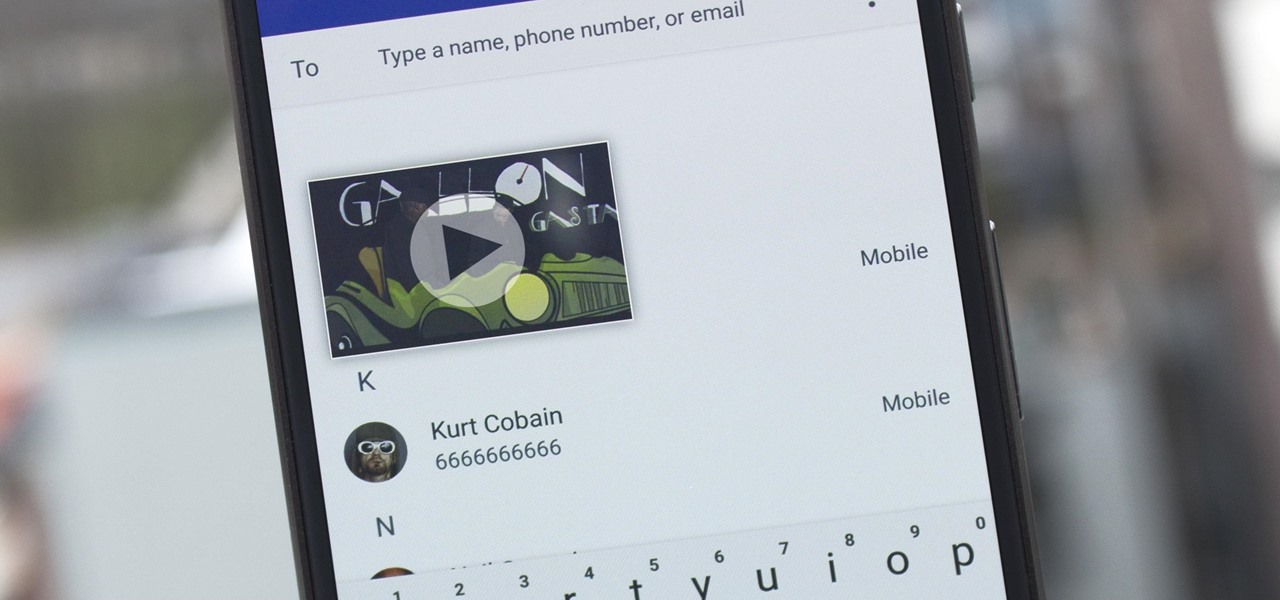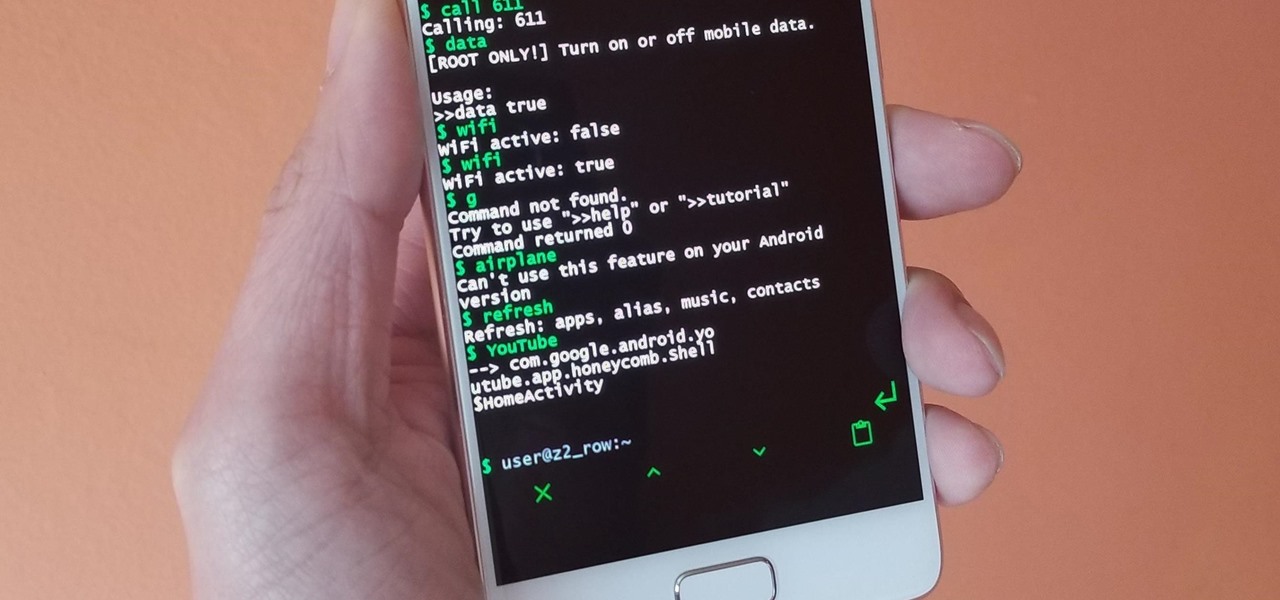
Running commands on Linux seems so complicated for the layman that it may as well be a foreign language. But for the die-hard terminal users, or for those who are just curious about the Linux experience, there's a new Android launcher that gives your home screen a command line makeover.

