In this tutorial, we learn how to use Linux: Commandline Dependencies with gdebi. First, download a Deb file then use dpackage to install the package on the command line. If this fails, you will be able to use gdebi to install all the dependencies in command mode. This will save you time from trying to figure out how to open your file any other way. When you are finished, you will be able to open you file and enjoy what's inside. If you aren't familiar with how this works, search the internet...

Want a cool text effect? It's easy in GIMP. Watch this video tutorial to learn how to create a simple neon glowing text in GIMP.
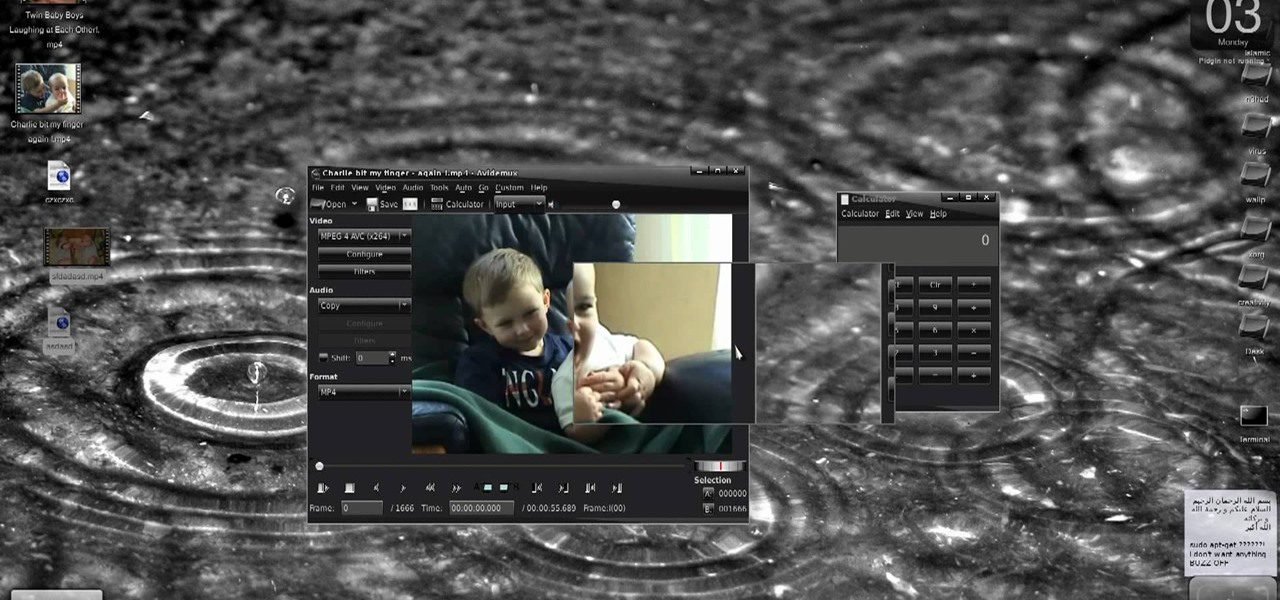
New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to create fake HD from low quality vids in Avidemux on Ubuntu.

