For years, PuTTy has reigned supreme as the way to establish a Secure Shell (SSH) connection. However, those days are numbered with the addition of the OpenSSH server and client in the Windows 10 Fall Creators Update, which brings Windows up to par with macOS and Linux's ability to use SSH natively.

With the V30, LG has really delivered an amazing smartphone that hits all the major features consumers want. Amazing camera, beautiful edge-to-edge display, great battery life, water resistance, and smooth performance — there isn't much not to like about the LG V30. Unfortunately, it does suffer from heavy bloatware thanks to the carriers. The good thing is, unlike in the past, you are not stuck with it.
Google has already issued a few updates to Android 7.0 Nougat. There aren't many headlining features, as these minor updates are mostly bug fixes and performance improvements. But there's a few security enhancements as well, so staying up-to-date with the latest patches is important for a number of reasons.

Alright, since I notcied this article was too advanced for some users, ive decided to revision this!

Welcome back, my novice hackers! You have probably heard of the Panama Papers hack by now. This was a hack of the servers at Mossack Fonseca, a major law firm in Panama. This law firm specializes in assisting the rich and powerful to hide their wealth from taxes and scrutiny by creating tax havens overseas.

Yes, I understand some people may consider this a repost. However, I have been searching for this answer for 3 weeks and after reading numerous reddit post, Kali Forums post and Null byte post I finally have gotten it to work for me. I would like to compile and share this information with you guys.

Welcome back, my greenhorn hackers! Over the years, I have written many articles here on Null Byte chronicling the many the hacks of the NSA, including the recent hack of the Juniper Networks VPN. (By the way, my speculation in that article has proven to be correct. The NSA did embed a backdoor on those devices.)

Hi everyone This is something that I should've done the first day but hey...better later than never right?

Google has finally released the next version of the world's leading operating system—Android 6.0 Marshmallow. This latest iteration isn't as much of a visual overhaul as Lollipop was, but it packs in more new functionality than almost any update before it. Awesome features like Now on Tap, granular permissions control, and a deep sleep battery-saving feature called Doze round out the highlights, but there is far more to it than that.

Apple just released the latest developer preview of OS X 10.11 El Capitan, currently in its sixth beta. While this latest build mostly deals with tiny improvements and bug fixes, it also includes a brand new breathtaking wallpaper of the El Capitan rock formation in Yosemite National Park.

Hey Everyone! Welcome to my post. We have seen a numerous GUI Tool in kali linux. Armitage, wireshark, Burpsuite etc,. Lets see an another GUI tool.

Welcome back, my tenderfoot hackers! A short while ago, I started a new series called "How to Spy on Anyone." The idea behind this series is that computer hacking is increasingly being used in espionage and cyber warfare, as well as by private detectives and law enforcement to solve cases. I am trying to demonstrate, in this series, ways that hacking is being used in these professions. For those of you who are training for those careers, I dedicate this series.

Welcome back, my greenhorn hackers! Continuing with my series on how to crack passwords, I now want to introduce you to one of the newest and best designed password crackers out there—hashcat. The beauty of hashcat is in its design, which focuses on speed and versatility. It enables us to crack multiple types of hashes, in multiple ways, very fast.

Welcome back, my budding hackers! I've written several listener guides on creating a malicious PDF or malicious Word document that would carry in it a payload with the Meterpreter, or reverse shell enabling you to own the system. One of the hurdles to using these techniques is the antivirus (AV) software on the target system. For instance, if you try to email a malicious PDF or Word doc, it's likely that the victim system will alert the victim that it contains a virus or other malware.

Welcome back, my hacker apprentices! Metasploit framework is an incredible hacking and pentesting tool that every hacker worth their salt should be conversant and capable on.

Welcome back, my fledgling hackers! The database is the hacker's "pot-of-gold," as it contains information that is very valuable to both the business and the hacker. In this, the second of my series on hacking databases, we're on the "hunt" for Microsoft's SQL Server. Although far from the most commonly used database (Oracle hold's that title), Microsoft's SQL Server is very often found in small-to-medium sized businesses. Even a few big businesses use it.

Welcome back, my greenhorn hackers. When Wi-Fi was first developed in the late 1990s, Wired Equivalent Privacy was created to give wireless communications confidentiality. WEP, as it became known, proved terribly flawed and easily cracked. You can read more about that in my beginner's guide to hacking Wi-Fi.

If you're a small guard in basketball, paradoxically you often want to get a bigger man defending you so you can exploit their lack of speed. Watch this video to learn from Deron Williams how he uses a crossover / step back move from a screen to get the big man on him, then fake him out and take a wide open jumper.

Pygame! And what you can accomplish with it. Another python article... (Blame Alex for getting me hooked on yet another coding language...)

Another great thing about Batman: Arkham City? The rogues gallery! Every great villain from Batman's history shows up in the game, and it's always awesome when they do turn up. Even Mr. Freeze, my least favorite of Batman's enemies, is kind of cool in the game (see what I did there?).

