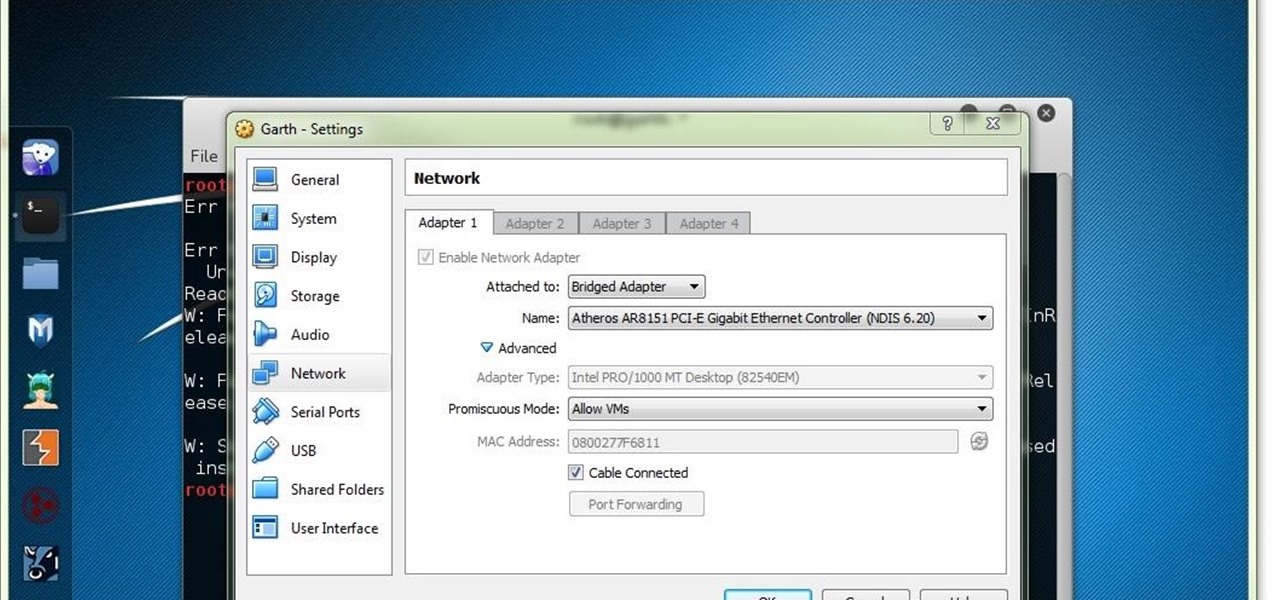
OpenVPN is the open-source VPN (Virtual Private Network) client, used over the PPTP (Point to Point Tunneling Protocol). It allows you to connect to a remote network over a secure, encrypted connection and mask your IP addresses over all ports. Since there is only one "hop," the network speeds are barely effected and are far more secure.

Downgrade Firefox 5 to Firefox 4 or any earlier versions:[Windows users] 1. Visit Link

The Ironkey is a high security thumb drive designed to provide strong AES encryption, tamper resistance and other security services. Some of the topics covered will include: How is the drive mounted without admin privileges in Windows? How is it mounted in Linux? How does the "Self Destruct" feature work? What is Secure Sessions? How is the Ironkey better than just using Truecrypt? For answers to these questions, take a look. Use the Ironkey High Security Flash Drive.

Devil2005 has created a video on compiling and configuring dhcp daemon, or dhcpd, from source. He's using the Fedora 9 distribution of Linux for the video, but the lessons learned should be applicable to other distros. For that matter, even if you are not interested in installing dhcp in this way it's still a good lesson on how to download and compile various applications from source. Compile and configure dhcpd from source in Fedora 9.
Perfect World International, also called PWI, is a hit new MMORPG in the vein of World of Warcraft or Silk Road. It's also currently able to be exploited using the free game hacking tool, Cheat Engine. This tutorial shows you how to use Cheat Engine to hack your copy of Perfect World International for more coins, a higher level and more in game resources. No cheat codes required, just open up the program and follow along with the instructions! Hack PWI (Perfect World International) using Chea...

A quick primer on how to use Gaim with Ubuntu Linux to instant message.

