A flaw in WPS, or WiFi Protected Setup, known about for over a year by TNS, was finally exploited with proof of concept code. Both TNS, the discoverers of the exploit and Stefan at .braindump have created their respective "reaver" and "wpscrack" programs to exploit the WPS vulnerability. From this exploit, the WPA password can be recovered almost instantly in plain-text once the attack on the access point WPS is initiated, which normally takes 2-10 hours (depending on which program you use).
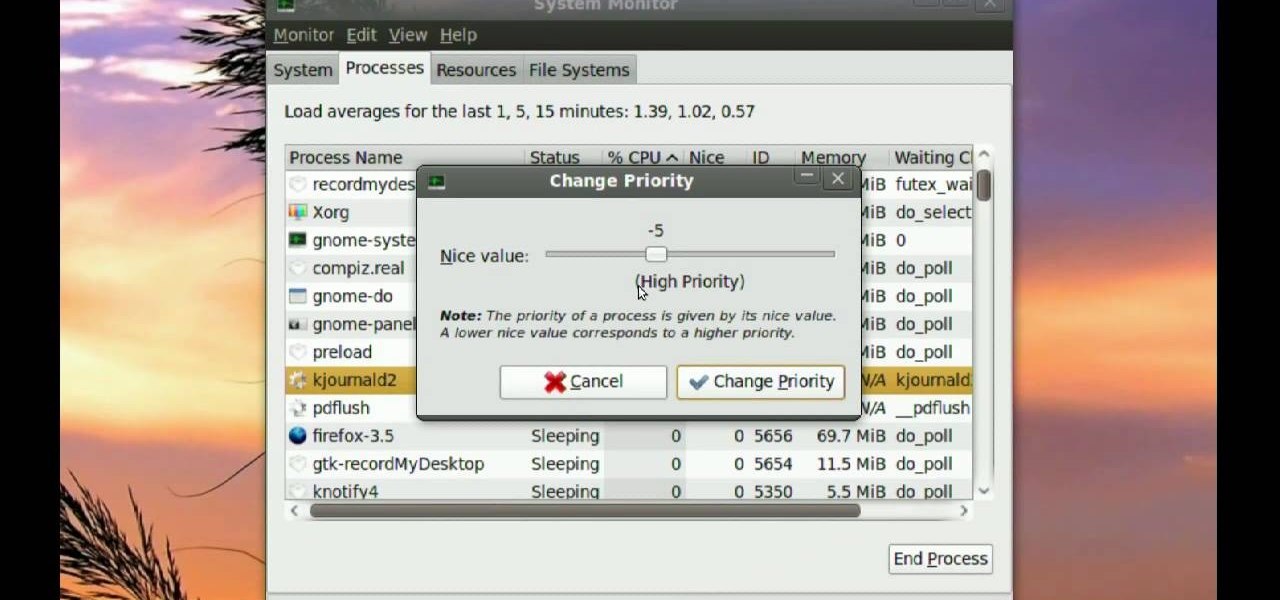
Ubuntu comes with pre-installed tools that can help solve problems you may encounter when using Ubuntu Linux. This video tutorial shows how to identify and address common problems in Ubuntu Linux. Such tools discussed include the system monitor, the log file viewer and the network tools.

Are you, as a Linux user, jealous of the gaming possibilities available to your Windows and GNU/Linux-running friends? In this tutorial, Linux Journal Gadget Guy Shawn Powers walks you through how to play Windows games on Linux using Wine, an open source implementation of the Microsoft Windows API built on the X-Window System.

Welcome back, my rookie hackers! I recently began a series on using Metasploit, and my goal with it is to teach you the very basics the incredibly powerful hacking tool has to offer while progressively moving on to the more advanced features.

When I left off on our last hack, we had hacked into the ubiquitous Windows Server 2003 server by adding ourselves as a user to that system so that we can return undetected at any time. The problem with this approach is that a sysadmin who is on their toes will note that a new user has been added and will begin to take preventative action.
What's the best way to cheat death in Dark Souls? By cheating of course. IGN reveals an exploit on the PS3 that allows you to stop the game during a save and resume it with humanities and souls intact. Be sure to use this exploit at your own risk.

