
Hack Like a Pro: Linux Basics for the Aspiring Hacker, Part 5 (Installing New Software)
Welcome back, my hacker wannabees!


Welcome back, my hacker wannabees!

Lock screen exploits are becoming increasingly common in the mobile world. Four weeks ago there was the iPhone 5 passcode bug (which just got fixed yesterday...kinda). Then there were a couple lock screen bugs on the Samsung Galaxy S3 two weeks ago.
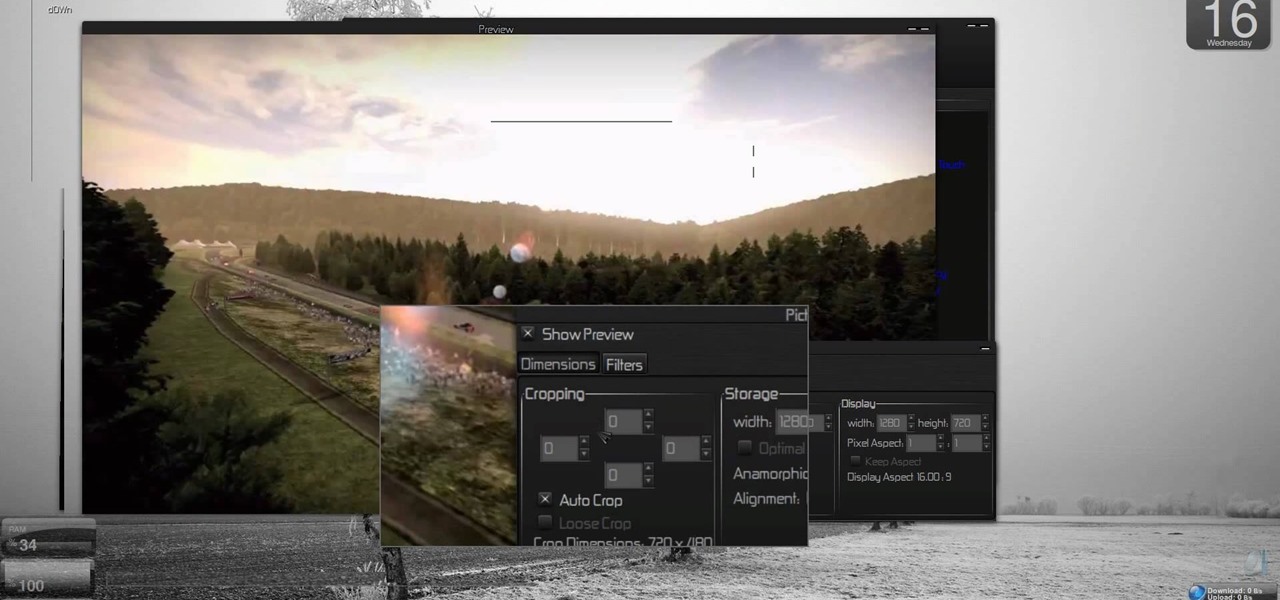
Everybody is going digital these days, so everybody has a reason for software like HandBrake. You can save your entire DVD collection on your computer in digital files, and you can convert videos into different formats. Check out this video tutorial on how to rip DVDs and convert videos on Ubuntu Linux, Windows, and Mac.
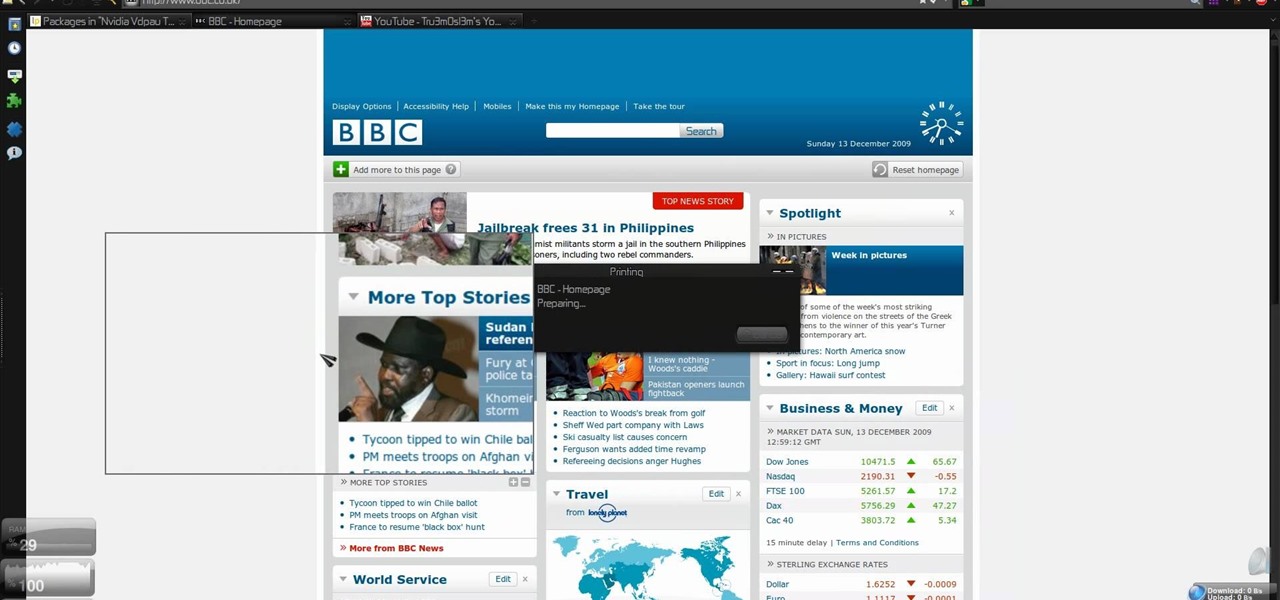
There's plenty of reasons why one would want to convert a webpage to a PDF document. And there's numerous ways on how one can convert that web page (HTML) into a PDF file. Check out this video tutorial on how to convert webpage HTML to PDF on Ubuntu Linux.