Create a bootable USB flash drive to keep an extra OS of Windows or Ubuntu. You always want to have a copy of your Linux or Windows operating system on a separate device other than your computer. Because even if your computer or laptop is relatively new, it's very easy for some random fluke - an internal error or virus - to completely shut you down when you least expect it.
Installing two operating systems and then dual boot your machine. This is to put more than just Windows and Linux and OSX on the same machine. Another option is a virtual desktop option. This video will guide you through the steps of setting your computer up to boot two different operating systems.
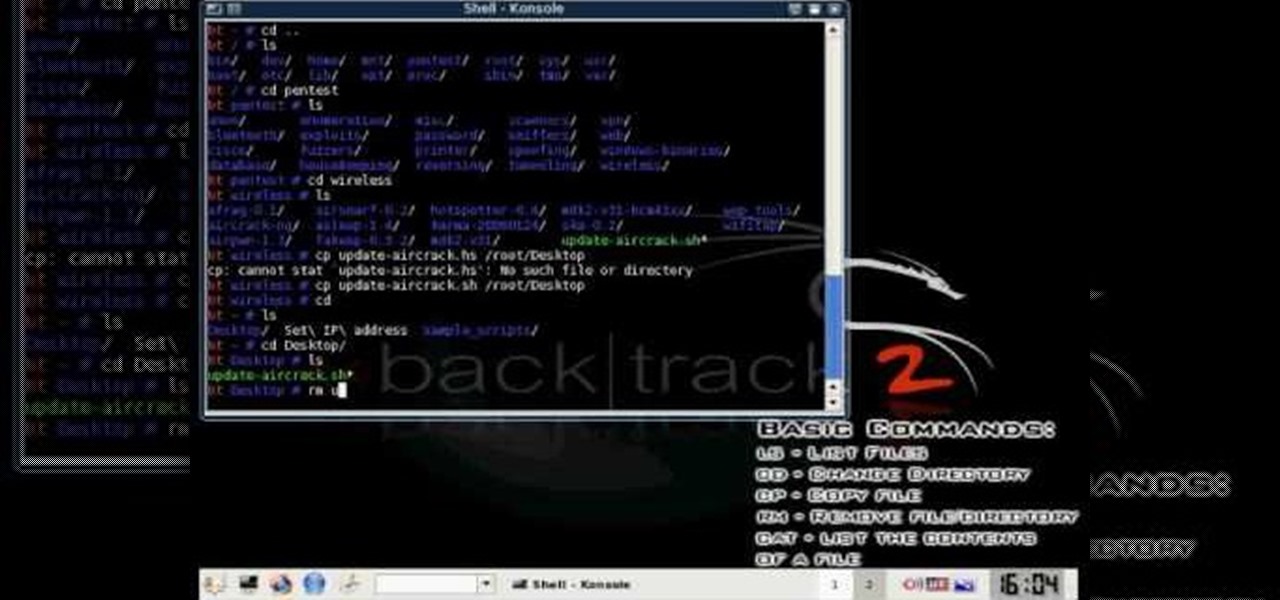
A basic tutorial from InfinityExists.com on using Backtrack - the Linux-based security software package. This tutorial covers: Where to get Backtrack 2, How to burn an .ISO file, How to boot Backtrack 2, How to login, and start the GUI interface. It also illustrates basic Linux commands, and how to set up your Network Interfaces.

The next libSSH or OpenSSH exploit may be just around the corner. Keep your SSH service out of Shodan's database before hackers find new ways to bypass the password protecting the server.

The ability to execute system commands via a vulnerable web application makes command injection a fruitful attack vector for any hacker. But while this type of vulnerability is highly prized, it can often take quite a bit of time to probe through an entire application to find these flaws. Luckily, there is a useful tool called Commix that can automate this process for us.

It's been little over a month since the official release of LG's latest flagship phone, the LG V20. Despite a few minor hiccups, the V20 has been attracting attention from all over for being an amazing phone. But like with most Android phones, there's no better feeling than rooting and taking complete ownership of it.

The Stagefright exploit, which allowed for malicious code to be embedded in files on your device, is now very real in the form of Metaphor. Developed by software research company NorthBit, Metaphor is their implementation of exploits to the Stagefright library, and when executed, can access and control data on your device.

I am very new to Null Byte but I find much of its content and community incredibly interesting. I spent quite a bit of time just chronologically going through the posts and I noticed a common theme in many of the beginner posts. Many people seem to want to know the 'secret' or a paragraph on "How to Hack" and become a hacker in a few minutes. I started off this post as a reply to a question from a beginner but thought it might be beneficial to have for those stumbling across this site.

Welcome back, my hacker novitiates! Many of you have written me that you're having difficulty installing and running Metasploit on a variety of platforms. No matter if you're using Mac, Linux, or Windows, I strongly recommend you install BackTrack as your secondary OS, a virtaulization system, or on an external drive. This particular Linux distribution has many hacking and security tools integrated—including Metasploit.

First off, I would like to say two things. One, this is not for beginners; if you don't feel that you understand this how-to at all, do not try it. Second, never ever install random software or change settings if you do not trust the source.
I assume you are on the same network with your router 1 - open a terminal window

Find which airlines Google is providing free Wi-Fi on this holiday season, fix shutter lag on digital cameras, wipe your hard drive for free, improve your Wi-Fi router performance, adjust your television and monitor for accuracy, choose the best 1080p projector, use a single server that can handle OS X, Windows & Linux simultaneously, and use the best audio encoding system for Windows Media Center and Zune.

