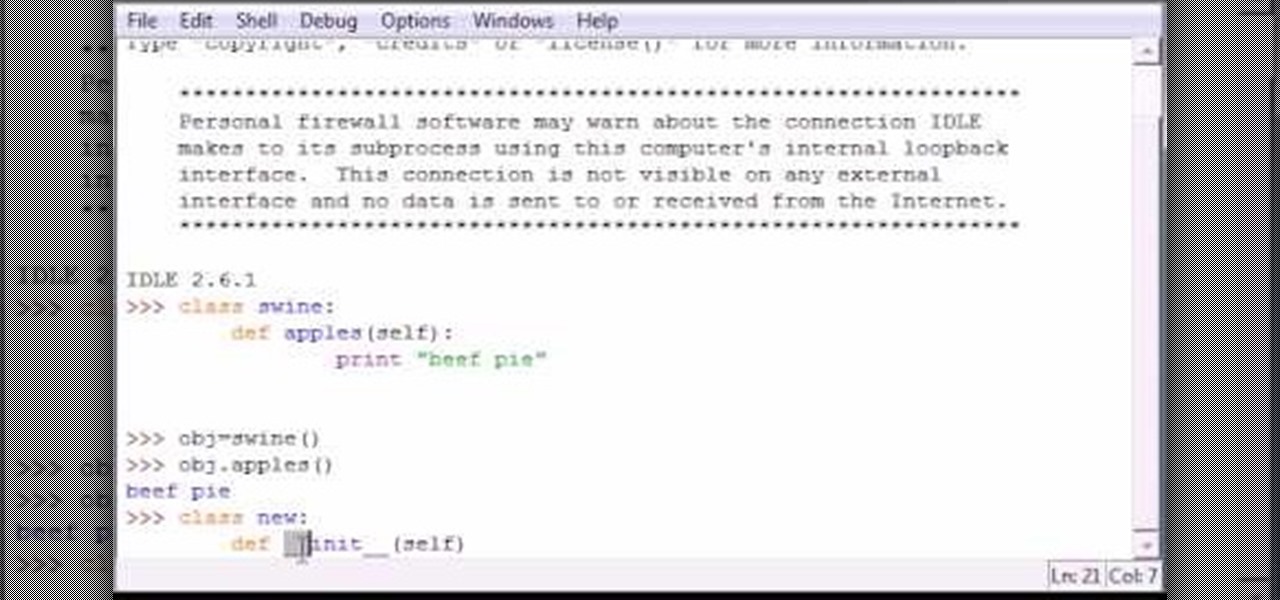
Bucky from The New Boston serves up this Python video tutorial on how to create and program constructors in Python. This is the program you use to write all of your Python code down. Learn how to create constructors and what they do!
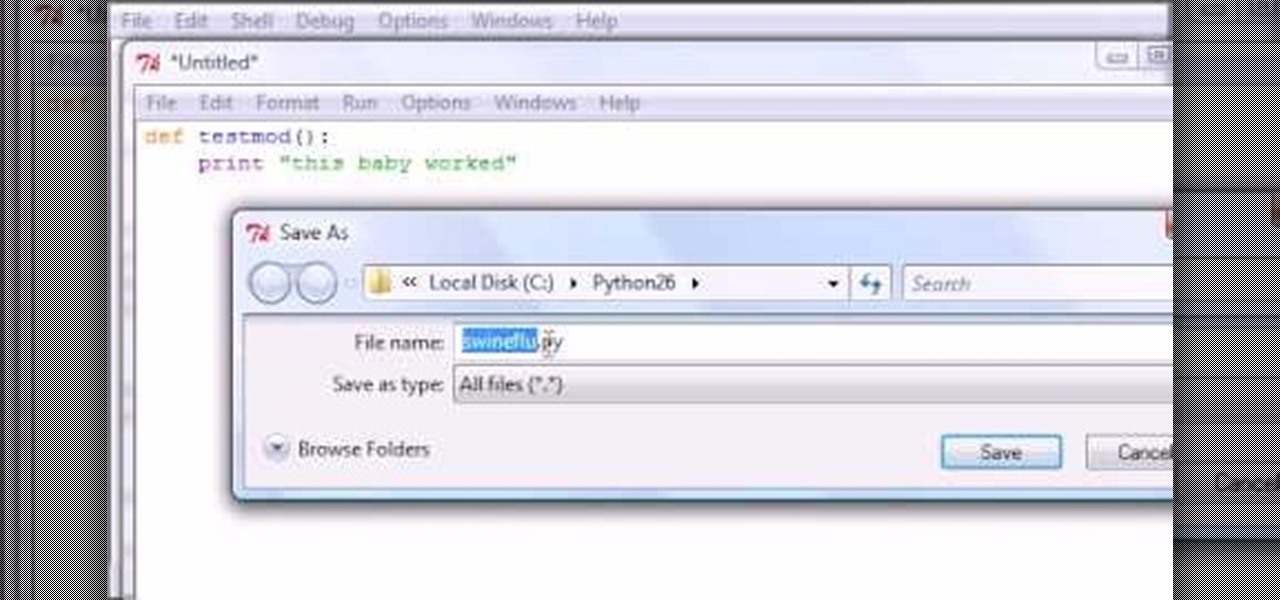
Bucky from The New Boston serves up this Python video tutorial on how to import modules into IDLE in Python. This is the program you use to write all of your Python code down. Fun with importing modules!
