A computer’s safe mode is useful when fixing problems or saving work after, say, your hard drive malfunctions. Safe mode can easily be accessed as your computer starts up and is a useful tool to have in your belt.

This video is about how to lock the screen in Mac OS X. 1. Opening the Keychain Access utility: Open up the Utilities folder. You can get to this by either hitting Command+Shift+U with the desktop (Finder) selected, or by opening Finder, browsing to the Applications folder, then double clicking on the Utilities folder.

Your desktop background image is feeling a little dull lately, huh? Fix that with some great background images for any sized computer screen. All you have to do is go to the website Desktop Nexus and find the one that fits your personality. This video shows you where to go and how to find your favorite backgrounds. All you do is search via the search bar on the site or browse around for cool backgrounds. Click "Enlarge" and it will scan you computer for the correct resolution, for the perfect...

In this tutorial, we learn how to take apart an Xbox 360 wireless controller for repair. First, grab your controller and grab a few different sizes of screwdrivers. After this, turn your controller over and start to remove all the different screws from their spots and place them onto a table where they won't fall. now, take the bar code off and take off the final screw that is on the inside. After this, you will be able to take apart your controller and fix whatever issue you are having with ...

In this tutorial, we learn how to create a new Windows partition with GParted software. First, insert your boot CD into your computer, then turn your computer off and it will automatically boot. Next, hit enter to select the first option, then wait for the scan to complete. When done, select your type of keyboard, then hit enter. After this, select your language and then continue to wait for the boot to continue. Once loaded, you will see the main partition. To split this, select it and click...
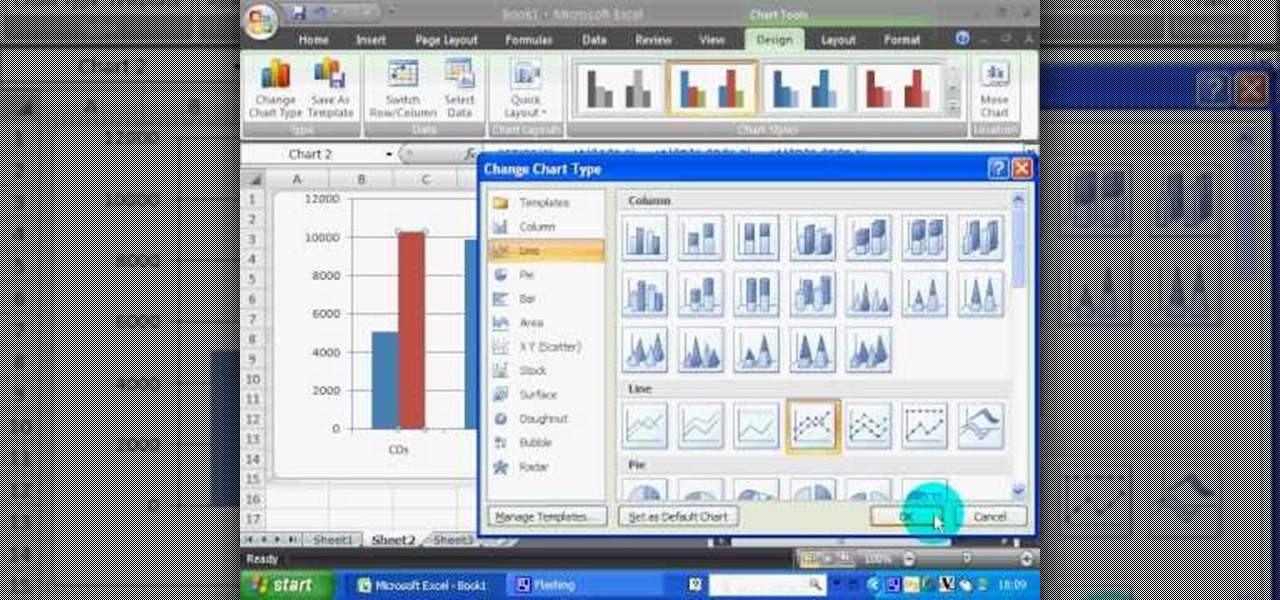
In this software video tutorial you will learn how to create a column line graph in Microsoft Excel 2007. First you type in the data in to the work sheet. Then highlight the data and click 'insert' on the menu bar. Here you select the 'column' option and go down and click on the type of column that you want. And the graph is automatically presented. Now click on 'move chart' and select a sheet where you want the graph to be moved to and click OK. To change any field in the chart in to a line ...

