Welcome back, my fledgling hackers! It's been awhile since we did a Metasploit tutorial, and several of you have pleaded with me for more. I couldn't be happier to oblige, as it's my favorite tool. For the next several weeks, I'll intersperse some new guides that'll help expand your Metasploit skills and keep you abreast of new developments in Metasploit, so look for them in the near future.

Welcome back, my rookie hackers! Several of you have written me asking about where they can find the latest hacks, exploits, and vulnerabilities. In response, I offer you this first in a series of tutorials on finding hacks, exploits, and vulnerabilities. First up: Microsoft Security Bulletins.

In my first tutorial on Linux basics, I discussed the importance of hackers using Linux and the structure of the directory system. We also looked briefly at the cd command. In this second Linux guide, I'll spend a bit more time with changing directories, listing directories, creating files and directories, and finally, getting help. Let's open up BackTrack and getting started learning more Linux for the aspiring hacker.
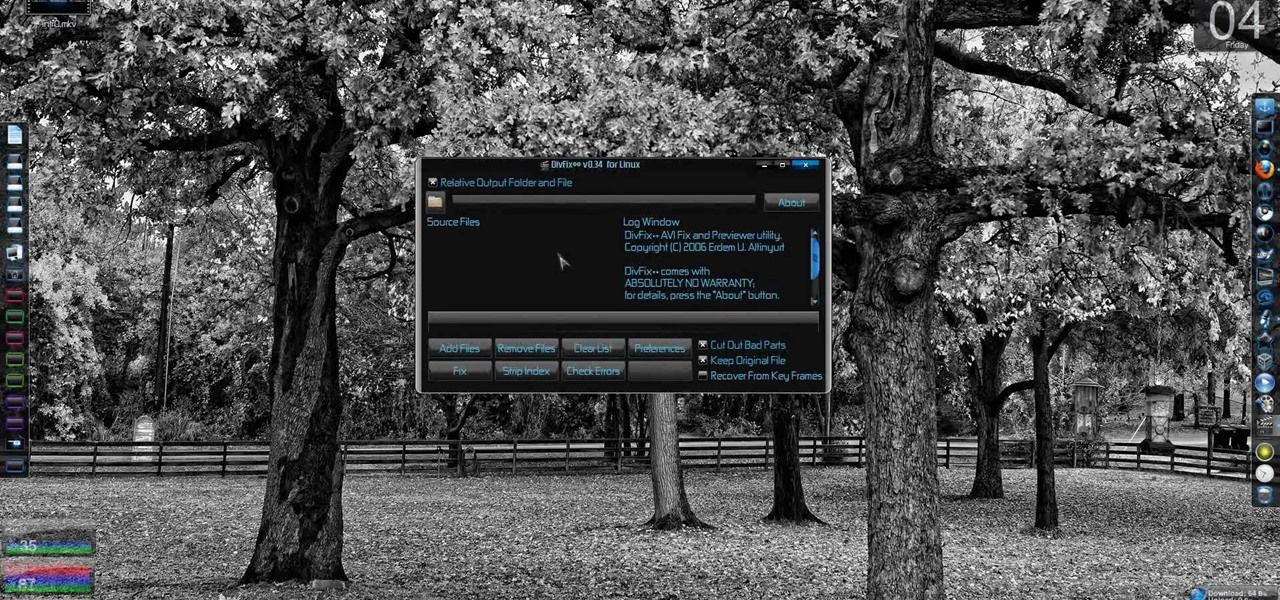
Broken AVI video files are your worst nightmare. Nobody wants to watch a video and find out it's corrupted and not working anymore. But there could be a solution on Linux. This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to fix broken AVI files with DivFix++ on Ubuntu Linux.
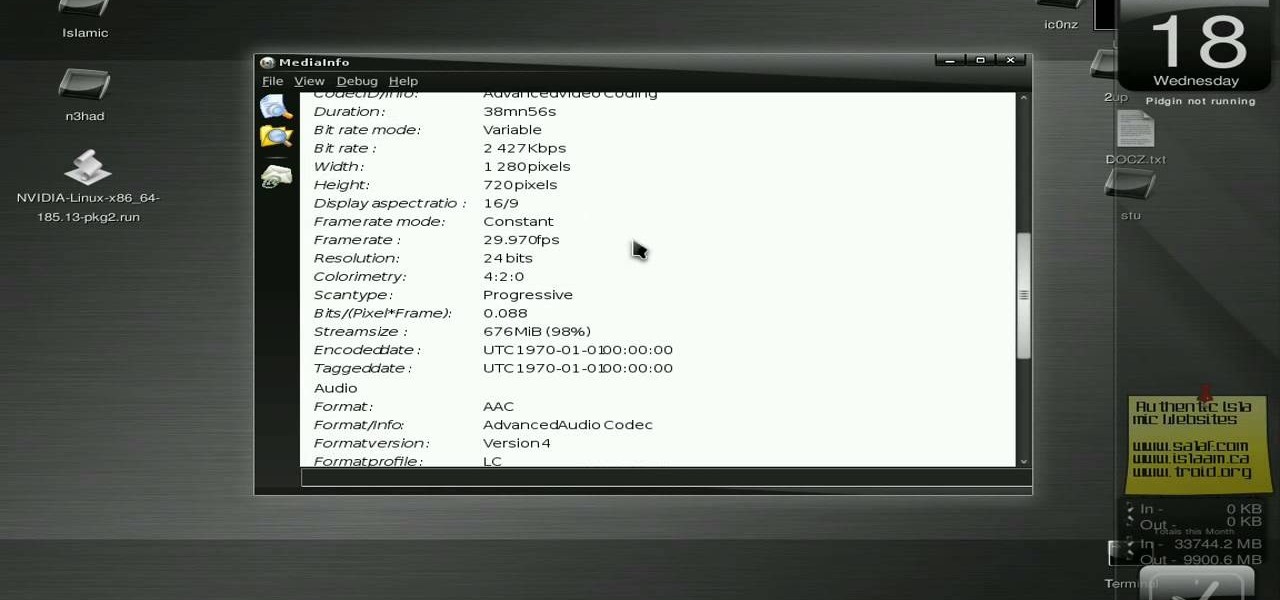
New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to install the MediaInfo GUI on Ubuntu Linux.