A router is the core of anyone's internet experience, but most people don't spend much time setting up this critical piece of hardware. Old firmware, default passwords, and other configuration issues continue to haunt many organizations. Exploiting the poor, neglected computer inside these routers has become so popular and easy that automated tools have been created to make the process a breeze.

I'm sure that many of us have heard of that nasty Shellshock vulnerability, but not very many people know how to exploit it. Try these few tricks on vulnerable websites!

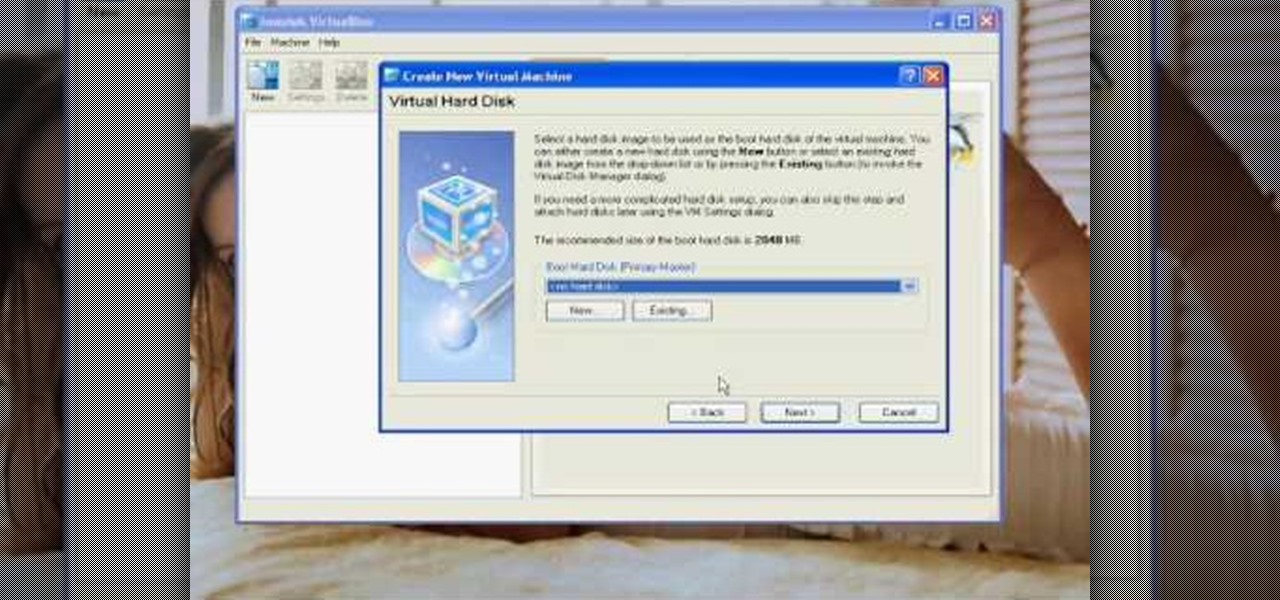
The author shows how to install Puppu Linux 4.3.1 in Innotek VirtualBox 1.5.2. He shows steps to create a new virtual machine in Innotek VirtualBox, by showing the various configuration settings like the RAM size, hard disk space etc. He shows how to boot the virtual machine with the Puppy Linux installation ISO file. Next, during boot up, he shows how to set the language and regional settings, resolution settings etc. In the next screen he shows how to access the local drive and partition it...