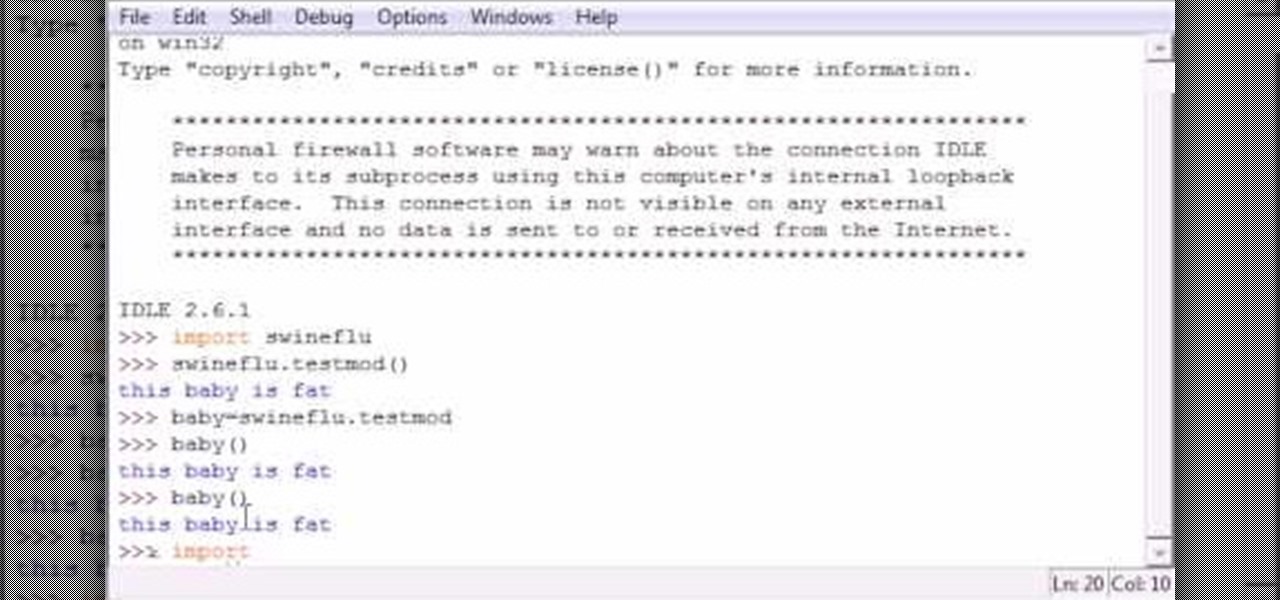
Bucky from The New Boston serves up this Python video tutorial on how to reload modules in Python. This is the program you use to write all of your Python code down. Learn how to reload modules once your source file has been edited!
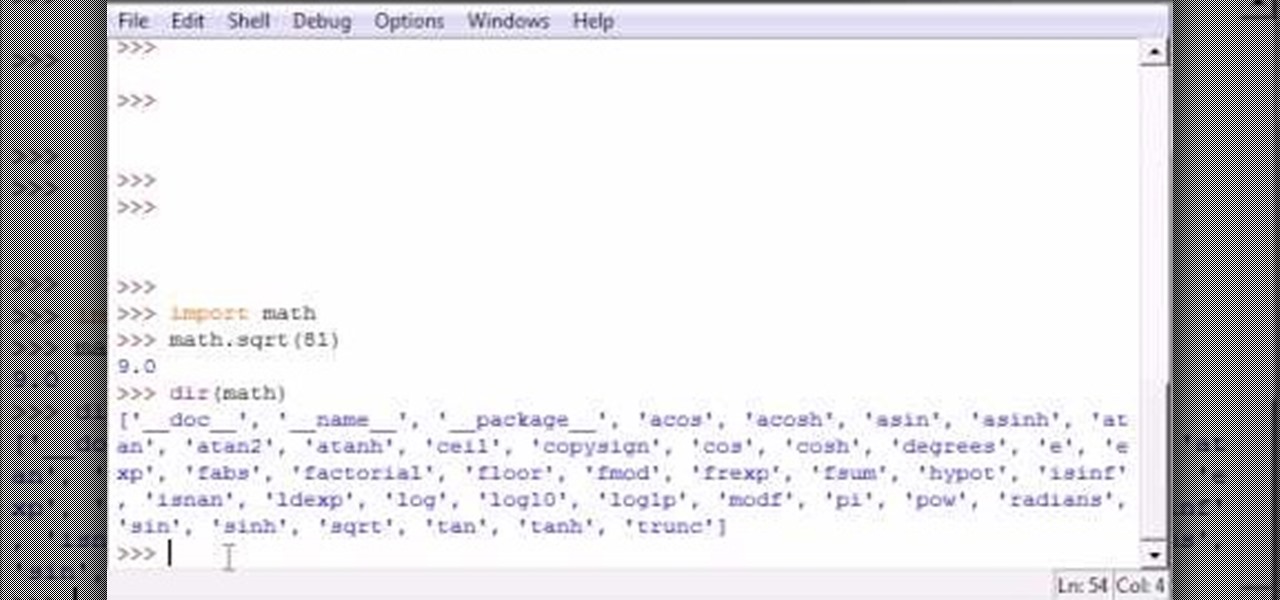
Bucky from The New Boston serves up this Python video tutorial on how to get module information in Python. This is the program you use to write all of your Python code down. Learn how to get extra info from outside modules!

