When Google introduced the Pixel 3 on October 9th, one of new additions they briefly mentioned was the Titan M security chip. While they did talk about how it will improve overall security, they didn't expand on the number of changes it brings to the Pixel 3's security. Well, they finally shared more, and it's a pretty big deal.

For years, Skype has been synonymous with video calling and messaging. However, as the industry moved toward encryption and privacy, Skype usage was discouraged by experts due to its murky encryption. To combat this, Skype has introduced true end-to-end encryption.

Passwords stored in web browsers like Google Chrome and Mozilla Firefox are a gold mine for hackers. An attacker with backdoor access to a compromised computer can easily dump and decrypt data stored in web browsers. So, you'll want to think twice before hitting "Save" next time you enter a new password.
Magic Leap has reached a major milestone in the lead-up to the launch of its Magic Leap One: Creator Edition by opening access to its developer portal and software development kit (SDK) to all developers.

When hacking into a network during a penetration test, it can sometimes be useful to create your own wireless AP simply by plugging a Pi into an available Ethernet port. With this setup, you have your own backdoor wireless connection to the network in a matter of seconds. Creating an AP is also helpful while traveling, or needing to share a connection with a group of people.

Besside-ng is the hidden gem of the Aircrack-ng suite of Wi-Fi hacking tools. When run with a wireless network adapter capable of packet injection, Besside-ng can harvest WPA handshakes from any network with an active user — and crack WEP passwords outright. Unlike many tools, it requires no special dependencies and can be run via SSH, making it easy to deploy remotely.

Google's working on a new mobile operating system called Fuchsia, and while we don't know much about how they intend to use it, we're now getting a glimpse at what the main interface will look like.

ProtonMail has long been the favorite of journalists and security-conscious professionals, with Edward Snowden the most famous example. But these days, everyone cares about anonymity, so it's no surprise that ProtonMail currently has over 2 million users. And now the service is even better.

DAQRI, a company mostly known for its odd but fun-looking industrial Smart Helmet, unveiled their new Smart Glasses product at CES 2017. Their smartglasses look like a strange attempt to answer the Microsoft HoloLens, and the price tag of $4,995 for the developer's edition reinforces that notion.

If your phone has an unlocked bootloader, you can use Fastboot commands to flash factory images. That may sound like a bunch of technical jargon, but when it comes down to it, this is the best method for updating a rooted device, fixing a bricked phone, reverting to stock, or even getting new Android updates before everyone else.

Alright, this will be my first tutorial in C. Note that this guide is written for Linux.

So yeah. Its AugustFackYou and I felt like posting today and being an active member of the community. After reading this please tell me if you have any comments on what I can do better or if this method is bad. Anyway today I will be showing you how to get root on a mac. I managed to become an administrator at my school with this and one other method.

This tutorial was written with Windows 7 in mind, but the principle applies to all versions starting from 7.

All across the web, you'll find guides on setting up various apps and mods for your Android device—but while these are certainly useful, they all seem to be working under the assumption that the reader has a certain level of knowledge about Android. For someone that's just getting started with the world's most popular mobile operating system, the basics of Android simply aren't covered as well as they should be.

After seeing the title of this post from me, you might be thinking, "Why did The Joker made another post on a topic on which we already have a nice sticky post?"

In many programs on Linux, you'll come across programs which allow you to specify additional arguments instead of just simply running the program by itself. If you've used the Kali distribution, I'm more than certain you'll have come across these with the command line tools, else if you have been following these tutorials, we have already come across three tools which also use the same technique, i.e. gcc, gdb and wc. How do we do this with C? Let's find out.

CEO's of IT companies doesn't know this because they are not a hacker. Only a true hacker can become a successful Security head officer.

Hi Folks. This is my first post. I will teach how to create a server and client python reverse shell using sockets and python language. The script i'll post here is going to be very simple, and from here you'll have the possibility to adapt to your own purpose. For example, my original script can download files, upload files, make changes to registry, create user accounts and more. I'm sure you could do it on your own too.

Hello guys, its been quite a while since my last post. (sorry for the lack of images)

Hi all, Pro Hackers/Crackers, Let's see how we can use batch for our own Protection instead of exploiting someone with it.

Google recently announced the beta release of a developer tool called ARC Welder for Chrome, which allows developers to run and test their Android apps on any computer with the Chrome browser installed.

As many of you know, I firmly believe that hacking is THE skill of the future. Although the term "hacking" often conjures up the image of a pimple-faced script kiddie in their mother's basement transfixed by a computer screen, the modern image of the hacker in 2015 is that of a professional in a modern, well-lit office, hacking and attempting to development exploits for national security purposes. As the world becomes more and more digitally-dependent and controlled, those that can find their...

Google's Chrome browser is evolving into a very powerful platform. Not only can it be used to view your favorite website or mirror tabs to your Chromecast, but now that it has an App Engine, more powerful tools can be run within Chrome.

Hi there, Elites Welcome to my 6th post, This tutorial will explain how to hack windows, using a program (No-IP)

Welcome back, my tenderfoot hackers! Now that we have begun this trip down web app hacking lane, we need to first address target reconnaissance. Like any hack, reconnaissance is critical. (Are you tired of me saying that yet?)