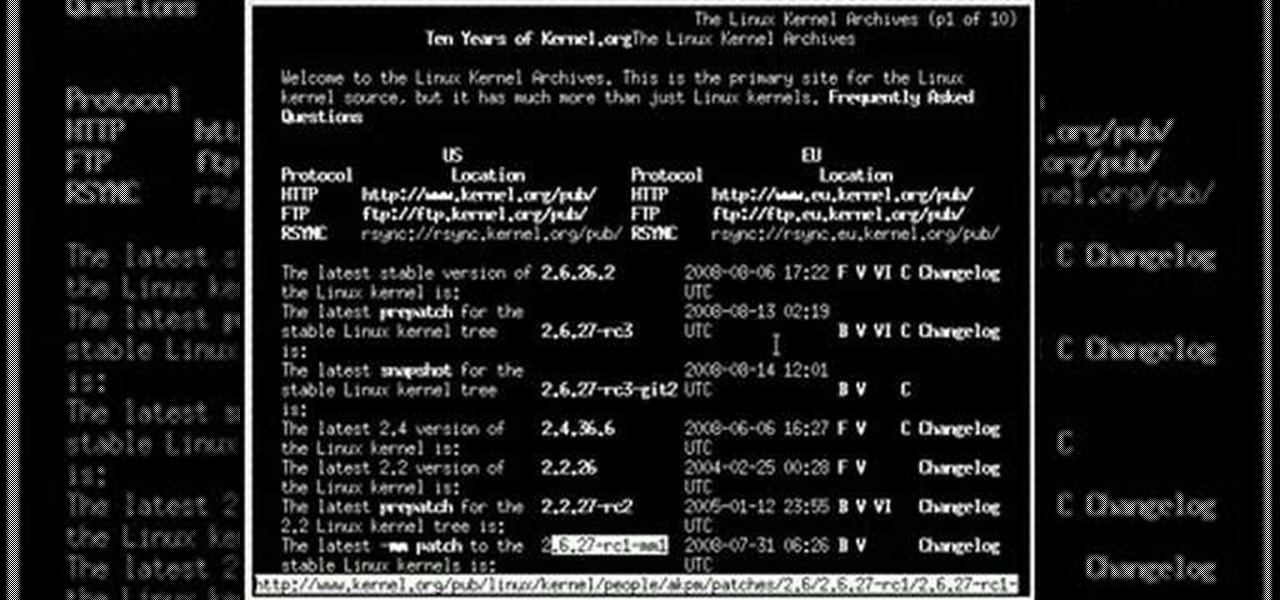
In this four-part video tutorial series, you'll learn how to compile a Linux kernel on a Debian-based system (e.g., Ubuntu). You'll learn two separate methods for kernel compilation, both (1) how to make the kernel into a Debian package, which can be handy if you're using a package manager and (2) how to install the kernel manually with make and make install. Take a look!

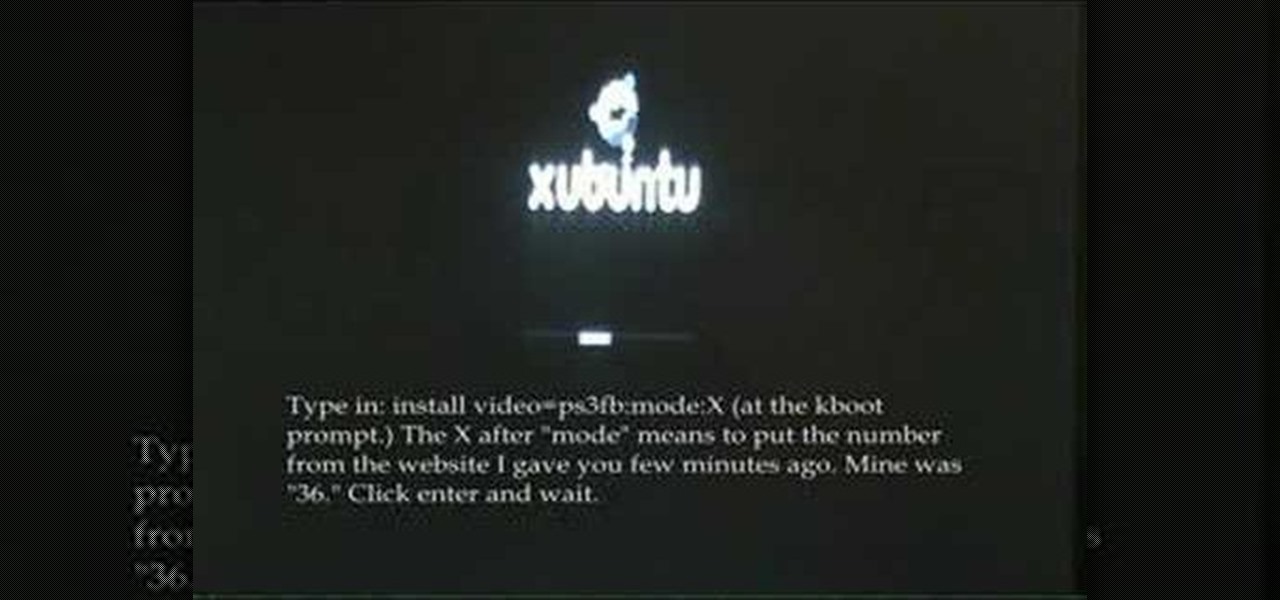
Learn how to install the Xubuntu OS on a Playstation 3. This is an alternative to installing yellow dog Linux.

