Samba can be configured to allow any user with write access the ability to create a link to the root filesystem. Once an attacker has this level of access, it's only a matter of time before the system gets owned. Although this configuration isn't that common in the wild, it does happen, and Metasploit has a module to easily exploit this security flaw.

Apple's ARKit has built a considerable lead in terms of features over Google's ARCore, but Google's latest update to ARCore adds a capability that makes the platform a bit more competitive with ARKit.

So you've managed to get a shell on the target, but you only have measly low-level privileges. Now what? Privilege escalation is a vast field and can be one of the most rewarding yet frustrating phases of an attack. We could go the manual route, but like always, Metasploit makes it easy to perform local privilege escalation and get root with its exploit suggester module.

While the long-awaited HoloLens 2 officially arrived this week, details leaked about another, arguably longer-awaited AR headset, the fabled wearable from Apple, and a previously undisclosed partner assisting the Cupertino-based company with the hardware.

Augmented reality gaming pioneer and Pokémon GO mastermind Niantic is putting the pieces on the gameboard to prepare developers and gamers for the launch of its AR cloud platform.

Facebook recently hit a snag in its quest to take augmented reality face effects to its millions of users.

Apple unveiled the latest generation of its flagship earbuds, AirPods Pro, on Monday, Oct. 28. Aside from the increased price tag, new in-ear design, and wider charging case, the biggest change by far is in Active Noise Cancellation. Finally, we can listen to AirPods on a plane, walking by a busy road, anywhere with a lot of noise pollution. But how does it work?

Augmented reality plays a key role in the evolution of adjacent technologies, such as 5G connectivity and brain-control interfaces (BCI), and the business news of the week serves up proof points for both examples.

Your iPhone has seen a lot of new features in a very short amount of time. For starters, iOS 13 introduced over 200 of them, including, among many others, system-wide Dark Mode. Before you even had a chance to breathe, however, iOS 13.1 came along and dumped an additional 22 features in your lap. For us beta testers, now its time to explore new features all over again with the first public beta for iOS 13.2.

This week, while Apple was the subject of thinly sourced reports that it had canceled development of its oft-rumored smartglasses, the Cupertino was actually laying the foundation for its AR hardware future with a new initiative focused on mentoring Chinese developers in mobile AR development.

When it comes to augmented reality (AR) on Android, you might be wondering how you can get those cool new games and apps on your unsupported phone. Google has an officially supported device list for its ARCore platform, which usually consists of the more modern devices. You won't find very many older devices on the list for a reason, but that doesn't mean your "old" phone can't use ARCore still.

One of the best ways to dig into a website and look for vulnerabilities is by using a proxy. By routing traffic through a proxy like Burp Suite, you can discover hidden flaws quickly, but sometimes it's a pain to turn it on and off manually. Luckily, there is a browser add-on called FoxyProxy that automates this process with a single click of a button.

It is said that the best way to avoid detection when hacking is to leave no trace, and often that means not touching the filesystem at all. But realistically, in most cases, it's impossible not to interact with the filesystem in one way or another. The next best thing to do to throw off any investigators is to change the file attributes to hide activity. We can do this with Metasploit's Timestomp.

While Apple's smartglasses development reportedly moves forward behind-the-scenes, the company continues to build on its AR software foundation in its mobile ecosystem with further iterations to its ARKit platform and the introduction of new AR development tools.

