If you've ever wiped your computer without having a proper backup of your operating system, or just wanted to cause some havoc online, chances are you've had to rely on Linux to help you out, specifically the Ubuntu distro.

Welcome back, my tenderfoot hackers! Hacker newbies have an inordinate fixation on password cracking. They believe that cracking the password is the only way to gain access to the target account and its privileges. If what we really want is access to a system or other resources, sometimes we can get it without a password. Good examples of this are replay attacks and MitM attacks. Neither requires us to have passwords to have access to the user's resources.

I love Android, and I think its apps are great—the polish that came with the Ice Cream Sandwich update truly put Android design on the map. That being said, one of the more frequent complaints from iOS fans continues to be that apps just "run smoother" and "look better" on iOS than they do Android.

Welcome back, my aspiring hackers! Domain Name System (DNS) is one of those things we seldom think about unless it doesn't work. Then, it can be very frustrating when we attempt to navigate to a website and we get that frustrating error message.

Welcome back, my neophyte hackers! Have you ever had a neighbor that you're certain is up to no good? Maybe you've seen him moving packages in and out at all hours of the night? Maybe you've seen people go into his home and never come out? He seems like a creep and sometimes you hear strange sounds coming from his home? You know he's up to no good, but you aren't sure what it is exactly.
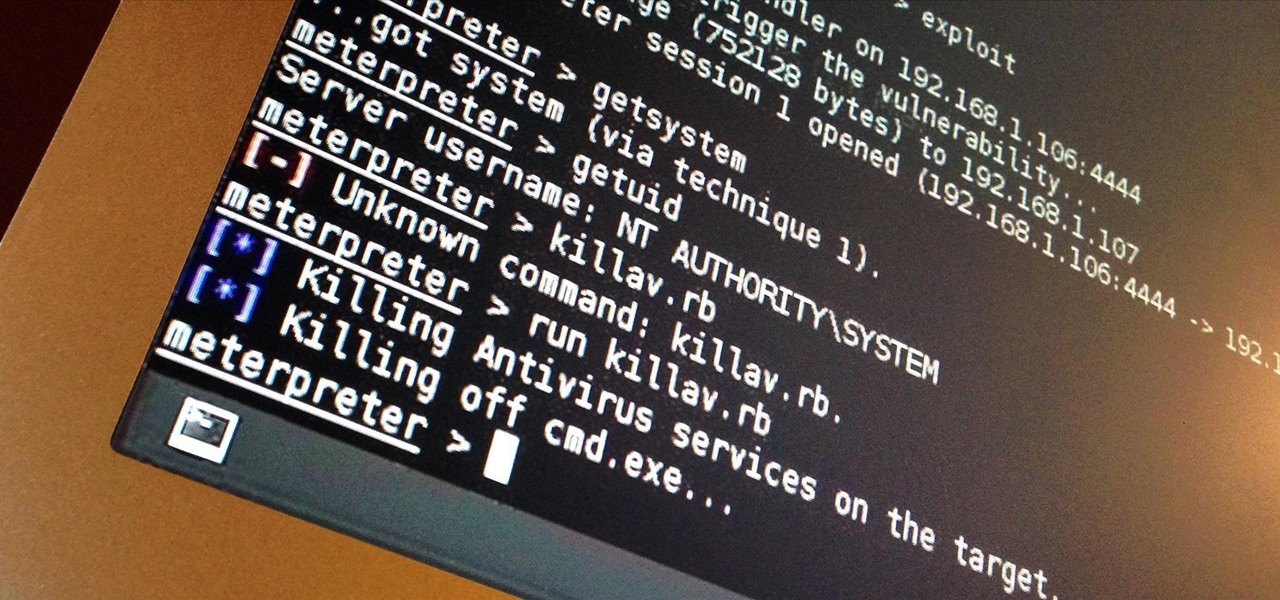
I've done numerous tutorials in Null Byte demonstrating the power of Metasploit's meterpreter. With the meterpreter on the target system, you have nearly total command of the victim.

