I have gotten comments from my last tutorial on not being able to do anything because of a lack of a monitor. In order to address this problem I'm gonna show you how to connect and control the Rasberry Pi through a SSH client on Linux, Mac, Windows, and Chromebook computers. This will probably we a long tutorial so please bear with me. Anyway, lets get to work.
This is for those using Kali Linux 2.0 that need to edit the CRDA values to get the increase in Txpower

What you probably don't know is when you remove a file on your system, it is actually still saved, and not entirely removed. Let me tell you how to get rid of it completely.

If your iPhone is rebooting or your Messages app is constantly crashing, you might be the victim of an iOS exploit or just a buggy software update. While one problem sounds worse than the other, they both can get annoying real quick when you can't send any messages or even read new ones.

At last, what you all finally waited for! Hi! Fire Crackers,

Welcome back, my tenderfoot hackers! As hackers, we often are required to get past antivirus (AV) software or other security measures. To do so effectively, we need to have some understanding of how AV software works. In this tutorial, we will take a cursory view of how AV software works so that you can better strategize on how to evade detection by it.

Google's latest Nexus device is big, bold, and beautiful—and now it's got root. Thanks to some quick work by legendary Android developer Chainfire, the Nexus 6 already had a clear-cut root method before most stores even had it in stock.

Heartbleed, move over. There's a new bug in town, and this time it's also affecting Mac and Linux computers. It's called Shellshock (its original official title is CVE-2014-6271), and it's currently got a 10 out of 10 severity rating over at the National Cyber Awareness System. While some updates have been issued to fix this bug, they were incomplete, and your system is probably still vulnerable, as it has been for the last probably 20 years.

Welcome back, my hacker novitiates! In previous guides, we have used one of the most powerful hacking platforms on the planet, Metasploit, to perform numerous hacks. They ranged from exploiting Windows XP and Windows 7/8 vulnerabilities, to installing a keylogger and turning on a webcam remotely. We have even been able to save the world from nuclear annihilation, see if our girlfriend is cheating, spy on suspicious neighbors, evade antivirus detection, and more.

Anyone who is familiar with Linux knows that to use your OS to the max, you will need to use the terminal every now and then. Whether it is to install a package or update the system or even delete a file.

Who am I? First let me introduce myself. I am Th3skYf0x, an -well lets call it

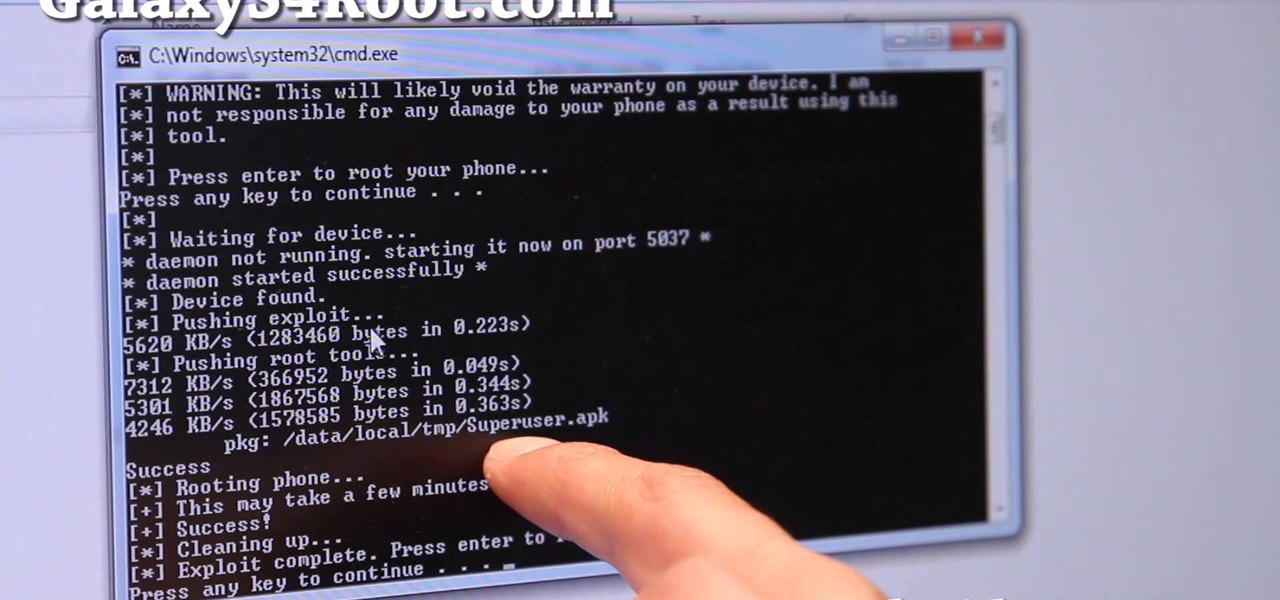
Here's a quick and easy video tutorial on how to root any Qualcomm-based U.S. or Canadian Galaxy S4 Android smartphone.