New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to install cool themes on Ubuntu Linux.

If you need to scan a large number of domains for a specific web app vulnerability, Dorkbot may be the tool for you. Dorkbot uses search engines to locate dorks and then scan potentially vulnerable apps with a scanner module.

NMAP is an essential tool in any hacker's arsenal. Originally written by Gordon Lyon aka Fydor, it's used to locate hosts and services and create a map of the network. NMAP has always been an incredibly powerful tool, but with it's newest release, which dropped mid-November of last year, they've really out done themselves.

Welcome back, my tenderfoot hackers! Recently, Microsoft released a new patch (September 8, 2015) to close another vulnerability in their Windows Vista, 7, 8, and 8.1 operating systems. The vulnerability in question (MS15-100) enabled an attacker to gain remote access to any of these systems using a well-crafted Media Center link (MCL) file.

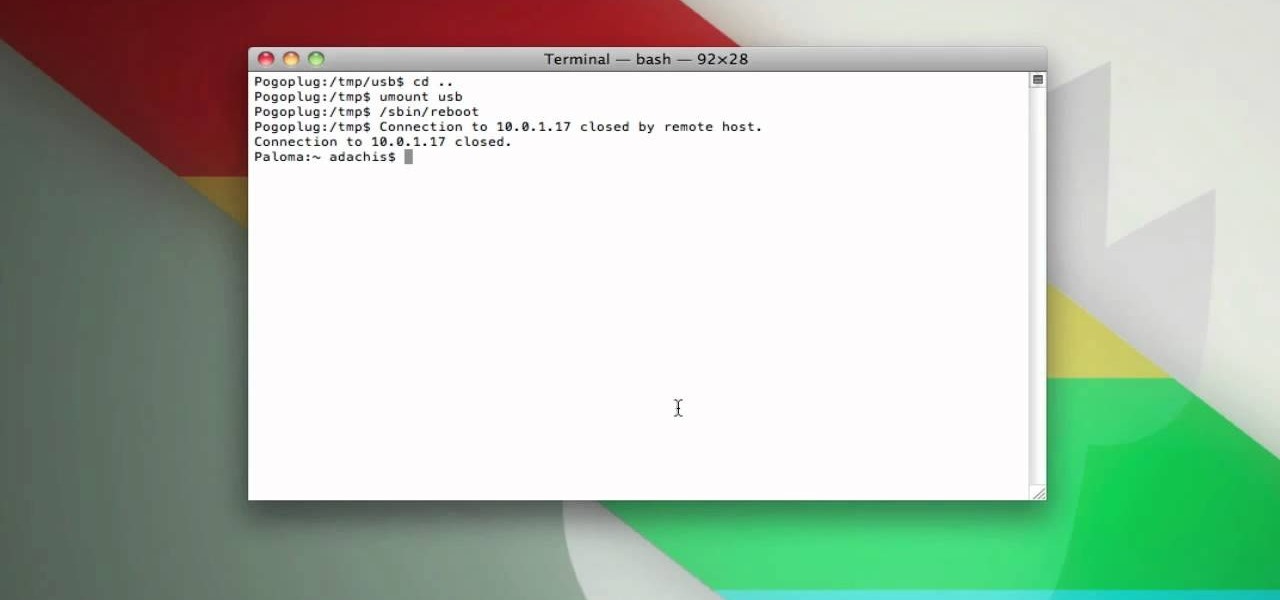
The Pogoplug is a great device for accessing your info from anywhere, but did you know that with a little bit of work you can install Apache, Linux, MySQL, and PHP on the Pogoplug and use it as a cheap, functional, Linux-friendly web server.

