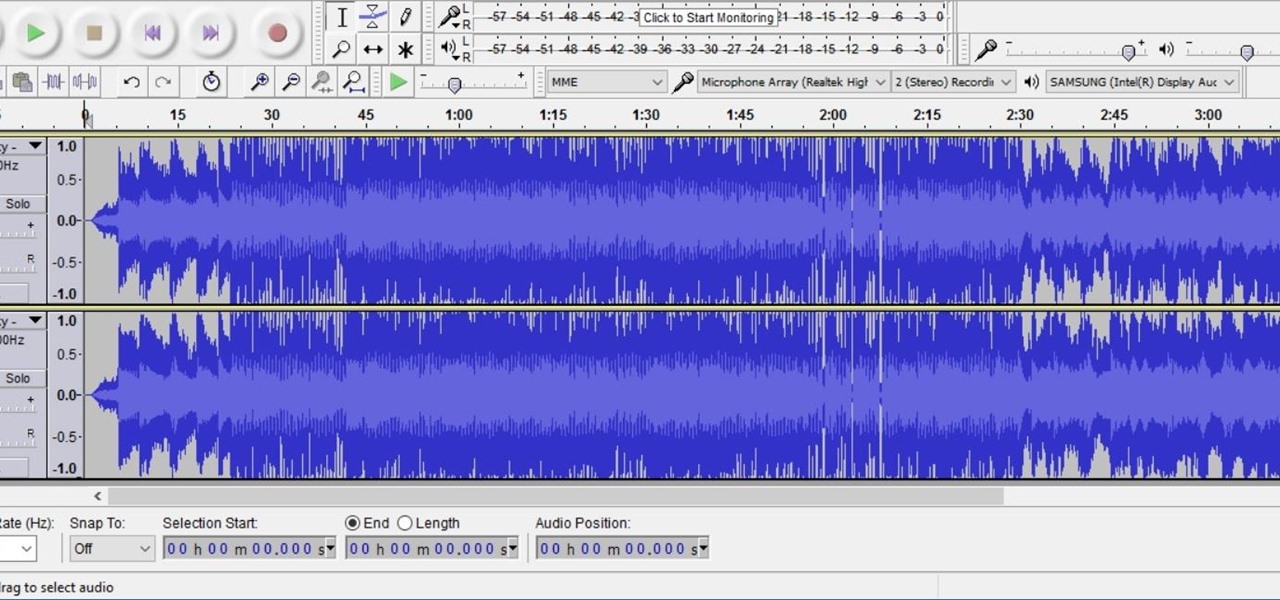
Need to remove the vocals from a song? Audacity just might be the answer. It's one of the few free audio editing programs out there with many, many features, making it simple to create a track for karaoke or simply to listen to an instrumental version.
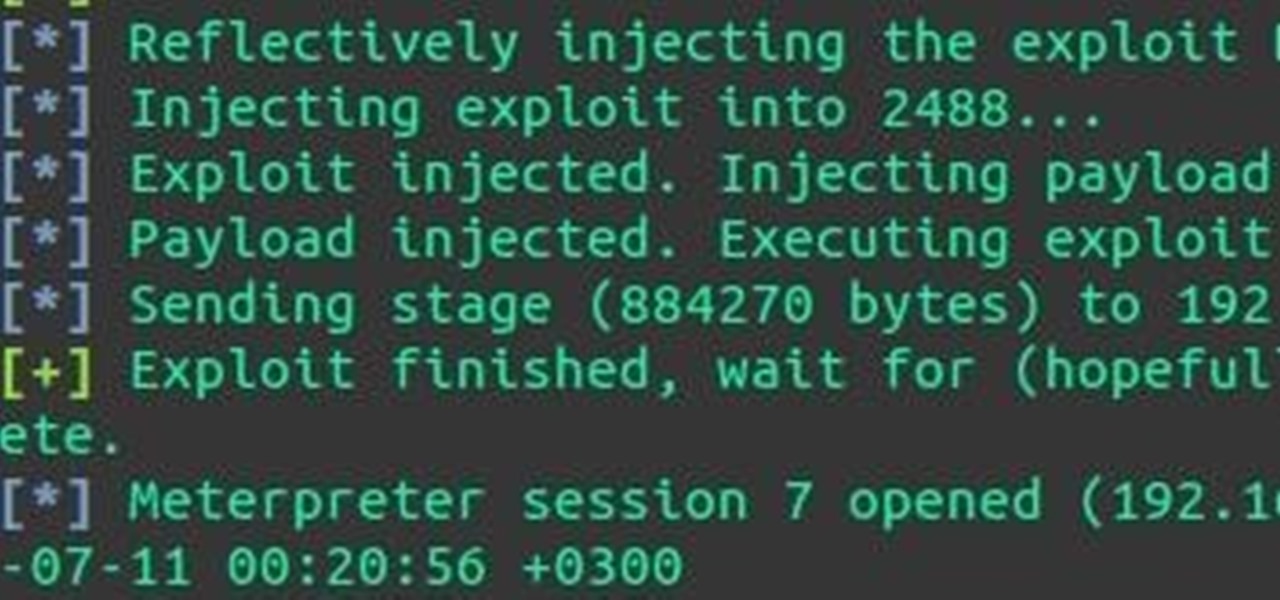
Hey everyone, I've been encountering some problems with privilege escalation when the target has an AV installed, so here's a tutorial for when the almighty "getsystem" doesn't cut it and "bypassuac" gets blocked by the AV. The machine is running Windows 7