A vulnerability in the design of LiDAR components in driverless cars is far worse than anything we've seen yet outside of the CAN bus sphere — with a potentially deadly consequence if exploited.
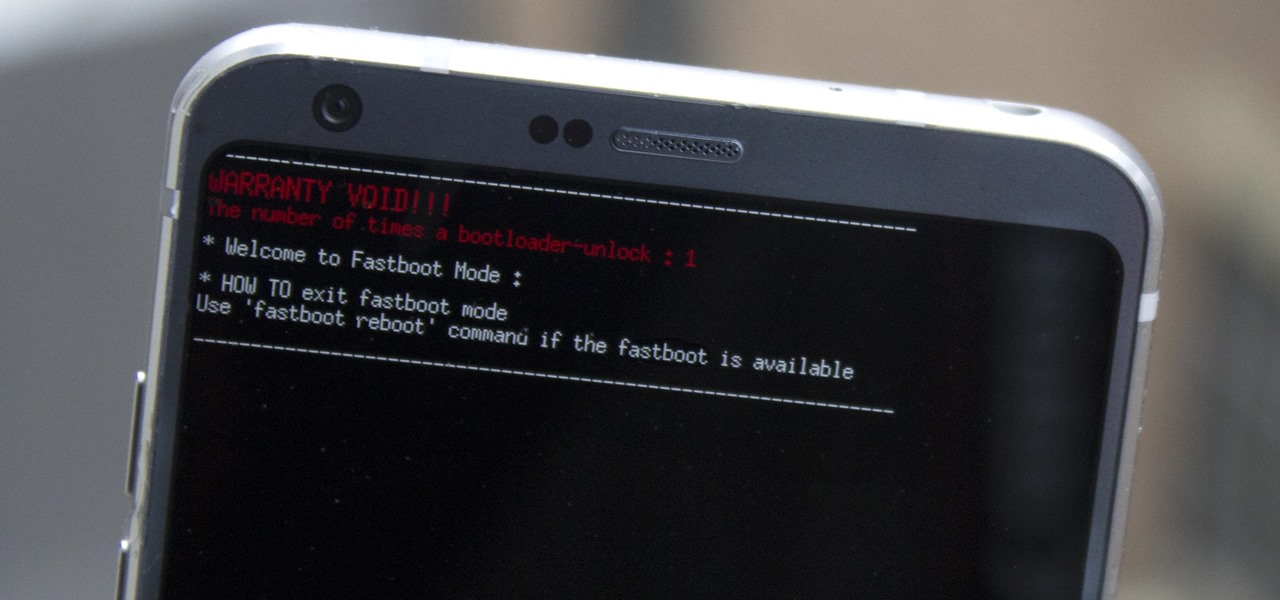
Preorders for the LG G6 have all been fulfilled, and the phone has been up for grabs at local cell phone providers for three weeks now. However, not every LG G6 was created and released equally. The T-Mobile variant of the LG G6 features an unlockable bootloader, while most other North American variants come with a tightly locked down bootloader, which effectively limits the full potential of your brand new fairly expensive phone.