Augmented reality software developer Edgybees has launched Drone Prix. The new mobile app immerses DJI drones and their pilots in more than 30 augmented reality obstacle courses.

We know your time is valuable to you, so starting this week — and continuing every Wednesday — we are going to release weekly Dev Reports that quickly highlight important news and updates that augmented and mixed reality developers should know about.

Asobo Studios, one of the first companies to partner with Microsoft on HoloLens development, is applying their expertise towards building applications for various business verticals through their internal HoloForge Interactive team.

Sony has upped the ante for the promotion of Smurfs: The Lost Village, which was released on April 7 in the US, with a mixed reality experience via Microsoft's HoloLens.
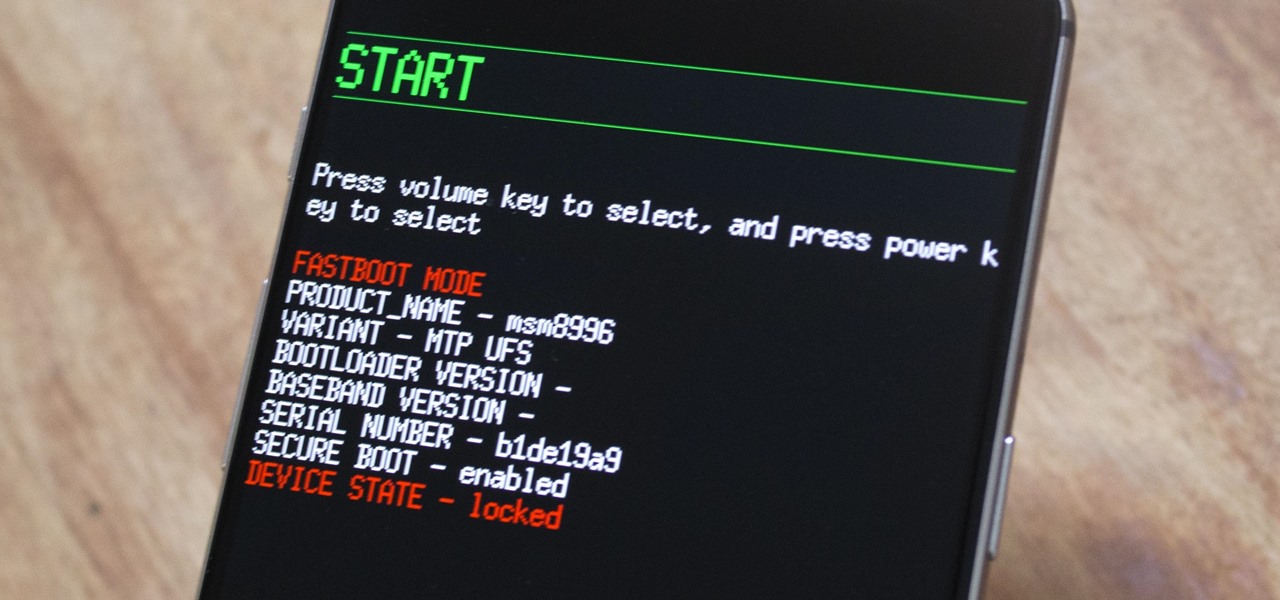
The OnePlus 3 and 3T are two of the most modder-friendly devices to be released in 2016. Not only that, but they're both extremely solid phones which happen to sport a very reasonable price tag. Among the things that make these devices such a joy for tinkerers is the fact that they have an unlockable bootloader, receive timely kernel source releases, and are actually quite easy to root.

The first public beta of Android O, (most likely to be called "Android 8.0 Oreo") was released on May 17, bringing tons of new features and goodies for Android enthusiasts with supported devices. However, not all of Android O's features were available to try out right off the bat. Possibly the single biggest feature announced during the developer preview of Android O, Picture-in-Picture mode, is nowhere to be seen.