Before you can start making awesome 3D games on your Linux computer using C++, then you're going to need to download and install these developer programs. This video lesson will show you how to download and set up OpenGL and GLUT for C++ on a computer running a Linux operating system, so you can start making 3D programs.

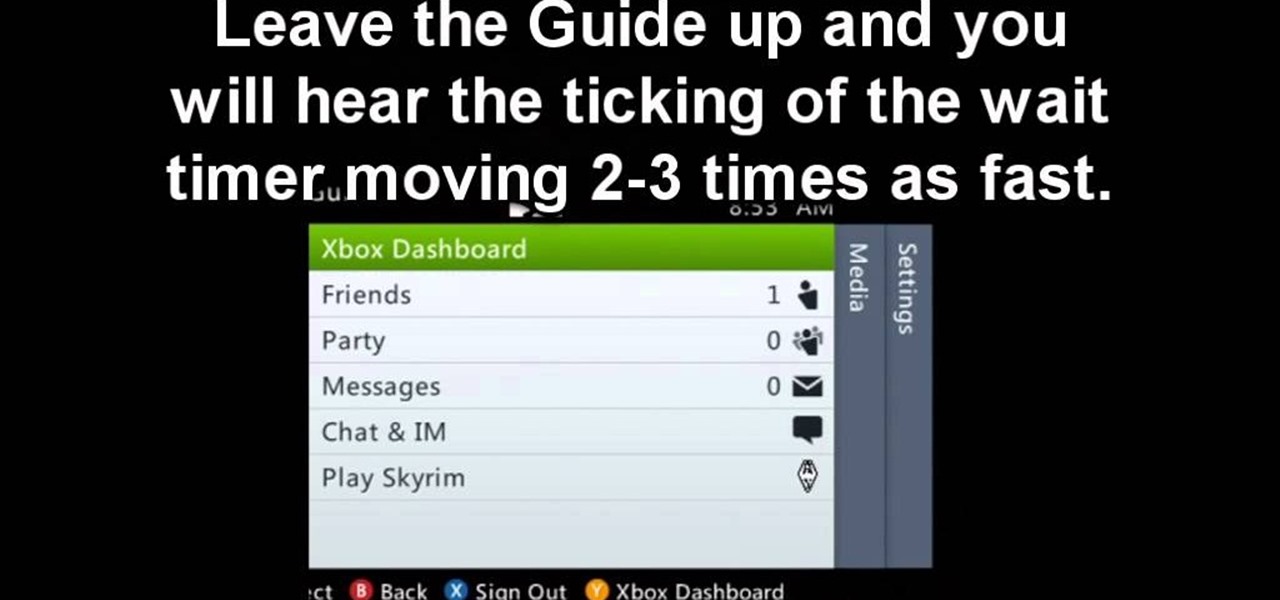
Here's a nifty little exploit for you Xbox 360 people playing The Elder Scrolls V: Skyrim. If you're tired of waiting ten seconds while you wait ten hours in-game, just bring up your Xbox guide by pushing the Xbox button on the controller. It's easy as that!

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

Hi guys. I'm here to go for level 7 now lets get it start but i apologize u all that i posted this very late but now lets rock:

No more carrying around heavy laptops and thousands of Linux Live CDs and USBs to always be ready for pentesting on the fly!

Welcome back, my greenhorn hackers! Before we attempt to exploit any target, it is wise to do proper reconnaissance. Without doing reconnaissance, you will likely be wasting your time and energy as well as risking your freedom. In previous guides, I have demonstrated multiple ways to perform reconnaissance including passive recon with Netcraft, active recon with Nmap or hping3, recon by exploiting DNS or SNMP, and many others.

How to connect to IRC using GAIM within Puppy Linux. Connect to Puppy Linux IRC with GAIM.

Thanks to Yifan Lu, it's been discovered that the operating system running on the Kindle Touch is written mostly in HTML5 and JavaScript, unlike the previous models which used Java. This is exciting, because when a device is hacked or rooted, that means homebrew programs can be run on the device, maximizing its potential and getting the most for your money.