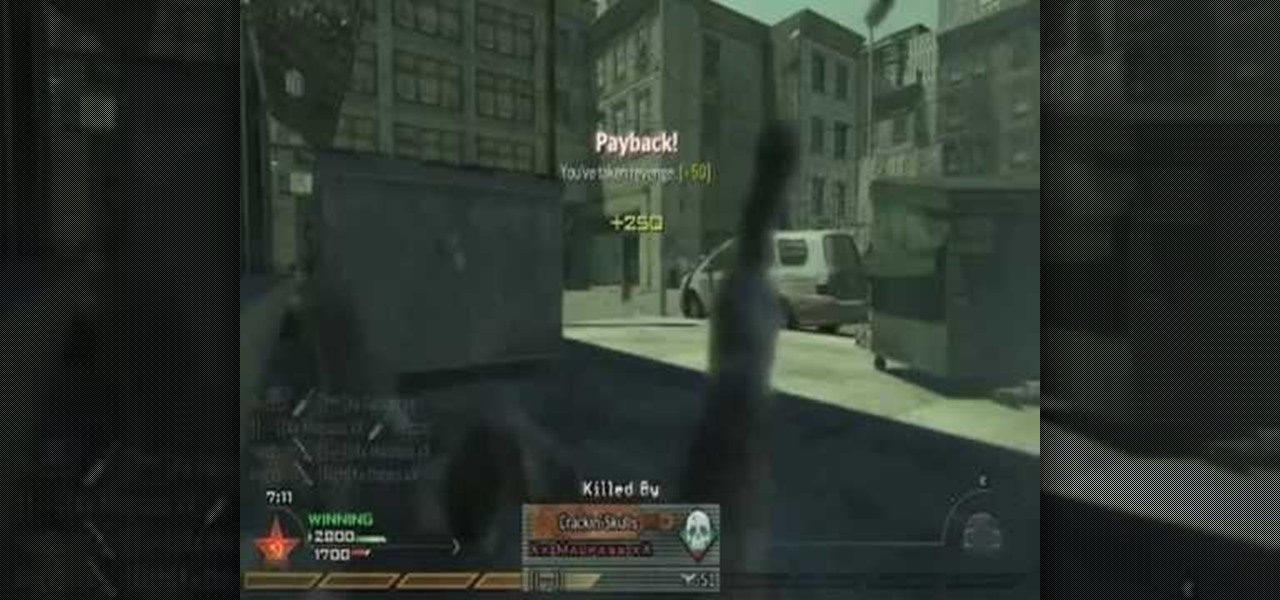
Welcome back, my neophyte hackers! In today's hack, we're going to have a bit of Halloween fun. Have you ever had a boss who made you miserable with his micro-management and nagging? Maybe you thought he unfairly fired your friend/colleague? Well, now here's your chance to get a bit of revenge and keep him or her off your back!

Welcome back, my newbie hackers! Hackers often are associated with clandestine and illegal activity, but that is not necessarily always the case. Hackers are increasingly being used and employed for law enforcement, national security, and other legitimate purposes. In this installment, we will look at how a single hacker could save the world from nuclear annihilation.

Linux is generally a pretty stable OS, but occasionally things happen. However, as long as your keyboard has a SysRq key, you'll never need to worry about freezes again.

DD-WRT is a Linux firmware available for many Linksys, NetGear, Belkin, D-Link, Fon, Dell, Asus and other vendor's wireless routers. DD-WRT is far more feature rich than the stock firmware that comes with most routers. This video covers the basics of installing and configuring DD-WRT. Install and configure DD-WRT firmware on your router.