Baidu's self-driving car unit has had a tough week. Today, the company's leading artificial intelligence (AI) expert, Andrew Ng, announced in an optimistic blog post that he would be leaving the Chinese search engine company to pursue AI research on his own.

Before you bite into that beautiful tomato in your garden, the tomato fruitworm, or the Colorado potato beetle, might have beat you to it.

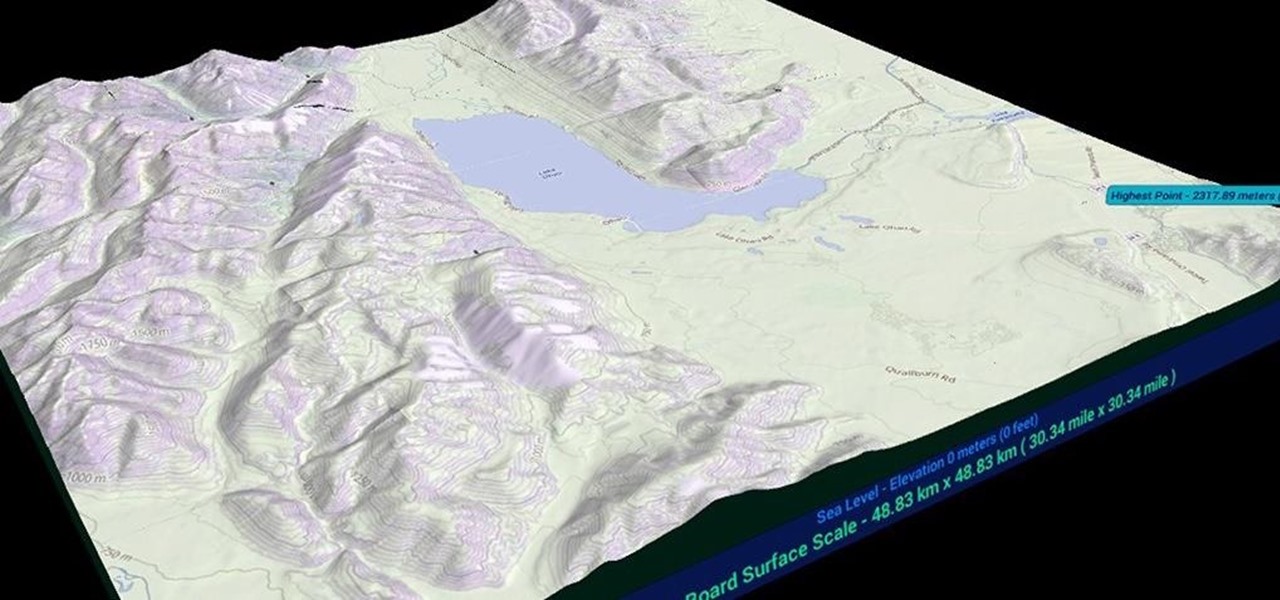
After what appeared to be an issue with the Windows Store for HoloLens not showing many newer applications, including one that I had released over a month ago, Microsoft finally squashed the bug. So, at first glance, it would seem as if there were lots of new HoloLens projects that just appeared in the store, even though they've likely been hiding out there for a while. HoloTerrain is one of those apps.

These days, if you walk through Best Buy, you will see an entire area designated to smart home technology. Thanks to the interest and growth of the Internet of Things (IoT), this exciting new technology has finally entered the mainstream. Appliances, thermostats, and even the lighting throughout your house can be controlled from your computer or smartphone. You could also use artificial intelligence; Simply tell Amazon's Alexa what you want your house to do, and she will do it.

No matter which smartphone you buy, it will come with an internet browser preinstalled. Depending on your OEM, the default browser might be called Samsung Internet, HTC Internet, Silk Browser by Amazon, ASUS Browser, or Google Chrome—there's just so many stock browsers available.

Don't let the lack of owning a HoloLens stop you from joining in on the fun of creating software in this exciting new space. The HoloLens Emulator offers a solution for everyone that wants to explore Windows Holographic development.

Metasploit is an extremely popular pentesting tool capable of enumeration, exploitation, and injecting shell code, and is a part of almost every hacking toolkit. So there's no way I could leave this out of our series on getting your Mac set up for hacking.