Hello everyone, I am Brandon Hopkins from TechHut and I am going to be showing you how to install Minecraft Texture Packs on Windows, Linux, and Mac. I will also link you to one of the best Texture Pack I have used and a website where you can download 100+ different texture packs.

Windows users have looked on with envy at Mac owners wrangling torrents with ease for years. Now, finally, a new Windows torrent client is making downloads easier, safer, and more customizable.

Hello y'all! I apologize if this question has been solved somewhere else, but I have looked around on Google, Yahoo, and Null Byte and have not been able to find any working solutions.

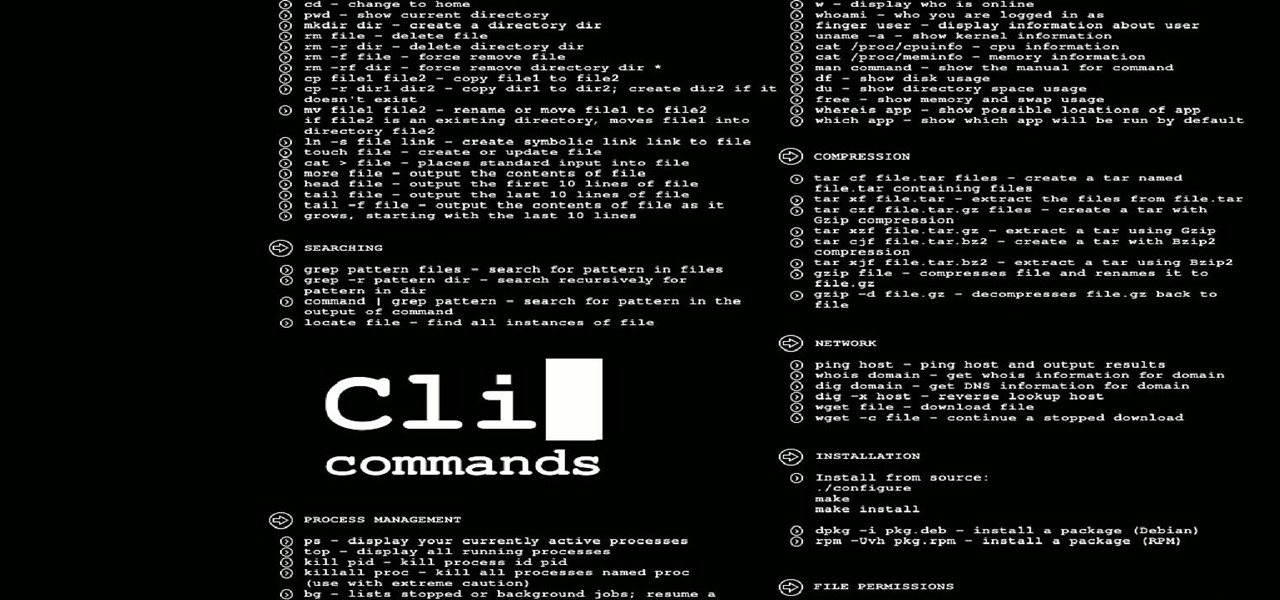
Hello everyone on null byte this is my first tutorial This Tutorial Is on Useful Lesser Known Commands on Linux

There are many tools out there for Wi-Fi hacking, but few are as integrated and well-rounded as Bettercap. Thanks to an impressively simple interface that works even over SSH, it's easy to access many of the most powerful Wi-Fi attacks available from anywhere. To capture handshakes from both attended and unattended Wi-Fi networks, we'll use two of Bettercap's modules to help us search for weak Wi-Fi passwords.

The Raspberry Pi Zero W and Pi 3 Model B+ include integrated Wi-Fi, Bluetooth Low Energy, and more than enough power to run Kali Linux. They sound like perfect all-in-one penetration testing devices, but the lack of support for monitor mode and packet injection usually meant buying a supported Wi-Fi adapter. Now, it's possible to use monitor mode on the built-in Wi-Fi chip with Nexmon.

The public leaks of NSA tools and information have led to the release of previously secret zero-day exploits such as EternalBlue, which was used in the notorious WannaCry ransomware attack. Despite multiple patches being released, many users have failed to update their systems, so many devices are still vulnerable to these now-public attacks.