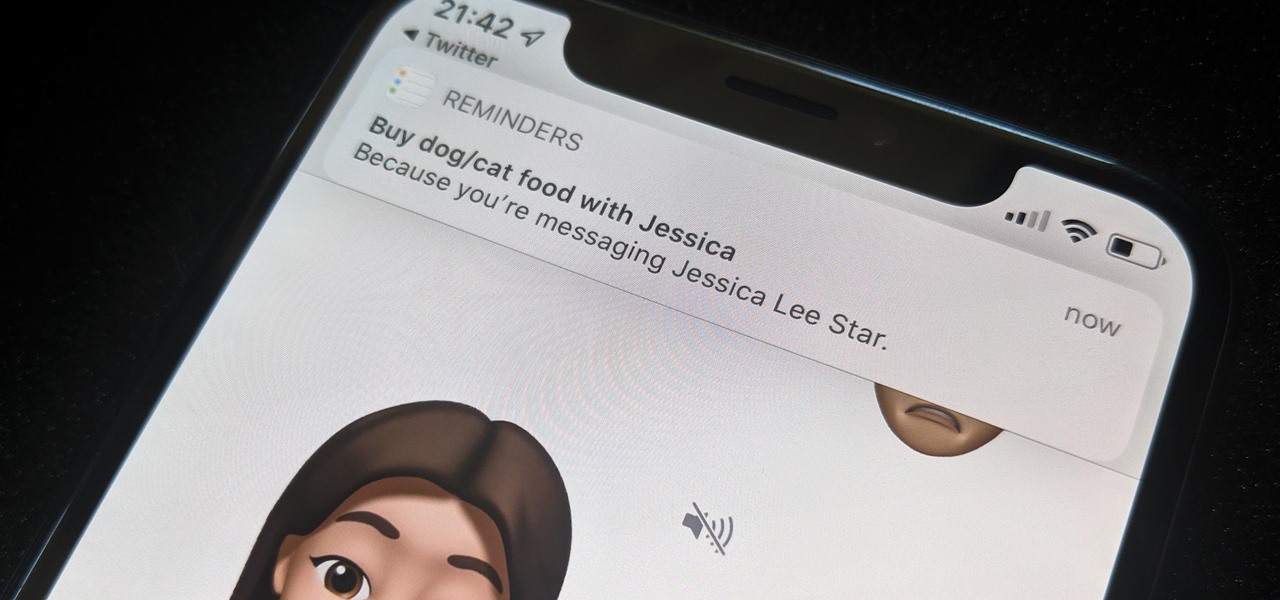
While iOS 13 might have made waves for some of its more prominent features — most notably system-wide Dark Mode — some of the more interesting tools lie with its smaller, unannounced updates. One of those updates is a new Reminders setting to tag contacts in a to-do task so that iOS pings you when texting that person in Messages.

They say home is where the heart is. So, the opportunity to view the inner sanctum of Magic Leap is like gaining access to what makes the company tick, just as the fruits of its labor make it into select AT&T stores.

Websites are often misconfigured in ways that allow an attacker to view directories that are not ordinarily meant to be seen. These directories can contain sensitive information such as private credentials or configuration files that can be used to devise an attack against the server. With a tool called Websploit, hackers can scan targets for these hidden directories without difficulty.

New updates are always exciting, even more so when Google's behind the wheel. Yes, Android 10 "Q" is here, at least in beta form, ready for software testers to dive in and explore all the new changes. Among those changes, however, lie some issues. We won't sugarcoat it — there are some annoying things baked into Android 10.

When you need to know how to get somewhere, Google Maps is the app to beat, but the king of navigation doesn't want to stop there. Google aims to make its navigation app for more than just directions, as made clear by its recent feature that lets you follow businesses in the app. Combining timely news and events posted by local businesses with real-time transit seems like the perfect match.

All of the the tech industry giants, including Apple, Facebook, and Google, are working on new smartglasses and/or AR headsets, but this week, Google took a major step forward with gesture recognition technology that could make its way into AR wearables, posing a threat to Leap Motion and its hand-tracking controllers.

You're minding your business when your Apple Watch taps you. To your surprise, the watch claims your heart rate dipped abnormally low. The news might come as a shock — especially if you have no history of a heart condition — but before you panic, you should take the time to fully understand what this alert is really saying and what you can and should do about it.