Skyrim is an enormous RPG recently released by Bethesda. After many long years of waiting (I had 1000's of hours clocked into its predecessor, Oblivion, way back in 8th grade) the game is finally out and it surpasses everyone's expectations—save for removing custom spell crafting... Why, Bethesda?

Formerly ipchains, iptables is a script-based firewall that's included with both Mac and Linux operating systems. In my opinion, it's the best firewall in existence. The only downfall is that it's complicated for some people to use due to its script-based nature. But this should be disregarded, as firewalls are nearly the entire security of your computer.

Dropbox continues to make headlines with their recent programming blunder which left the accounts of its 25 million customers wide open during a four-hour time span. During the duration, anyone in the world could access any Dropbox profile by typing in any password. And seeing as this wasn't the first security failure, everyone, including the most loyal users are considering dropping the Dropbox.
One of the most effective ways to sift out weak programs is to do market research. Take some time to study the market you are interested in by reading reports, reviews, and market studies. This should help you to determine whether or not the particular affiliate products or services you will be campaigning for is actually worth your time. A successful affiliate marketing program will be targeted at a broad population while offering products or services that are highly in demand or exclusive. ...

When i went to class today, a good friend asked me a question. He wanted to know what the best hacking software was to basically do everything. What i told him was this: Well there isn't an "Ultimate" tool boot there are a number of tools which deserve a "Medal." So what i'm trying to say here... What are some of the best hacking tools available right now? For starters i created a list with some of the tools.

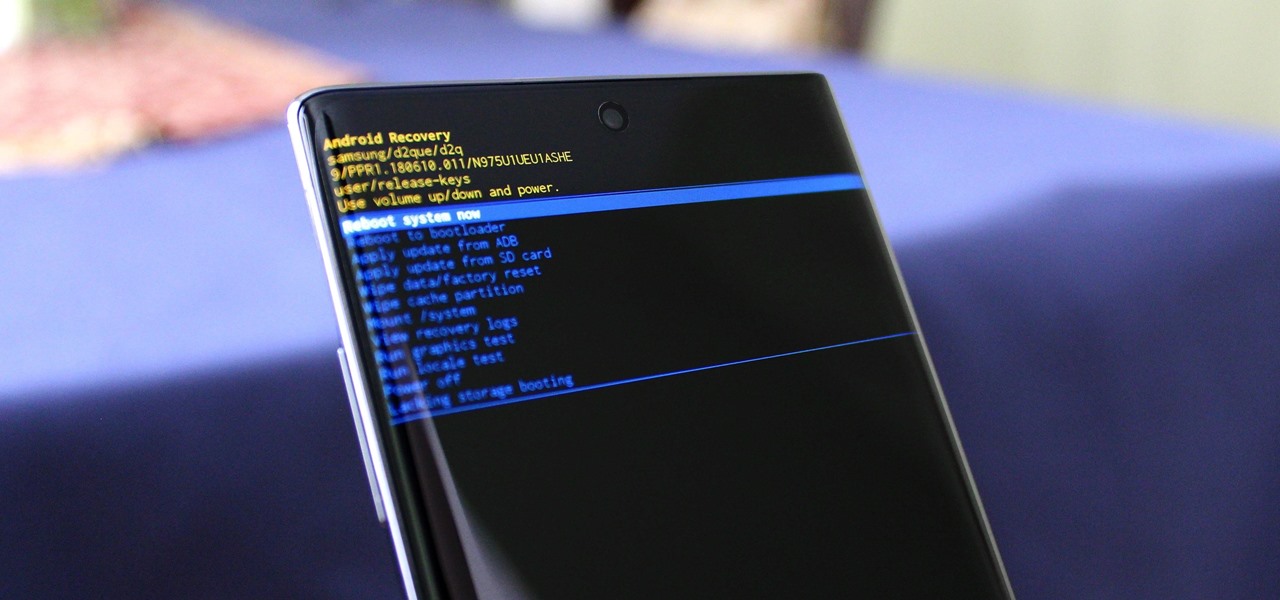
You can't call yourself an Android pro without knowing about Recovery or Download Mode. These menus are critical to do more advanced tasks on your phone, include sideloading software updates and un-bricking a device. But this year, Samsung changed the button combinations that will get you there.

Years ago, in 2013, Occipital introduced its original Structure Sensor for iOS, a mobile 3D scanning device for measuring three-dimensional objects. Soon after, in an unrelated deal, Apple acquired PrimeSense, the company that made one of the components for Occipital's scanning device.

If you've grown bored of day-to-day hacking and need a new toy to experiment with, we've compiled a list of gadgets to help you take password cracking and wireless hacking to the next level. If you're not a white hat or pentester yourself but have one to shop for, whether for a birthday, Christmas present, or other gift-giving reason, these also make great gift ideas.

Putting your Galaxy S9 in Immersive Mode lets you truly enjoy the gorgeous display that Samsung is so famous for. You can't have it set on at all times, however, so you'll still have to deal with the status and navigation bars that cut the phone's aspect ratio down to that of a standard phone. But if you're willing to dig a little deeper, there are ways to go full Immersive Mode on your S9 for good.