One of the main reasons for installing a custom ROM on an Android device is all of the added features. For instance, OmniROM offers a souped-up multitasking mod called OmniSwitch, so instead of the regular app switcher, you get an interface that lets you pin your favorite apps, access settings, view memory usage, and more.

Augmented and mixed reality experiences attempt to break us out of windowed computing experiences and allow us to place software anywhere in the room. But that software doesn't have to take a rectangular form—theoretically, the web doesn't have to restrict itself to a page in a browser any longer. Does this mark the end of the web browser entirely? Probably not. A lot of information works well on the page, and the Microsoft HoloLens still uses a pretty standard version of their own Edge brows...

Although there has been much speculation about how much damage could be done if hackers were to take control of a country's SCADA systems, there have been few examples - until a few months ago, with the power outage in Ukraine caused by hackers.

It's about that time again. Spring weather is here, a new season of Game of Thrones is upon us, and we're getting ready for the next version of Android.

Whether you're ready to admit it or not, we've all got our alter egos—especially when it comes to the internet. Perhaps you have one Facebook account that you use publicly, while maintaining a second account for more private interactions.

Welcome back, my hacker novitiates! Often, to hack a website, we need to connect to and exploit a particular object within said website. It might be an admin panel or a subdirectory that is vulnerable to attack. The key, of course, is to find these objects, as they may be hidden.

If you've ever used the YouTube mobile app for Android or iOS, you've probably noticed a cool little multitasking feature it has. While watching any video, you can simply swipe down on your screen to shrink the video down to a thumbnail view, which then allows you to browse the rest of YouTube while the original video keeps playing.

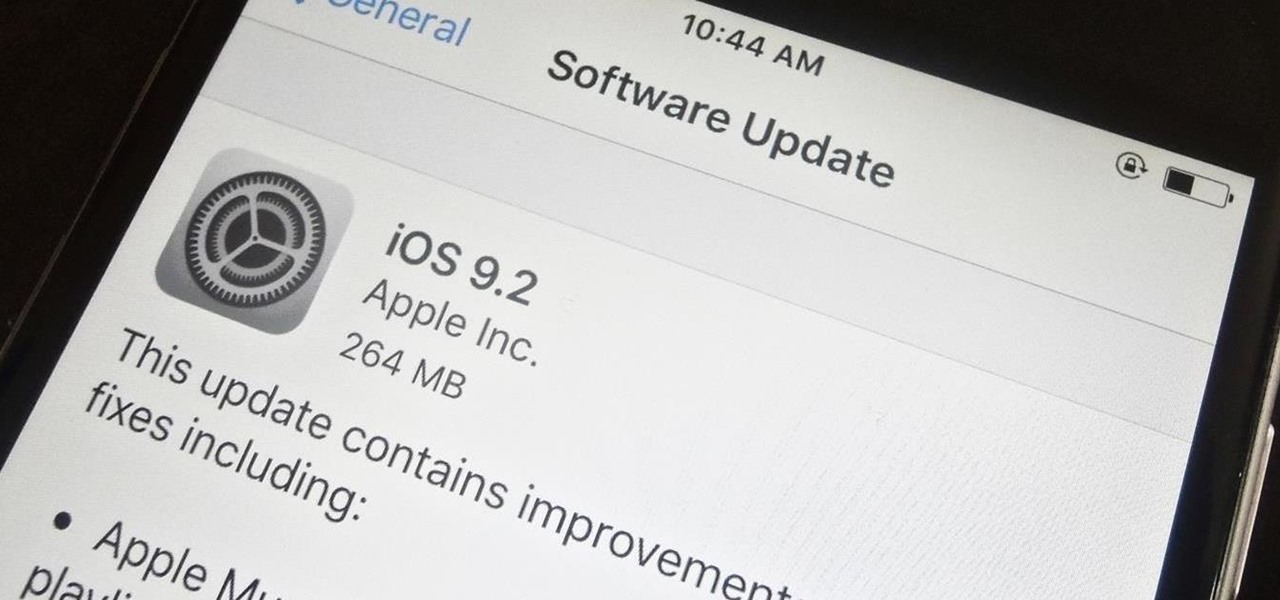
We're near the end of a productive year for Apple, one that introduced a new Apple TV, the iPad Mini 4 (in conjunction with the Apple Pen), the iPad Pro, and the iPhone 6S and 6S Plus, as well as iOS 9. Now, the second major update to iOS 9—version 9.2—has just been released to the public.