In this video tutorial, we learn how to install and run the Ubuntu GNU/Linux distribution on a USB flash drive. For more information, including a complete demonstration and detailed, step-by-step instructions, watch this how-to from the folks at CNET TV.

Linuxjournalonline teaches you how to use GRUB to dual-boot Linux and another operating system. You need to go to etc/default/grub and edit that file. Here you can configure the time it needs to start booting a system and what OS to boot. You need to be root to edit this configuration file. Don't forget to run update-grub to force an update of grub.cfg. And this is the end of the short process needed to configure Grub 2 for Linux.

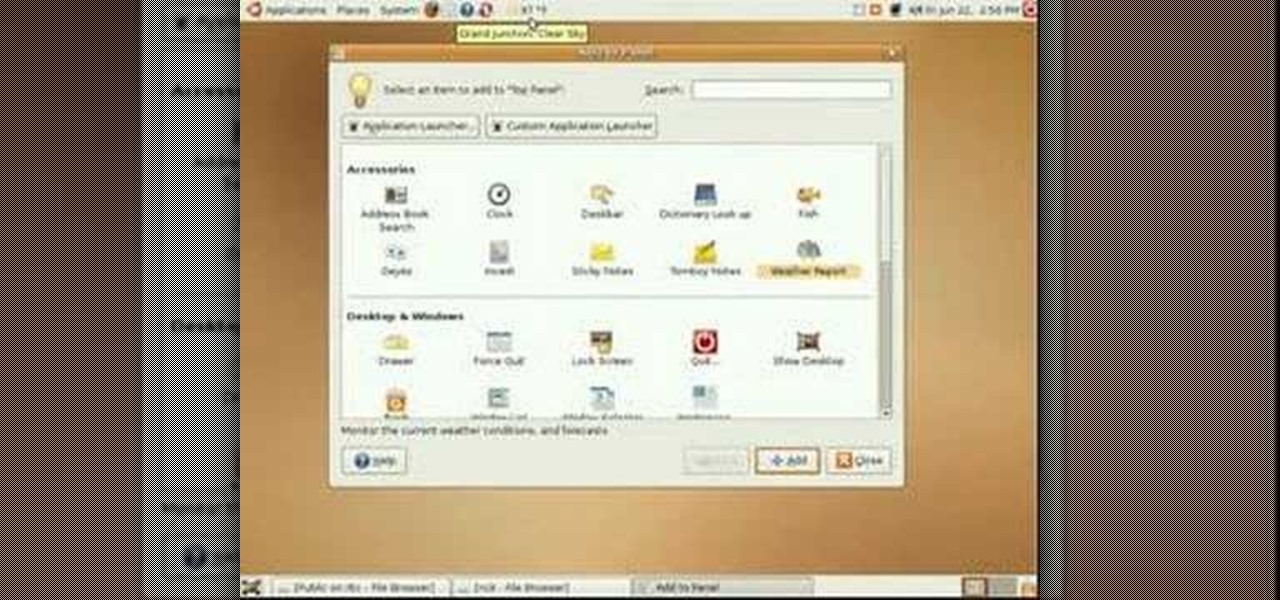
Ubuntu Linux offers panels that you can create and customize to launch your most commonly used programs and applications quickly and with ease. Ubuntu panels and the applications launcher are found at the top of your screen–at least initially. This video tutorial offers step-by-step instructions for customizing your own Ubuntu panels. For more information on using panels within Ubuntu Linux, take a look!