In this video tutorial, viewers learn how to make donuts from biscuit dough. The biscuit dough should be jumbo sized. Then make a hole in the center of the dough. To make a hole, simple place a circular object into the center of the dough and press down on it to cut the hole out. Now fry the dough, making sure that the oil is hot enough. Make sure not to over fry the dough. Then add 1/4 cup milk and mix it with the dough. Now mix and melt a bar of chocolate. Now dip the donuts into the chocol...

On the 2010 Lincoln Navigator there's a handy feature called the deployable running boards, which are essentially step bars that automatically deploy when the car door is opened, to help you step inside your vehicle. This video demonstrates how they work, and how you can shut them on or off, because not everybody will find these useful — tall people definitely won't.

In this tutorial, we learn how to find your computer's IP address. An IP address is used to know the exact location of someone using a computer with internet access is located at. First, turn your computer on and go to your main desktop. Then, click on "start", (which is located on the lower left hand side of the tool bar at the bottom), then click "run" and once that opens up, type "cmd" into the white empty space. Hit "ok" and when this comes up, type in "IPConfig" and hit "enter". Your com...

In this video tutorial, viewers learn how to record songs on the Internet without a microphone. Begin by putting the sound control icon into the application bar. Then go to Volume Control and click on Properties. Click on Recording and then select all the recording options. Now close the window. Then select the mixage on the volume control, but do not close it. Then open the sound recorder in the Start menu and find the song that you want to record on the Internet. Play the song and click on ...

To take apart the controller you will need a Torx t8 screwdriver and a Philips head screw driver. There are 6 obvious screws on the back of the controller and there is one hidden and one behind the bar-code in the battery compartment on the back. Remove all of the screws, push down on the right and left triggers and pull the controller apart. Pull the board apart and don't worry you won't break anything unless you are really rough. Remove the rest of the buttons, they come out just by pulling...

All of us guitar players love to play our favorite songs on our own guitars. Sometimes it is hard to learn how to play specific songs. It can also be difficult to locate a tutorial on how to play these songs! Old Crow Medicine Show's "Wagon Wheel" is a great song that is fun to play, especially for fans of Bob Dylan. By viewing this 5 minute video and with practice, you'll learn how to play "Wagon Wheel" like a professional! If it is hard for you to bar your frets, be sure to use a capo and l...

Delete Your Cookies and Browsing history.

This how-to video shows you how to make an infield base to anchor your baseball centerpiece for your Bar or Bat Mitzvah, theme wedding party, sports theme event, corporate event, etc. Indoor/outdoor grass carpeting covers the infield, baseball bases and baseball (or team color) ribbon add accents. Ideas of what your final centerpiece can look like as well as other enhancements, are also shown. Watch this how-to video to learn how to make your own baseball diamond centerpiece.

If you prefer to use Google or another search engine for everyday browsing in Safari but would also like a more secure browsing experience for all your secret searches, there's a simple way to switch between them quickly while also adding additional layers of security on top of your already clandestine browsing.

The iOS 16 update for iPhone has many new and exciting options, most of which improve the user experience overall. Some of the features and changes fix frustrating issues from iOS 15 and older, and some of those "fixes" can seem annoying if you're used to doing things a certain way.

Screen mirroring software has been around for ages, allowing you to mirror your iPhone to a projector, laptop, TV, or another device. It's useful to have during lectures, presentations, and meetings, so it's no wonder why Apple created its AirPlay technology. However, AirPlay doesn't work in all situations.