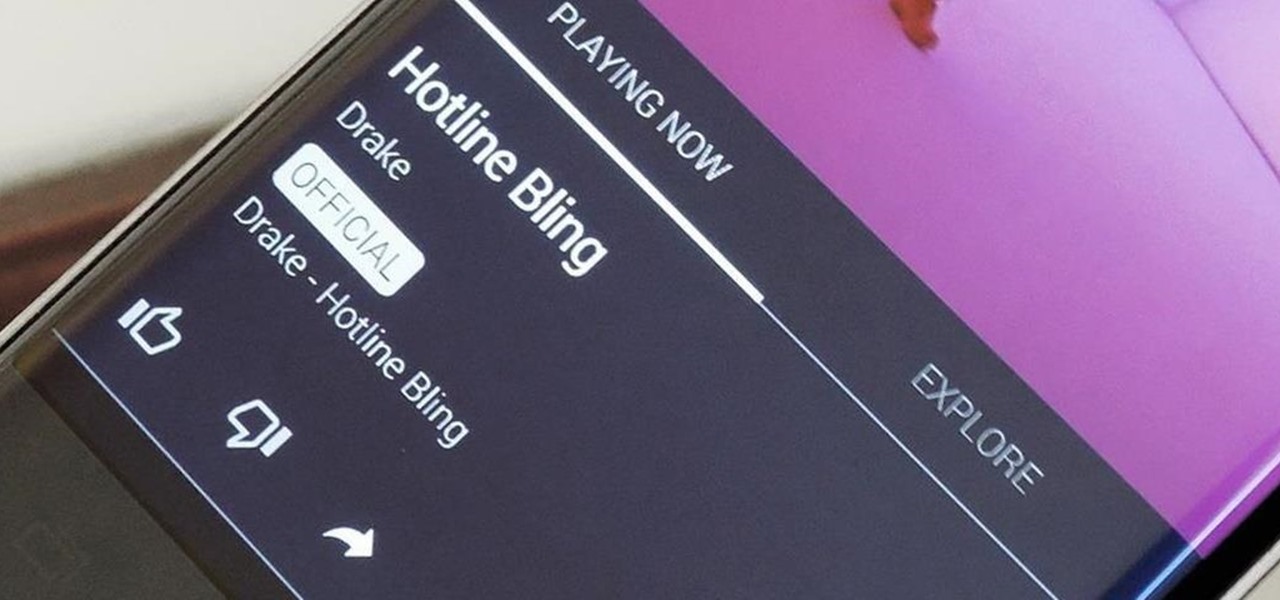
In the wake of Apple Music making its debut on Android devices, Google has finally released its highly anticipated YouTube Music app. With these two tech heavyweights throwing their hats into the ring, the streaming music world is about to get rocked.

Microsoft's "Fall Update" to Windows 10, code named Threshold 2, has a lot of new tricks up its sleeve. It's the biggest update we've seen since Windows 10 was released this summer, and it's rolling out to all users right now.

In this article, we will explore the basics of radare2, a powerful package that comes with Kali. We are going to write a simple program, and then disassemble it, to see what is really doing in the processor.

Greetings dear null byters, today we start a new series, we will start to attack users using social networking that are popular such as Facebook, Skype, and much more, and in part 1 of the series will engage users of Skype.

Welcome back, my novice hackers! This new series on Bluetooth hacking was inspired by a recent episode of Mr. Robot (my favorite TV show). In episode 6, Eliot hacked the bluetooth keyboard of the police office in order to hack the prison and release his nemesis, Vera. This is just one of the many hacks we will explore in the series.

Welcome back, my tenderfoot hackers! In this series, we are exploring the myriad of ways to hack web applications. As you know, web applications are those apps that run the websites of everything from your next door neighbor, to the all-powerful financial institutions that run the world. Each of these applications is vulnerable to attack, but not all in the same way.

The peanut butter and jelly sandwich has officially left the building. When you eat this every other day in elementary school, you've sort of reached your limit. The thing is, peanut butter itself is delicious and quite versatile if used in the right way. Let's explore this kitchen cabinet staple and showcase it via the three dinner courses.

Welcome back, my rookie hackers!

I'm human, so it goes without saying that I love bacon. You're human too, which means chances are pretty good that you also love bacon. Yet as beloved as bacon has always been, it's just now experiencing a culinary renaissance, which I love. Bacon chocolate? Heck yes. Bacon donuts? Bring it on. Bacon booze? Now we're talking.

While its hardware may already be a little outdated compared to newer flagship phones, the OnePlus One is still a great value thanks to the dedicated community that continues to develop ROMs for it. Cyanogen 12 and Oxygen OS are the two most popular ones, but neither offers the type of unique experience you get with Xiaomi's MIUI (pronounced "Me You I").