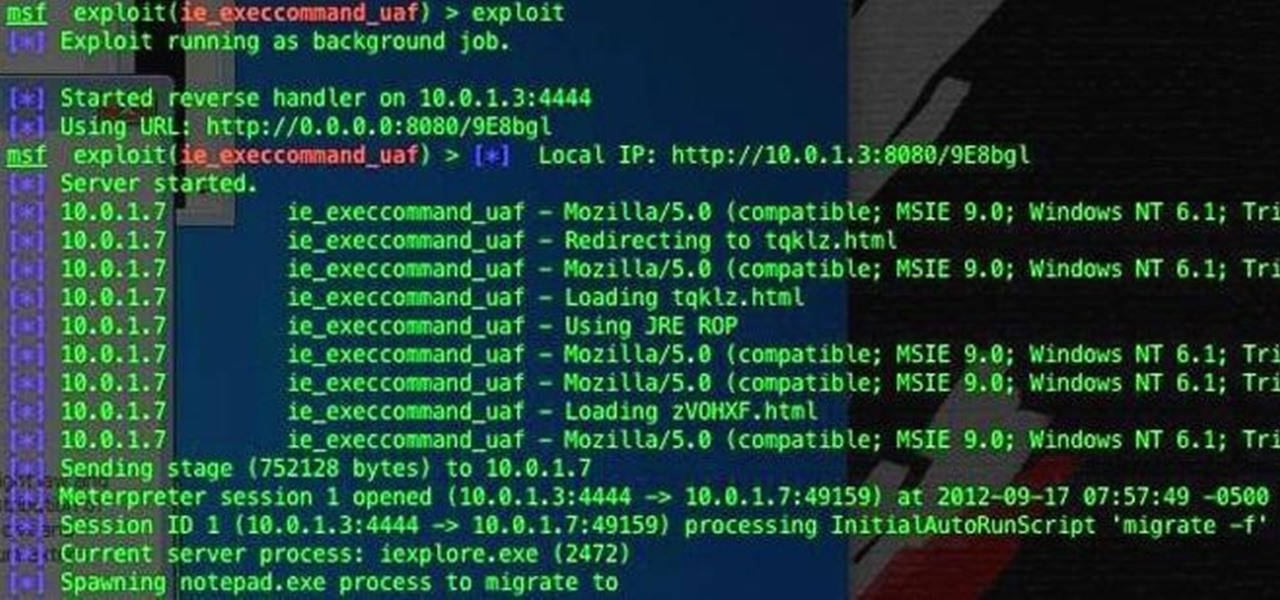
If you're one of the people who make up the nearly 24% of Internet users on Internet Explorer, now is a good time to click on 'Check for updates.' Researchers have found yet another Metasploit Zero-Day exploit that leaves IE 7, 8, and 9 vulnerable for Windows users. Brought to us by the same group as the Java 7 exploit a few weeks ago, this one uses a malicious site to install the Poison Ivy backdoor trojan while unsuspecting users browse. Once installed, it basically gives the attacker the s...