Bucky from The New Boston serves up this Python video tutorial on how to work with files in Python. This is the program you use to write all of your Python code down. Fun with files!

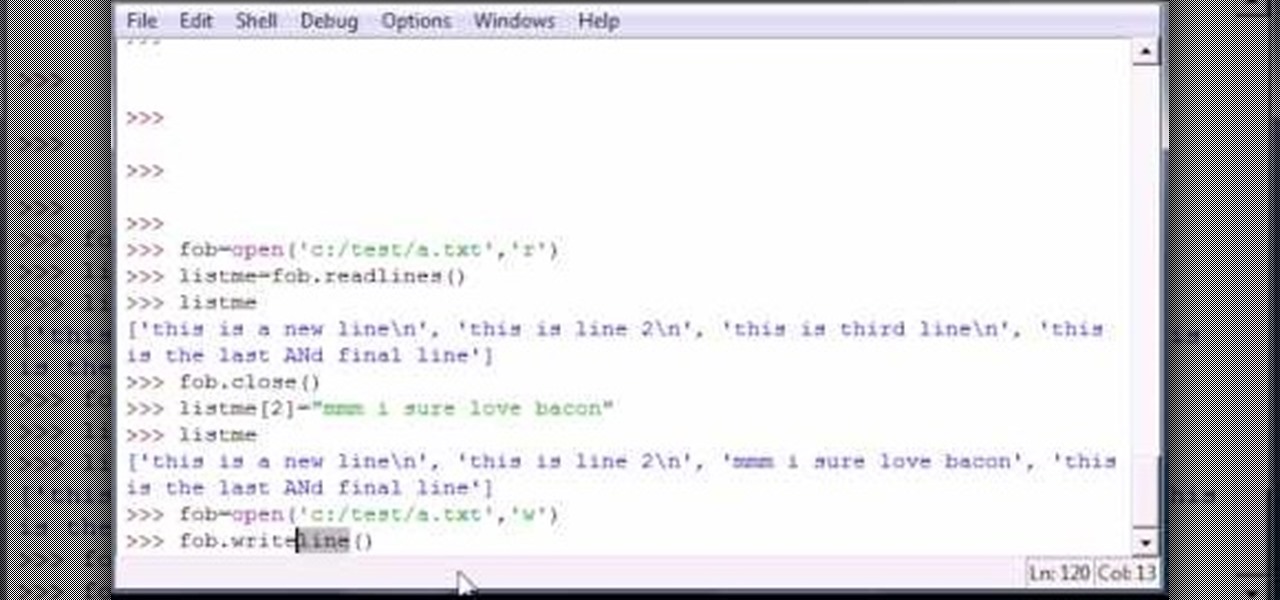
Bucky from The New Boston serves up this Python video tutorial on how to read and write lines in files in Python. This is the program you use to write all of your Python code down. Fun with reading and writing lines into a file!

Bucky from The New Boston serves up this Python video tutorial on how to program and write lines in files in Python. This is the program you use to write all of your Python code down. Fun with writing lines into a file!

Bucky from The New Boston serves up this Python video tutorial on how to download and install wxPython for Python. This is the program you use to write all of your Python code down. Learn how to install the GUI (graphical user interface) toolkit.

Bucky from The New Boston serves up this Python video tutorial on how to program methods in Python. This is the program you use to write all of your Python code down. Fun with methods! Learn what methods are and how to use them.