Rather than reaching for aspirin the next time a headache strikes, try grabbing a drink of lemonade instead. Not only can it help ease your head pain, but it can also help relieve stress, anxiety, and depression. But not just any old lemonade will do the trick—reach for the lavender lemonade.

Hi everyone! In the previous part of this series, I introduced one way to hijack a program's execution flaw, though I only showed you how to crash the program and left you with a little mystery to solve. Today we are giving the solution of that and then introducing shellcode usage and remote command execution.

Hi everyone! Last time we explained what roles Ebp and Esp registers have. We first introduced function's stack frame building, return address and calling conventions, but left some of the concepts floating without a full stop.

The Apple Watch is finally here! We'll have loads of guides and videos for you guys to check out in the following week and beyond, but we thought it'd be best to start off showing you how to set up and pair that brand new beautiful Apple Watch of yours to your iPhone.

Welcome back, my neophyte hackers! In previous tutorials, we learned how to steal system tokens that we could use to access resources, how to use hashdump to pull password hashes from a local system, and how to grab password hashes from a local system and crack them.

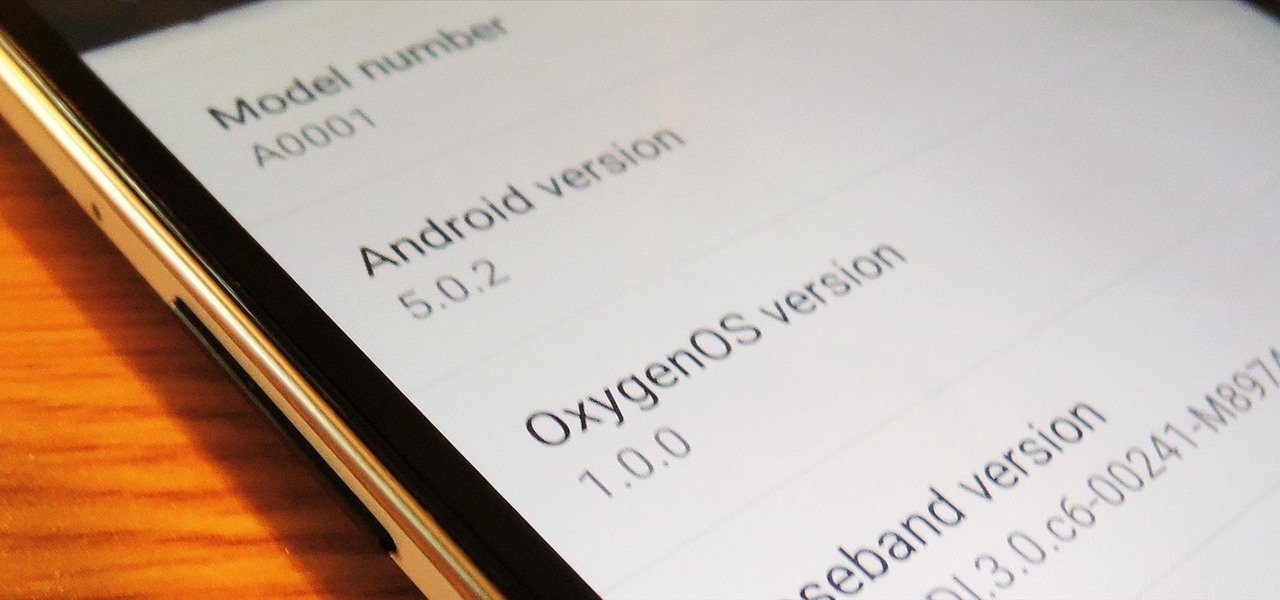
Despite CyanogenMod actively working on their CM 12S Lollipop-based ROM, OnePlus has opted to develop their own ROM, and after a few setbacks, OxygenOS is finally out. The OS is the result of OnePlus wanting to ship their devices without needing an outside company to create a ROM to power it. Like CyanogenMod's ROMs, Oxygen OS offers a vanilla Android Lollipop experience tailored for the OnePlus One.

Inspiration for tutorial: Foxtrot's "How to Trap a Tracker"

Welcome back, my fledgling hackers! In an earlier tutorial, I introduced you to probably the most popular scripting language for hackers, Python. To become a professional hacker, you need to have some scripting skills and Python is a good choice if you want to master just one. In this latest guide, I will expand your background in Python and offer you a tidbit of Python code to whet your appetite for all of the hacking to come.