In a world increasingly regulated by computers, bugs are like real-life cheat codes. They give you the power to break the rules and do good or bad without ever leaving your seat. And government agencies around the world are discovering and stockpiling unreported bugs as cyberweapons to use against anybody they see fit.

We're nearly done getting our Mac set up for hacking. If you haven't checked out previous tutorials, I'd recommend you do so first before diving right into this one.

I am back this time showing you guys how to theme your kali linux. Being true kali is good for pentesting but when it comes to looks it is lifeless , maybe the kali rolling could be an exception but even that makes you feel bored after a long time . So in this tutorial I am gonaShoe you how to theme up your kali

So you want to create a meterpreter virus, but you keep getting caught by AV. How do you create one that will go undetected? In this tutorial, I'll teach you how to code your own simple virus that will download a powershell payload from an apache webserver and execute it - bypassing antivirus.
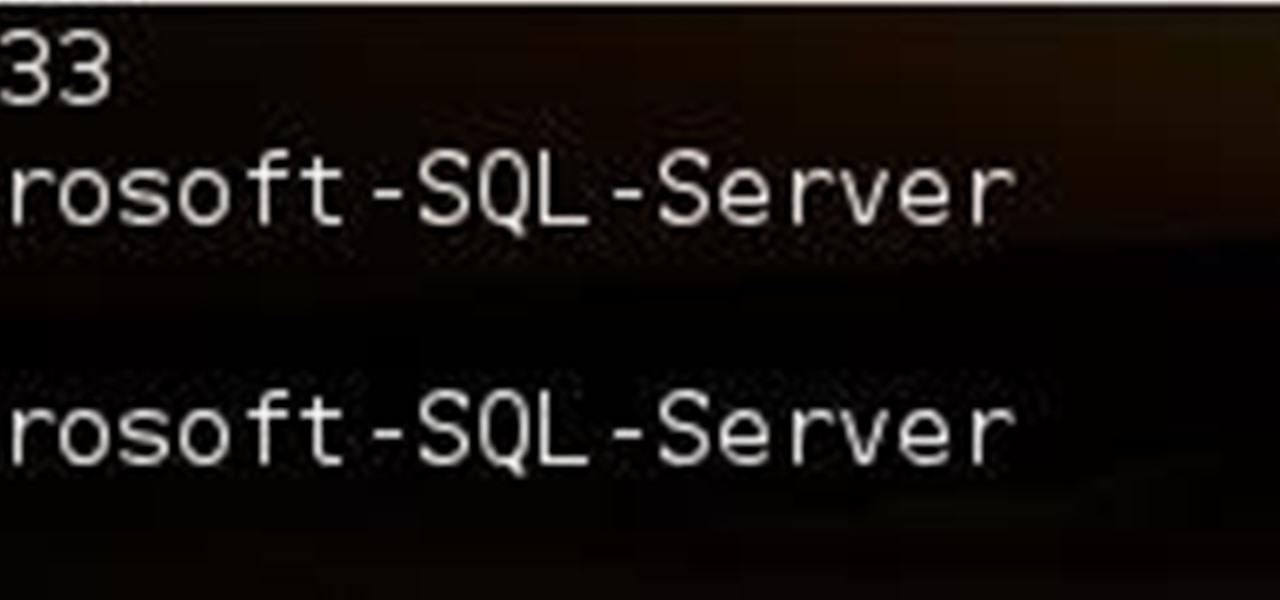
I wrote a python script that allows you to easily ask what service runs on a specific port and vice-versa. Now, I am sure that such a program already exists on our lovely linux OS's, but... I didn't think of that before I started, and haven't found it yet. So if you haven't found it yet either, maybe you'll find this of some use. It's just called getport. If I have a port number, and want to know what services run on that port, I do:
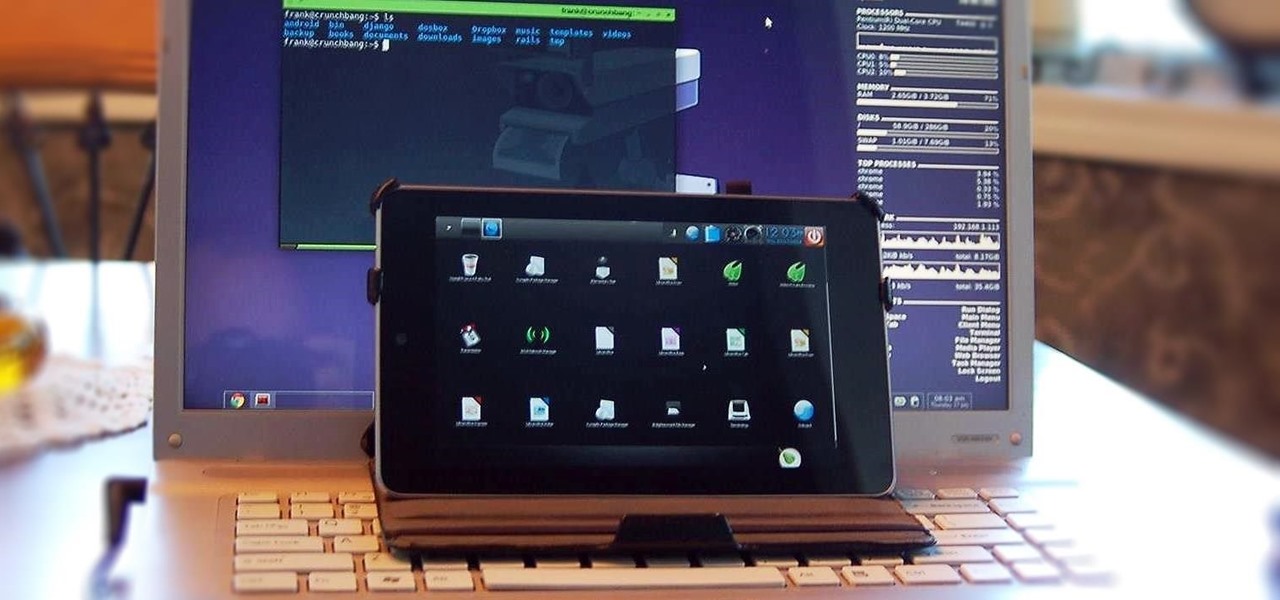
When people first learn that their Android device is capable of dual-booting different operating systems, e.g. Linux, they almost universally respond with, "That's so cool." And for those of us ambitious enough to actually try one out, we are typically filled with glee as we see Ubuntu, or something similar, boot up for the first time on our tablet or phone.