Many windows users, if not all, run into a virus infection once in a while. This is unavoidable when using Microsoft's operating system. Without digressing too much, the fact that Windows is such a popular OS with no controlled software sources makes it easy for viruses and malware to spread. And while there's a plethora of antivirus tools for Windows, sometimes infections (such as certain scareware) can disable the install and/or use of antivirus systems and render your OS unusable until cle...

Adamantine is the best, most versatile metal in Dwarf Fortress, but discovering and using it bears great risk. This video will teach you all about adamantine and how you should react to ensure you survive what happens after you find it.

If your fortress is pretty big and advanced, watch this video. It will give you some advanced tips on building a nearly complete fortress, then show off the creator's beautiful, 20-tutorials-in-the-making fortress.

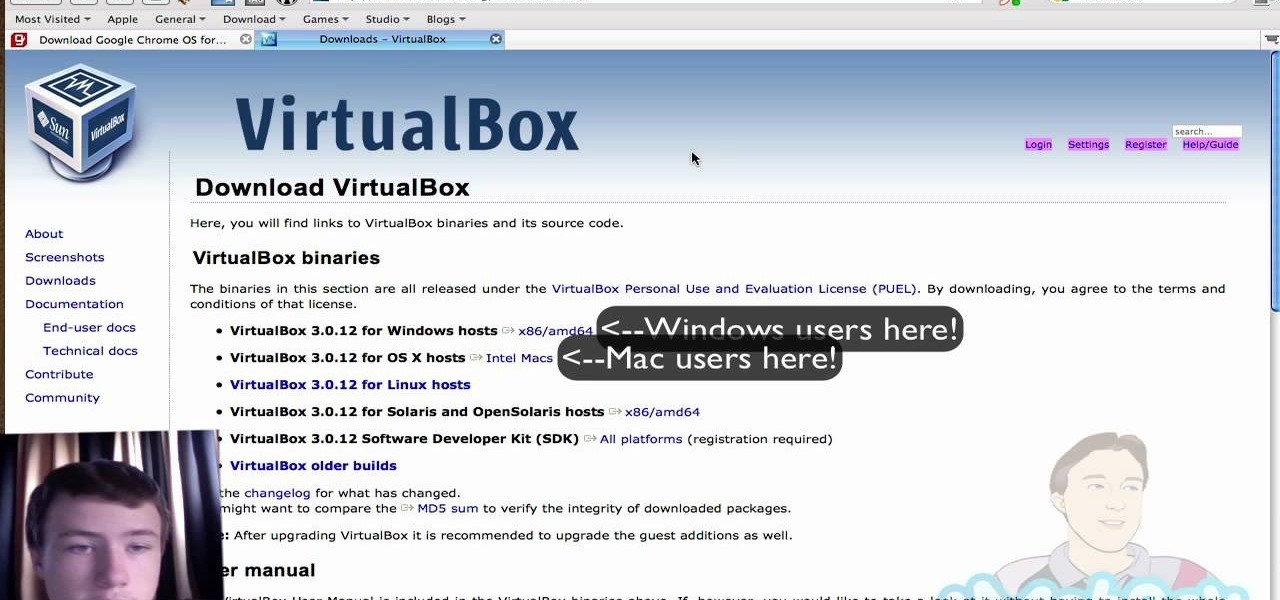
First download the virtual box, download it for Mac and install it. Now download the Chrome OS and extract it. Now launch your virtual box and click new. A "create new virtual machine" wizard will open, click next, put the name of the OS and choose Linux in operating system and Ubuntu in version now click next. Now give memory atleast 1000 MB and click next. Select "use existing hard disk" and tick the "boot hard disk" and choose the OS file by clicking the folder icon next to it, click add a...