Coinhive, a JavaScript cryptocurrency miner, was reportedly discovered on the BlackBerry Mobile website. It was placed there by hackers who exploited a vulnerability in the site's e-commerce software that allowed them to anonymously mine cryptocurrency every time the website was viewed. There's no doubt Coinhive, an innovative mining method, is being abused and exploited by hackers in the wild.

Shodan calls itself "the search engine for internet-connected devices." With so many devices connected to the internet featuring varying levels of security, the special capabilities of this search engine mean it can provide a list of devices to test and attack. In this tutorial, we'll use Python to target specific software vulnerabilities and extract vulnerable target IP addresses from Shodan.

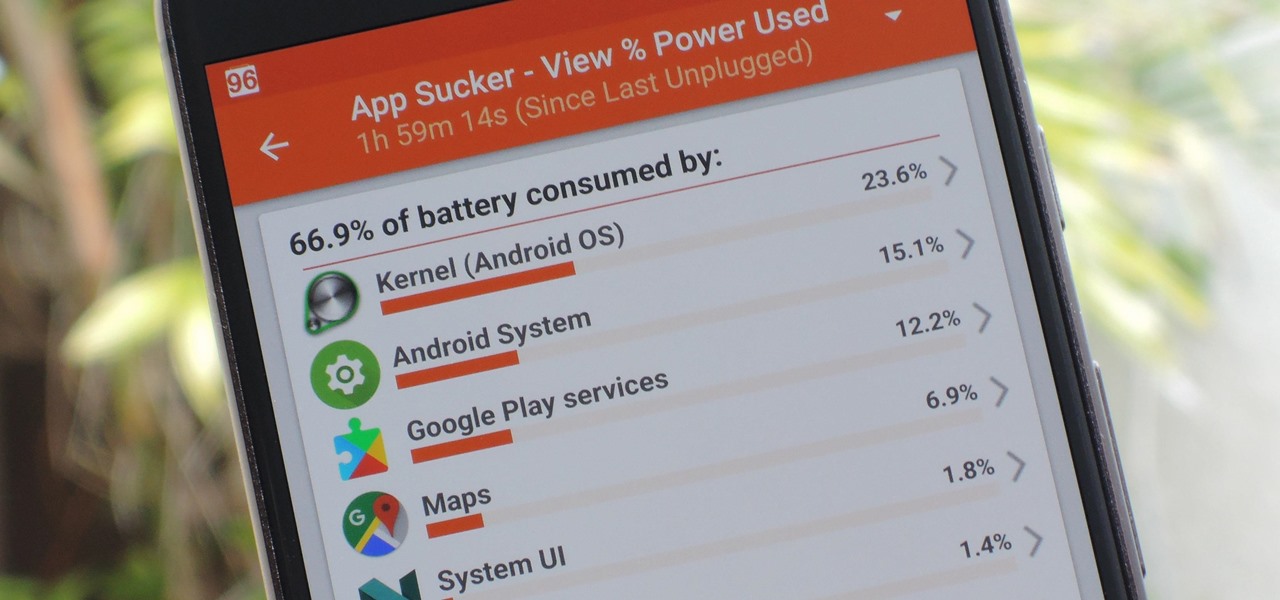
Figuring out exactly which apps on your phone are eating through resources and battery life can be a difficult task. Though some information can be found in Android's battery menu, the charts and graphs provided here pale in comparison to what's offered by the GSam app. If you configure this app properly, it provides deep insight into battery, CPU, and data usage.
Hello, I'm a new guy around here and since I'm not seeing much tutorials in C i thought of contributing with something relatively simple. This will be a short series.

This is my first article on here, it's based off of a project that I'm working on at school which is on three ways to bypass windows user password's. If all goes as planned and you all would like I'll work on part two and part three and post them as soon as I can. I do have to give credit to Puppy Monkey Baby and The Defalt, both of whom are my classmates at college and have helped me with writing this article.

Welcome my aspiring hackers and programmers! Today i will introduce you to a programming language that as a hacker you should have in your set of hacking/programming skills (except if you're only interested in web hacking/programming...then you should go learn some html or PHP instead of C#).

Greetings null-bytians. Firstly, I would like to apologize for the no images thing. I guess I can't upload them.

Do you have a file (or many files) that, in the wrong hands, may cause you trouble? Don't worry about it, because I'll show you how to wipe it (or them) from your computer in order to leave no trace behind.

Hi, everyone! Recently, I've been working on a pretty interesting and foolish project I had in mind, and here I'm bringing to all of you my findings. This guide's main aim is to document the process of building an Android kernel, specifically a CyanogenMod kernel and ROM, and modifying the kernel configuration to add special features, in this case, wireless adapter Alfa AWUS036H support, one of the most famous among Null Byters.

One of the few areas where Android lags behind iOS is a comprehensive backup solution for apps. Root tools, such as the popular Titanium Backup, are capable of backing up all of your apps and their data, but not everyone wants to root their device and potentially run into issues with voided warranties.

There are tons of good reasons that you might want to use Android on your desktop. Perhaps your favorite game is only available on Android, or maybe you use a messaging service that doesn't have a Windows companion app.