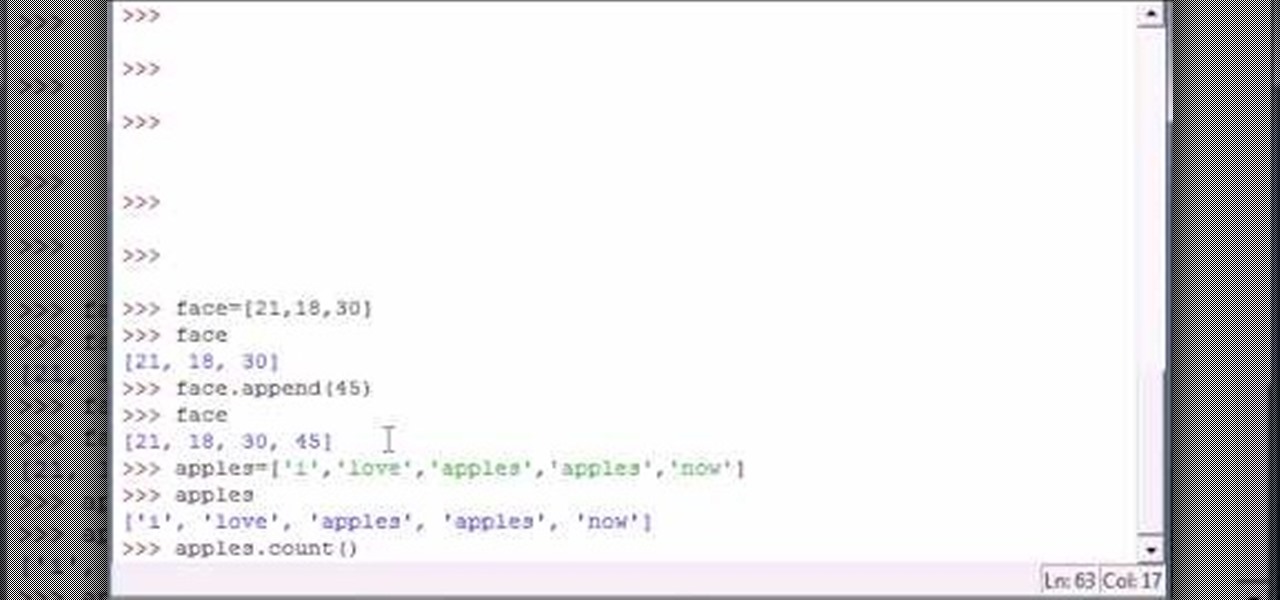
Bucky from The New Boston serves up this Python video tutorial on how to program slice lists in Python. This is the program you use to write all of your Python code down. Slice Python!

Bucky from The New Boston serves up this Python video tutorial on how to program lists functions in Python. This is the program you use to write all of your Python code down. Fun with list functions!

Bucky from The New Boston serves up this Python video tutorial on how to program slices in Python. This is the program you use to write all of your Python code down. Slice Python!

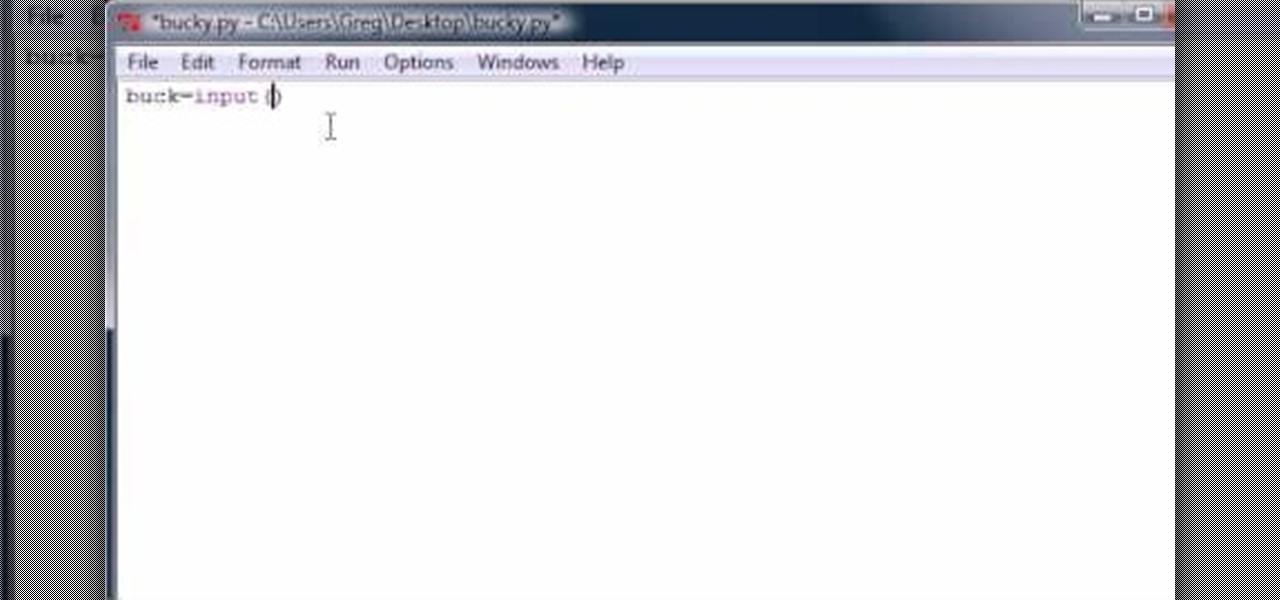
Bucky from The New Boston serves up this Python video tutorial on how to program raw input in Python. This is the program you use to write all of your Python code down. Fun with input versus raw input!