After updating to iOS 14 or getting a new iPhone with iOS 14 preinstalled, you'll notice orange and green dots that occasionally appear at the top of your iPhone. These dots appear on all supported iOS 14 devices, from the iPhone 6S to the iPhone 12 Pro Max, and are there to protect you, but how?

Except for the second-generation iPhone SE, all new iPhone models omit the Home button. In its place, the Side button takes charge, taking care of tasks like pulling up Siri, activating AssistiveTouch, and opening Apple Pay. If you swap your older Home button model for an iPhone 12, 12 mini, 12 Pro, or 12 Pro Max, you'll need to relearn simple actions like shutting down and restarting the device.

The Music app for iPhone underwent a significant update back in iOS 8.4 when the Apple Music subscription service was incorporated into the user interface. It then had another transformation in iOS 10 that improved the UI for everyone. But things can still feel a little cluttered in Music, even in iOS 14, especially if you don't or never will subscribe to Apple Music.

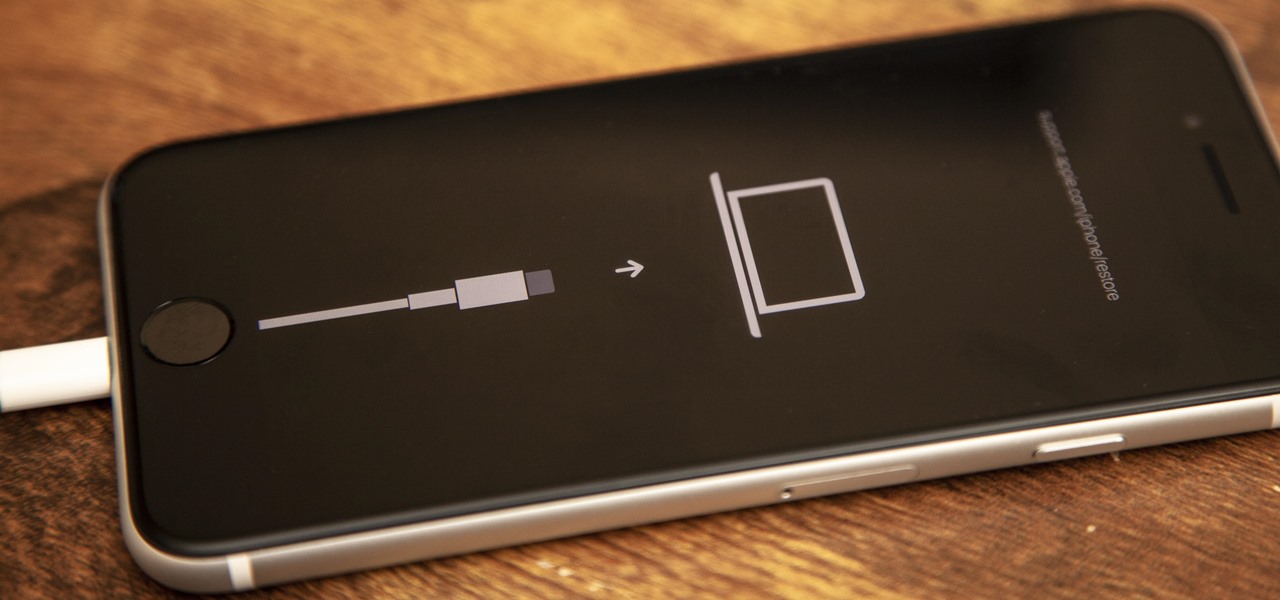
If your new 2020 iPhone SE is frozen, unresponsive, or won't load the system, and a standard power down and up procedure didn't work, there are few more things you can try. Force-restarting the device may do the trick, recovery mode is a last-ditch option, and DFU mode is your fail-safe.

So far, iOS 13's major point updates have all been pretty exciting for iPhone. We've seen iOS 13.1, 13.2, and 13.3 come and go, offering more than 60 new features and changes combined to that very first version of iOS 13. While iOS 13.3.1 was a minor update, its successor, iOS 13.4, is a return to form.