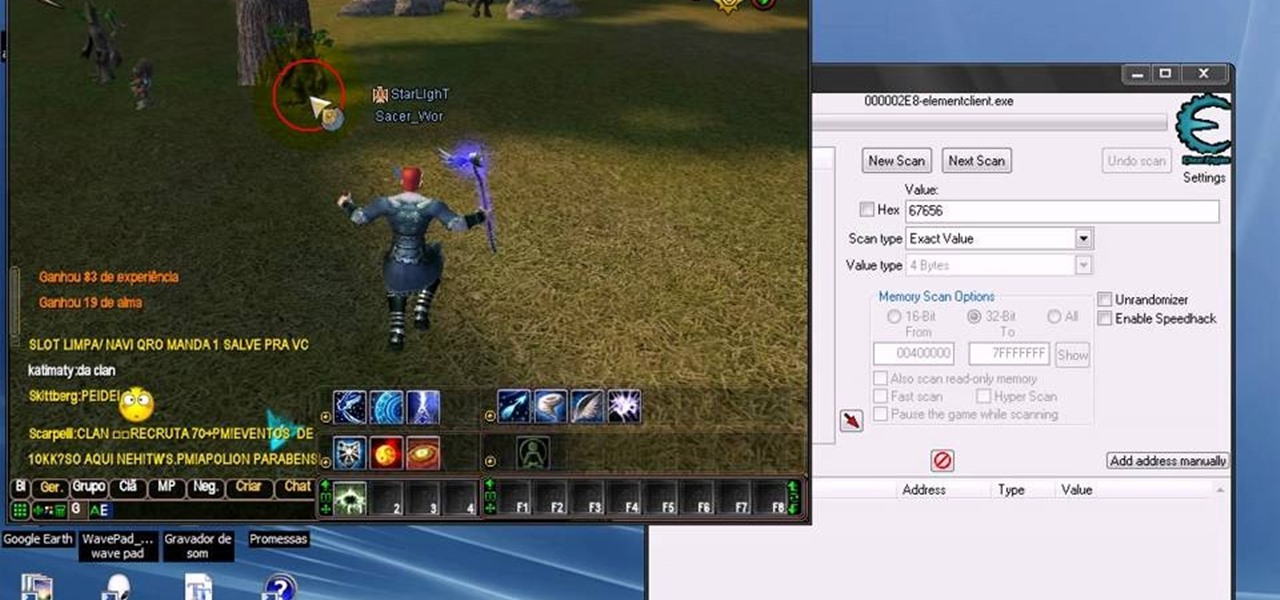
Tired of grinding out endless, boring quests for meager returns when you're playing Perfect World International? Want to rocket to high level and immense piles of treasure immediately? Cheat Engine is your answer! This free game hacking program frees you from having to hunt for cheat codes or exploit glitches to get ahead in PWI. Just follow along with this easy and quick hacking tutorial, which shows you how to use this program to change many of the values of your character and in the game.

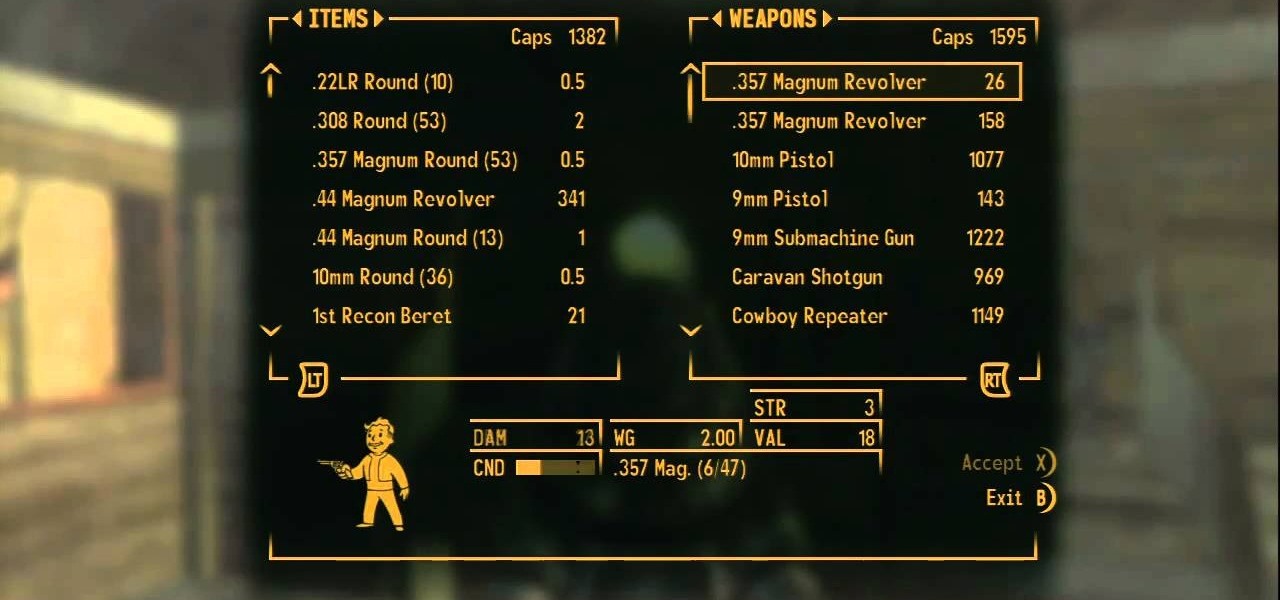
An old glitch seems to have carried itself over from Fallout 3 right into Fallout New Vegas! Not surprising as they used the same game engine and resources, but regardless of that, you'd think that the Q&A team would have caught it. In this video you will learn how to exploit this glitch by purchasing a cheap item and then selling it back for more than the original price over and over and over again. Details in the video!