Firesheep is a packet sniffing browser exploit that can access the exposed accounts of people on Facebook and Twitter while they use public Wi-Fi connections. This video shows what steps can be taken to protect yourself against someone accessing your Facebook account.
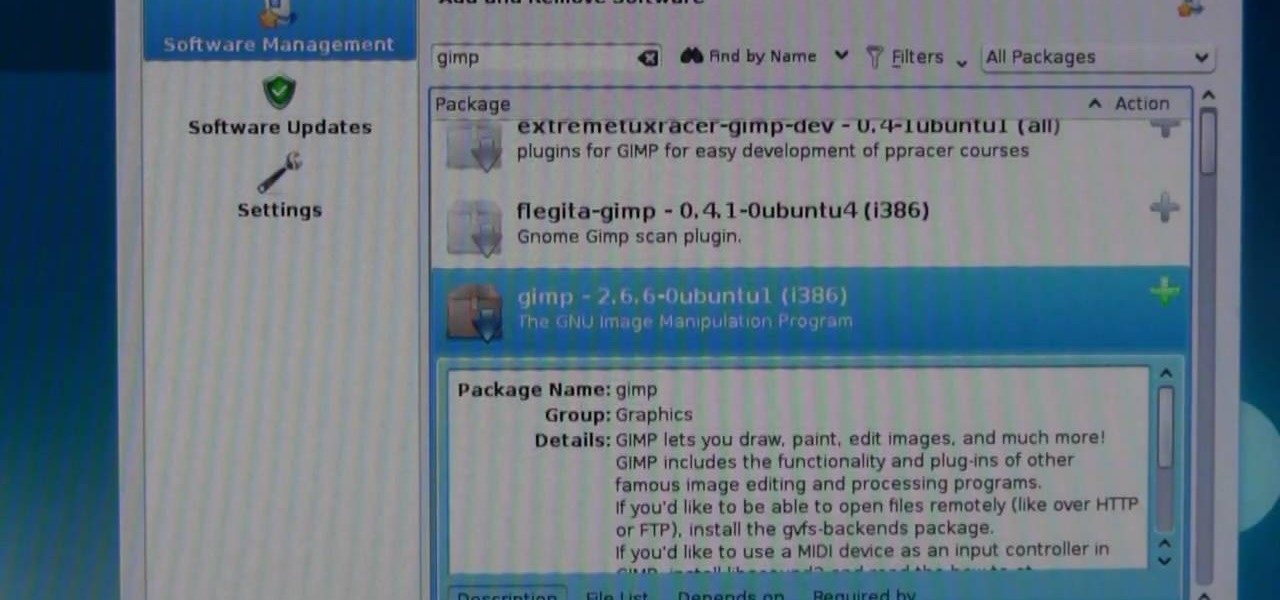
Finding Linux hard to handle after using Windows? Well this should help, here is how to install software on Linux. Start off by clicking on application launcher. Here go into applications, then into 'system' where you should find software management. In this program go straight into the settings and then edit software sources. Under 'downloadable from internet' make sure every option has a check against it. Now press the software management tab on the side. Now this is where you can get which...
Ever hear of SmillaEnlarger? It's a small graphical tool (based on QT) to resize, especially magnify bitmaps in high quality. Check out this video tutorial on how to back up and restore data easily on Ubuntu Linux.

