Barrow's article on Pupy made me wish for a RAT that could target an OS frequently used by gatekeepers at startups, tech companies, and creative firms: macOS. Once run, a RAT can do severe damage by dumping a user's stored credentials for many accounts. The best loot lives in the Chrome Password cache, and EvilOSX, an OS X RAT, infiltrates macOS and dumps these credentials.

While the USB Rubber Ducky is well known by hackers as a tool for quick in-person keystroke injection attacks, one of the original uses for it was automation. In this guide, I'll be going the latter, explaining how we can use it to automate Wi-Fi handshake harvesting on the Raspberry Pi without using a screen or any other input.

On April 7, 2017, residents in Dallas, Texas, woke to the sound of emergency sirens blaring all over the city. No one could shut them off, and after repeated efforts to contain the situation, the city had to shut down the entire system. While the media reported a sophisticated computer hack was responsible, the truth was much less high-tech.

Hello my anxious hackers, the week has started and here we begin a new series that I think will help many here and not only, for those that have the opportunity to follow our tutorials but they are not yet part of the community.

Welcome back, my fledgling hackers! Over the years, we have examined multiple ways to own, exploit, or compromise a system. On the other hand, we have not spent a lot of time on denial-of-service (DoS) attacks.

It would only make sense that Google is one of the most active app developers on the Android platform, particularly when you consider that they develop the platform itself. From my count, there are an astounding 117 unique apps that the search giant and its subsidiaries have published on the Google Play Store.

This is a great glitch that makes you become invisible in Wizard 101. You can turn invisible or you can simply seem invisible by being turned into pets or mounts.

In these videos our expert will teach you how to do at-home waxing as well as what to expect if you go to a spa to get waxing done from a professional. You will learn what types of supplies you need to purchase in order to perform waxing at home. You will also learn about alternative hair-removal products, and the advantages and disadvantages of shaving vs. waxing. In these videos our expert will demonstrate how to do different types of waxing. You will see demonstrations of eyebrow waxing. Y...

Ray Temeyer introduces beginners to the canoe and kayak. The canoe has been used for thousands of years to explore and trade upon waterways and seas. Though motor boats have, for the most part, replaced the canoe for commercial trade canoes and kayaks are very popular as recreational water craft

In these sax video lessons, our expert will explore the basics of tenor saxophone, from how to hold the instrument, embouchure and choosing reeds, to scales, arpeggios and jazz improvisation. Learn the art of playing the tenor saxophone today.

In this video series, Steve Romey, a massage therapist for the elderly and ill, teaches how to give a massage to senior citizens. Learn the difference between ambulatory and non-ambulatory care, how to communicate well with the elderly, the universal precautions of massage, how to massage feet, hands, arms, legs, neck and head, and different ways intuition and spirituality help with massaging the elderly, ill, and active seniors. Massage is a positive and low impact treatment for seniors suff...

In this online video series learn from our expert esthetician Brigette Beasse as she teaches and demonstrates important aspects of a facial treatment.

Game design is among the fastest-growing industries in tech. What once was a passing hobby or niche job has become a thriving industry with a huge variety of work. If you are interested in learning game design, either as a hobby or a profession, then The 2021 Complete Learn to Code by Making Games in Unity Bundle will hold some interest for you — and it's on sale for $39.99.

Having the right air quality can turn a room into an atmosphere. With a humidifier, you can see your skin dewy and your sinuses clear. Proper temperature control will keep you comfortable and content, and the right air purifier will give you clean air and peace of mind. If you're in the market for a humidifier, an air conditioner, a heater, or an air purifier but just need to find the perfect one to match your needs and your budget, then check out some of these great deals.

As necessary as sleep is, millions of people struggle with it every night. More than 50 million Americans suffer from any number of sleep disorders. If you're one of them and want a more satisfying, consistent sleep, then the LectroSound Sleep & Relax Soothing Noise Machine may be the perfect addition to your bedroom. For only $15.99, you can give yourself the rest and reinvigoration that your body and mind crave.

In this year of everything going virtual and remote, it makes even more sense now that Hollywood is leaning heavily on augmented reality. In this case, it's HBO using AR to promote its highly-acclaimed original programming.

There's no denying that adding more programming languages to your arsenal is crucial to boosting your career, but learning a new language in the literal sense is just as enriching and mentally stimulating. Not only will you be smarter — those who know more than one language are known to have better reasoning, problem-solving skills, and creativity — but it'll also open you up to more job opportunities.

Everybody wants to build an app, but no one wants to start it from scratch. Building a full-blown application — or any other digital product for that matter — from the ground up entails some tedious work, which is why frameworks exist. Django, a Python-based framework, happens to be one of the best

Amazon Web Services (AWS) offers over 200 services, including networking, computing, storage, analytics, blockchain, mobile, and developer tools. Not surprisingly, numerous companies rely on AWS's massive infrastructure. Instead of building their own server farms, they rent space and computing power from AWS's secure and robust system.