For those of you who have grown tired of the Playstation 3's user interface and are proficient with Linux, this video is a must-see. It demonstrates how to install Linux on your PS3 operating system without reformatting its hard drive or needing to pay for the USB keyboard for you PS3. Download the necessary file here.

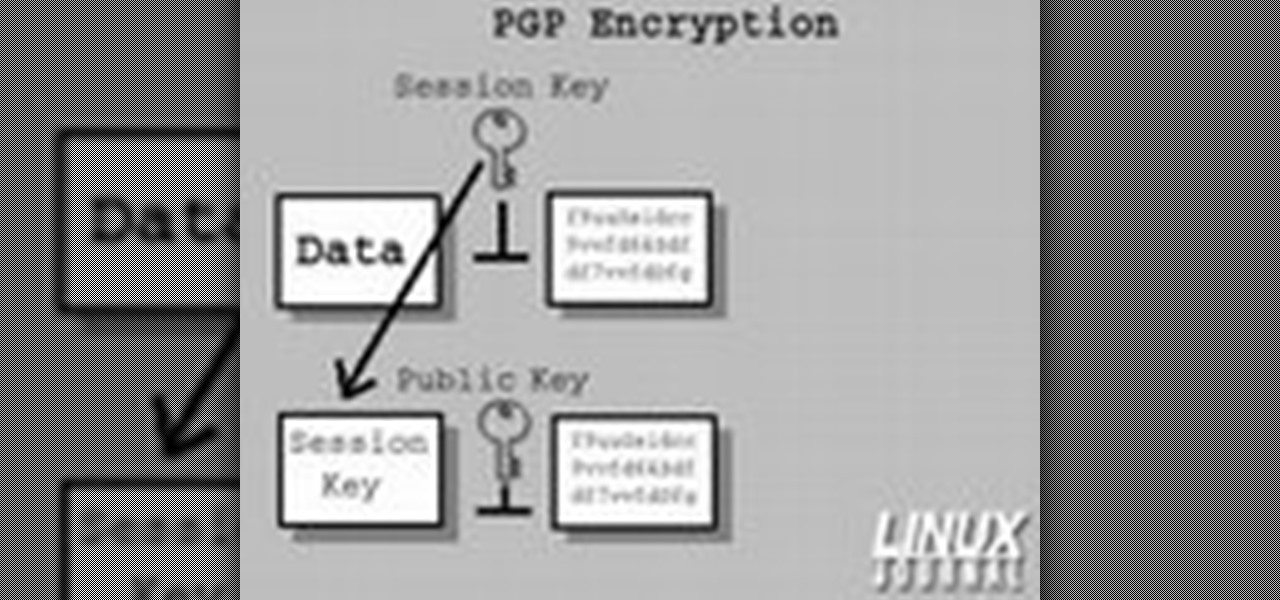
In today's time of rampant IT crimes, including identity theft, security is more important to the average computer user than ever. This tutorial, which was recorded and encoded for the Internet usingly only open source tools, demonstrates how you can use GnuPG to secure and verify data on your GNU/Linux box. Secure your Linux computer with this how-to.

In need of a general (and quick) introduction to the Ubuntu GNU/Linux distribution or just Linux more generally? Let this video be your guide. For more information, and to learn more about Ubuntu Linux, watch this home-computing how-to from the folks at Butterscotch.