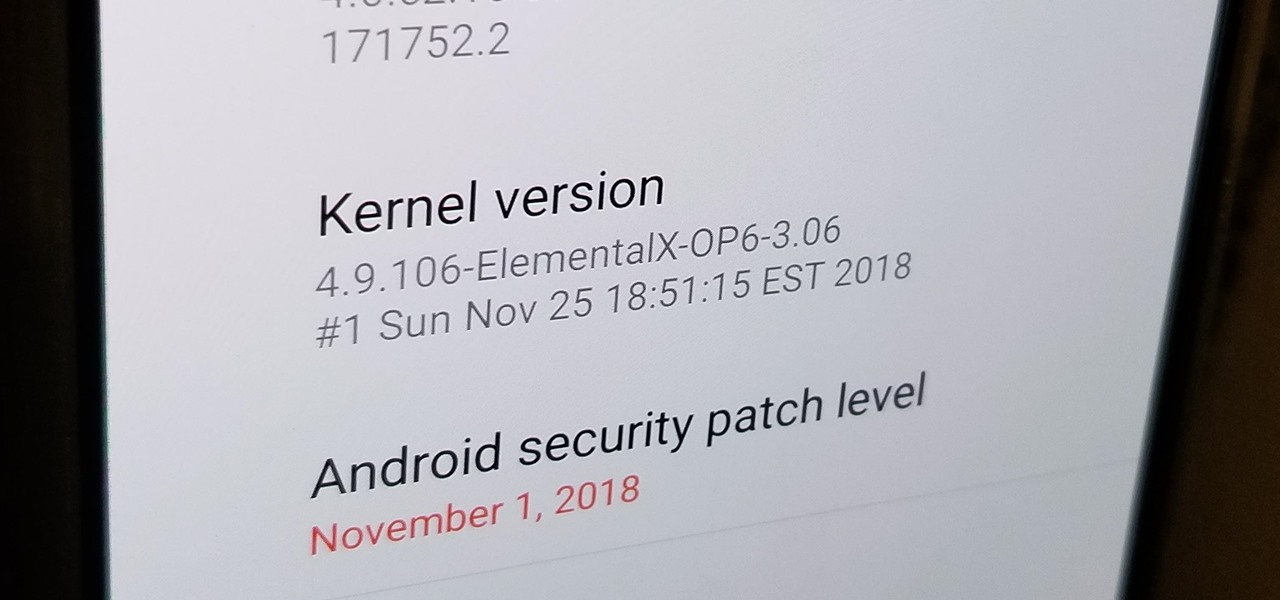
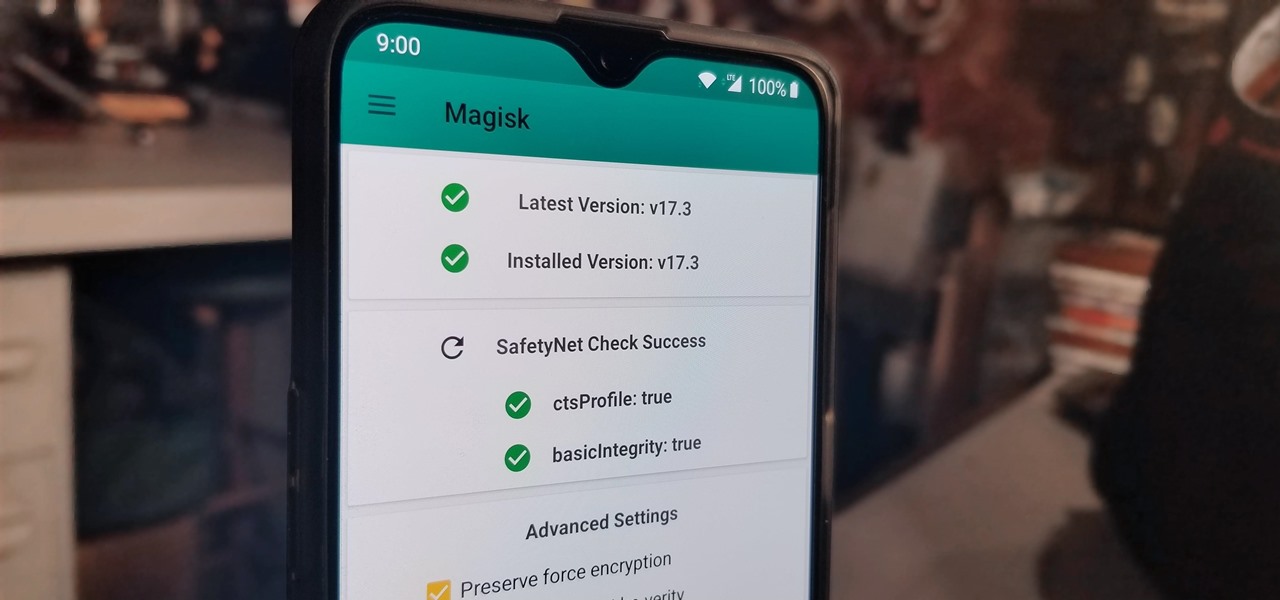
After you unlock the bootloader, install TWRP custom recovery, and flash Magisk to gain root access, what might be the next step of your modding adventure? A custom kernel, of course! Flashing a custom kernel onto your device gives you a whole new level of tweaks and customizations, and it allows you to have full control over how your system performs.