Google Drive has been a gamechanger in the business world. First launched in 2006, Google Sheets has become much more than an alternative to Microsoft Excel. The powerful spreadsheet program is a boon for efficiency that's accessible wherever you have an internet connection—or when you have time edit offline.

Data analytics is crucial to the operations of any modern business these days. This trend is going to continue: in three years, 71% of global enterprises predict a rapid increase in data analytics.

Gaming immerses you in environments. To get the most out of the gaming experience, you want the most immersive experience possible. That starts with great audio.

Data analytics is one of the hottest fields around. With so much data at our fingertips, top companies are seeking experts to put all of this information to real-world use.

Now that the transfer tool for migrating your Google Play Music library to YouTube Music is rolling out, more fans of the former, which will meet its end in 2020, are giving its replacement a try.

Penetration-testing frameworks can be incredibly useful since they often streamline certain processes and save time by having a lot of tools available in one place. Of course, the most popular pentesting framework is undoubtedly Metasploit, but there are many others out there that cater to particular needs. For auditing web applications and servers, Tishna comes in handy.

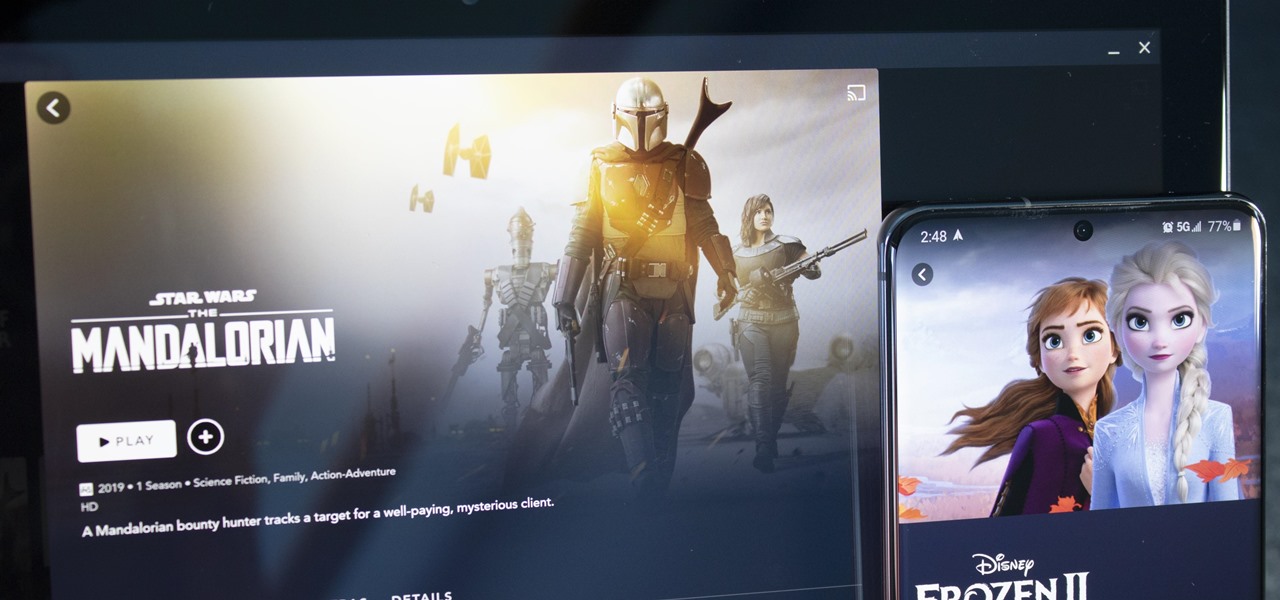
With shows like "The Mandalorian" and movies like "Frozen 2," Disney+ has quickly become a must-have streaming service. However, with Netflix, Amazon Prime Video, and Hulu, adding another subscription-based service can become expensive — but there are ways to trim down the cost.

Hacking web applications can sometimes be challenging due to the sheer amount of moving parts they possess. At the core of these apps are HTTP requests and parameters, but these things are often concealed from the user, due to security reasons, convenience, or both. However, a tool called Arjun can be used to discover hidden HTTP parameters in web apps.

Anyone who has used Linux long enough is familiar with sudo. Short for superuser do (or substitute user do, depending on who you ask), it allows users to run commands as either root or another user on the system. From a hacker's point of view, sudo is often all that stands between them and root access. We'll be exploring an older vulnerability in sudo that allows a user to run commands as root.

The impact of the COVID-19 pandemic caused by the novel coronavirus has practically guaranteed that the virus, along with the phrases "social distancing" and "flattening the curve," will rank among the top search terms of 2020. USA Today combined the phrases in its latest augmented reality experience, which quizzes your knowledge in the best practices of social distancing.