If you want to die in style, check out this video for a tutorial on how to use the javelin to serve as a martyrdom utility!
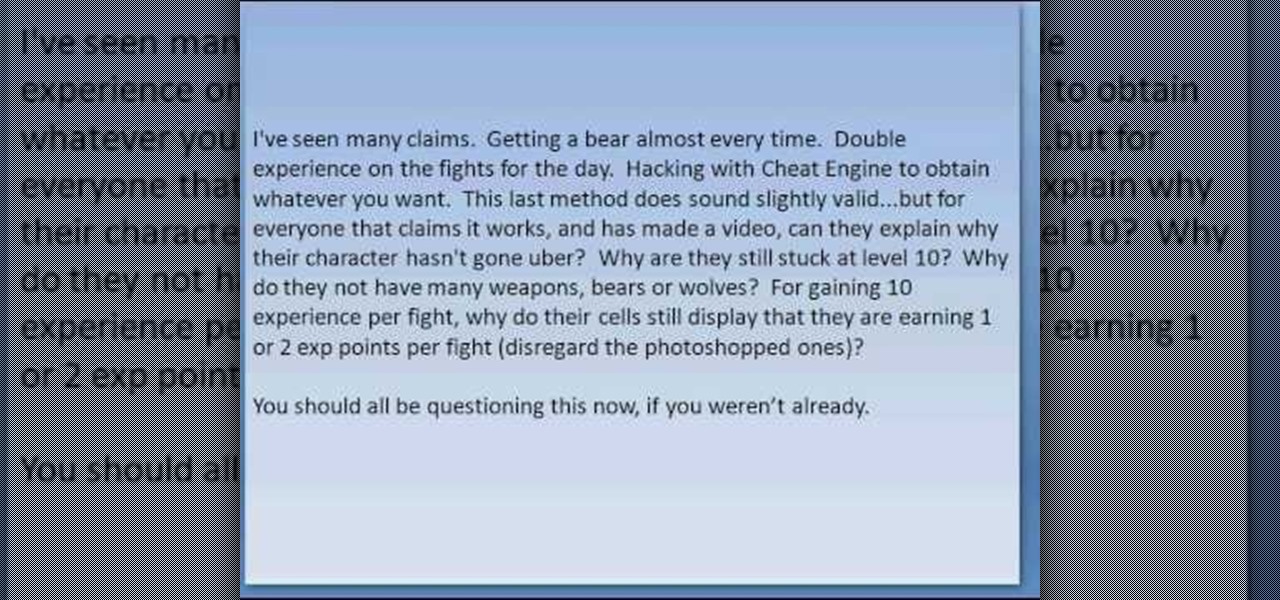
For all those people who are looking for ways to cheat, hack, or otherwise exploit mybrute.com. Here is the perfect, and 100% guaranteed method.

There are lots of Linux distros out there. Normally, you'll have to download the ISO and then burn the image onto a CD. But nowadays, it's easier and cheap to install it on a USB drive.

The term "hacker" often has negative associations attached to it, yet the world is in dire need of professionals with hacking skills. White hat hackers are ethical computer hackers that use their hacking skills to pinpoint network vulnerabilities and patch them up before they can be exploited by the bad guys.

If you've tossed around the idea of turning your interest in white hat hacking into a career in cybersecurity or IT, now's as good as time as ever to invest some time and energy into improving your skill set.

Downloading third-party screen recording apps can be dangerous. The primary function of these apps is being able to record everything on one's display, so it's easy to see how a malicious developer could exploit this for their own gain. That's why the addition of Android 10's built-in screen recording is so impactful.

Samba can be configured to allow any user with write access the ability to create a link to the root filesystem. Once an attacker has this level of access, it's only a matter of time before the system gets owned. Although this configuration isn't that common in the wild, it does happen, and Metasploit has a module to easily exploit this security flaw.

Any internet user will need to download files eventually, and most simply have faith that what they are downloading is trustworthy. This doesn't give much clarity into the contents of the file, but if the file's author published the original checksum, comparing it to the SHA-256 hash of the downloaded file can ensure nothing was tampered with.

To hack a Wi-Fi network using Kali Linux, you need your wireless card to support monitor mode and packet injection. Not all wireless cards can do this, so I've rounded up this list of 2019's best wireless network adapters for hacking on Kali Linux to get you started hacking both WEP and WPA Wi-Fi networks.

As the world goes into a frenzy over the latest strain of WannaCry ransomware, it might be a good time to remember to update all your devices. Yes, those little reminders your phone and computer throw at you every now and then to update your junk can be really annoying, but not without merit.