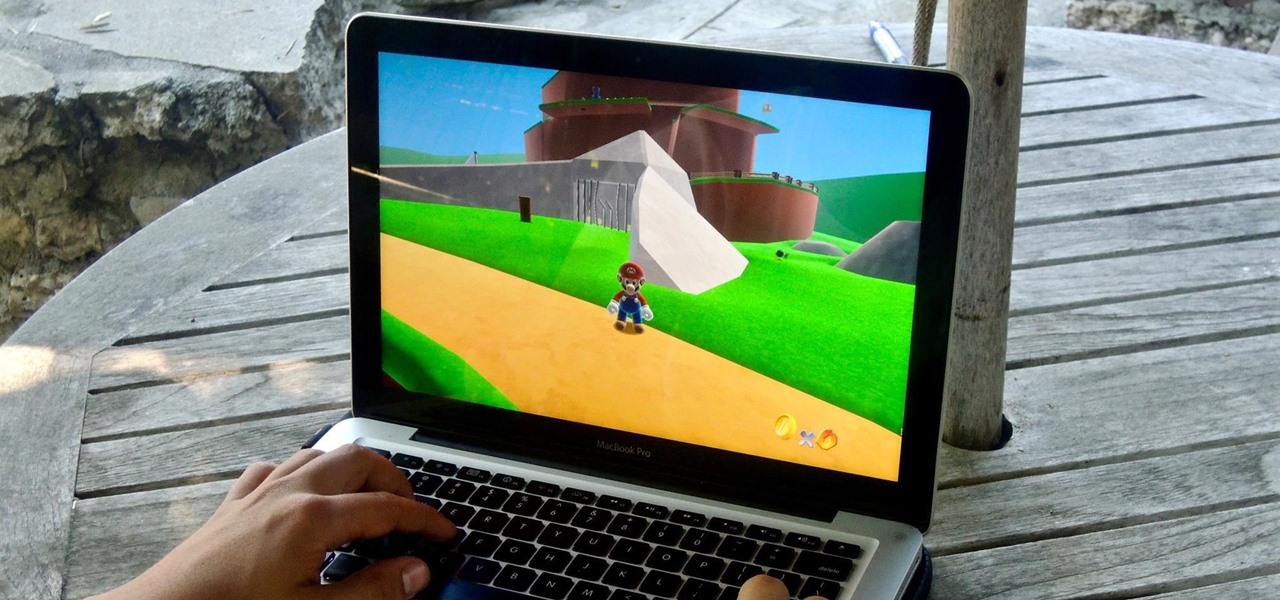
Yup, you read that right. As of now, you can actually play the first level of one of the most popular video games of all time—Super Mario 64—directly in your web browser.

Deep down, Android is a fork of Linux, which is a desktop operating system that started out as entirely command prompt-based. For that reason, many system-level tasks can still be executed within a terminal emulator app.

Google's Chrome Remote Desktop, which allows for remote access to your personal computer from your smartphone, has been out for almost a year now. Sadly, it's only been available for Android devices—until now. So, if you got an iPhone (or other iOS device), you can now access and control your computer directly from your smartphone or tablet just like with Android.

Steam is by far the biggest and best service for getting games on your Linux, Mac, or Windows PC. With their catalog containing everything from the biggest blockbusters to indie games created by one-man development teams, it's no easy task to keep track of their best values—until now.

With the release of the ARChon Runtime, many Android apps can now be run within the Chrome web browser. Minor changes must be made to existing Android APK files before they can be installed on Chrome, so the process isn't exactly as easy as pasting an Android app into a folder on your computer.

Airports are terrible germ-infested purgatories where people sit around for hours without Wi-Fi while they anxiously await to get wherever they really want to go. Unfortunately, there isn't much we can do about waiting, but this little Wi-Fi hack could help make the waiting a little less boring.

Hangouts and WhatsApp might be the preferred messaging apps for Android, but it's only a matter of time before Facebook Messenger surpasses them.

Real suffering is sitting through a thirty-second ad to watch a fifteen-second video, or watching your favorite music video in three-second fragments. Real suffering is this: “An error occurred, please try again later.” If you’re a modern human and multitask with multiple tabs while you're on YouTube, you don’t have to sacrifice your bandwidth and sanity. There's a simple way to watch YouTube ad-free and lag-free.

Popcorn Time is an app that streams movies directly from torrents on to your computer, and it's seen its fair share of publicity, being lauded as a free Netflix alternative and chastised as an illegal file-sharing network.

As you may have already heard, the worst bug in OpenSSL history went public yesterday, dubbed Heartbleed. While we can go deeper into the technical details of it later, the short version is that OpenSSL, the library used to encrypt much of the web running on Linux and Apache has been vulnerable for up to two years.

Watch out Samsung (and you too, Pebble, Sony and the still unrealized Apple), your hold on the smartwatch market is about to get a lot less firm. Announced today, Google has released Android Wear, their platform for developing smartwatches, along with a preview of the Moto 360 smartwatch from Motorola.

Welcome back, my rookie hackers! Many newbie hackers focus upon the technical aspects of hacking and fail to give enough attention to social engineering. In fact, I would say that technical hacks should ONLY be attempted if social engineering attacks fail. Why bother spending hours or days trying to hack a password if someone will simply give it to you?

Even if you have the fastest internet connection in the world, it's not going to be fast if your Android device isn't optimized to use all of the bandwidth. I have pretty fast speeds at home, but every now and then my web surfing on my Nexus 7 tablet is halted in its tracks—for seemingly no reason.

With so many cloud storage services out there, many people are starting to keep their important documents online, especially when they know they'll need to view them when they're away from their computer.