Bucky from The New Boston serves up this Python video tutorial on how to save and execute your programs in Python. This is the program you use to write all of your Python code down. Fun with saving programs!

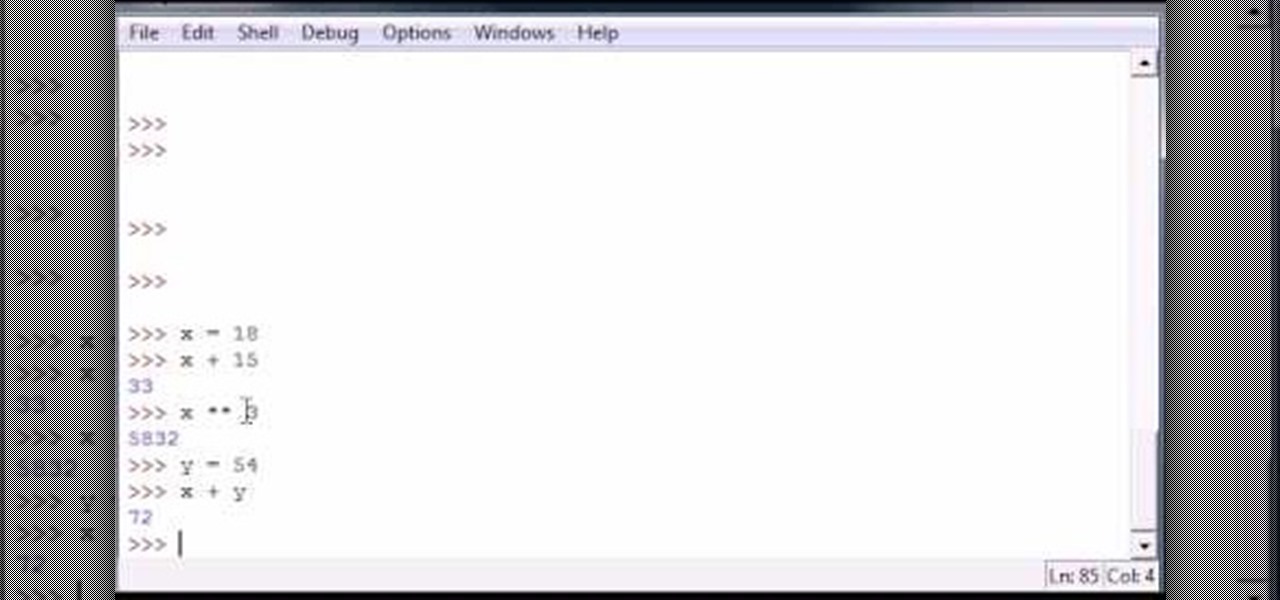
Bucky from The New Boston serves up this Python video tutorial on how to program variables in Python. This is the program you use to write all of your Python code down. Fun with variables!