Watch this video to learn how to exploit this cool glitch in Infamous 2 for PlayStation 3. There's not a lot of driving in the game, with the superpowers and all, but you can still get inside a car with this Infamous 2 glitch.

Get unlimited money in Dragon Age: Awakening, without cheating! You can easily exploit this loophole with any merchant in the game. Just sell certain pieces of equipment back and forth until you have maxed out on how many sovereigns you have!

Let's face it, CDs and DVDs are a thing of the past. We no longer use them as a storage medium because they are slow, prone to failure in burning, and non-reusable. The future is flash memory. Flash memory is cheap, fast, and efficient. Eventually, flash drives might even replace discs as the preferred prerecorded selling format for movies.

Linux can have the most beautiful interface in the world, because it is simply what you make of it. You can change every little detail with relative ease because that's what Linux is all about: Freedom and OpenSource.

Post-exploitation is often not quite as exciting as popping the initial shell, but it's a crucial phase for gathering data and further privilege escalation. Once a target is compromised, there's a lot of information to find and sift through. Luckily, there are tools available that can make the process easy. One such tool is Postenum.

People use browsers for all types of things, and in general, we trust a lot of personal information to them. That's why browsers are a perfect attack surface for a hacker, because the target may not even know they are infected and feed you all of the information you could want.

Correctly identifying the underlying technologies that run on a website gives pentesters a considerable advantage when preparing an attack. Whether you're testing out the defenses of a large corporation or playing the latest CTF, figuring out what technologies a site uses is a crucial pen-tester skill.

In 2019, the Raspberry Pi 4 was released with specs including either 1 GB, 2 GB, or 4 GB of memory, a Broadcom BCM2711B0 quad-core A72 SoC, a USB Type-C power supply, and dual Micro-HDMI outputs. Performance and hardware changes aside, the Pi 4 Model B runs Kali Linux just as well, if not better, than its predecessors. It also includes support for Wi-Fi hacking on its internal wireless card.

Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.

Hello everyone Today I will show a different way to exploit a windows machine with a reverse https payload..."wait...why https? Isn't tcp good anymore?"

Ruby is a dynamic, general-purpose programming language created by Yukihiro "Matz" Matsumoto in Japan around the mid-90's. It has many uses but with it's flexibility, it makes a great language to write exploits in. In fact, the entire Metasploit Framework is written in Ruby! The sole purpose of this series is to teach hackers the basics of Ruby, along with some more advanced concepts that are important in hacking.

Welcome back, my tenderfoot hackers! Those of you who have been reading my posts here for awhile know how much I emphasize good reconnaissance. Novice hackers often jump into a hack/exploit without doing proper recon and either fail or get caught. Experienced and expert hackers know that 70-80 percent of a good and successful hack is dependent upon successful and accurate reconnaissance.

Welcome back, my rookie hackers! Most often, the professional hacker is seeking protected information from the target system or network. This might be credit card numbers, personally identifiable information, or intellectual property (formulas, plans, blueprints, designs, etc.). Most of my Null Byte guides have been focused on getting into the system, but this only begs the question—"what do I do when I get there?"

Welcome back, my rookie hackers! The more we know about a system or network, the better our chances of owning it and not leaving a trace for investigators to follow. One of the often overlooked sources for information is the Simple Network Management Protocol (SNMP). Many rookie hackers are not even aware of it, but it can prove to be a treasure trove of information, if you understand how it works and how to hack it.
Ok, now lets introduce myself i am also a newbie but conducted many pentests.This is the tutorial for customizing kali linux

This morning, I received a message from a friend who was reading a hack log, and she had some questions about the commands used. This got me thinking, as Linux has a ton of commands and some can be archaic, yet useful. We are going to go over everything you need to know to read a hack log and hopefully implant the steps in your head for future use.

Have you ever been away from home or on holiday and noticed an open network connection? FREE INTERNET! But then you find out that every search or page redirects you to an "enter password" or "signup here" page. Well, there are ways around this.

We're officially seeking Null Byters interested in teaching others! Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (if up to par, of course). This is a job meant for anyone with the will to share knowledge. There is no need to be intimidated if you fear you lack the writing skills. I will edit your drafts if necessary and get them looking top-notch! You can write tutorials of any skill level, and anything you feel like...