Tired of Windows? Want to see what all the buzz is about Linux but you're not a computer expert? In this video, you'll learn how to use a free program called "Wubi" that lets you effortlessly install any flavor of Linux onto your Windows PC, without changing or damaging your existing Windows installation! Wubi handles all the installation and configuration for you, and allows you to dual-boot both Windows and Linux on the same computer.

This 2 part video will show you how to install Linux on the playstation 3 (PS3). Part 1 of 2 - How to Install Linux on the PS3.

A video on how to install Linux on the Playstation 3 (PS3). Part 1 of 2 - How to Install Linux on a Playstation 3.

A two-part tutorial on installing the Yellow Dog Linux operating system on a Sony Playstation 3 (PS3). With this, you can install firefox on your PS3.
Proposition 22 Prohibits the state from borrowing or taking funds used for transportation, redevelopment, or local, government projects and services. Initiative constitution amendment.

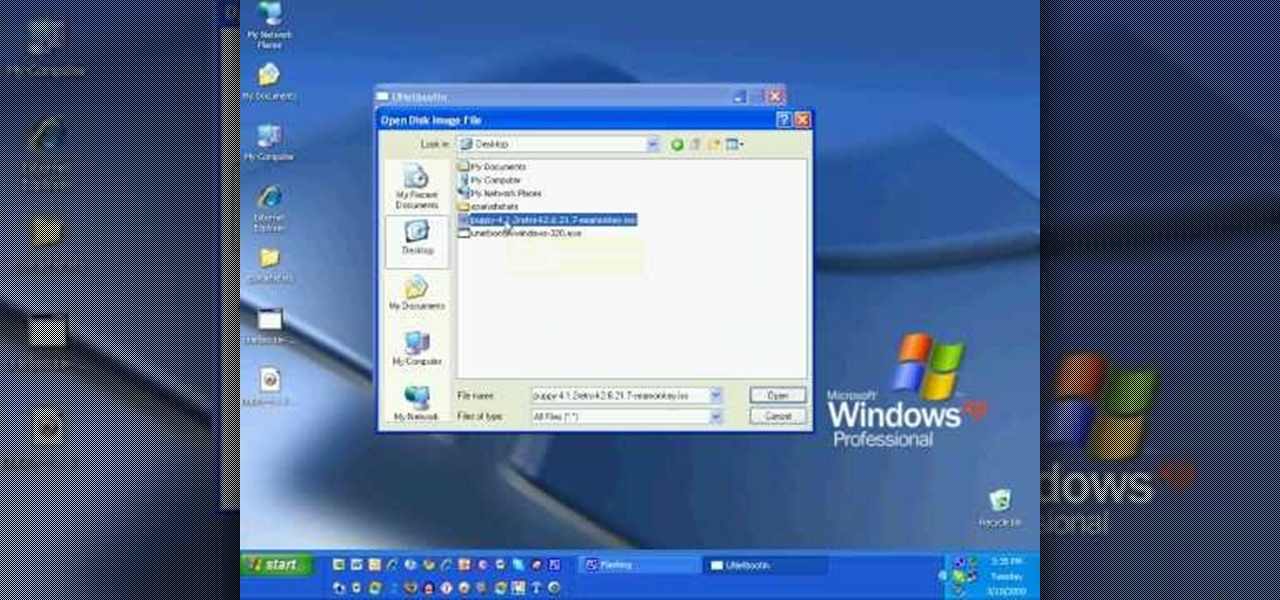
Puppy Linux is a more user friendly version of the Linux operating system. In this tutorial, learn how to use UNetbootin from Windows to install Puppy Linux on a USB thumbdrive. This will allow you to boot your PC using the thumbdrive so that you can use your new operating system.

Sneekylinux will show you how you can install small Linux on your computer. You can install Linux on you you computer and this helps your DSL run faster. Find out what programs to open to get the Linux install. You will be installing the Linux on to your hard drive so it can boot as you turn your computer on and make running your DSL faster. Take the guess work out of the process, and put DSL on your hard drive.

New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to split video files with MKVToolnix on Ubuntu Linux.