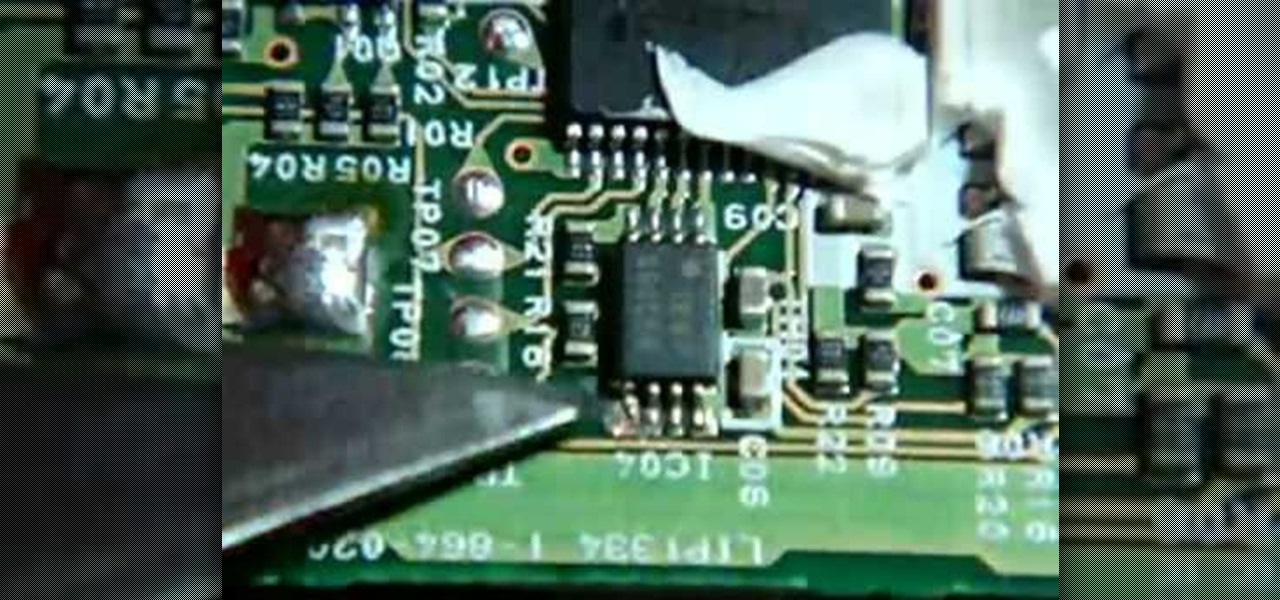
In this video tutorial, viewers learn how to create a Pandora battery for the fat PSP. A Pandora battery allows the user the process of using exploits and hacks to execute unsigned code on the PSP. Before beginning, users are advised to completely drain the battery. Begin by taking out the battery and cut it open. Use a knife and gently pry it open. Do not damage the circuit board. You will need to break the pin under the number 4. Then put it back together and place it back into the PSP. Thi...

Have you ever wondered how sumo wrestlers are able to obtain and maintain such massive figures? Joseph Stickland, an applied clinical nutritionist, will explain to you exactly how a sumo wrestler is able to do this. Joseph will also explain the health detriments and the dangers to this type of lifestyle. Joseph explains that sumo wrestlers will skip breakfast, exercise, eat massive amounts of calories, (10,000 calories at least) for lunch, take a nap, and then have another mega calorie meal f...