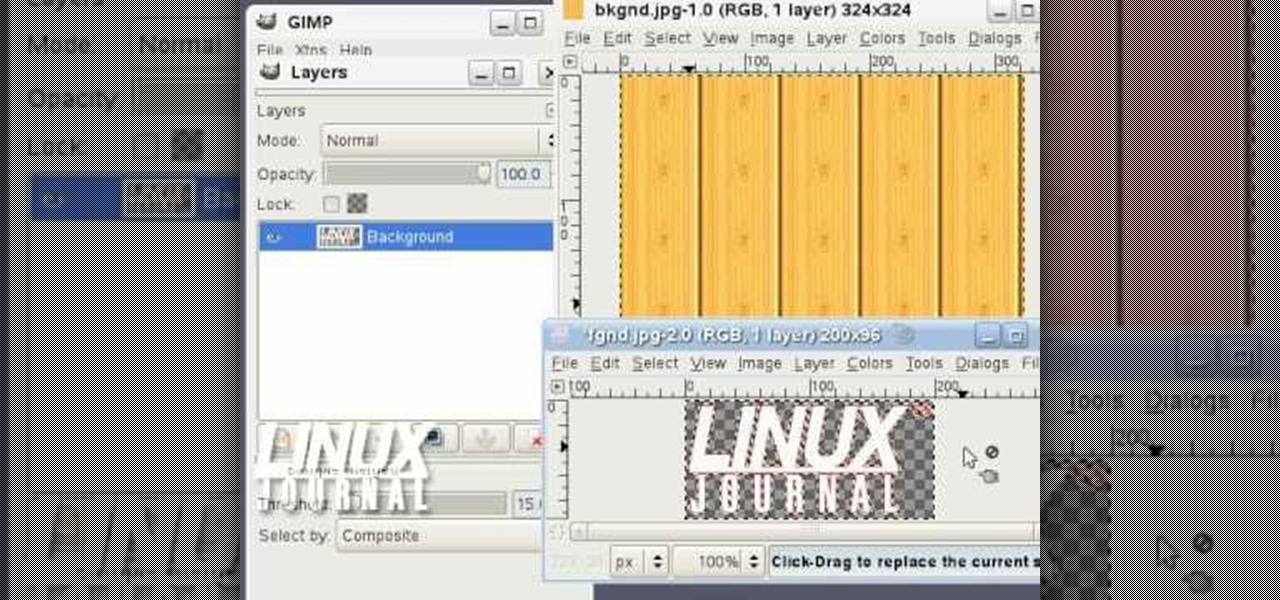
Learn how to add a new background to an image using Gimp. 1 Open the original image and the new background in Gimp. 2 Open the layers dialog and then click on add an alpha channel. 3 On the original image choose 'Select by color' from the menu and then hit delete. 4 Copy the image. 5 On the new background, select 'Add a layer'. 6 Paste on the new background. 7 Save and you are ready to go.

Bored of using complicated keyboard shortcuts to zoom in and zoom out of web pages? This simple, yet useful Firefox extension (QuickPageZoom 1.6.2) adds two icons to the status bar and two context menu items that enable quick access to the Full Page Zoom feature (Page Zoom In, Page Zoom Out and Reset Page Size).

Whenever you see a website that has some weird fonts or characters displayed on the web page, like a website containing Arabic fonts, but which are not displayed properly, then InshaAllaah, check this tutorial and you'll have the problems rectified.

Need a way to convert your scanned documents back into text files? Check out this video tutorial on how to convert scanned documents (JPG, PDF) to text.

New to Windows? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to reconnect media files to Windows Media Player.

New to Windows? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to create HD 1080p/720p videos with Windows Movie Maker.

VNC stands for Virtual Network Computing. It is remote control software which allows you to view and fully interact with one computer desktop (the "VNC server") using a simple program (the "VNC viewer") on another computer desktop anywhere on the Internet. The two computers don't even have to be the same type, so for example you can use VNC to view a Windows Vista desktop at the office on a Linux or Mac computer at home. For ultimate simplicity, there is even a Java viewer, so that any deskto...

TorrentFlux is an web-based system for managing bit torrent file transfers. It is an open source package (GPL) and developed for Linux, Unix & BSD platforms on the ubiquitous LAMP stack. In video tutorial, you'll learn how to set up TorrentFlux and how to share your downloaded content via a Samba share to an Xbox running XBMC. For detailed, step-by-step instructions, or to get started watching your own torrented media from the comfort of your couch, take a look.