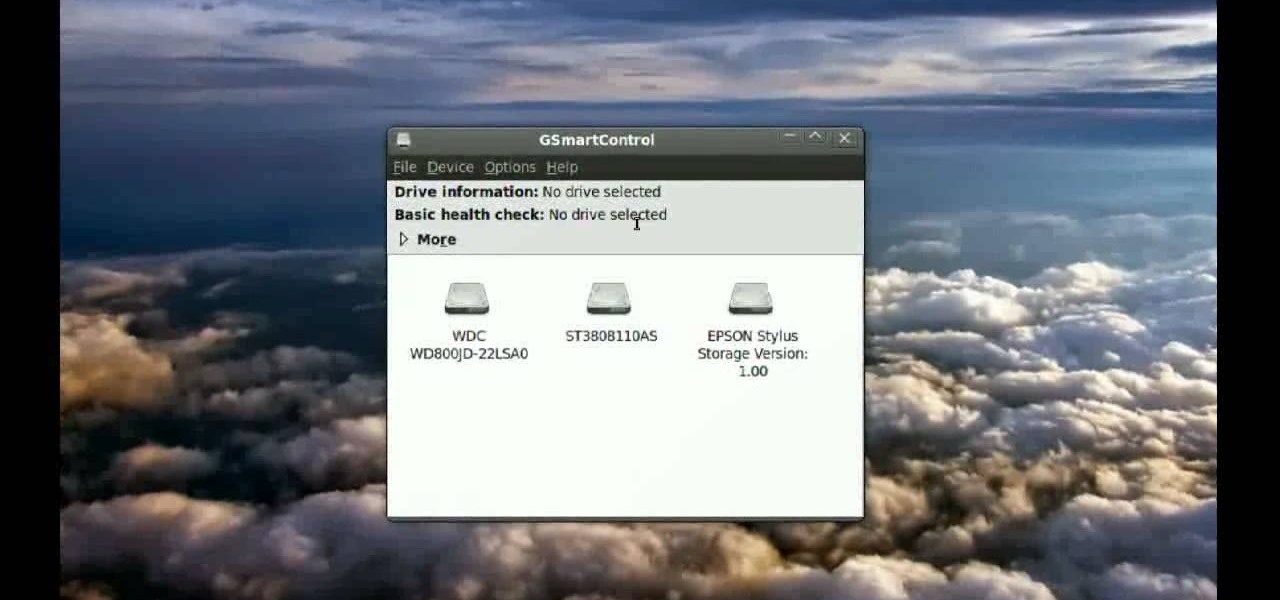
With this video, we learn how to tell if your hard drive is failing in Ubuntu Linux. If you have a failing hard drive, it will start making noises like clicking or grinding. If you hear these noises coming from your hard drive, you will need to get a new one before it fails completely and you lose all your data. You could have a failing hard drive but it doesn't make any noises. Hard drives come with a monitoring system so you can see what shape the hard drive is in. To see this, open up the ...

Shawn Powers teaches us how to install Truetype fonts on your Linux systems. First, log onto your web browser and go to Halloween Fonts. Once on this site, browse through the different types of fonts until you find one that you like. After this, save the file for the font onto your desktop. Now, install this font on your command line by first unzipping it. Go to the user share Truetype folder, then make a new custom folder. Move the file into the folder, then make sure the font and the folder...

This video tutorial in Computers & Programming category will show you how to delete temporary files in Ubuntu, Linux Mint or Debian. For this you will need the program called bleachbit. You could get it from Bleachbit Sourceforge/ or from Synaptic package manager. For synaptic manager, click on ‘package manager’ in the ‘start’ menu and log into the program by typing your password. Then search for ‘bleachbit’, download and install it. Go to ‘terminal’, type in ‘su’ and enter, then type in your...

In this video, viewers learn how to install and setup JDownloader on Ubuntu Linux Downloader is open source download manager. It simplifies downloading files from One-Click-Hosters like Rapidshare.com or Megaupload.com - not only for users with a premium account but also for users who don't pay. It offers downloading in multiple parallel streams, captcha recognition, automatically file extraction and much more. Of course, JDownloader is absolutely free of charge. This video will benefit those...

New to Audacity? Audacity is a free, open source software for recording and editing sounds. It is available for Mac OS X, Microsoft Windows, GNU/Linux, and other operating systems.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to defend your hacker space with a USB missile launcher.

In today's time of rampant information crimes, including identity theft, security is more important to the average computer user than ever. This tutorial from Linux Journal Online shows how you can use GnuPG to secure and verify data on your Linux box. (This video was created using only free and open source software tools: TightVNC, pyvnc2swf, ardour2, audacity, jackd, LAME, kolourpaint, cinelerra-cv, mjpegtools, and ffmpeg.)