While the USB Rubber Ducky is well known by hackers as a tool for quick in-person keystroke injection attacks, one of the original uses for it was automation. In this guide, I'll be going the latter, explaining how we can use it to automate Wi-Fi handshake harvesting on the Raspberry Pi without using a screen or any other input.

The sheer variety of Android devices on the market is staggering—one report suggests there are well over 24,000 distinct phones and tablets floating around out there. When you consider that each manufacturer adds a few tweaks to the Android code base here and there, that makes for a lot of software variations, which in turn means there needs to be many different root methods to match this variety.

It's been a while when the major web browsers first introduced HTTP Strict Transport Security, which made it more difficult to carry Man In The Middle (MITM) attacks (except IE, as always, which will support HSTS since Windows 10, surprised?).

Welcome back, my neophyte hackers! I have already done a few tutorials on password cracking, including ones for Linux and Windows, WEP and WPA2, and even online passwords using THC Hydra. Now, I thought it might be worthwhile to begin a series on password cracking in general. Password cracking is both an art and a science, and I hope to show you the many ways and subtleties involved.

Windows is a mess sometimes, full of problems. And your password just might be the biggest problem of all, if you've lost it, of course.

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast.

You might be sitting there thinking that I'm crazy, but the truth is you're only partially right. You can get free text messaging for life, all for a cheap, one-time fee. But, how can that be possible? An exploit in AT&T's prepaid GoPhones is the culprit behind this sweet, oh-so rare opportunity for exploitation. The exploit grants a lifetime of free texting, assuming that the company stays afloat from now until the end of time.

Last Friday's mission was to accomplish solving HackThisSite, basic mission 10. This mission teaches us how to use JavaScript to manipulate cookies on poorly coded cookie-based authorization.

Null Byte is looking for moderators! In today's Null Byte, we're hacking Netflix. As most of you know, Netflix is a subscription service that streams movies and TV shows to your devices over the internet. A common stance amongst my Xbox Live friends is that Netflix isn't worth the cost. The instant movies predominantly consist of old titles, and new movies aren't added often enough.

Uproxx recently posted a guide to making popular YouTube video, and I have to say, I'm not surprised that the models of success include web culture faves such as babies, cats and zit popping.

In this tutorial, you'll learn how to exploit weak security questions to take control of a given Yahoo! Mail account in much the same way Sarah Palin's Yahoo! account was recently "hacked." (To access Sarah Palin's account you will need, in addition to the tutorial, some manner of time travel device.) For a detailed, step-by-step reenactment of the "hack" (scare quotes very much intended), take a look. "Hack" Sarah Palin's Yahoo! Mail account.

Learn how to paint lush summer trees in watercolor using just two colors and three brushes. Then look at a complete tree portrait in a landscape setting. Here you'll find out how to 'turn on the sunlight' with the contrast between sun and shadows and how to exploit those green colors. Make sure to watch both videos! Paint summer trees in watercolor.

This video is a must-see for any Dragon Age 2 player. It will teach you how to use a small glitch to get as much money and XP as you want, quickly and easily. It has not been patched, and will allow you to cheat your way through Dragon Age 2 as much as you see fit.

They are after you from all over the globe. Looking for ways to exploit you. Ways to hurt you. Not political terrorists, but rather "info terrorists." Each month thousands of websites get hacked into and have hidden links inserted into the pages by people wanting their spam sites to rank highly in the search engines.

XSS Shell is a cross-site scripting backdoor into the victim's browser which enables an attacker to issue commands and receive responses. During a normal XSS attack an attacker only has one chance to control a victim's browser; however, the XSS Shell keeps the connection between the attacker and the victim open to allow the attacker to continuously manipulate the victim's browser. XSS Shell works by setting up an XSS Channel, an AJAX application embedded into the victim's browser, that can ob...

Apple just released iOS 13.5.1, the latest update for iPhone, on Monday, June 1. The update comes 12 days after iOS 13.5, which introduced COVID-19 exposure notifications, a Group FaceTime update, and Face ID improvements when wearing a mask.