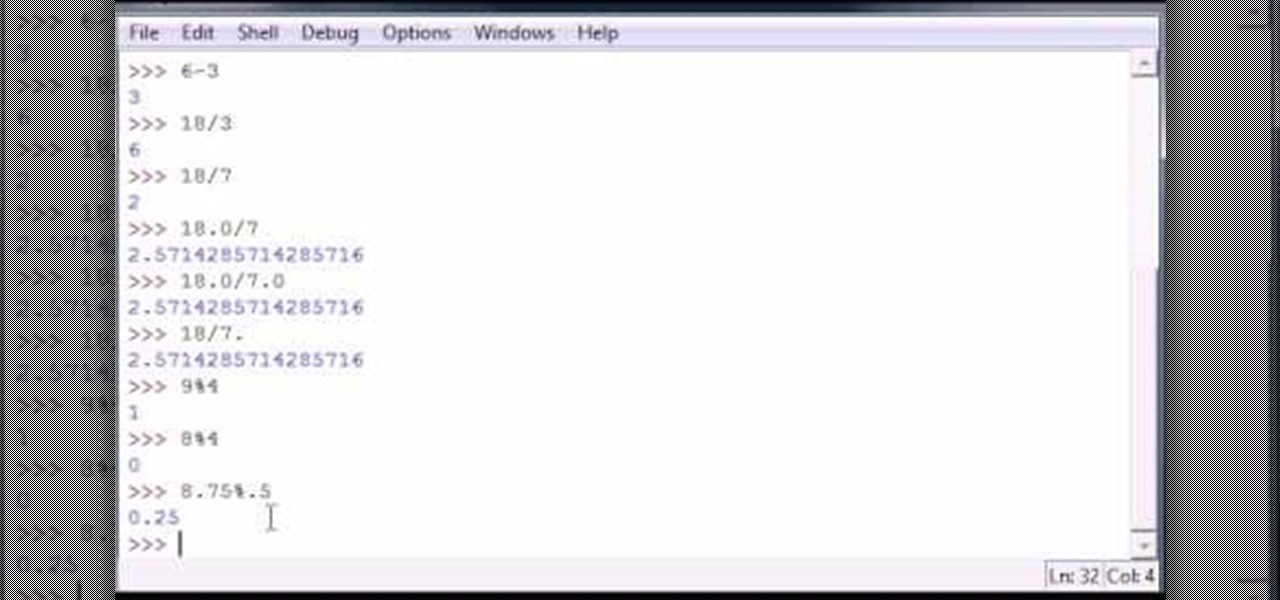
Bucky from The New Boston serves up this Python video tutorial on how to use simple numbers and math calculations in Python. This is the program you use to write all of your Python code down. Fun with numbers!

Bucky from The New Boston serves up this Python video tutorial on how to download and install Python. This is the program you use to write all of your Python code down.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to install a Wii homebrew hack using the Twilight Hack.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to backup Wii games to SD to play in HD.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to get free WiFi by tunneling through DNS.

This video tutorial is about Android, and no it's not a robotic creature, it's a software platform and operating system form mobile phones and PDAs. The Android system is based on Linux and was developed by Google and the Open Handset Alliance. Code is managed in the Java language, but can be written in C also, although C is not officially supported. A lot of the new cell phone and other mobile devices will be running off of Android, so know how to use it.

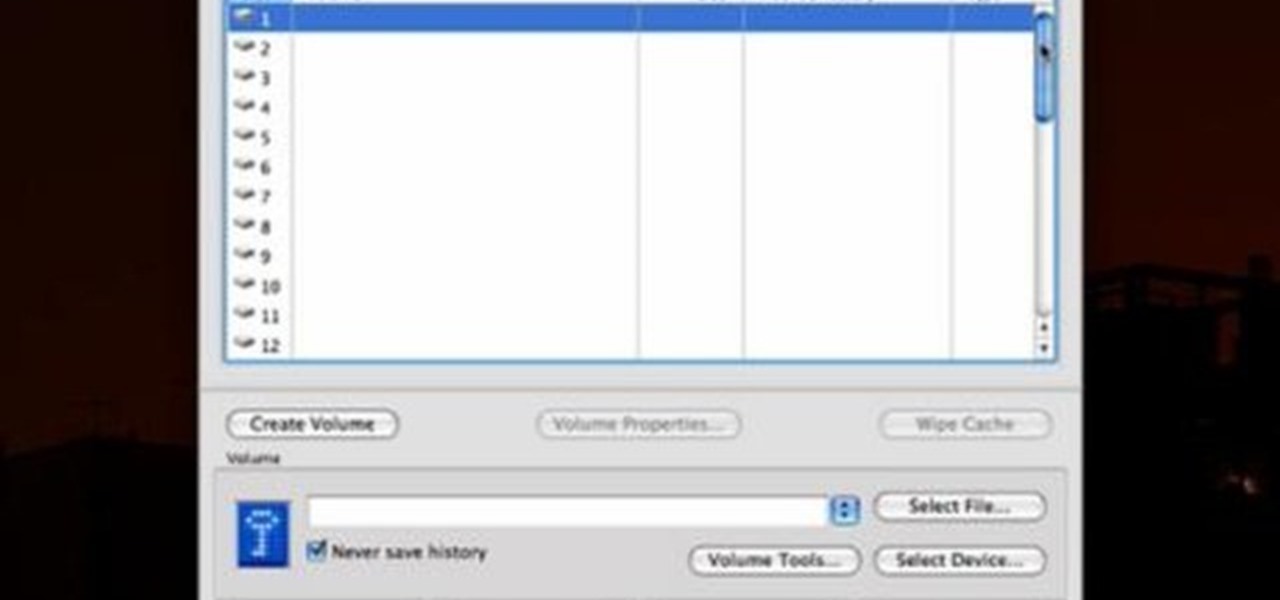
Check out this video tutorial to see how to keep your private files private, even if you have to email them to yourself at your office? TrueCrypt, an open source piece of software, lets you encrypt your files so they remain accessible only to you. This works on any platform; Windows, Linux, or Mac. So, watch this video to see the TrueCrypt download process, how to install it, and how to create an encrypted volume on your hard drive.