WPA-secured wireless networks, or WiFI Protected Access, is a form of internet security that secures your wireless LAN from being accessed by unauthorized users. Safer than WEP, or wireless equivalent privacy, WPA still has weaknesses that are prone to cracking - IF, that is, you know what you're doing.

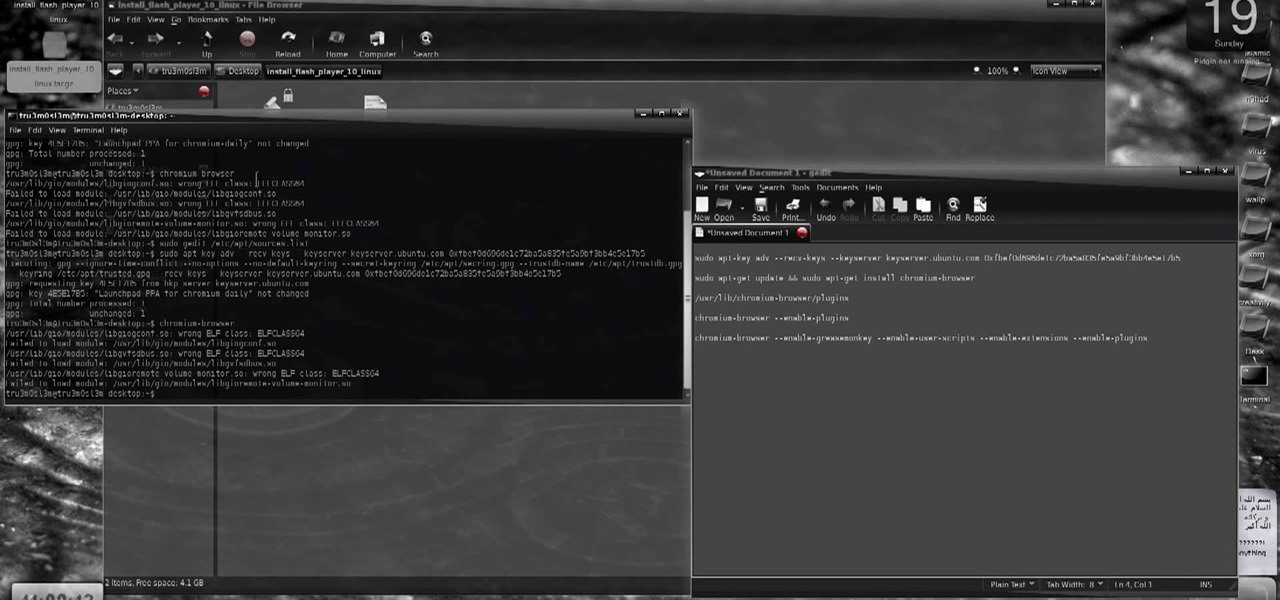
New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to install and enable Flash for Chromium on Ubuntu Linux.

Managing hard drives in Linux is crucial to understanding your system and its operation as well as understanding the system you are exploiting or conducting a forensic analysis on. Linux has numerous commands that can provide us with information, control, and management of hard drives, and in this tutorial, we will examine a number of the most important ones.

Welcome back, my greenhorn hackers, and happy New Year! Now that your heads have recovered from your New Year's Eve regaling, I'd like to grab your attention for just a moment to preview 2015 here at Null Byte. I hope you will add your comments as to what you would like to see, and I'll try to honor as many requests as I can.

Welcome back, my novice hackers! New hackers often ask me the same question: "What is the easiest platform to hack?" My response is always the same—it is not a platform, but rather a particular piece of software that is easiest to hack, which is on nearly every client-side system. That software is Adobe Flash Player.

Ação de unir o preenchimento e contorto & usar o contorno como borracha para o preenchimento. Tutorial em Português.

Interested in running Linux but are afraid of accidentally formatting your primary hard drive? One solution is to bypass your hard drive altogether and run your Linux distribution live from a CD. This three-part video tutorial series will show you how to do just that using Ubuntu.