As you all know, the first Null Byte Technical Excellence Tutorial Contest ends this coming Monday, Feb. 15, 2016. If you are working on another great article or your first article, try to complete it and submit it before midnight Pacific Standard Time (PST) to be considered in this contest. The winner of this contest will not only receive a certificate verifying the technical excellence of their tutorial, but they will also receive a free copy of the Professional version of the Exploit Pack ...

Forget keyboard commands, try out some simple mouse gestures to control your Windows computer. You can customize mouse gestures that let you take command of your PC in ways you never thought existed. If you prefer the mouse over the board, this is for you!

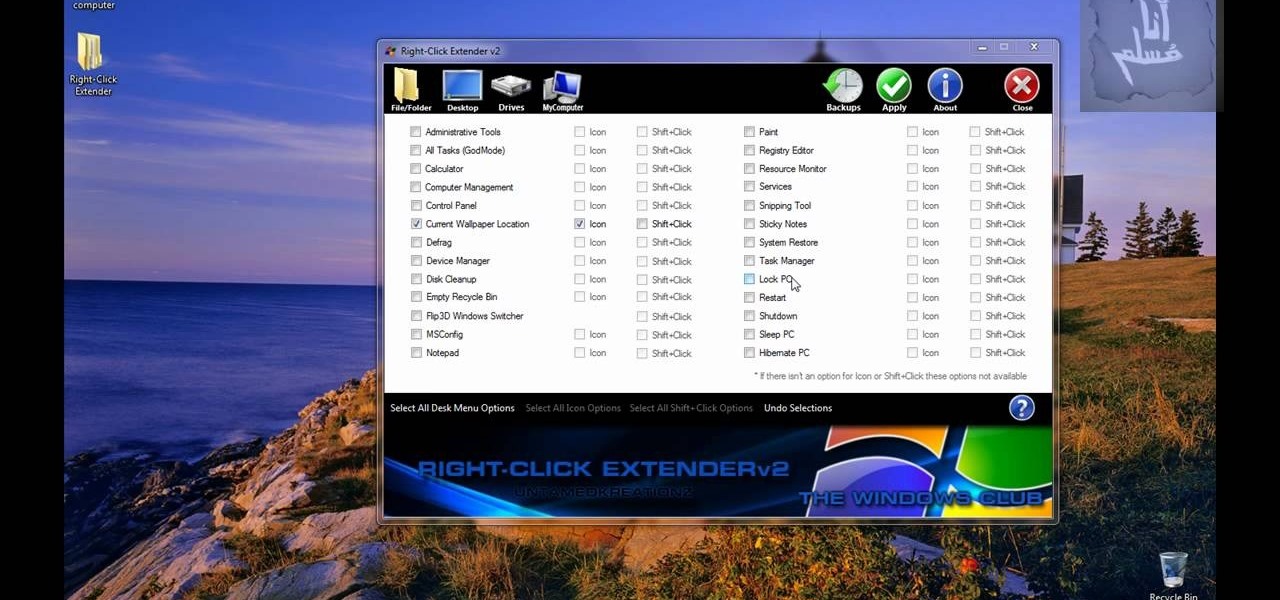
Tired of being limited with your right-click options in Microsoft Windows? There's a program that could help you out, and it's called Right-Click Extender. Insert many different additional items to the right-click context menu.