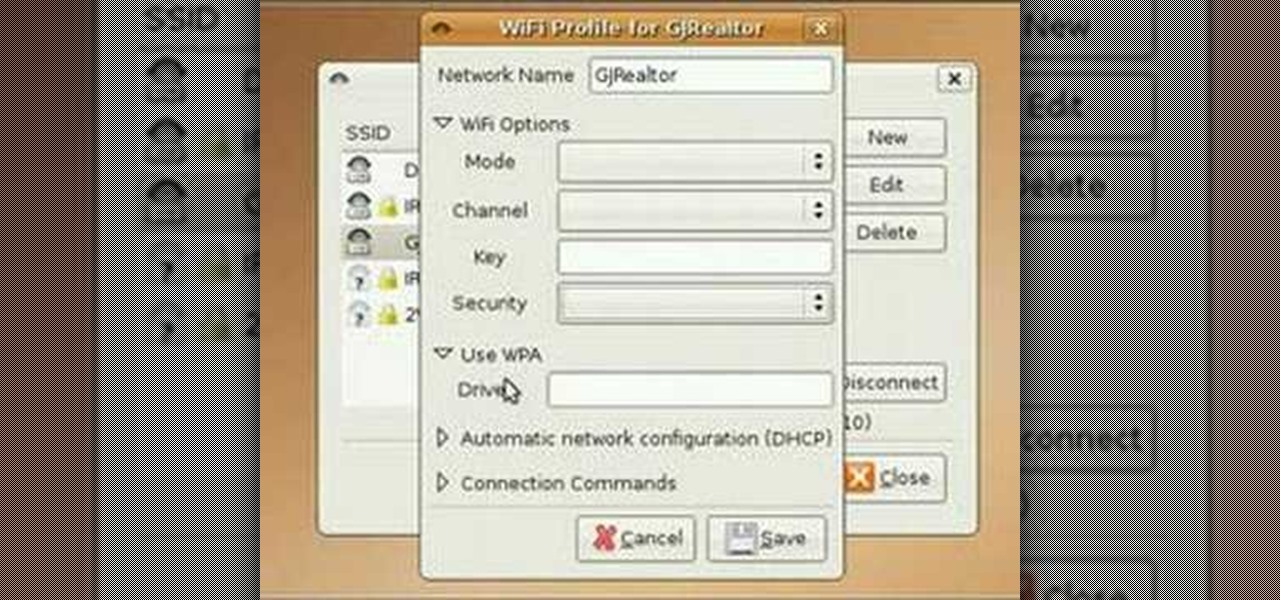
In this video tutorial, you'll learn how to use the WiFi Radar application to find wireless networks while running the Ubuntu Linux distribution. For more, and to get started finding and using wireless networks in Ubuntu for yourself, take a look!