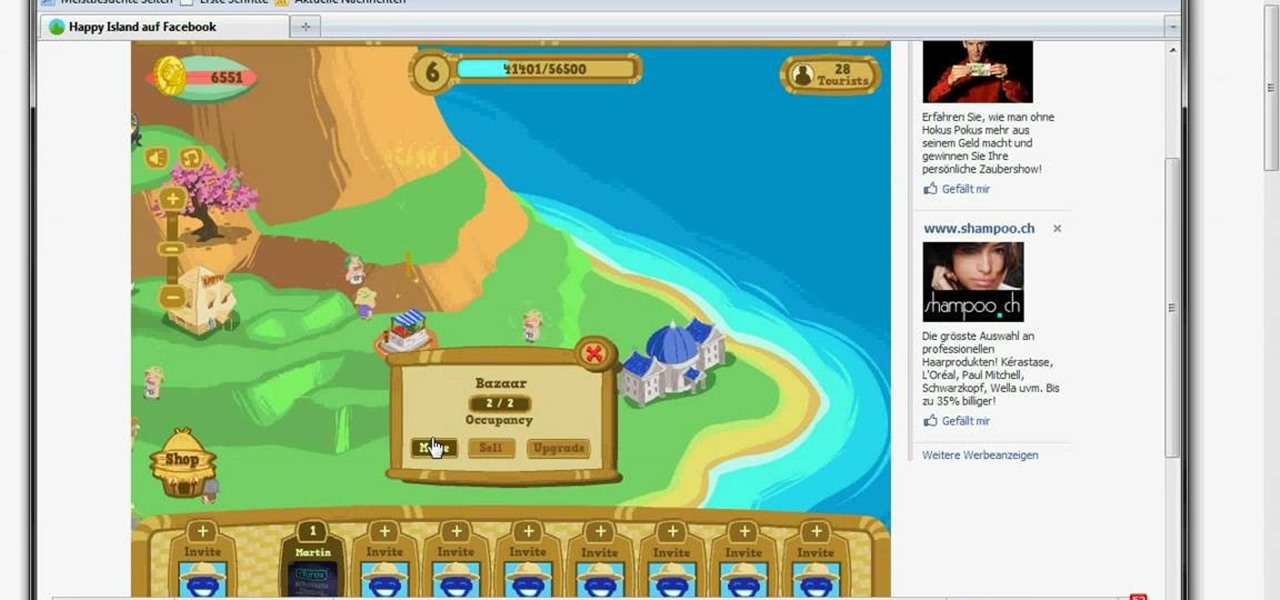
There's an easy way to get more money in Happy Island, and the answer is Cheat Engine. With CE, you can easily earn more money, so start hacking today!

The javelin glitch in Modern Warfare 2 is currently being exploited for great and evil purposes. Watch this video to learn how to take advantage of this glitch, for both the XBox 360 and the PS3. Fair warning, though: doing this glitch could get you banned by the powers that be at XBox Live.

Stick Wars hacks, cheats, glitches. How to hack the flash game Stick Wars from Addicting Games. Watch this video tutorial to learn how to hack Stick Wars with Cheat Engine (09/27/09).

This is a tutorial for the PC game Spore. Spore is about creating a universe of creatures you dream up. It's a super easy and accessible game and this walkthrough shows you how to mod your creatures so they have floating limbs and parts. Put parts on the end of a limb, then extend or thicken the limb. Simple as that. This game is from the creator of The Sims.

Check out this two-part 3ds Max video tutorial which exploits a little known capability of Max to create a head. You'll find this technique easier than box modeling for heads since your topology and edge flow are there from the beginning. With box modeling, there's a lot of division, connecting, turning, etc. to get basic topology in place.

I have to say, the Xbox 360 controller is the best controller ever created. When I first held it back in 2005, I swore that the dudes working at Microsoft came over and took a molding of my hands because of how great it felt. The thing felt like it was born there.

Archiving and compression is a great way to store and prepare files for sending. You can reduce the size of a file, turn a group of files into a single file, and even encrypt and password the contents! Just take a look at this image to see how much it compressed a 28GB text file.

In Linux, all password hashes are normally stored using the MD5 hashing algorithm in the /etc/shadow file, but MD5 is algorithmically weak due to collision vulnerabilities. The new recommended standard are the higher level SHA-2 hashing algorithms, SHA256 or SHA512. As a friend pointed out to me, Ubuntu is currently the only distro implementing SHA-2 as the default. With SHA-2, your passwords take an unreasonably larger amount of time to calculate. This will greatly decrease how many password...