Welcome back, my budding hackers! In this series, I have been trying to familiarize you with the many features of the world's best framework for exploitation, hacking, and pentesting, Metasploit. There are so many features, and techniques for using those features, that few pentesters/hackers are aware of all of them.

Welcome back, my greenhorn hackers! A few years back, Microsoft implicitly recognized the superiority of the Linux terminal over the GUI-based operating system by developing PowerShell. Since Windows 7, every Windows operating system has had PowerShell installed by default, and they even made PowerShell capable of running Linux commands on Windows!

Hello friends! This tutorial will teach you how to build a local pentesting lab on your Linux machine which will enable you to easily install common web applications so you can practice locating and exploiting their known vulnerabilities (or discover new ones!). In particular, this is an excellent way to learn how to hack Wordpress, Joomla, and Dupral plus many more!

Hello! This is my first post on this awesome website! I know that Windows exploits are less common than the more advanced hacks, but I found something I deem pretty cool and figured why not share it with you all. Alright, enough about me, lets begin.

Recently I was trying to install Kali Live on a USB drive with persistence and struggled to find a tutorial online that was simple and actually worked. After some trial and error I figured out how to do it correctly and decided to make an article for anyone who is experiencing the same difficulty I did. You will need an USB with at least 8GB. Mine is 132GB, nice and large.

Hello all! In this tutorial, I'd like to show you one way of getting root on OS X. Check out this GitHub page for a recent privilege escalation exploit that was recently discovered. I've tested it and it works on both OS X 10.9 Mavericks and OS X 10.10 Yosemite, but appears to have been patched with OS X 10.11 El Capitan. If you check out the file main.m you can see where most of the magic is happening. This source code can very easily be changed to make it do more than just the system("/bin/...

When security firm Zimperium discovered Android's biggest security risk in years, it sent shock waves through the ecosystem. As a result, Google, LG, and even Samsung decided to change the way they issue updates to their devices, by pledging to release monthly security patches to plug up loopholes exactly like this one. Yeah, it's that big of a deal.

Long time reader, first time 'How To' poster. This tutorial has been highly requested. Here are the steps to perform a Pixie Dust attack to crack a WiFi password that has WPS enabled.
If you've got a desktop computer, I can almost guarantee that you've got a widescreen monitor set up in landscape mode. It's how just about everyone uses their monitor these days, including myself. Except that it's not always the best way of working.

Today I am going to teach the various ways that you can use social engineering to hack a system. For those of you that have followed my past tutorials, you know that social engineering can unlock a world of possibilities. This is because no matter how many firewalls, no matter how many patches there are on a server, the password is kept in the minds of people...and people, are not as smart as computers.

Welcome back, my hacker novitiates! Eluding and evading antivirus software and intrusion detection systems is one of the most critical tasks of the hacker. As soon as a new exploit is developed and discovered, the AV and IDS developers build a signature for the attack, which is then likely to be detected and prevented.

It's becoming more and more apparent that Siri continually drops the ball when it comes to lock screen security. In the past, Siri was exploited in iOS 7.0.2 to send messages without needing a passcode. Then in iOS 7.1.1, Siri was use to bypass the lock screen again to access contacts, make calls, and send emails and texts.

Welcome back, my greenhorn hackers! My preference for Linux as a hacking platform is well documented, and I have even created a series of tutorials to train new hackers. Without being proficient in Linux, you can't really call yourself a hacker.

Welcome back, my greenhorn hackers!

If you pre-ordered your Samsung Galaxy S4, it might very well be possible that you're reading this on your brand spanking new Android device. As is commonplace with the release of popular smartphones, rooting instructions are usually released simultaneously. I mean, what's the point of paying so much for an expensive phone if you can't have a little fun? Android developer Dan Rosenberg (aka djrbliss) recently announced that you can root your Samsung Galaxy S4 using the root exploit he origina...