If you're worried about the security of your Mac, there are easy measures to prevent the most dangerous attacks. Named after the tactic of accessing an unattended computer in a hotel room, we can thwart "evil maid" attacks with Do Not Disturb and LuLu, free macOS tools by Objective-See that keep an eye on unattended computers and flag suspicious network connections that indicate a malware infection.

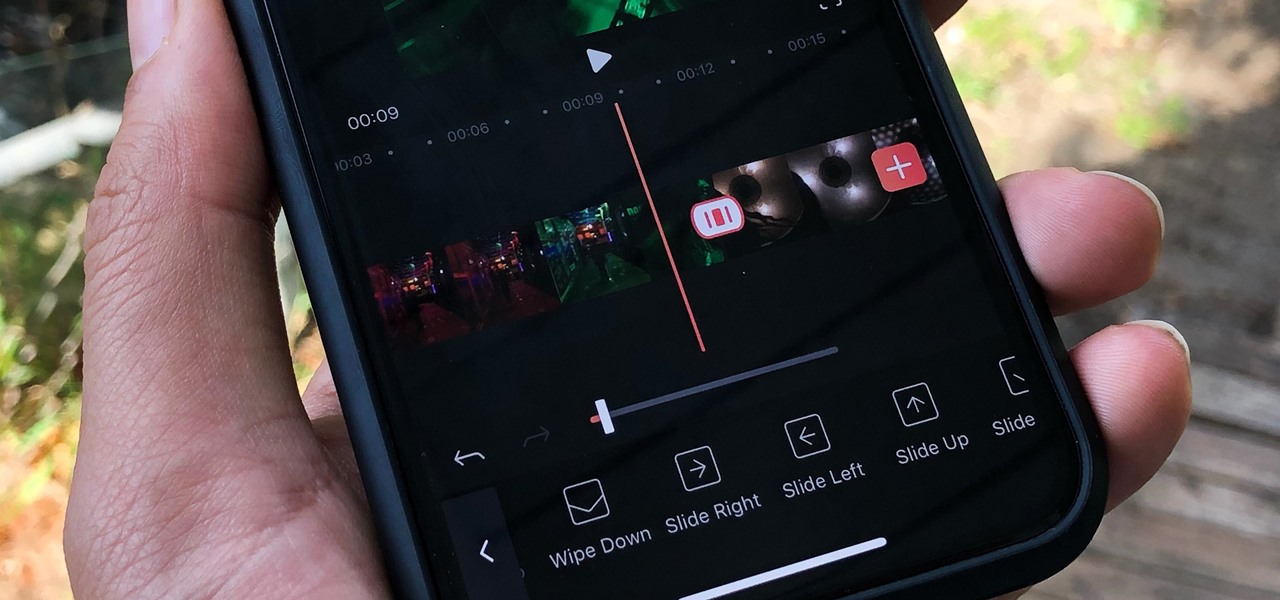
An edited video with lots of different clips needs great transitions to be successful. Transitions support your story and message, and without any, there's always a chance that your audience might lose track of what's going on and when. When editing in Enlight Videoleap for iOS, you can easily add cut, dissolve, iris, wipe, slide, and fade transitions to your video clips with just a few taps.