This tutorial is on GIMP Basics. GIMP is a free Photoshop substitute available for all platforms and pre-loaded in Linux operating systems. The tutorial covers the scale, crop, cut with transparency, flip, and rotate commands of GIMP. Part 2 covers saving and file size reduction in GIMP.

Learn to access a number of Google Easter eggs with this simple Google hacker's how-to. Best of all, each of these Easter eggs can be found directly from Google search through use of Google's own "I'm Feeling Lucky" tool. The full list of Easter eggs explored in this video is as follows:

Ever here of the "overworked" defender" chess move? Of course you have, but that doesn't mean you know how to pull it off. See how to do it, right here. A chess piece is overworked when it has more than one defensive job (guarding pieces or squares) to do. Typically, the overworked piece is exploited by capturing one of the pieces it's defending or occupying a square it's defending. This forces it to leave one of its defensive jobs usually resulting in material loss or checkmate.

As Android bug bounty hunters and penetration testers, we need a properly configured environment to work in when testing exploits and looking for vulnerabilities. This could mean a virtual Android operating system or a dedicated network for capturing requests and performing man-in-the-middle attacks.

If you want to follow Null Byte tutorials and try out Kali Linux, the Raspberry Pi is a perfect way to start. In 2018, the Raspberry Pi 3 Model B+ was released featuring a better CPU, Wi-Fi, Bluetooth, and Ethernet built in. Our recommended Kali Pi kit for beginners learning ethical hacking on a budget runs the "Re4son" Kali kernel and includes a compatible wireless network adapter and a USB Rubber Ducky.

You may have seen news reports over the last two days detailing a major security flaw in virtually all smartphones. The devices that are at risk are not limited to either iPhone or Android — all of us are affected. If you want to make sure your smartphone and its data stay secure, there are a few steps you can take.

Kali Linux is the obvious first choice of an operating system for most new hackers, coming bundled with a curated collection of tools organized into easy-to-navigate menus and a live boot option that is very newbie-friendly. But Kali isn't the only distribution targeted at pentesters, and many exciting alternatives may better fit your use-case. We've already covered BlackArch Linux, now it's time to talk about Parrot Security OS.

In five short years, three generations of ultra-low-cost Raspberry Pi devices have challenged the boundaries of what a person can do with a $35 computer — especially with Kali Linux.

WordPress did not become what is arguably the most popular blogging and CMS platform on the planet because it was difficult to use. Rather, its user-friendly and rich feature set led to it finding a home on somewhere north of 70 million websites—and that's just counting blogs hosted on WordPress.com.

It's a given that if you're driving, you or someone you know has Waze as a go-to on their smartphone. The Google-owned crowdsourced navigation app is one of the best for avoiding traffic, roadblocks, and even cops.

Hackers are claiming money for a security flaw in Apple's new update. Quick Summary:

Hello, fellow hackers. I'm sure we've all seen it somewhere: the undying question of "How do I hack the game so-and-so?" And the answer usually is, "Come back when you actually know how to hack!" But how does one even go about "hacking" a game? What could that even mean?

Welcome back, my hacker novitiates! In an earlier Linux Basics tutorial, I had demonstrated the basics of the Apache web server. Since Apache is the world's most widely used web server on the Internet (as of July 2015, Apache was 38%, IIS was 26%, and Nginx is 15%), the more you know about it and understand it, the more success you are likely to have hacking it.

Welcome back, my novice hackers! Episode 6 of Mr. Robot has come and gone and, as usual, it did not disappoint. Once again, our hero, Elliot, has used his extraordinary intellect and hacking skills to awe and inspire us.

Welcome back, my budding hackers! This is the initial post of a new series on how to hack Facebook. It's important to note here that each hack I'll be covering is very specific. I have said it before, but I feel I need to repeat it again: there is NO SILVER BULLET that works under all circumstances. Obviously, the good folks at Facebook have taken precautions to make certain that their app is not hacked, but if we are creative, persistent, and ingenious, we can still get in.

Probably SSH is not as clean and fast as other useful tools like netcat, but it has some features which are very useful, and when you'll need them, here's how to behave with that huge amount of computers all over your house.