This video tutorial is about Android, and no it's not a robotic creature, it's a software platform and operating system form mobile phones and PDAs. The Android system is based on Linux and was developed by Google and the Open Handset Alliance. Code is managed in the Java language, but can be written in C also, although C is not officially supported. A lot of the new cell phone and other mobile devices will be running off of Android, so know how to use it.

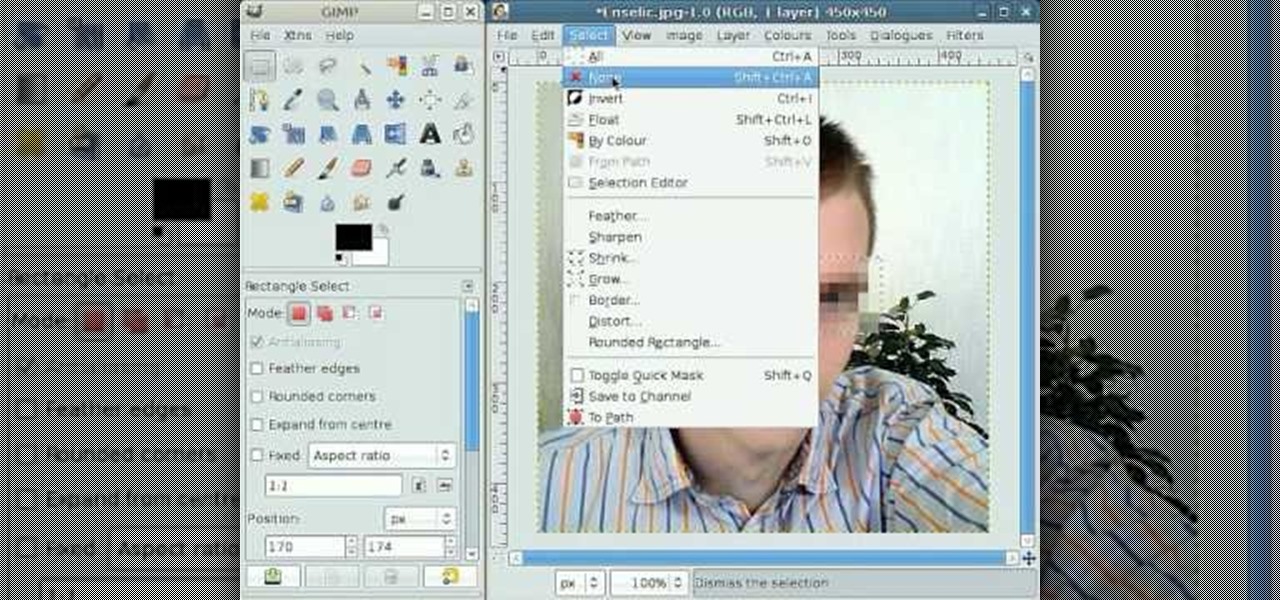
By following this tutorial you will learn the concept of selections in GIMP. Whenever he says "layer mask" he really meant "selection mask".

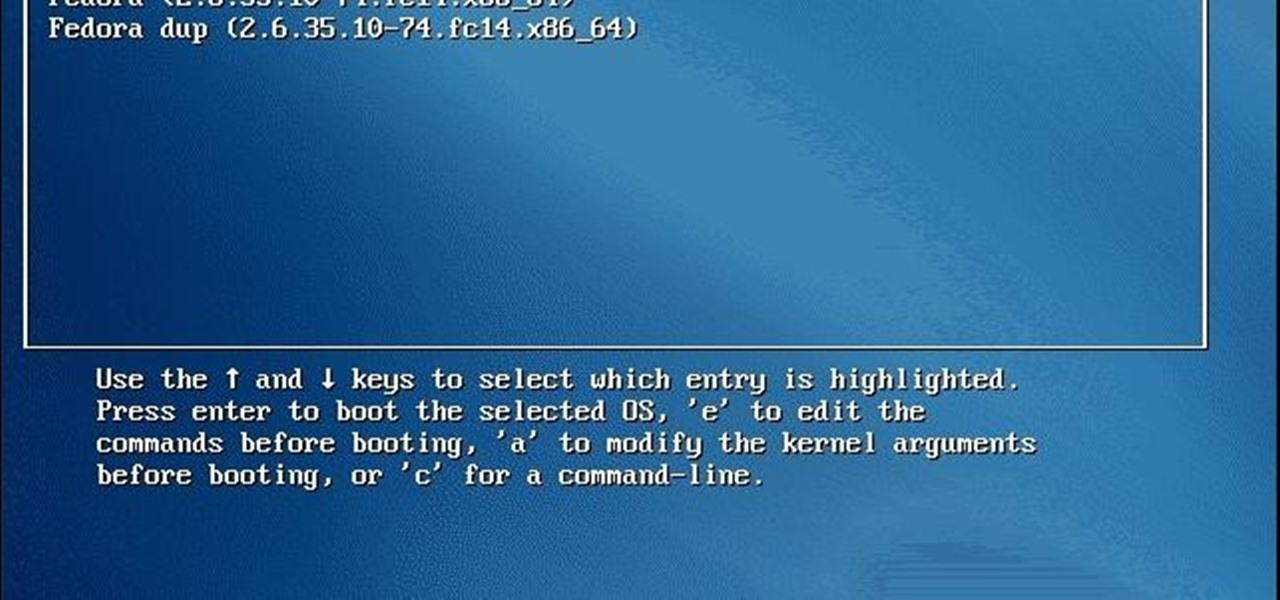
Hey guys, I am back this time with a small trick. Many of us do not like the old background in GRUB BOOT LOADER, you might be using kali linux or any other linux and using GRUB BOOT LOADER then this is for you.