File recovery on Linux is a bit different than Windows. It requires different software than the Windows counterparts because every OS has their own file system. Windows uses NTFS, or FAT file systems, while on the other hand, Linux uses ext-based file systems. I personally use ext4 file system because it's the latest and greatest ext-journaling system and supports a large level of directory recursion and file sizes, but most installations still use ext2 or ext3. When files are deleted from a ...

Having a custom Linux distro can be the coolest thing ever. Most of you will probably be satisfied with any particular Linux distribution, but I know I'm not the only one out there who wants it to have custom configurations and programs preloaded while leaving the bloatware behind.

One of the main reasons I was held back from fully switching over to Linux was the fact that media streaming is nearly impossible. You have two choices in Windows: either you use file sharing with Windows Media Player, or you can just use the Windows Media Center. But both of these softwares are not for Linux or Mac. Microsoft doesn't like to make open source software because they believe in making a profit, instead of allowing others to innovate it.

This Null Byte is a doozey.

This article describes the very basics of compiling a program on Linux. It is targeted at the absolute beginner. Sometimes beginners search for programs on the web for their Linux systems, and is faced with the reality that they have to compile the program themselves, either because there exists no binary for their architecture, or the author of the program just doesn't release any binaries at all, but only sources.

This video is about how to play AVI files on a Playstation 2

THis video will show you how to use the immensely useful magma forges to make items without using fuel, and also how to use roads, sculpture gardens, and ponds to improve your fortress.

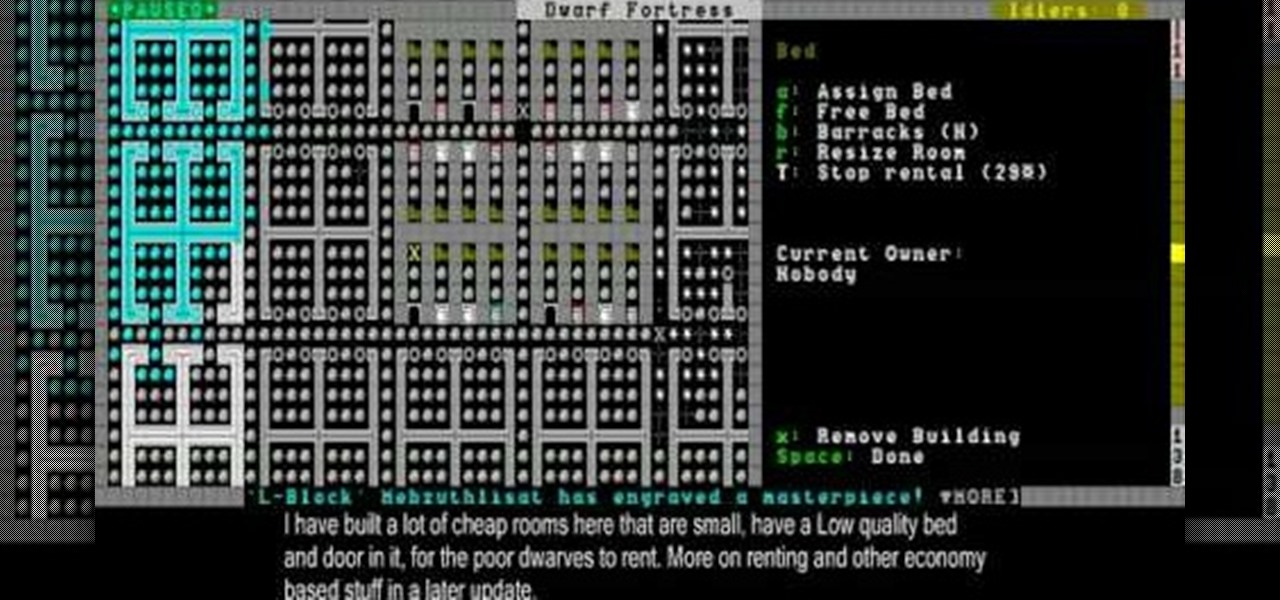
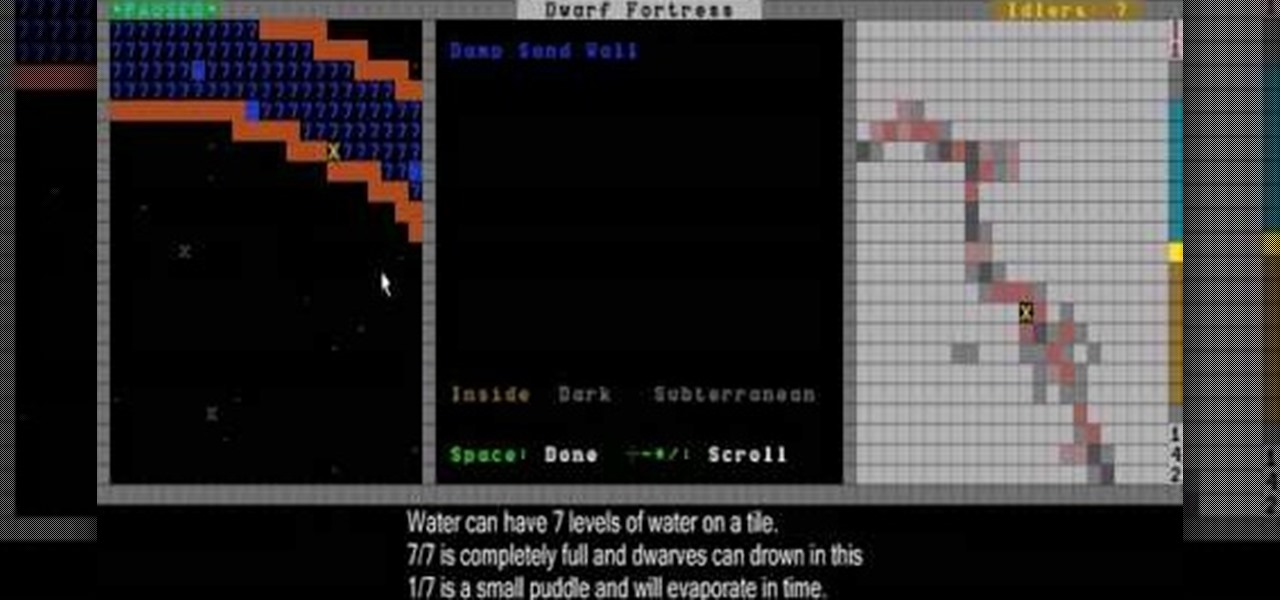
Now you've got a little bit of a fortress going, and it's time to continue building your infrastructure. This video will show you how to build bedrooms, farms, and stairs.