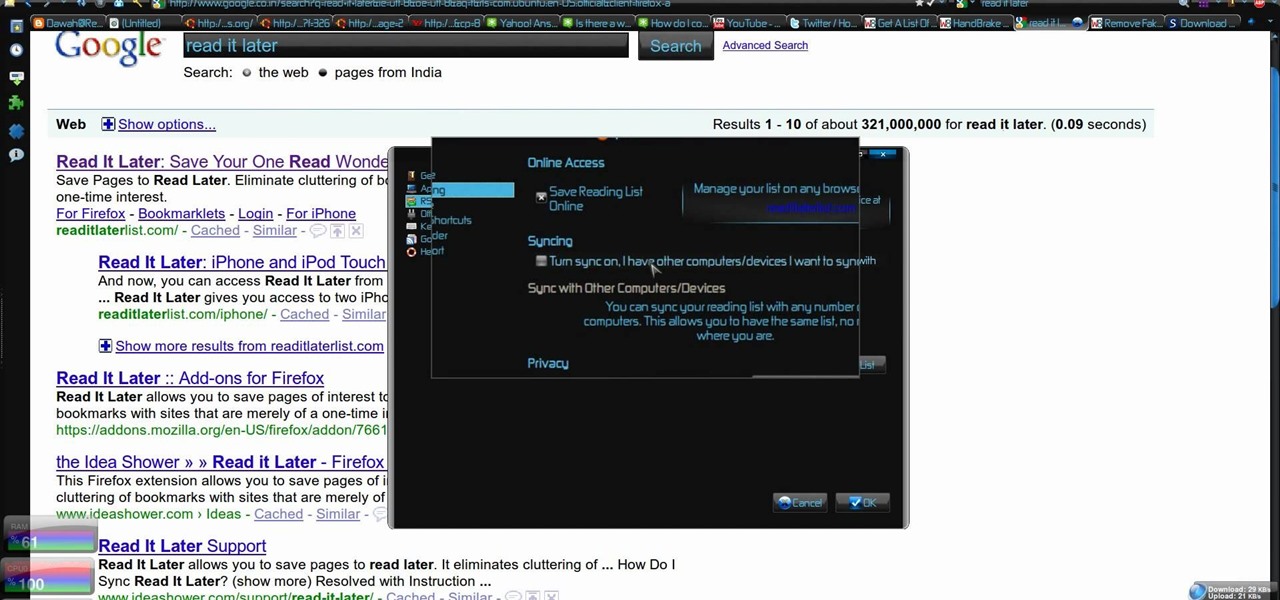
Is there another option for reading a webpage later than bookmarking? Nobody wants to bookmark something they're going to look at once and that's it. It creates clutter and confusion. But there is a way to stop that. This video tutorial will show you how to save pages in one click to read later on Firefox.

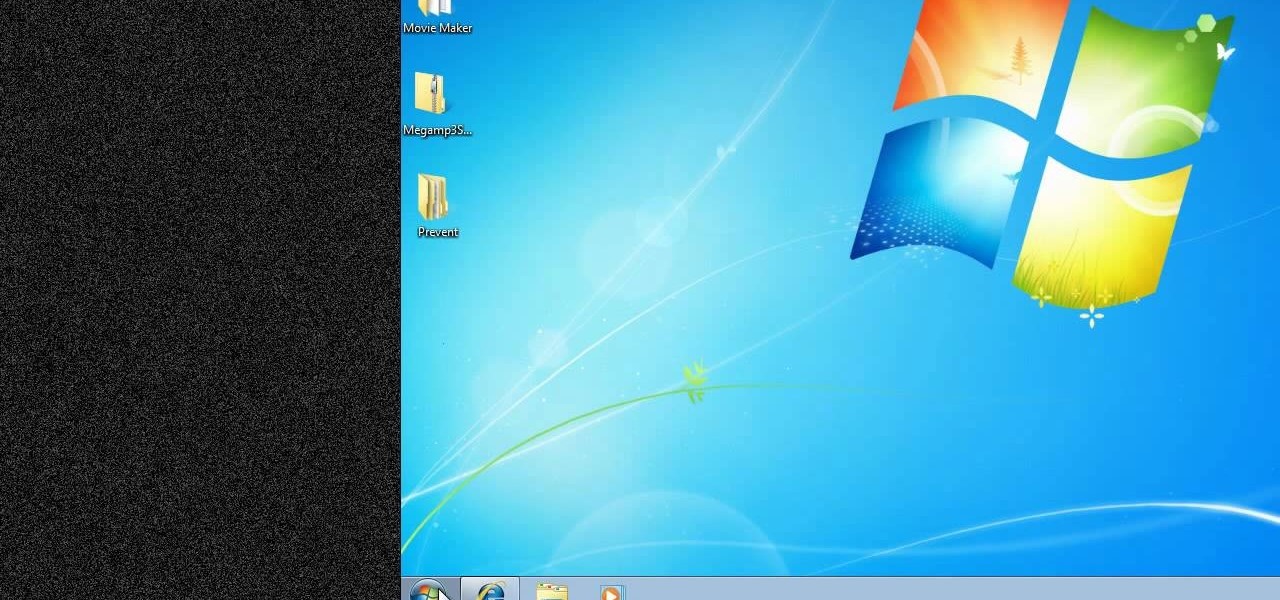
New to Windows? No problem... here's a beginner's video tutorial that will teach you how to prevent cut, paste, copy, and delete on Windows files.