Want to try out a Linux installation without deleting Windows? This is a brief tutorial on how to install Ubuntu linux as a dual boot with Windows. This should work with Windows 3.1, Windows 95, Windows 98, WIndows 2000, Windows ME, Windows XP, Windows 2003, and Vista.

So you've managed to get a shell on the target, but you only have measly low-level privileges. Now what? Privilege escalation is a vast field and can be one of the most rewarding yet frustrating phases of an attack. We could go the manual route, but like always, Metasploit makes it easy to perform local privilege escalation and get root with its exploit suggester module.

Welcome back, my hacker novitiates! As you know by now, the Metasploit Framework is one of my favorite hacking tools. It is capable of embedding code into a remote system and controlling it, scanning systems for recon, and fuzzing systems to find buffer overflows. Plus, all of this can be integrated into Rapid7's excellent vulnerability scanner Nexpose.

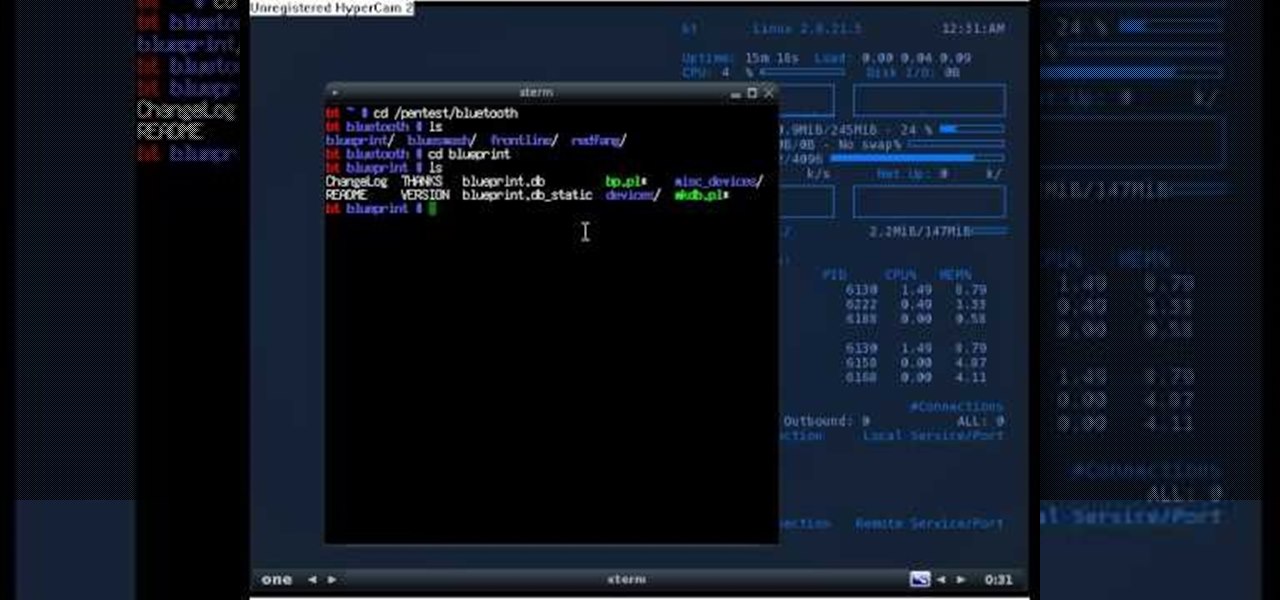
If you're new to the Bluetooth hacking world, here's a little background on using Linux BackTrack to hack a Bluetooh device: Linux Backtrack is a Live DVD device that offers security tools - like password crackers - that allow you penetrate networks.

Watching this video will allow you to learn the complete step-by-step process of uninstalling a dual-boot partition of Linux on a Windows Vista machine. The author will first walk you through uninstalling GRUB, the boot manager used while the partition with Linux was still being used. After showing how to uninstall GRUB, you will be walked through both with audio instructions and corresponding on-screen actions in windows to remove the Linux OS files from the two partitions used by the machin...

Gloobus Coverflow is a new program on Linux that lets you view all of your files without actually opening them! It's very similar to Apple's Quicklook, but is made for Linux.