In this day and age, maintaining your privacy is a perpetual battle, and doing so with an internet-connected device like your smartphone is even more of a struggle. Every website you visit, every app you install, every message you send, and every call you make is a potential vulnerability that could expose you to prying eyes.

hello my dear colleagues, I made a visit to nullbyte and found that there is not a complete tutorial about the google dorks, so I felt the need for this tutorial, and seeing that there are many newbies around, so here's a tutorial that will teach you how to use google to hack.

These instructions are applicable to both bObsweep models. Follow the video or text descriptions to replace the disinfecting UV lamp on your automatic vacuum.
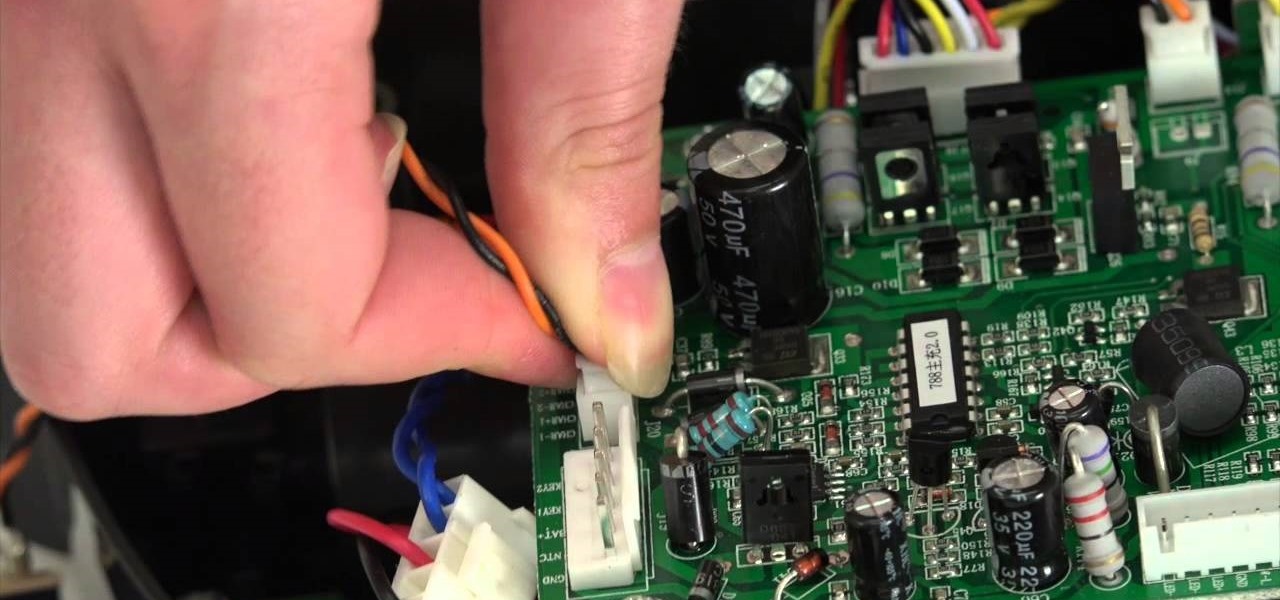
The guide will walk you through a power switch replacement on a bObsweep Standard or Pethair. It includes:

Lemons and limes might be among the most useful fruits in the kitchen and even beyond. Their bright, tart flavor livens up just about any dish, while their mildly acidic nature makes them incredibly useful when you want to clean your house safely. We already knew lemons were great for keeping fruits and vegetables from turning brown, deodorizing garbage disposals, disinfecting cutting boards, and neutralizing odors. But just when we thought we knew all the ways that lemons can be used around ...

Only a handful of food products are impervious to spoilage—dried rice, salt, sugar—but even among those, honey is unique in that it remains edible without any preparation necessary. It's like this: if you came across honey in an Egyptian tomb, as archaeologists have, you could taste it and never guess it was thousands of years old.

When the Chromecast first came out about a year ago, developers were quick to find a way to root the streaming device. Google was almost as fast, however, in updating the Chromecast's firmware to close the loophole that this method used.