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

If left unattended, a hacker with a USB Rubber Ducky and physical access to the computer can infiltrate even the most secure computer. Such attacks often go undetected without the use of a tool like USBRip, which can provide you with assurance that your device hasn't been compromised.

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

Hacking from a host machine without any form of proxying is reckless for a hacker, and in a penetration test, could lead to an important IP address becoming quickly blacklisted by the target. By routing all traffic over Tor and reducing the threat of malicious entrance and exit nodes with a VPN, we can configure Kali to become thoroughly private and anonymous.

When it comes to modifying Android, the single, most powerful tool available is TWRP custom recovery. It's even more capable than simple root access when it comes to changing the look and feel of your software, and you can even use TWRP to root your device in a few simple steps.

Welcome back, my greenhorn hackers! The Holy Grail of any hacker is to develop a zero-day exploit—an exploit that has never been seen by antivirus (AV) and other software developers, as well as intrusion detection system (IDS) developers. In that way, you can exploit systems with your newly discovered vulnerability with impunity!

UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found at my blog, here - at my blog, here - https://techkernel.org/2015/12/11/embed-metasploit-payload-in-apk-easily/

This year, Google released two Nexus phones to glowing reviews, and as we've grown to expect, the Android community wasted no time in coming up with a root method for both. In fact, legendary root developer Chainfire even devised an entirely new "systemless" method for rooting that should make updating a bit less complicated, along with a few other benefits.

Welcome back, my greenhorn hackers! Throughout this series on Metasploit, and in most of my hacking tutorials here on Null Byte that use Metasploit (there are many; type "metasploit" into the search bar and you will find dozens), I have focused primarily on just two types of modules: exploits and payloads. Remember, Metasploit has six types of modules:

Welcome back, my rookie hackers! So many readers come to Null Byte to learn how to hack Wi-Fi networks (this is the most popular hacking area on Null Byte) that I thought I should write a "how-to" on selecting a good Wi-Fi hacking strategy.

With each day that dawns, there is a new, major hack that makes the news headlines. If you are paying attention, there are usually numerous hacks each day and far more that never make the news or are kept private by the victims. Every so often, a hack is so important that I feel compelled to comment on it here to help us learn something about the nature of hacking and IT security. This is one of those cases. Last week, the U.S. Office of Personnel Management (OPM) revealed that they had been ...

There's a recently discovered flaw by iDownloadBlog that lets thieves reset a stolen Apple Watch without a hitch, which is the result of Apple not including the Activation Lock feature that iPhones have had since iOS 7.

No, your Apple Watch isn't totally hacker-proof, despite what some have claimed.

Just short of a week after its release, the new HTC One has been rooted thanks to Android devs beaups and jcase, the same guys that brought us S-OFF for the original HTC One (M7).

While the Google Play Store is filled with big name magazines like Time, Forbes, Sports Illustrated and Maxim, it also panders to smaller audiences, like with Coin Prices, Soap Opera Digest, Watch Journal and Quilter's World (which yes, is all about quilting). If you have a select few that you enjoy reading, prices aren't usually a problem; issues range from $1.99 to $4.99 for each one, or from $19.99 to $39.99 for yearly subscriptions. If you're someone that is a magazine connoisseur, prices...

This video provides information on how a hacker can find an vulnerability on a remote computer and exploit it to gain remote access. Also, the video shows how a hacker can raise their privileges on the remote machine to administrator. Hack a computer for remote access.

Common programming blunders can be your best friend when trying to craft your own exploits. If you spend a little time reading what some of these common blunders are, they can uncover potential attack vectors or just show you the weird ways in which computers can store and recall data or access system resources.

Motorola may have changed its mind about making its devices hard to unlock by creating a tool to do it for you, but they've been slow to update it to include the latest and greatest models. Want to beat them to the punch? Just consult djrbliss over on XDA-Developers, who came up with a root exploit that will unlock all the newest Motorola smartphones, like the Motorola Atrix HD, Photon Q, and new Razrs. It's simple. Just connect your device to your computer, download and extract the zip file ...