Your IP (Internet Protocol) address is your unique ID on the internet. It's synonymous with your home address. Anyone in the world can contact your computer through its IP address, and send a retrieve information with it.

In the world of technology, there's often a trade-off between convenience and security. The Java Remote Method Invocation is a system where that trade-off is all too real. The ability for a program written in Java to communicate with another program remotely can greatly extend the usability of an app, but it can also open up critical vulnerabilities that allow it to be compromised by an attacker.

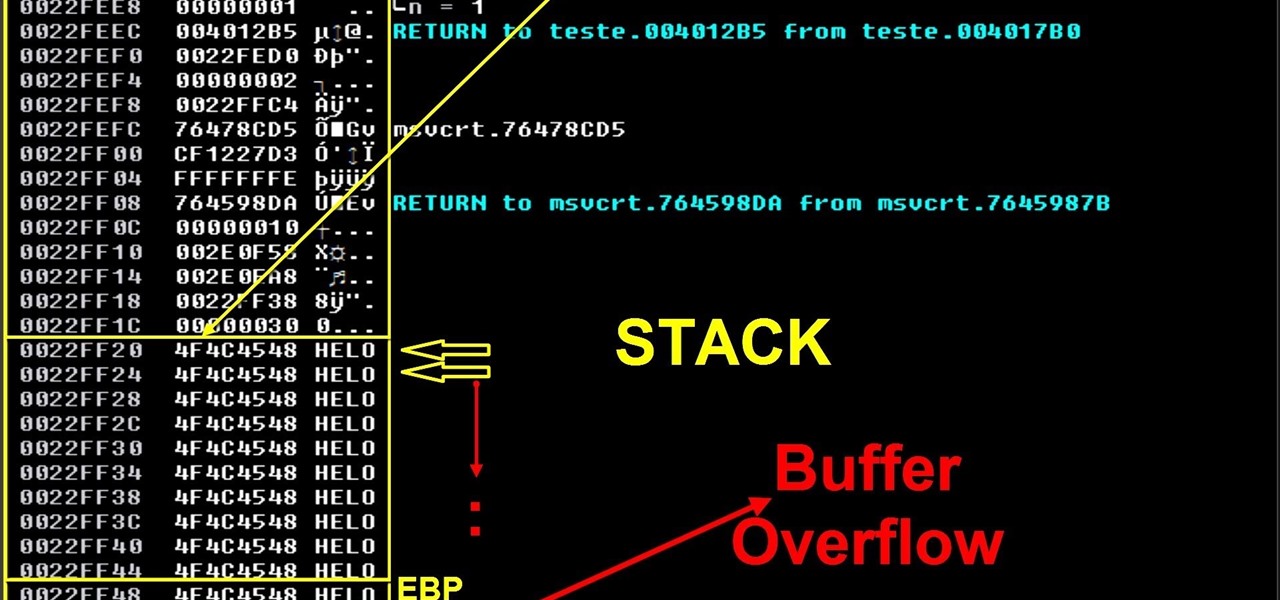
On this video I will demonstrate a simple concept of stack base overflows. This is the first part of my exploit development tutorials and after that I will demonstrate seh buffer overflow, ROP/DEP/ASLR, spraying the heap, search for bugs/think different etc.

In part one of this tutorial we found out that your English teacher is a paedophile, by using a Man in the Middle attack to intercept his internet traffic.

Many of my aspiring hackers have written to me asking the same thing. "What skills do I need to be a good hacker?"

Welcome back, my greenhorn hackers! In my continuing effort to demonstrate to you how to hack the ubiquitous Windows 7, we will going after that notoriously vulnerable Adobe Flash that is on nearly every client Windows system (you are not likely to find it on servers).

Welcome back, my budding hackers! In previous tutorials, we've looked at some of the basic commands and concepts for using Linux. Along the way, I realized that I've failed to provide you with some basic background material on the stdin, stdout, and stderror.

Welcome back, my greenhorn hackers! After the disaster that was Windows Vista and the limited and reluctant adoption of Windows 8 and 8.1, Windows 7 has become the de facto standard operating system on the desktop/client.

Welcome back, my aspiring hackers! As mentioned several times in previous Linux tutorials, nearly everything in Linux is a file, and very often they are text files. For instance, all of the configuration files in Linux are text files. To reconfigure an application in Linux, we simply need to open the configuration file, change the text file, re-save, and then restart the application and our reconfiguration is applied.