People tend to skip toasting nuts in recipes or before adding them to salads because it seems time-consuming and the margin for error is high. However, skipping this step is a big mistake. Why? Because when you skip toasting your nuts (go ahead, you can laugh, we're all doing it), you sacrifice flavor and texture. And not just a little flavor, but a lot. Alton Brown recommends wok-frying peanuts before making your own nut butter for this very reason.

The point of ice in your cocktail is to make it cold, right? Yes and no.

Why can't I see who is stalking my Facebook profile?

The airline is not your friend. It will do anything it can to gouge your dignity, time, and most of all, money. One of the biggest scams to get a few extra bucks out of you are those dreaded baggage fees. If the lines, security, "random" screenings, and unwanted fondling aren't bad enough, you have to pay them to check your bags (which, most of the time, is done poorly). Flying truly is the most inconvenient way to travel.

Sherlock Holmes is one of the most famous characters in modern history, and has appeared in film more often than any other character. No less than 78 different actors have taken their turn at portraying the enigmatic deduction machine in various mediums, and each has brought their own foibles to the role. Some of the names may even surprise you: Tom Baker, John Cleese, Peter Cushing, Charlton Heston, Christopher Lee, Roger Moore, and even Leonard Nimoy.

A travelator, also known as a moving walkway or moving sidewalk, seems like a tricky thing to build in Minecraft, especially when it's zigzagging, but there are really simple autowalks out there (like this one).

If you've never heard of geocaching, it's kind of a grown-up treasure hunt you play everywhere in the world. GPS coordinates are given as clues and the players must find the cache box. There is usually a log book to write your name and a small toy or present to collect.

I always found that those safety lights for bicyclists on the market were never good enough when riding in the dark. That got me thinking about people who use wheelchairs and how unsafe the night could be when they want to go out. So here's what I came up with:

In the first part of this series, we took a factual and technical look at the history of the Internet. I explained how all of these wires and servers got here in the first place. Obviously, a firm did not just create and build the Internet around 1995! Now that we know how the Internet came to be, we can get into the really fun stuff—what the Internet looks like now! Well, that's not quite the network design I was talking about, but it does show what the Internet looked like back in 2007 befo...

If you're always taking blurry and underexposed pics with your mobile device, try using some of the tips below to turn your phone into a valuable photography asset. It doesn't matter if you have an iPhone, Android smartphone, or even a first-gen camera phone... you can still take some beautiful, winning photographs.

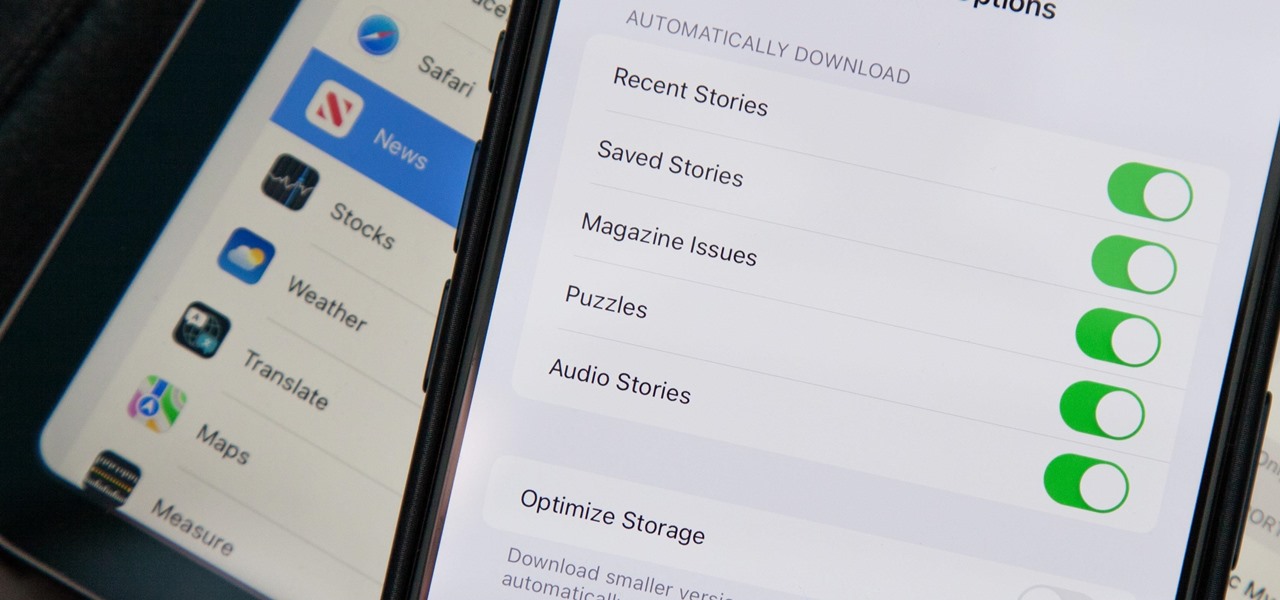
There are a few significant improvements for your iPhone with the iOS 17.5 software update, released May 13, but my favorite is Apple's enhancements to the Apple News app, which is making its Puzzles section even more fun with Game Center integration and even a new type of word puzzle.