There are times when leadership is tested. This is one of those times. As government and business leaders around the world are grappling with the unfolding coronavirus pandemic, the real-time responses to the crisis from many leaders have been great and, at times, less-than-optimal.

Whether you were exposed to the COVID-19 virus or just taking precautionary measures, self-quarantining is a tremendous disruption for anyone. Still, we all have to eat, pandemic or not. But unless you like eating canned food for two weeks, you're going to want to explore other options. That's why food delivery apps are going to be so necessary during such a hectic and uncertain time.

The results of Microsoft's $480 million contract with the US Army are on display and users continue to test the suped-up version of the HoloLens 2.

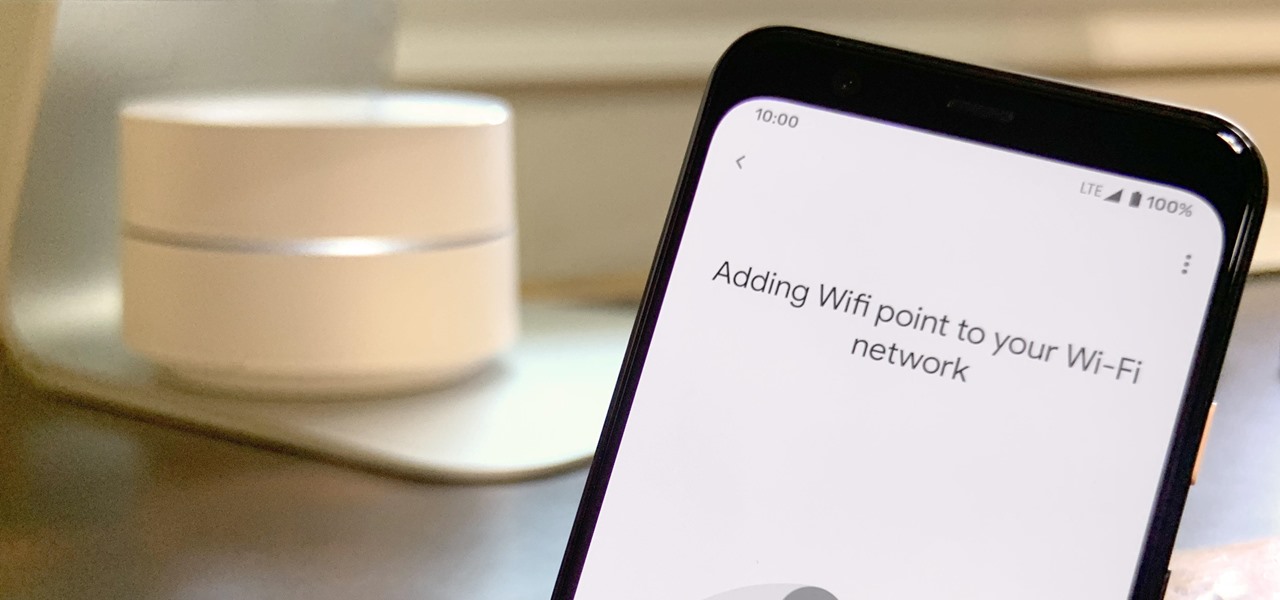
Google is known for merging older products into a new one's ecosystem for ease of use. The transition can take time, and that's the case with the old Google Wifi system now that Nest Wifi is out. Google is working on phasing out the dedicated Google Wifi app in favor of using the Google Home app for all your IoT needs.

Password cracking is a specialty of some hackers, and it's often thought that raw computing power trumps everything else. That is true in some cases, but sometimes it's more about the wordlist. Making a custom, targeted wordlist can cut down cracking time considerably, and Wordlister can help with that.

Android 11 won't be available as a beta update for Pixel devices until May 2020. Until then, the only way to try the latest Android version is by manually installing it. Usually, this means carrier models are left out since their bootloaders are locked, but there's still a way to get it done.

In years past, the Consumer Electronics Show (CES) mostly dabbled in the future as far as the long-term vision for augmented reality was concerned. This year, however, objects in the future are much closer than they appear.

While consumer-grade smartglasses are the holy grail for tech companies, smartglasses maker Vuzix knows where its bread is buttered, and that's in the enterprise segment.

There are many password-cracking tools out there, but one of the mainstays has always been John the Ripper. It's a powerful piece of software that can be configured and used in many different ways. Metasploit actually contains a little-known module version of JTR that can be used to quickly crack weak passwords, so let's explore it in an attempt to save precious time and effort.

It looks like Pokémon GO players may get a surprise gift from the game's developer, Niantic, this holiday season.

No operating system is stricken with as many vulnerabilities as Windows, and it's often a race to release the latest patches to fix things. From an attacker's point of view, knowing which patches are present on a Windows machine can make or break successful exploitation. Today, we will be covering three methods of patch enumeration, using Metasploit, WMIC, and Windows Exploit Suggester.