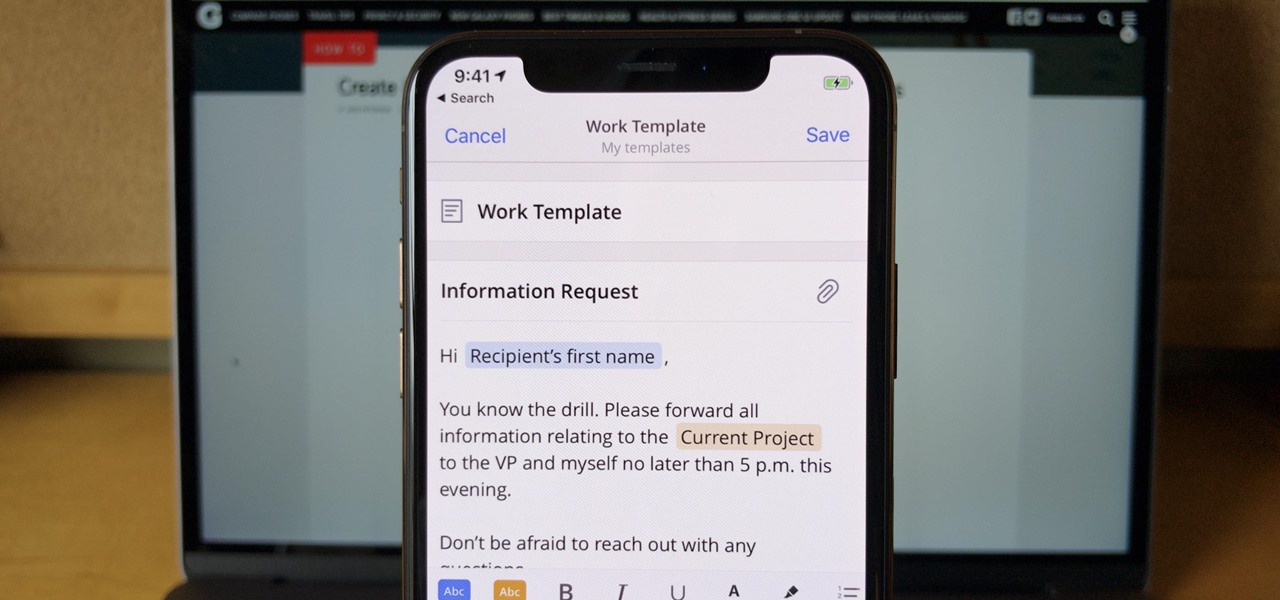
If you find yourself emailing the same email over and over again with just a few changes such as new addressees, or if you're constantly replying to messages with the same response, typing it out every time is, well, a waste of time. Spark, a third-party email client for mobile devices, takes all the work out of this — no matter which email account you need it for.

Since iCloud's introduction in 2011, you get only 5 GB of complimentary cloud storage with your Apple account. With iPhone backups, app data, iCloud Drive files, and even emails (if you have a Mac, Me, or iCloud email address), you'll quickly run out of space to back up photos and videos. Fortunately, Google offers 15 GB of free storage, making it easy to upload your Camera Roll for safekeeping.

Directory traversal, or path traversal, is an HTTP attack which allows attackers to access restricted directories by using the ../ characters to backtrack into files or directories outside the root folder. If a web app is vulnerable to this, an attacker can potentially access restricted files that contain info about all registered users on the system, their permissions, and encrypted passwords.

Twitter's official iOS app is adequate if you're not much of a tweeter, but if you are, there's a lot of useful features that are missing. Luckily, there are plenty of free Twitter clients available that you can use on your iPhone. These third-party apps have features such as customizable interfaces, post scheduling, and different browser options for opening links, to name just a few.

It's not uncommon for hackers to attempt to move laterally between devices in proximity of a compromised device to maintain a prolonged presence in the network. Malware utilizing USB flash sticks to self-replicate and compromise air-gapped machines isn't a new concept.

Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

There's a feature in the Gboard keyboard that enables people who cannot talk, type, or swipe normally to still have a way to communicate in the digital age on their smartphones. While it's mainly an accessibility feature for those who actually need it, it's a good way for anyone to learn or brush up on their Morse code skills — and it works on both Android and iOS.

There are a number of options and hidden menus within Android that provide users more control over their device. With this control, you can better manage how your phone operates. We came up with a list of tips and shortcuts that, when used, will slowly put you on a path to becoming an Android power user.

As a developer, before you can make augmented-reality robots that move around in the real world, controlled by a user's finger, you first need to learn how to harness the basics of designing AR software for a touchscreen interface.