GamingGuy118 shows a live walkthrough of glitches & tricks for Modern Warfare 2 on Favela. Watch step by step how to use a variety glitches & tricks during gameplay for Modern Warfare 2 on Favela. Strafe jump like a pro, learn the Elevator trick, find the perfect sniping places, and earn a lot of points. Learn the tricks to accessing untouchable positions. Exploit glitches to take out your enemies and render yourself untouchable. Hover a mile above the ground and take down your opponents. Fol...

This shows me getting the highest possible medal on Bejeweled Blitz on Facebook applications by exploiting the timing window when the clock runs out (250k medal). To keep getting combos when the timer runs out, you need to select the next gem you want to swap before all the other gems are done falling. Once you have the desired gems selected repeatedly click the square that you want to swap. If you did it right, as soon as the gems on the screen all stop falling, your combo will go off and th...

For Infinity Exists Full Disclosure's first Website Hacking episode, we demonstrate how to exploit a security vulnerability occurring in a website's database to extract password hashes. Sql (Structured Query Language) is a computer language designed for the retrieval and management of data in a system's database. The Attack, known as Sql Injection, manipulates Sql statements before they are sent to the Sql Server, allowing the Attacker to create, change, or retrieve data stored in the database.

If you ever want to root your OnePlus 6, install TWRP, get Magisk and Xposed, or flash a custom ROM, the first thing you'll need to do is unlock your bootloader.

Android used to have a notification ticker, but those days are long gone. Now, important new messages pop up on the top half of your screen with what's known as a "heads up notification." If you're in the middle of something, these popup notifications can be pretty annoying — luckily, it's pretty easy to turn them off.

The Raspberry Pi loads an operating system from whatever SD card you insert, allowing you to keep different operating systems on separate SD cards depending on which OS you wish to run. A tool called BerryBoot cuts down on the number of SD cards needed by providing the ability to boot multiple operating systems from a single SD card, similar to Boot Camp for Mac computers.

With chips in four out every five PCs made since 2010, few companies are as pervasive in modern computing as Intel. That's why an advisory released Monday, May 1, confirming a remotely exploitable vulnerability in all non-server business hardware made in the last seven years has sent shockwaves through the technology world.

A new repository appeared in Microsoft's GitHub account a few months ago for a project called HoloJS. For those JavaScript developers out there that have been wanting to make HoloLens apps, this one's for you.

When it comes to modding an Android device, a custom kernel can take you farther than almost anything else. Most offer the ability to overclock your processor for performance gains, change your CPU governor, or even under-volt to increase battery life, among other features.

Welcome back, my hacker novitiates! Often, to hack a website, we need to connect to and exploit a particular object within said website. It might be an admin panel or a subdirectory that is vulnerable to attack. The key, of course, is to find these objects, as they may be hidden.

Welcome back, my amateur hackers! With Halloween right around the corner, I thought you could have a little fun with your newfound hacking skills using a hack that is guaranteed to freak out your boss, teacher, coworker, friend, etc.

Welcome back, my tenderfoot hackers! WordPress-based websites are among the most numerous on this planet (maybe other planets too, but I can't vouch for that). According to WordPress's own website, WordPress powers 23% of the top 10 million websites. That's approximately 2.3 million sites using WordPress!

This tutorial is for those who've purchased an account with Private Internet Access to hide your VPN and would like to set it up in Kali. Please note, you can chose to run your PIA service from your Windows computer without configuring it in linux as long as you'll be using a NAT connection. Using a NAT connection will allow your Windows machine and Kali Virtual Machine to use the same IP address, hence if your IP is hidden on one, it will be hidden on the other.

So, you want your terminal to be customized with awesome script every time you fire it up, huh?! Well, look no further because I am here to answer this calling!

Relentless in its fury, the iOS text messaging exploit that exploded onto the scene late last week seems to do more damage than initially reported.