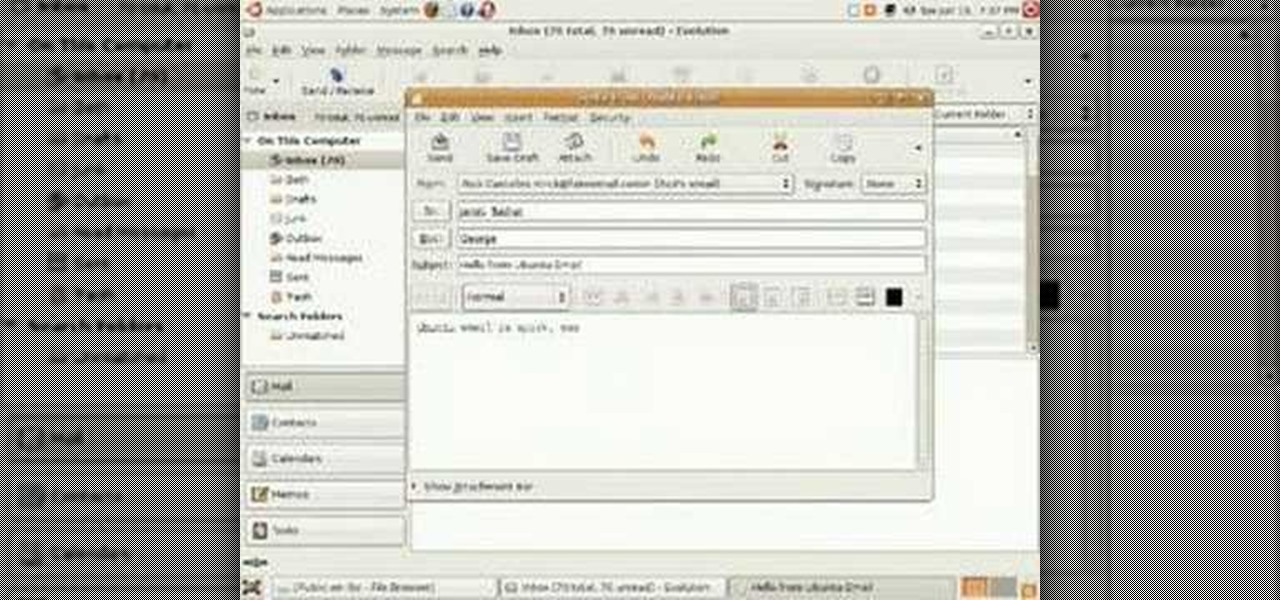
Sending email with the Evolution client in Ubuntu Linux is much the same as with any other email program. In addition to offering step-by-step instructions for the setup and use of Evolution, this Ubuntu tutorial also will teach you how to access your address book when writing an email. For a detailed look at the Evolution email client, take a look!

Drag and drop doesn't work automatically in the Ubuntu Linux distribution. You'll need to make some settings changes to enable it. For a step-by-step look at the process to enabling drag and drop file management in Ubuntu, watch this Ubuntu tutorial.

New to the Ubuntu Linux distribution (or one of its derivatives) and looking for a way to start programs automatically when you boot up your machine? Take heart: This video tutorial will show you how to accomplish just that using your system preferences. Take a look!

New to the Ubuntu Linux distribution and interested in setting up an address book for to keep track of your contacts? In this how-to, you'll learn how to make maximum use of the address book built into the Evolution email client. Take a look!

If you're a Visual [blank] programmer heretofore intimidated by the thought of programming for the Linux operating system, take heart: this video tutorial will teach you how to visually code GUI applications with Ruby and Glade.

USB flash drives are great for moving files on and off of a linux server, but how do you do it? This quick tutorial shows you how easy it is!

The first of a two part series on setting up your linux server and network for external access through your cable modem or DSL. Covers modifying the Linux servers network setting to a static IP address.

A tutorial about why the two page resume isn't appropriate for most IT positions, and how to access a Linux server remotely and change the run level to turn off the GUI.

Get the installation CD and watch this easy step by step guide for installing the new Linux Ubuntu.

Django is a Python web framework used for rapid application development in any environment. In under 10 minutes, you can go from a bare Linux (Ubuntu) installation to a fully functional Django server.