Gboard is one of the best third-party keyboards available for iPhones, but you probably don't know everything you need to know about it to become a real Gboard pro and stop using Apple's stock keyboard for good.

We are most certainly not machines. We all need some downtime every once in a while to set our sanity scales back in balance, which in turn, makes us more productive workers. This is a premise that several forward-thinking employers fully understand, but these types of companies are few and far between in corporate America.

There's a 2800mAh battery powering the Samsung Galaxy S5, but even it's no match for the constant day-to-day torture you put it through. Taking photos, watching videos, and playing games can make your fully charged S5 powerless in no time.

There are definitely some great things about iOS 7, but like any good piece of software, it's got some things to kink out—and how wallpapers work seems to be one of the biggest issues, since it's so much different than in previous iOS versions.

Living in Los Angeles has given me the opportunity to attend a bunch of really cool events. I've been to Dodgers, Lakers, and Clippers games, a few concerts at the Staples Center, and a plethora of smaller joints.

Remote Desktop gives you access to your Windows 8 PC or device from wherever you are to run your applications and access your files remotely.

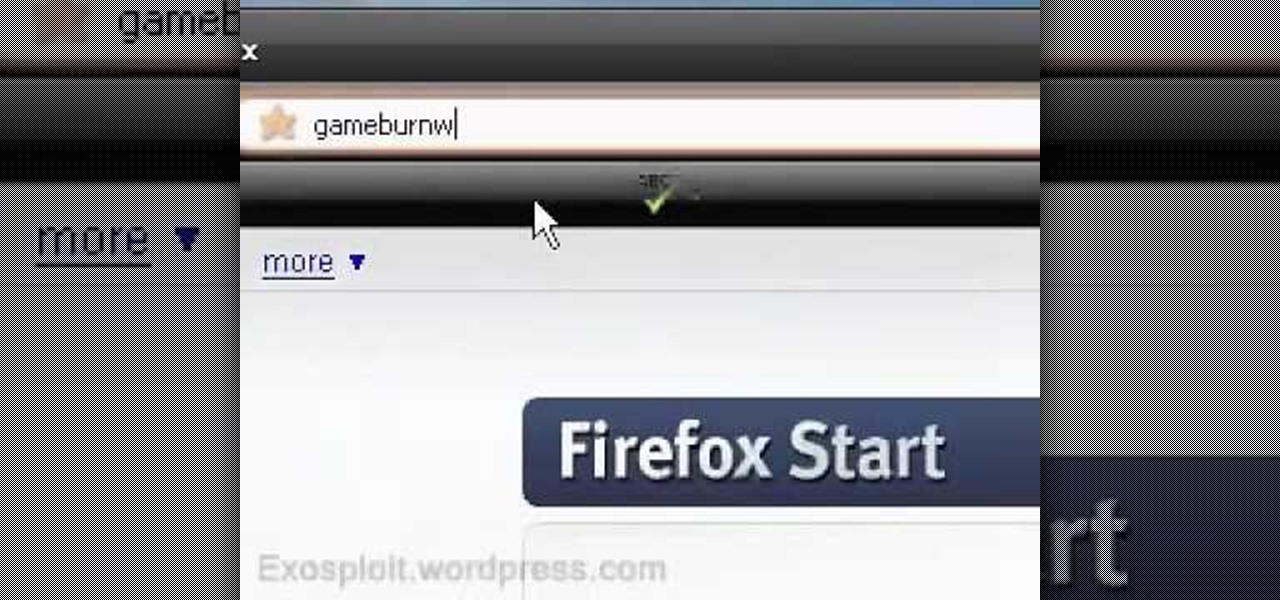
In this tutorial, we learn how to use a "no CD" crack to play PC games without a disc. First, go to www.gameburnworld.com and search for your game using the search bar. Once you find the game you want, click on the version that you want. After this, the game will start to download onto your computer using the software you choose. Once it's finished, install it and open up the executable file. Now, move this file and make a copy of it on your desktop. Now you can delete your original copy and ...