In the iOS 17.5 software update, released May 13, there are new features for EU countries and mobile device managers only, but there are also more widespread user-facing changes to Books, Podcasts, and other apps. News is one of those other apps, and it gives us more preferences for automatic downloads.

On this platform, we talk a lot about the future of augmented reality, and we pay attention to what is being said elsewhere as well.

The legal battle between Epic Games and augmented reality startup Nreal isn't cooling off anytime soon.

The experience of actually using the HoloLens 2 can be difficult to describe to anyone who hasn't had a chance to directly interact with the device in person and be blown away by its immersive capabilities.

Some record labels release albums across the entire music spectrum, dipping their toes into every genre, sub-genre, and language imaginable, while others attack only the categories they're good at. So if you're hunting for new music, and the Listen Now, Browse, and Radio tabs in Apple Music are getting stale, iOS 14.5 lets you browse like-minded artists, albums, and playlists by specific record labels.

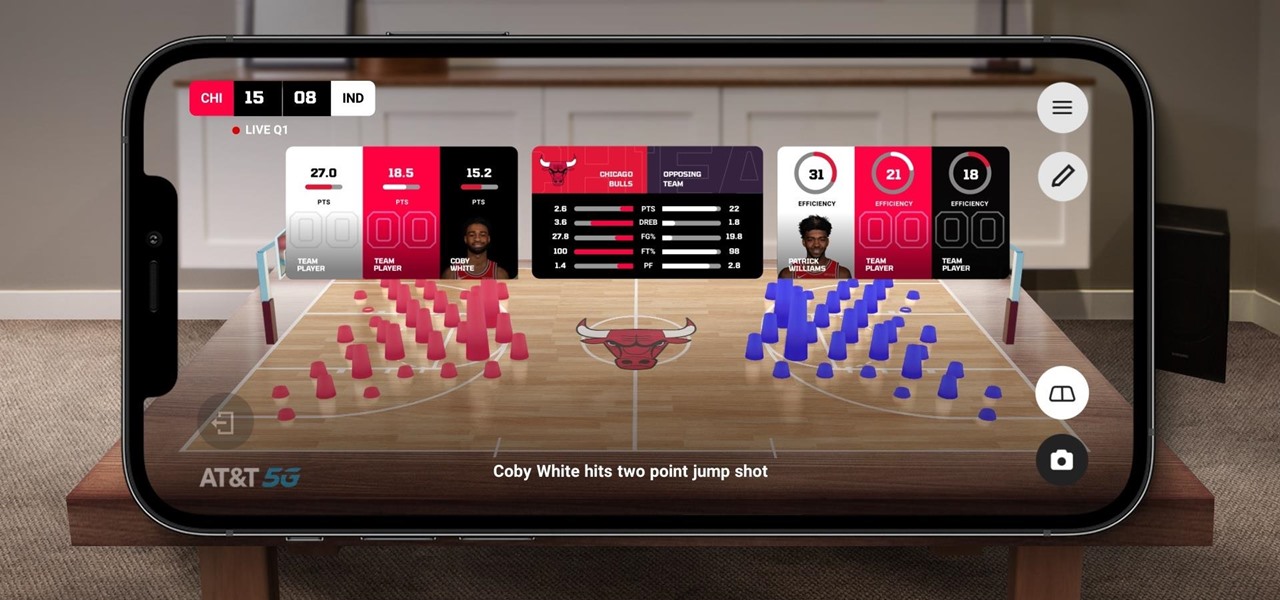
The Chicago Bulls may not be very relevant in the current NBA standings, but they do lead the league in one other area.