With the recent launch of the OnePlus 6T, the company continues to impress us with some of the best phones when it comes to the rooting and modding. OnePlus has made it easy enough to get up and running with the rooting process as fast as possible. The OnePlus devices follow the same core principles Google uses for their Pixels, which is excellent news for both the user and the development side of things.

Now that its first developer conference is in the rearview mirror, Magic Leap continues to nurture its content development community, this time with an assist from strategic investor and retail partner AT&T.

Hundreds of Windows 10, macOS, and Linux vulnerabilities are disclosed every single week, many of which elude mainstream attention. Most users aren't even aware that newly found exploits and vulnerabilities exist, nor that CVEs can be located by anyone in just a few clicks from a selection of websites online.

Having an efficient workflow is an integral part of any craft, but it's especially important when it comes to probing apps for vulnerabilities. While Metasploit is considered the de facto standard when it comes to exploitation, it also contains modules for other activities, such as scanning. Case in point, WMAP, a web application scanner available for use from within the Metasploit framework.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

Now that the augmented reality cat is out of the bag, Magic Leap is beginning to open up a bit more about how of some of its work came together in the years and months leading up to the Magic Leap One's release earlier this month. On Wednesday, the company unveiled a behind the scenes video of how the ethereal music-meets-AR app Tónandi was produced in collaboration with Icelandic music group Sigur Rós.

Transferring hundreds of screenshots, webcam recordings, keystroke logs, and audio recordings between your VPS and a local Kali machine can be tricky. Services like Dropbox don't always have the best privacy policies and suffer data breaches just like any other website. To mitigate these risks, we'll use a secure, open source, and decentralized alternative.

In its latest feature with an assist from augmented reality in storytelling, the New York Times shows readers the virtual crime scene it constructed to prove that the Syrian military conducted chemical warfare against its citizens.

Some of the big guns developing augmented reality technology fired shots at their competitors with announcements and leaked plans this week.

Before Google I/O 2018, the Google Assistant for Android and iOS had only two available voice options to choose from — a robotic female and male voice. But there are now six additional voices, and these ones sound way more natural than any other mobile voice assistant (plus, John Legend's voice is coming later this year).

Getting an insider view of the goings-on at Magic Leap is hard to come by, but occasionally, the company lets one of its leaders offer a peek at what's happening at the famously secretive augmented reality startup. One of those opportunities came up a few days ago when Magic Leap's chief futurist and science fiction novelist, Neal Stephenson, sat for an extended interview at the MIT Media Lab.

MoviePass may be popular with filmgoers on a budget, but it might not be with those of you who are concerned about your privacy, since MoviePass may be logging your location data even when you don't expect the app to do so.

Market boxes are an integral part of the player experience in Animal Crossing: Pocket Camp, but using them effectively can be a tricky task. The item-trading tool between human friends is the locale for both junk and diamond-in-the-rough deals, and it can greatly increase the number of bells you earn if you play your cards right.

Whenever you attend or remotely watch a major Apple event, you're likely to see Phil Schiller, the company's senior vice president of worldwide marketing, unveiling a brand new product on stage. Outside of an official event, Schiller is the second most likely person (after Apple's CEO Tim Cook) you'll find delivering a rare tidbit of new Apple info or perspective to the public.

There are over 3 million apps in the Google Play Store, all optimized for the small screen in your hands. While that number sounds staggering, there are still many online tools and websites that require you to use a mobile browser since app development is expensive. However, that's where Progressive Web Apps (PWAs) come into play, a cost-effective way to turn websites into mobile apps.

Augmented reality was recently named the "Mobile Disruptor of the Year" for 2017 by Mobile Marketer, but the technology is showing no signs of slowing down as we head into 2018. In fact, the technology appears to be gaining momentum.

When you run an augmented reality company worth billions of dollars, backed by some of the biggest names in tech, and you haven't even released a product yet, even late night tweetstorms rank as worthy of dissection. Such is the case with Rony Abovitz, CEO of Magic Leap, who decided to spend a little time on Twitter on Wednesday to outline his vision of the future of immersive computing.

We covered how to upload your library to Google Play Music, but now it's time to delve deeper into the platform. In this article, we'll discuss how to discover new music through a myriad of methods, by using your existing library as a foundation.