Once you've generated a world, picked a fortress location, and prepared seven dwarves, you're ready to start playing! This video will show you how the world map works and how to use it. It also covers how to rename your dwarves.

The Twitter bird, along with the Tux the Linux Penguin, is among the most popular of online animal logos. Not happy with the version that Twitter uses? Create your own twitty bird! This two-part video will show you how to draw the Twitter bird in Adobe Photoshop CS4. Now you can have a Twitter logo as large as you like, or make modifications to it like giving him a worm in his mouth or something. Whatever you want!

Android 10's new dark mode is a pleasure to behold for longtime users. Ever since OLED panels became widespread, we've been clamoring for the feature. But now that we have it, there's a new problem: it doesn't turn on automatically based on time of day. Thankfully, a simple app can turn dark mode into a true night mode.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

File inclusion can allow an attacker to view files on a remote host they shouldn't be able to see, and it can even allow the attacker to run code on a target.

The Shadow Brokers, a hacker group known for its dump of NSA hacking tools in 2016, has just leaked their remaining set of data which implies that the NSA compromised SWIFT, the global provider of secure financial services, to spy on banks in the Middle East.

Since Ive started to learn about nmap and metasploit and other tools I was learning well but I had one problem,

Welcome to my very first tutorial ever. Today I will be teaching you how you can use Arachni to scan vulnerabilities of web applications. I welcome all criticism good or bad as a teaching method for myself.

This tutorial is one technique to use the full functionality of your Pi. The small size makes it ideal for inside hacks, but still has the capabilities of a average desktop or computer. I should mention that a tutorial that OTW has done, but I'm gonna take it a step further. OTW made a brilliant article, but only touched on the surface of the possibilities. I hope this article will both show you many the possibilities and also allow you to start causing havoc, but I'm planning on making this ...