Earlier this month, the rumor mill suggested that Apple was gearing up for a Mar. 23 event, with a possible release of iOS 14.5 to boot. That event, as we can now see, never came to be. It seems Apple is also not quite ready to unveil iOS 14.5, either, as we now have a fifth beta to test on our iPhones.

Android 11 made a pretty significant UI change to the menu that appears when you press and hold your power button. Google created an entirely new system that apps can use to populate quick toggles in this menu, but the trouble is, not many apps are using this system yet.

In the tech world, our data is always under attack. When you download and install a new app, it can be difficult to know what information the app is actually accessing. Thankfully, a new emphasis on privacy in iOS 14 changes the game, exposing more of what your apps want access to — and even changing some behavior along the way.

As government officials scramble to contain the new coronavirus outbreak with bans on large gatherings, travel restrictions, and school closures, the rest of us have to worry about how we're going to safely purchase water, toilet paper, groceries, and other household goods during the global COVID-19 pandemic.

If you have a cat, trying to get all of the little clumps out of the litter probably feels like an impossible task. It pretty much is, but we've found the best cat litter scoop that gets more of those tiny pieces out than any other scoop. Plus, it's sturdy, degradable, and ethically sourced.

Apple might not have been the first to add a night camera mode to its suite of smartphones, but it's pretty impressive nonetheless. With "Night" mode, your iPhone can shoot photos with incredible detail in some horrendously dark lighting conditions. But when you open up your new iPhone to try it out, you might be wondering how you turn it on.

Websites and web applications power the internet as we know it, representing a juicy target for any hacker or red team. TIDoS is a framework of modules brought together for their usefulness in hacking web apps, organized into a common sense workflow. With an impressive array of active and passive OSINT modules, TIDoS has the right instrument for any web app audit.

A lot of people still trust their web browsers to remember every online account password for them. If you're one of those users, you need to adopt a more secure way of managing passwords, because browser-stored passwords are hacker gold mines. With a USB Rubber Ducky and physical access to your computer, they can have a screenshot of all your credentials in their inbox in less than 60 seconds.

Giving up your Wi-Fi password can be giving up more control than you think. Because of the way Chromecast and other IoT devices communicate, anyone on the same Wi-Fi network as your device can often make it do whatever they want. With a script called "Cast All the Things," we can hijack a Chromecast to play nearly any kind of media with a single command in terminal.

Before attacking any website, a hacker or penetration tester will first compile a list of target surfaces. After they've used some good recon and found the right places to point their scope at, they'll use a web server scanning tool such as Nikto for hunting down vulnerabilities that could be potential attack vectors.

WhatsApp is the go-to messaging app for millions worldwide and its easy to see why. The app can be considered the Swiss Army Knife of texting thanks to numerous features like Group Chats and Status Stories, in addition to striking a great balance between ease of access and overall security.

For 2019, Sony is trying to shake its failures of the past and start fresh. Following the unsuccessful Xperia XZ series, Sony is changing the name of their flagship to a single number: Xperia 1. With the name change comes a few upgrades, one of which is its new look. Secondly, its new display is unmatched in the mobile space.

Over the years, Magic Leap's long-cultivated shroud of mystery led some onlookers to buy into the company's dream before even trying the device, while for others, the secrecy seems to have stoked the kind of resentment and overcorrecting critique usually reserved for the mighty Apple.

Most companies have services like employee login portals, internal-only subdomains, and test servers they would prefer to keep private. Red teams and white hat hackers can find these obscure and often vulnerable services using a tool designed to help protect users from fraudulent certificates.

Reconnaissance is the phase of an attack where a red team or hacker designs a strategy based on the information they can learn about the target, as well as what the available attack surface looks like. These scans can take time to discover relationships, but Raccoon OSINT scanner coordinates multiple automated scans to produce invasively detailed reports on a target with a single command.

An incorrectly scaled object in your HoloLens app can make or break your project, so it's important to get scaling in Unity down, such as working with uniform and non-uniform factors, before moving onto to other aspects of your app.