In this tutorial, we learn how to install Linux Mint 7 in Windows Vista. Use Sun Virtual box to download the Linux Mint 7. When finished, open up the program and click the install button, then go through the install process to finish installing the Linux program. You can go through the default settings or you can choose your own. When it's finished installing, create a name and password, then choose if you want to log in automatically. When finished, you will have the operating system up, the...

Are you the type of person who gets bored easily? Then you probably tire of your PC's wallpaper after just a few days. Rather than switching it by yourself, though, you can activate a program that changes it for you.

This video is by Adrian McLaughlin, aka plasticraincoat1 on YouTube, who shows us one of the most magnificent examples of explosive polymerization ever. In the video, what appears to be about 1/2 tsp of p-nitroaniline (which is short for para-nitroaniline, which is also referred to as 4-nitroaniline) is treated with a few drops of concentrated sulfuric acid, in a ceramic dish, over a Bunsen burner flame.

Computación en la nube es un nuevo modelo de prestación de servicios de negocios y tecnología, que permite al usuario, acceder a un catálogo de servicios estandarizados, para responder a las necesidades de su negocio, de forma flexible, pagando únicamente por el consumo efectuado.

Que es el cubismo. Un movimiento artistico que es practicamente inentendible para muchos, y que tiene en Picasso, Braque y Juan Gris a sus principales exponentes.

Que es el phishing y como protegernos para que no nos roben nuestros datos.

Que son los codigos QR, el sistema que une el mundo real con el virtual para revolucionar nuestra vida.

Como funciona un horno de microondas. Es peligroso para la salud?.
Este vídeo tenta mostrar uma forma muito fácil de fazer uma correcção de cor apenas numa área da imagem, sem ser necessário o uso de seleções. Aqui usamos o Hue/Saturation, que é uma função do Photoshop para alterar toda a cor da imagem, ou apenas algumas cores.
AIDS Project Los Angeles (APLA) is a non-profit organization that offers programs and services for those living with HIV/AIDS. More information can be found in there website www.apla.org

When we think about operating systems, we tend to view them from the perspective of a user. After all, most of us have spent a substantial amount of time on our computers, and so we've become more than acquainted with the ins and outs of whatever system we have running on our personal device. But there is one operating system that, while being less commonly used on the user side, is behind a great deal of design and business technology: Linux.

Anyone who has used Linux long enough is familiar with sudo. Short for superuser do (or substitute user do, depending on who you ask), it allows users to run commands as either root or another user on the system. From a hacker's point of view, sudo is often all that stands between them and root access. We'll be exploring an older vulnerability in sudo that allows a user to run commands as root.

After gaining access to a root account, the next order of business is using that power to do something more significant. If the user passwords on the system can be obtained and cracked, an attacker can use them to pivot to other machines if the login is the same across systems. There are two tried-and-true password cracking tools that can accomplish this: John the Ripper and Hashcat.

It's always nice getting paid to do something you love. That's why Nintendo is offering all Nintendo Switch owners a chance to find vulnerabilities before another hacker beats them to it first. Depending on the vulnerability you find, Nintendo is willing to shell out rewards starting at $100, all the way to $20,000, to the first bug reporter who uncovers it.

When it comes to hacking guides, most are written from the perspective of a Linux user. There are a few outliers, but it's mainly Linux, which leads to the idea that Linux is the only OS that's viable for hacking. This couldn't be further from the truth. A properly set up Apple machine can do quite a bit of heavy lifting.

In this video tutorial, I'll show you how to remove the password from the log in screen on Linux Mint 17.2

Welcome back, my novice hackers! In this continuing series on Metasploit basics, let's next look at a module that many aspiring hackers find useful—autopwn.

I see that there are a lot of people that want to install and try the Aircrack-ng program for wireless auditing. But have problems because their Linux knowledge isn't that great. This How-To video tutorial explains step by step exactly what you have to do. No loud background music.

In this quick tutorial I will be showing you how to install java in CentOS, this method will also work for other linux distros such as Ubuntu, Debian, and Linux Mint.

In this video, we learn how to activate Linux windows without losing selected text. To avoid losing the texts, you can just click on the title bar so that the highlighted part doesn't remove. If you don't want to do this, there is an alternative. Simply mouse over the text that you have highlighted and scroll with the wheel that's on your mouse. After this, right click on the text and then you can copy what you need to. Now, you can go back to the other window you have open and paste it in, t...