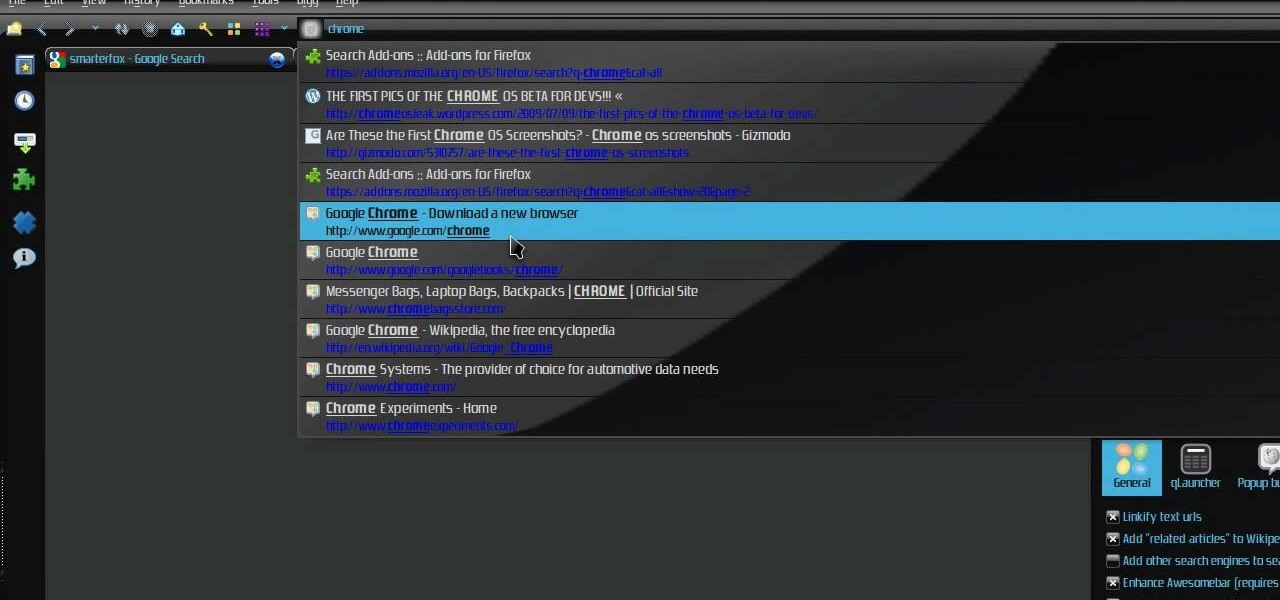
Check out this video tutorial on how to make your Firefox smarter using SmarterFox. Wikipedia sidebar SmarterFox adds a "related articles" sidebar to the left side of Wikipedia.

New to Windows? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to protect Windows from viruses without an antivirus software.

Penetration-testing frameworks can be incredibly useful since they often streamline certain processes and save time by having a lot of tools available in one place. Of course, the most popular pentesting framework is undoubtedly Metasploit, but there are many others out there that cater to particular needs. For auditing web applications and servers, Tishna comes in handy.

With the Galaxy S20, Samsung has officially removed the Bixby button from its flagships. While it was a controversial key, in its later days, it did give us the ability to launch an app or custom action at the press of a button. There's still a way to do something like that, but now, you'll have to use the power button instead.

One vital part of Android 10's new navigation system is the "QuickStep" gesture. Swipe up from the bottom of your screen, then pause. You'll see your recent apps along with a dock containing a handful of icons for quick access. This dock is provided by the phone's launcher, which means your home screen is now integrated into the multitasking UI. So what happens if you change your home screen app?

Android 11 won't be available as a beta update for Pixel devices until May 2020. Until then, the only way to try the latest Android version is by manually installing it. Usually, this means carrier models are left out since their bootloaders are locked, but there's still a way to get it done.